NETSCOUT
@NETSCOUT
We provide the #data that drives #observability, fortifies #cybersecurity, and keeps the world's most essential organizations resilient against disruptions.
You might like
How do you defend against threats hidden inside encrypted traffic without overwhelming your systems? The key is this: selective decryption paired with intelligent traffic analysis exposes hidden attacks without draining your capacity. That’s how you stay smart, efficient, and…

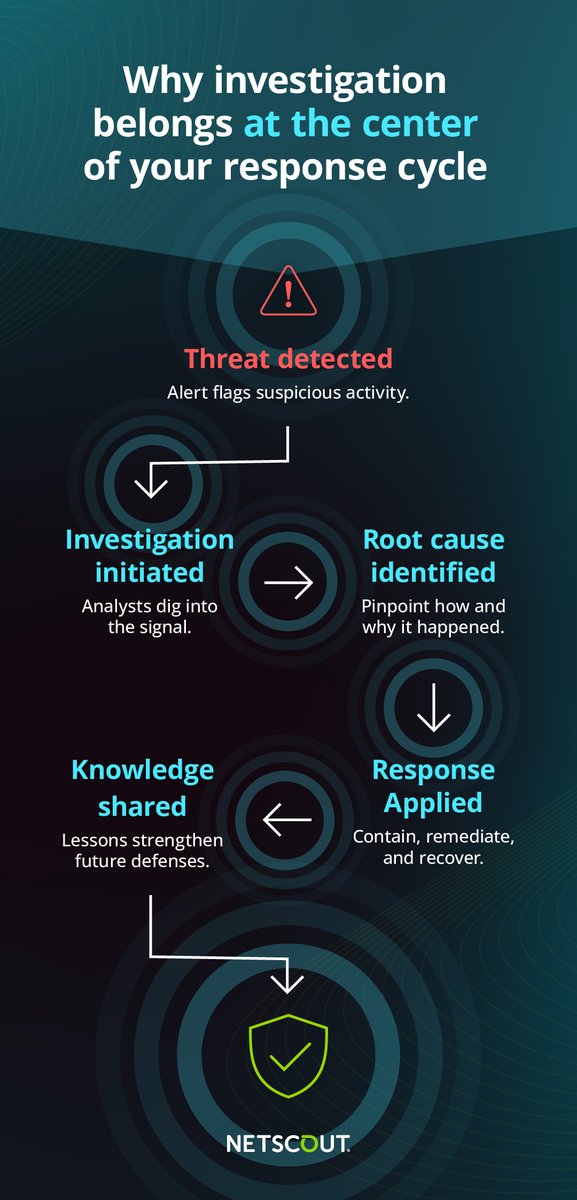
Investigation is the step most teams skip—not because it’s unimportant, but because it’s hard. Without packet-level data, root causes stay hidden, attacks repeat, and trust takes the hit. This context is everything. It transforms reactive actions into strategic decisions,…
IT disruptions are unavoidable, but the real question is whether your organization is prepared to detect, diagnose, and recover when they strike. Start strengthening your foundation by focusing on the four key actions you can take to build resilience before the next outage…

Behind every review is a person and a story that matters. When customers share how NETSCOUT helps them protect what’s essential, it’s more than technology. It’s about people, businesses, and lives connected across the globe. This season, we’re thankful for the trust of our…

Debby Briggs, VP & CISO at NETSCOUT, shares what true leadership demands today—from empathy and backbone to AI governance and mentorship. Hear her practical insights from 25+ years in cybersecurity on The True Leadership Podcast. Watch Now: netscout.link/60157SDNP

youtube.com
YouTube
Leading With Backbone and Heart: A Conversation with CISO Debby Briggs
10 p.m. The city goes dark. No traffic. No emergency response. Just chaos. You’d think it was a storm. Or a glitch. It wasn’t. It was a cyberattack—planned for months, executed in seconds. They didn’t break the system. They poisoned the data. Everything looked normal… until…

❌ Dashboards aren’t observability. ✅ Deep Packet Inspection is. Most tools give you summaries. Deep packet inspection gives you the truth about every packet, every detail, in real time. Why settle for surface-level metrics when resilience depends on depth? If you’re leading…

When it’s not making sense, bring it to us. Our deep-packet visibility tools and expertise can help you get a clearer picture. 🔎 Chat with us to learn more. netscout.link/60137oxTt

Network Time Protocol is the backbone of network timing, but attackers exploit it for DDoS amplification. A single misconfigured server can ripple into outages and security gaps. Action: ✔️ Audit your NTP settings ✔️ Monitor for anomalies ✔️ Build visibility into your defense…
🎶IT teams, this one’s for you! The holidays aren’t just about lights and laughter—they’re about keeping networks merry and bright. NETSCOUT’s Holiday Playlist is packed with tunes that speak to the heart of every IT leader juggling uptime and cheer.
From Daisies building bristle bots, to Brownies crafting art-bots, to Juniors programming Edison v2 robots, the scouts explored engineering and coding at their own level. They were especially amazed by the Stormgears robot demo 🤖✨ A huge thank you to our amazing volunteers…

More data sounds powerful until it slows you down. True visibility isn’t measured in terabytes. It’s measured in how quickly you can act with confidence. The right data at the right time changes everything.
On November 18, a Cloudflare outage disrupted major platforms, including X, ChatGPT, Spotify, and numerous others. The culprit? A configuration file used for bot management that ballooned beyond its expected size—triggering a crash in traffic-handling systems. Even trusted…
CDN-based DDoS protection is essential, but it’s not enough. Low-volume, application-layer attacks and outbound threats can bypass upstream defenses, leaving critical infrastructure exposed. Arbor Edge Defense closes those gaps with AI-driven, on-premises protection and global…

What happens when your monitoring tools miss the real problem? Downtime. Frustration. Lost trust. This customer solved that with NETSCOUT: ⭐ “NETSCOUT observability gives us the ability to see exactly what’s happening on the wire—rather than relying on internal app tools that…

United States Trends
- 1. The Quant 52.8K posts
- 2. Syria 326K posts
- 3. ISIS 40.5K posts
- 4. Go Navy 7,343 posts
- 5. #ThankYouCena 89.4K posts
- 6. #AskCena 3,230 posts
- 7. Polanco 9,572 posts
- 8. John Cena 131K posts
- 9. Villanova 1,366 posts
- 10. Trevon Brazile N/A
- 11. Toppin 1,379 posts
- 12. Dick Van Dyke 50.4K posts
- 13. #CelebrationBowl N/A
- 14. FINALLY DID IT 652K posts
- 15. SC State 1,429 posts
- 16. #SNME 32.7K posts
- 17. Barry Sanders N/A
- 18. Raphinha 36.5K posts
- 19. Cluff N/A
- 20. Rosario 16.9K posts
You might like
-
 CWNP
CWNP
@CWNP -
 BICSI
BICSI
@BICSI -
 Checkmarx
Checkmarx
@Checkmarx -
 Panduit
Panduit
@Panduit -
 RUCKUS Networks
RUCKUS Networks
@ruckusnetworks -
 F5
F5
@F5 -
 Jake Snyder
Jake Snyder
@jsnyder81 -
 Blue Planet
Blue Planet
@CienaBluePlanet -
 Tech Field Day
Tech Field Day
@TechFieldDay -
 WirelessNerd
WirelessNerd
@Wirelessnerd -
 Tom Carpenter
Tom Carpenter
@carpentertom -
 Rasika Nayanajith
Rasika Nayanajith
@mrncciew -
 Radware
Radware
@radware -
 Ben Miller
Ben Miller
@benmiller -
 Infoblox
Infoblox
@Infoblox
Something went wrong.
Something went wrong.