TESSA INTERNET TACTIC📨
@INTERNETTACTIC
ACCOUNT FIX SPECIALIST | TACTICAL EXPERT IN CYBER THREAT PREVENTION | PROVIDING TRUSTED STRATEGIES IN ALL ACCESS WITH SECURE, LEGAL, AND CONFIDENTIAL METHODS.
Your digital security deserves the highest level of care. We specialize in multi account Fixing , recovery, and restoration services, ensuring discretion, speed, and reliability at every step. For priority support, contact us directly via WhatsApp: 📞 wa.me/+16815492442

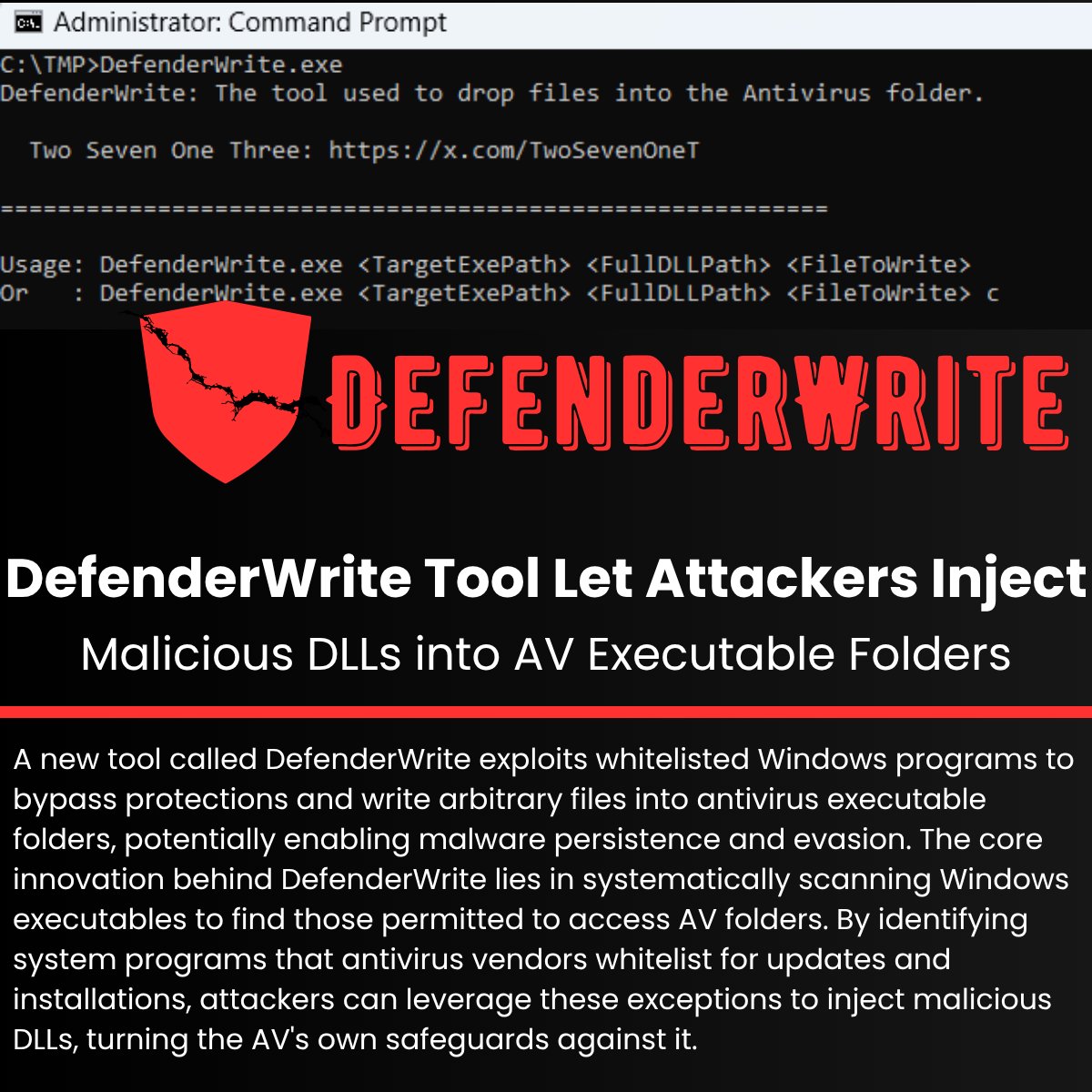
⚠️ DefenderWrite Tool Let Attackers Inject Malicious DLLs into AV Executable Folders Read more: cybersecuritynews.com/defenderwrite-… A new tool called DefenderWrite exploits whitelisted Windows programs to bypass protections and write arbitrary files into antivirus executable folders,…
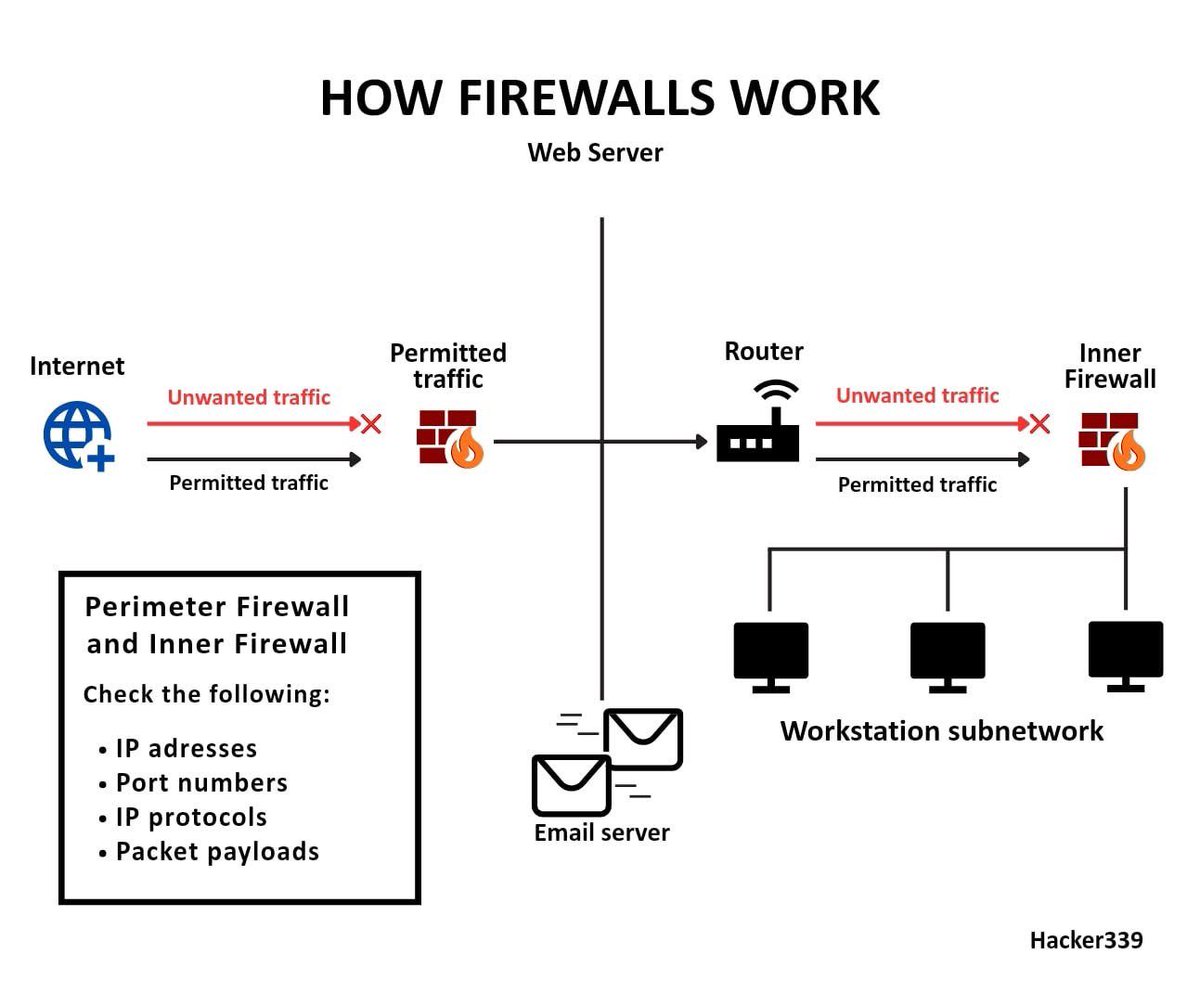
⚔️Ethical Hacking Tools by Category 🔹Wireless Network Tools 🔹Forensics Tools 🔹Exploitation Frameworks 🔹Web Application Testing Tools 🔹Network Scanning and Enumeration 🔹Vulnerability Assessment Tools




Friday night lights 🔥 Last weekend was wild at @emocarnival, Great time with my friends this one’s all about balance — chill time and a bit of grind. What’s your vibe tonight?


🔐 Windows BitLocker Vulnerabilities Let Attackers Bypass Security Feature Read more: cybersecuritynews.com/windows-bitloc… Microsoft has disclosed two critical vulnerabilities in its Windows BitLocker encryption feature, allowing attackers with physical access to bypass security…

Violation Of Community Guidelines Can't Be Kicked Out As No One Is Above Making Mistakes But @meta Appeals Should Be Able To Help Explain Why Some Guidelines were Violated. I Can Assist With; @instagram @facebook @whatsapp @snapchatsupport @google & Other Accounts Recovery. Inbox


🐉 100 Kali Linux Commands You Should Know Your go-to compact guide of Kali/Linux CLI essentials for navigating systems, managing packages, handling permissions, networking, and troubleshooting perfect for labs and hands-on learning. ⚡💻

🚨 This Week in Cyber Hell 🚨 Breaches, Deepfakes & Zero-Days 🔓 Major Breaches ⬇️

secure shell protocol over HTTP/3 with faster session setup and modern authentication

🚨 Hackers Can Inject Malicious Code into Antivirus Processes to Create a Backdoor Read more: cybersecuritynews.com/malicious-code… A new technique enables attackers to exploit antivirus software by injecting harmful code directly into the antivirus processes. This method involves cloning…

Multifactor authentication never hurts! Add an extra layer of security by enabling multi-factor authentication, and avoid the pain of a hacked account. Learn more with your #CybersecurityAwarenessMonth toolkit: hubs.la/Q03L_vNN0
United States 趨勢
- 1. Baker 32.7K posts
- 2. #WWERaw 45.5K posts
- 3. Gibbs 21K posts
- 4. Lions 81.2K posts
- 5. Mike Evans 10.3K posts
- 6. Bucs 19.4K posts
- 7. #OnePride 8,023 posts
- 8. White House 93K posts
- 9. Tez Johnson 3,118 posts
- 10. Texans 19.6K posts
- 11. Dan Campbell 2,001 posts
- 12. Goff 8,290 posts
- 13. Dragon Lee 7,097 posts
- 14. Seahawks 18.6K posts
- 15. Kelvin Sheppard N/A
- 16. #TBvsDET 5,283 posts
- 17. Jameson Williams 1,584 posts
- 18. #LaCasaDeAlofoke2 6,612 posts
- 19. Josh Naylor 3,296 posts
- 20. AJ Lee 10.5K posts
Something went wrong.
Something went wrong.