내가 좋아할 만한 콘텐츠
2020 saw a significant change in the cyber threat landscape. Explore 5 threat trends we believe will continue to pose a risk this year -- including ransomware & supply chain risks -- and how you can respond: pwc.to/3qRVrJn

If you're running an Exchange Server system that got xChanged in this recent mass-hack: By all means patch, get backdoors off there, but don't neglect to backup the server, email, etc & put that backup somewhere offline. The risk of ransomware groups pouncing on this is high.
No matter who you love, how you identify, or where you are in your journey – New Jersey loves you and stands with you. And, together, we’ll keep up the fight for full equality. #NationalComingOutDay

Microsoft took action against the Trickbot botnet, disrupting one of the world’s most persistent malware operations. In this blog, we detail the evolution of Trickbot, associated tactics, recent campaigns, and dive into the anatomy of a specific attack. msft.it/6019TIb4l
#Adobe is warning of a critical flaw in Flash Player for #Windows, macOS, Linux and ChromeOS. threatpost.com/flash-player-f…
threatpost.com
Critical Flash Player Flaw Opens Adobe Users to RCE
The flaw stems from a NULL Pointer Dereference error and plagues the Windows, macOS, Linux and ChromeOS versions of Adobe Flash Player.
A new info-stealing malware we first saw being sold in the cybercriminal underground in June is now actively distributed in the wild. The malware is called Anubis and uses code forked from Loki malware to steal system info, credentials, credit card details, cryptocurrency wallets



The #Google Chrome web browser has a high-severity #security flaw that could be used to execute arbitrary code. threatpost.com/google-fixes-h…
threatpost.com
Google Fixes High-Severity Chrome Browser Code Execution Bug
The high-severity flaw, which was patched in the latest version of Google's Chrome browser, could allow code execution.
And @proofpoint goes boom: proofpointcommunities.force.com/community/s/ar…
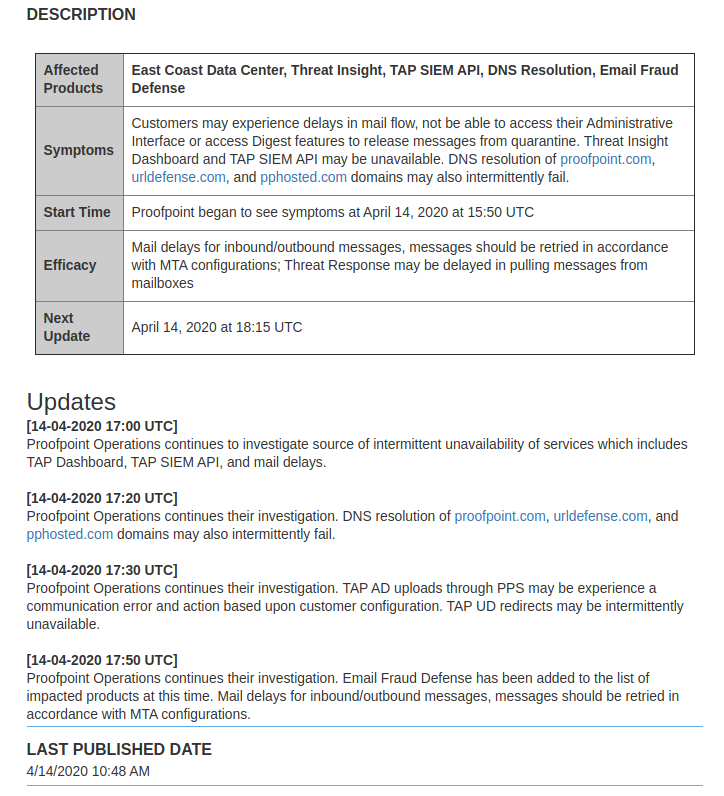
Advanced Analytics and Incident Response
lol
Locky Ransomware Campaign from August 28, 2017 which generated over 23 million emails. tinyurl.com/yby84e54
Petya ransomware successful in spreading because it combines both a client-side attack (CVE-2017-0199) and a network based threat (MS17-010)
United States 트렌드
- 1. Catherine O'Hara N/A
- 2. Don Lemon N/A
- 3. Epstein N/A
- 4. Bill Gates N/A
- 5. Home Alone N/A
- 6. Schitt's Creek N/A
- 7. FACE Act N/A
- 8. SCTV N/A
- 9. Declan Doyle N/A
- 10. Kwesi N/A
- 11. First Amendment N/A
- 12. Best in Show N/A
- 13. Beetlejuice N/A
- 14. USADF N/A
- 15. Moltbook N/A
- 16. Steve Tisch N/A
- 17. Moira Rose N/A
- 18. Grand Jury N/A
- 19. Journalists N/A
- 20. IndyCar N/A
Something went wrong.
Something went wrong.