AbuBakri
@Hackerrr_99
👨🏫 || SECURITY RESEARCHER || PENTESTING ||
Potrebbero piacerti
I am built for this. Talent means nothing without consistency. I’ll show up, put in the work, and keep pushing, because discipline will take me where talent alone never could. I refuse to quit!
We’re thrilled to announce that applications are now open for the H4ckerTreats 6-Month Cybersecurity Internship Program, starting November 3rd, 2025! At H4ckerTreats, we believe in empowering the next generation of cybersecurity minds through hands-on learning, collaboration,…

A society that tells a broke man he doesnt deserves a woman, cannot tell a rich man that he should only have one.
Quick Test: How Many Pentesting Terms Do You Actually Know? 🎯 Can you explain the difference between: Black Box vs White Box vs Gray Box testing? Lateral Movement vs Privilege Escalation? Red Team vs Blue Team vs Purple Team? OSINT vs Active Reconnaissance? Exploit vs Payload vs…

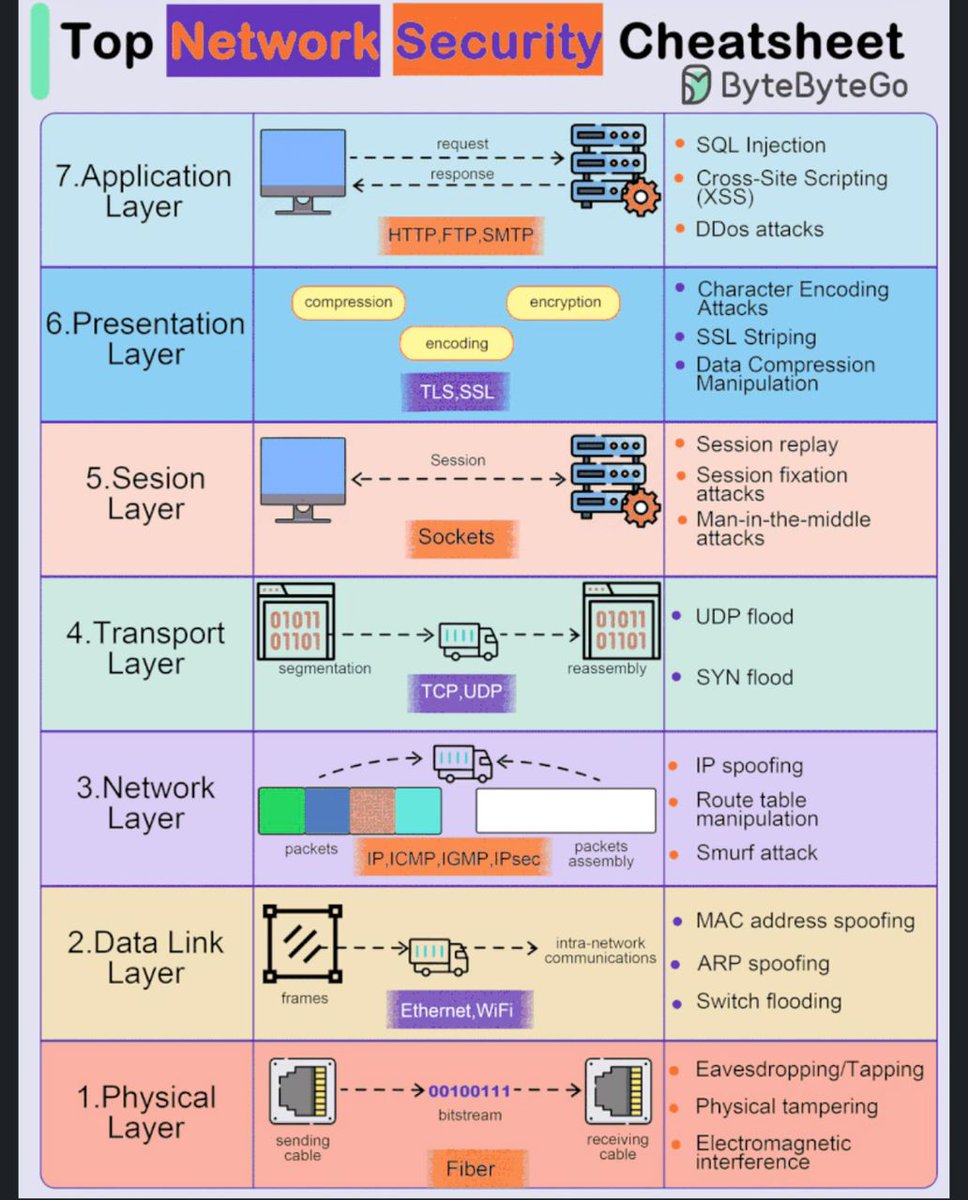
🔐 Network Security isn’t just firewalls and passwords, it’s layered defense at every step of the OSI model. This cheatsheet breaks down the 7 layers of networking and the common security threats at each: 1. Physical Layer: eavesdropping, tampering, interference 2. Data Link…
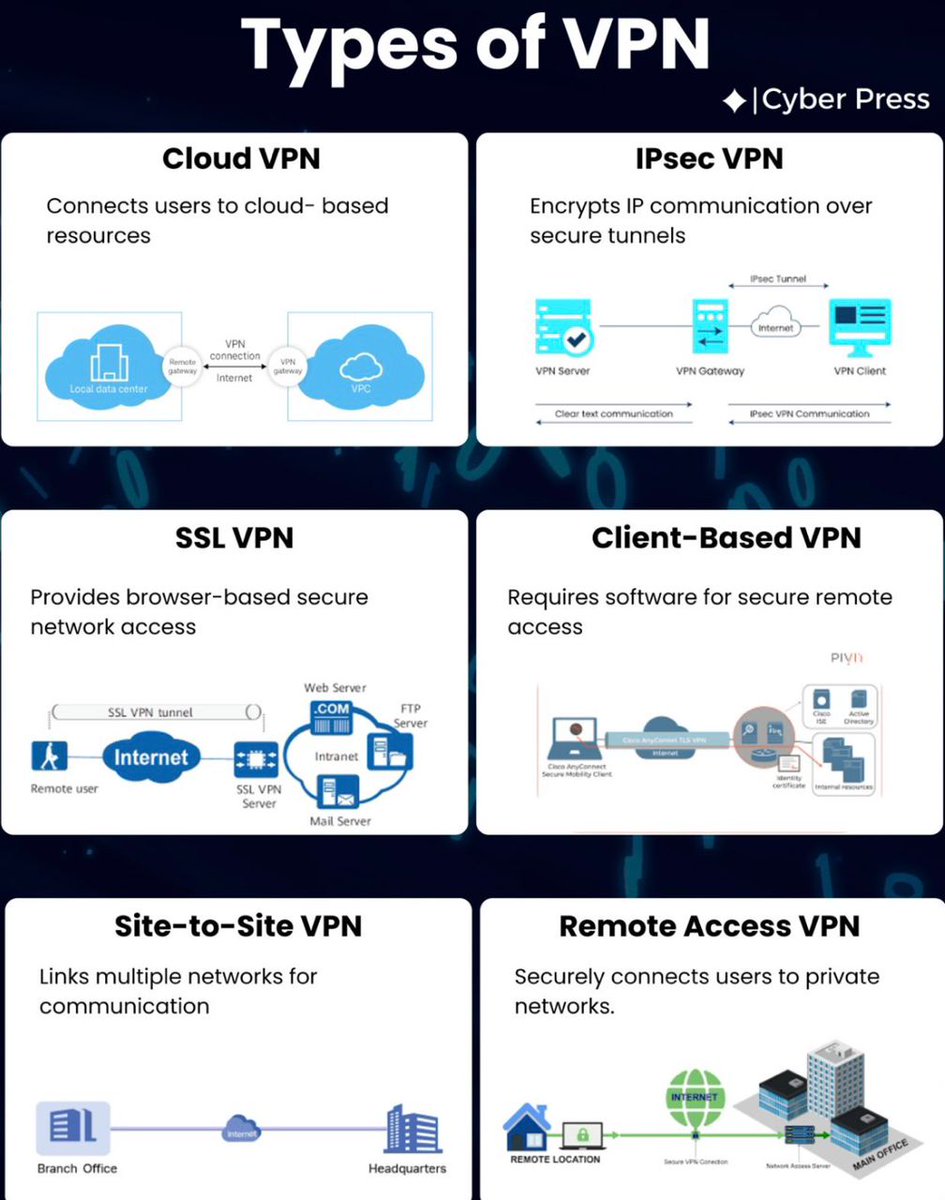
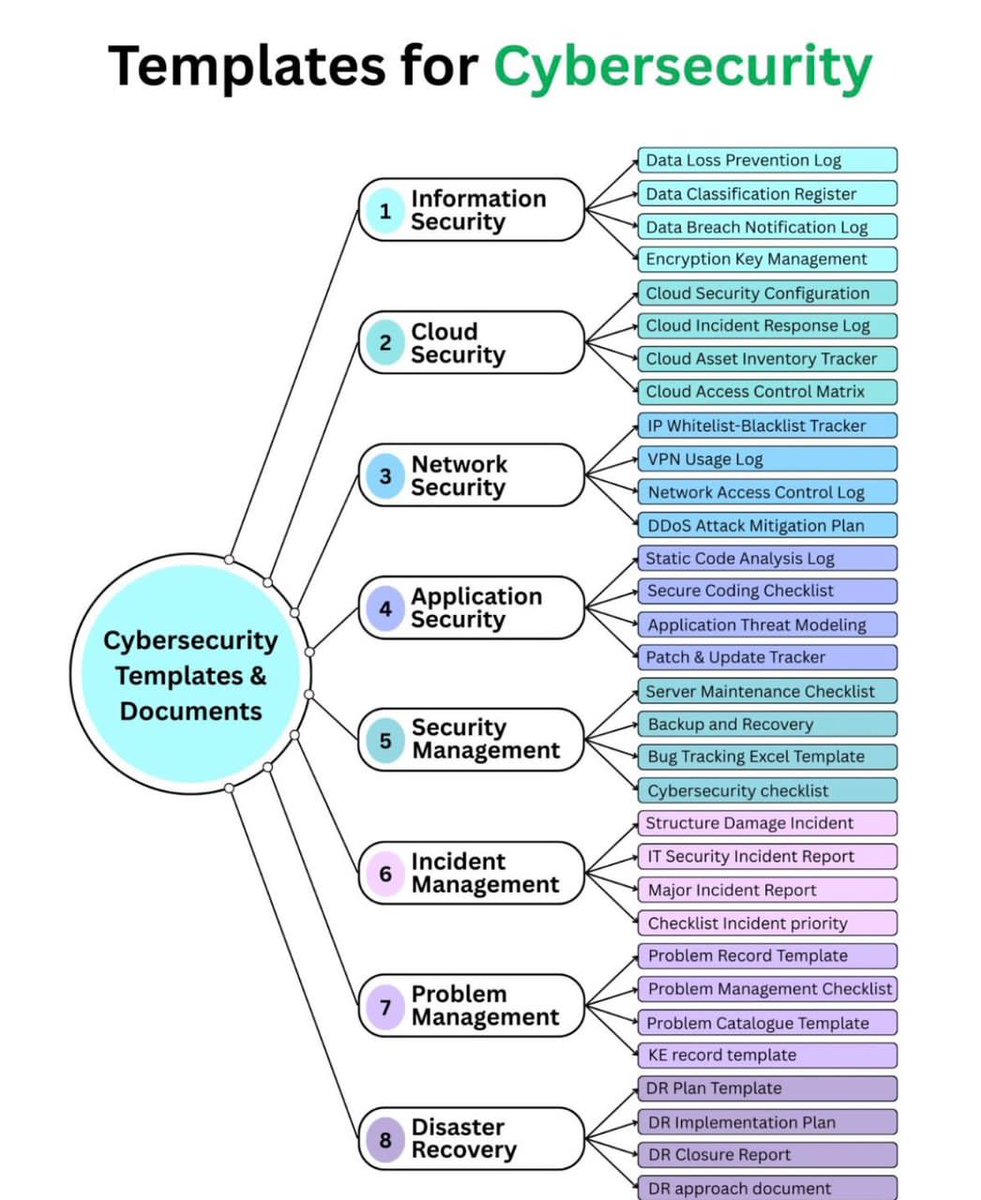
Cybersecurity Complete Suit: Cloud Security: >Cloud Access Control Matrix >Cloud Asset Inventory Tracker >Cloud Backup & Recovery Testing Tracker >Cloud Incident Response Log >Cloud Security Configuration Baseline Network Security: >DDoS Attack Mitigation Plan Tracker >IP…
When I first stepped into the world of cybersecurity, I was completely lost. I didn’t know where to start, what to learn first, or how people even got into this field. All I knew was—I wanted to be a part of this world where people protect, investigate, and defend against…

🔐 Network Security isn’t just firewalls and passwords, it’s layered defense at every step of the OSI model. This cheatsheet breaks down the 7 layers of networking and the common security threats at each: 1. Physical Layer: eavesdropping, tampering, interference 2. Data Link…
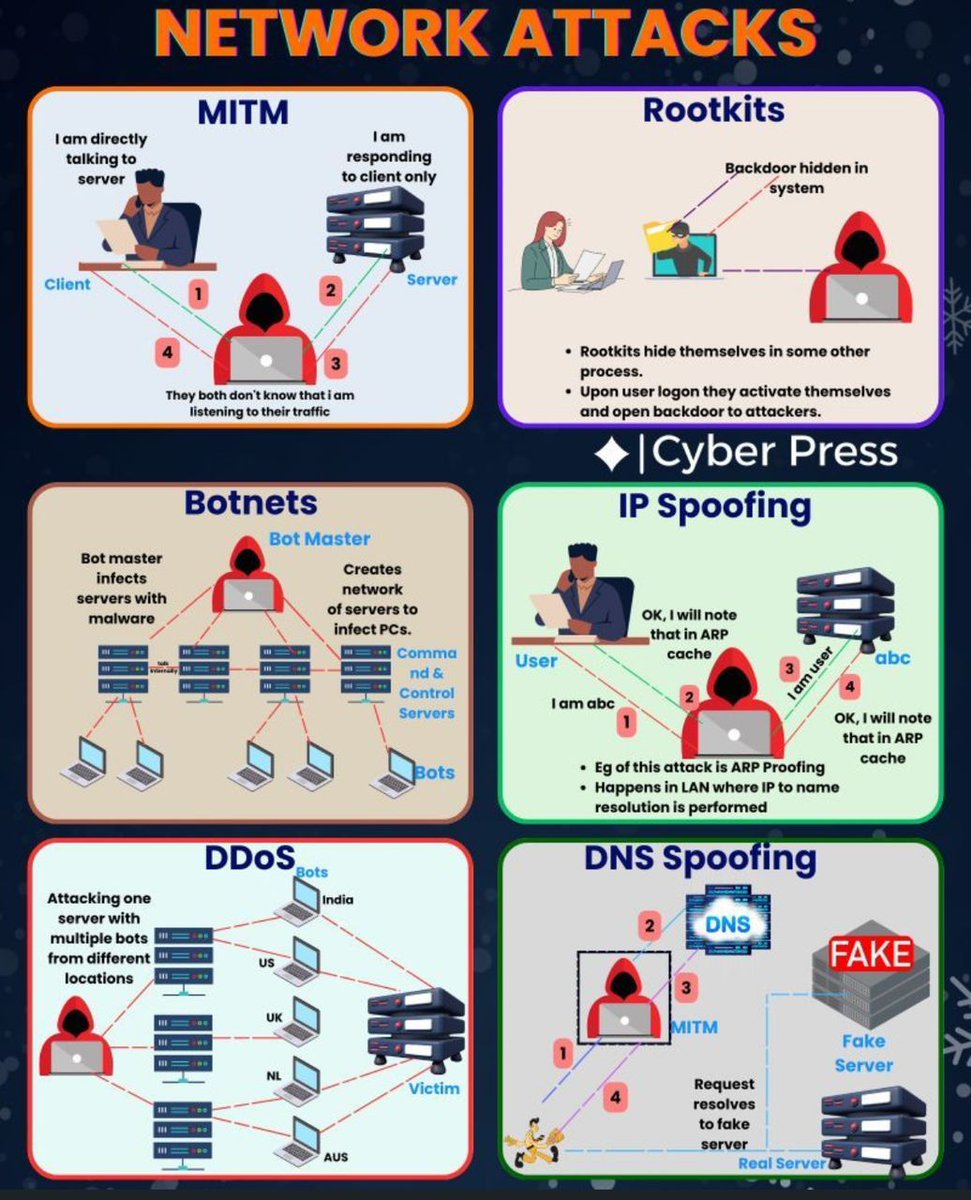
🔐 Understanding Network Attack Vectors: A Comprehensive Security Overview Sharing this detailed breakdown of six critical network attack methodologies that every cybersecurity professional should understand: 🎯 MITM (Man-in-the-Middle) - Intercepting communications between…
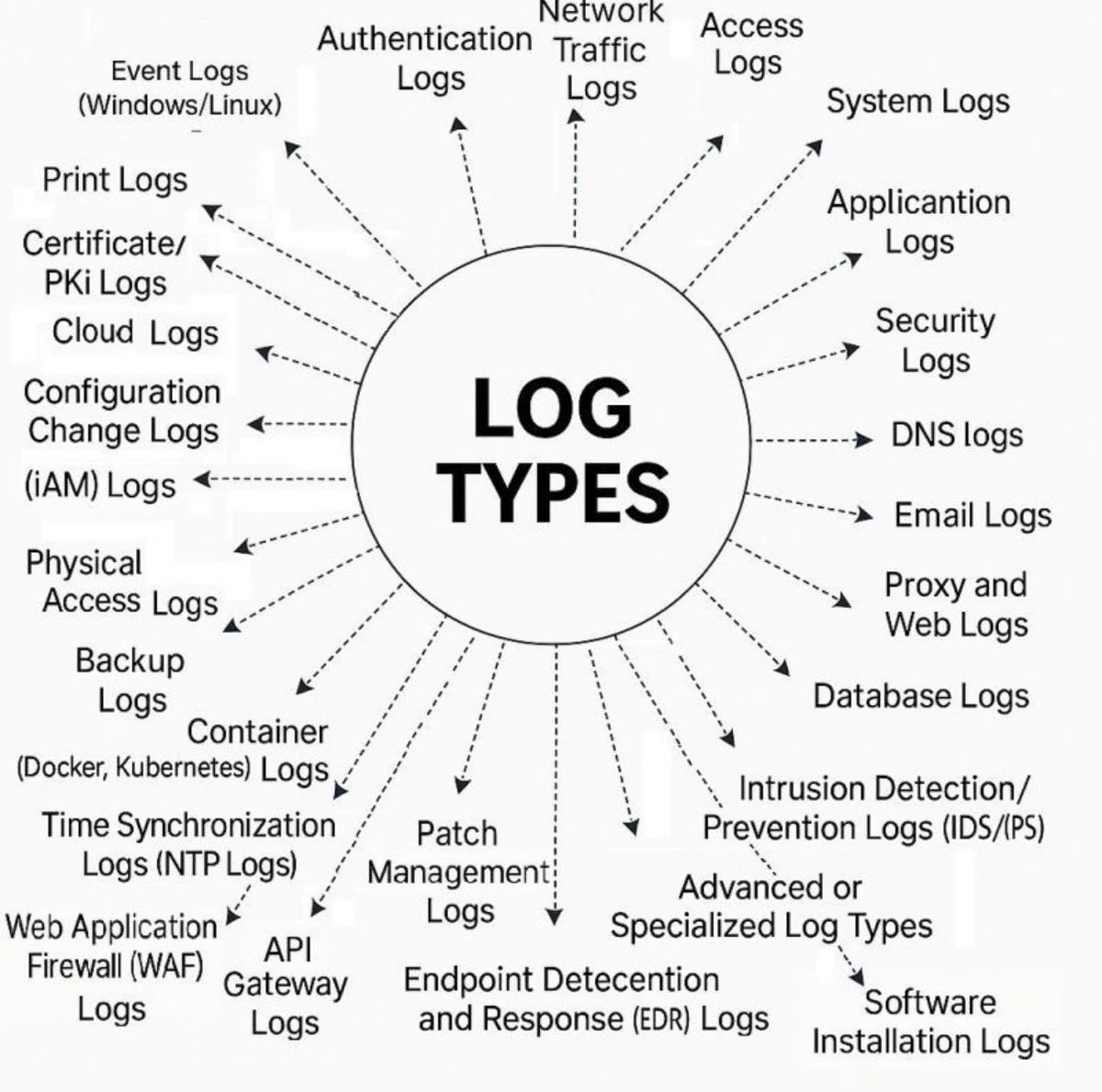
🔴🟣🟢 𝐔𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝𝐢𝐧𝐠 𝐋𝐨𝐠 𝐓𝐲𝐩𝐞𝐬: 𝐓𝐡𝐞 𝐁𝐚𝐜𝐤𝐛𝐨𝐧𝐞 𝐨𝐟 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐌𝐨𝐧𝐢𝐭𝐨𝐫𝐢𝐧𝐠 Whether you’re in a SOC, conducting a forensic investigation, or strengthening your threat detection capabilities, log data is everything. Here's a…
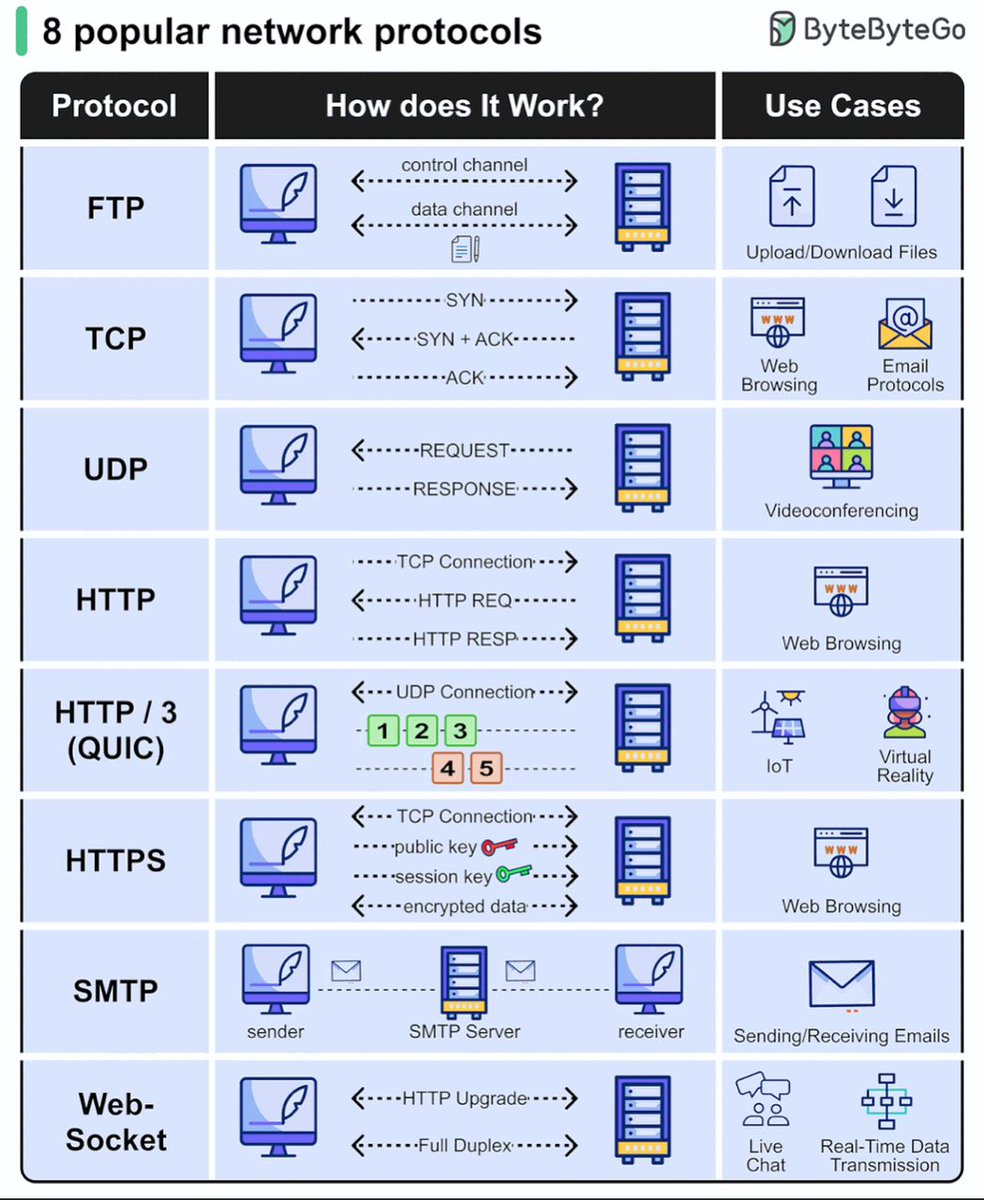
📡 How Protocols Work in Networking 📡 Every message we send online — emails, web browsing, video calls — follows a set of rules called protocols. They make sure data is organized, transmitted, and received correctly. Just like humans need a common language to communicate,…
🔌 Understanding Network Ports = Stronger Cyber Defense In cybersecurity, knowing common network ports and their associated services is fundamental. Attackers often scan these ports to find open doors, while defenders monitor them to detect anomalies. 📌 Why Ports Matter in…

United States Tendenze
- 1. #UFCQatar 42.2K posts
- 2. Harden 10K posts
- 3. Liverpool 174K posts
- 4. Newcastle 42.1K posts
- 5. Mizzou 4,014 posts
- 6. Rutgers 5,436 posts
- 7. Mateer 1,832 posts
- 8. Caden Curry N/A
- 9. Chris Paul 13.7K posts
- 10. Slot 120K posts
- 11. Harvey Barnes 3,534 posts
- 12. Ryan Day 2,325 posts
- 13. Waldo 4,323 posts
- 14. #Sooners 1,266 posts
- 15. Horiguchi 4,617 posts
- 16. Arbuckle N/A
- 17. Luke Riley 2,280 posts
- 18. Missouri 10.3K posts
- 19. #kufball N/A
- 20. Jack Hermansson N/A
Potrebbero piacerti
-
 Toyibah
Toyibah
@to_yibah -
 Hazeezah
Hazeezah
@ha_zeezah -
 mar_yam♥️
mar_yam♥️
@for_lar_khe -
 The Shoemaker❤️
The Shoemaker❤️
@wiqayatullahh -
 Zazaisapotato!
Zazaisapotato!
@Zazanotzazu -
 Dzxz
Dzxz
@CryptDris -
 Ife♡ || SOCIAL MEDIA MANAGER VIRTUAL ASSISTANT
Ife♡ || SOCIAL MEDIA MANAGER VIRTUAL ASSISTANT
@ifeeseyitan -
 Achalugo😍
Achalugo😍
@premiumbabyvibe -
 Fatiha
Fatiha
@Fatiha_Kuti -
 ABEOKUTA HAIRSTYLIST/ WIGMAKER
ABEOKUTA HAIRSTYLIST/ WIGMAKER
@_yourbeautygym -
 ❤️ Mardeeyah ❤️
❤️ Mardeeyah ❤️
@QueenDeeyah22 -
 zynah✨
zynah✨
@zynah_tomi -
 NickyGrace🖤
NickyGrace🖤
@coffeeforcomfy -
 Folu💖
Folu💖
@folu_shooo -
 El Triunfador⚽😎
El Triunfador⚽😎
@ELTRIUNFADOR17
Something went wrong.
Something went wrong.