SecAI
@SecAI_AI
Innovative threat intelligence-driven and AI-powered company aiming at cyber threat detection and response. 🏢 http://www.secai.ai 🔎 http://i.secai.ai/research
It’s going to be a packed day at @GISECGlobal with world-class sessions, but don’t miss a visit to @SecAI_AI at Booth P48. Stop by to see how our proprietary threat intelligence gives you actionable intelligence with near-zero false positives. See you there!

New #phishing assets of the #Kimsuky #APT group: #IOC: 141.164.56[.]44 taxdeliveryservice.kro[.]kr userauthoritydoc.p-e[.]kr i.secai.ai/research/141.1… i.secai.ai/research/taxde… i.secai.ai/research/usera…
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
#IOC:
141.164.56[.]44
taxdeliveryservice.kro[.]kr
userauthoritydoc.p-e[.]kr
i.secai.ai/research/141.1…
i.secai.ai/research/taxde…
i.secai.ai/research/usera…](https://pbs.twimg.com/media/GrdksSgboAALPbU.png)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
#IOC:
141.164.56[.]44
taxdeliveryservice.kro[.]kr
userauthoritydoc.p-e[.]kr
i.secai.ai/research/141.1…
i.secai.ai/research/taxde…
i.secai.ai/research/usera…](https://pbs.twimg.com/media/GrdkypkWgAA6uzB.jpg)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
#IOC:
141.164.56[.]44
taxdeliveryservice.kro[.]kr
userauthoritydoc.p-e[.]kr
i.secai.ai/research/141.1…
i.secai.ai/research/taxde…
i.secai.ai/research/usera…](https://pbs.twimg.com/media/Grdkyo5WsAAviNN.jpg)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
#IOC:
141.164.56[.]44
taxdeliveryservice.kro[.]kr
userauthoritydoc.p-e[.]kr
i.secai.ai/research/141.1…
i.secai.ai/research/taxde…
i.secai.ai/research/usera…](https://pbs.twimg.com/media/Grdky4zWgAA6DJk.png)
The #Konni #APT group used #compromised websites for command and control. #IOC: yukiicreatives[.]com rayanlynch[.]com i.secai.ai/research/yukii… i.secai.ai/research/rayan…
![SecAI_AI's tweet image. The #Konni #APT group used #compromised websites for command and control.
#IOC:
yukiicreatives[.]com
rayanlynch[.]com
i.secai.ai/research/yukii…
i.secai.ai/research/rayan…](https://pbs.twimg.com/media/GrCQFd1WkAA_GJ8.jpg)
![SecAI_AI's tweet image. The #Konni #APT group used #compromised websites for command and control.
#IOC:
yukiicreatives[.]com
rayanlynch[.]com
i.secai.ai/research/yukii…
i.secai.ai/research/rayan…](https://pbs.twimg.com/media/GrCQFd3XsAA9wXj.jpg)
![SecAI_AI's tweet image. The #Konni #APT group used #compromised websites for command and control.
#IOC:
yukiicreatives[.]com
rayanlynch[.]com
i.secai.ai/research/yukii…
i.secai.ai/research/rayan…](https://pbs.twimg.com/media/GrCQFd3W0AAhUgb.jpg)
![SecAI_AI's tweet image. The #Konni #APT group used #compromised websites for command and control.
#IOC:
yukiicreatives[.]com
rayanlynch[.]com
i.secai.ai/research/yukii…
i.secai.ai/research/rayan…](https://pbs.twimg.com/media/GrCQFd3WwAASWQo.jpg)
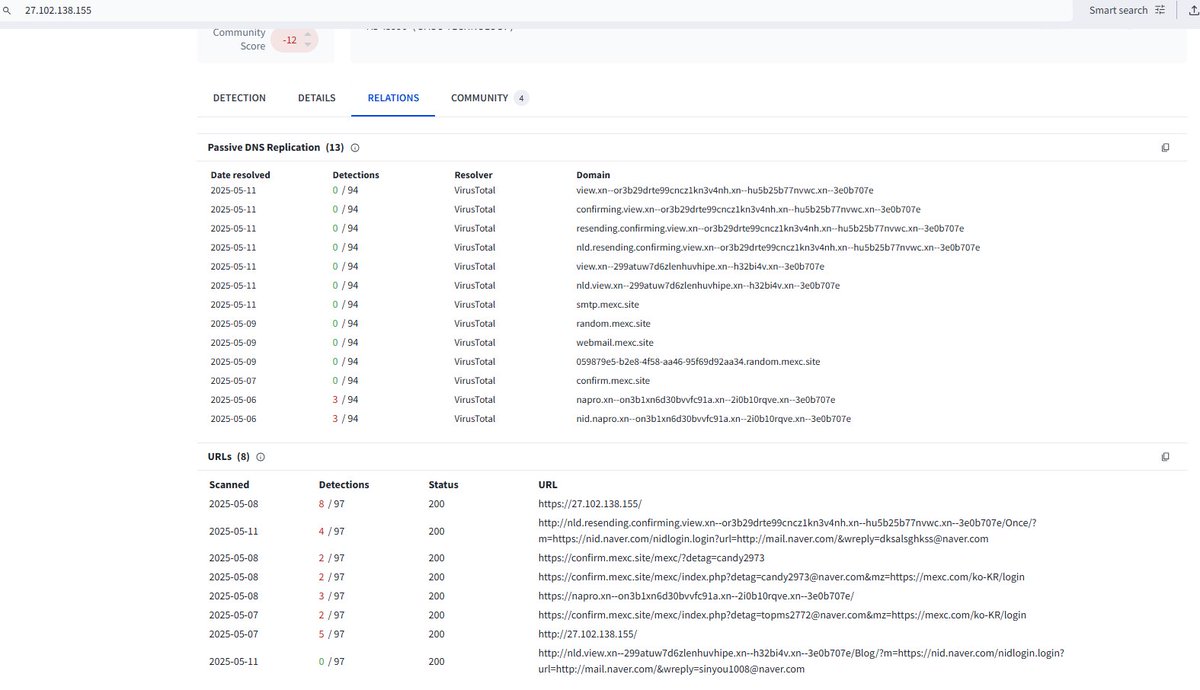
The #Kimsuky #APT group conducted #phishing using a Korean domain that means "Ministry of the Interior and Safety notification." #IOC: 27.102.138.155 행정안전부통지서.홈페이지.한국 블로그신고안내.메인.한국 i.secai.ai/research/27.10… i.secai.ai/research/xn--o… i.secai.ai/research/xn--2…



The #Konni #APT group used #compromised websites to deliver information. #IOC: bergaeroworks[.]co[.]za sitisrlweb[.]com seacura[.]com i.secai.ai/research/berga… i.secai.ai/research/sitis… i.secai.ai/research/seacu…
![SecAI_AI's tweet image. The #Konni #APT group used #compromised websites to deliver information.
#IOC:
bergaeroworks[.]co[.]za
sitisrlweb[.]com
seacura[.]com
i.secai.ai/research/berga…
i.secai.ai/research/sitis…
i.secai.ai/research/seacu…](https://pbs.twimg.com/media/Gqa5pUmWEAA_ul7.png)
![SecAI_AI's tweet image. The #Konni #APT group used #compromised websites to deliver information.
#IOC:
bergaeroworks[.]co[.]za
sitisrlweb[.]com
seacura[.]com
i.secai.ai/research/berga…
i.secai.ai/research/sitis…
i.secai.ai/research/seacu…](https://pbs.twimg.com/media/Gqa5rnZXQAAtusF.jpg)
![SecAI_AI's tweet image. The #Konni #APT group used #compromised websites to deliver information.
#IOC:
bergaeroworks[.]co[.]za
sitisrlweb[.]com
seacura[.]com
i.secai.ai/research/berga…
i.secai.ai/research/sitis…
i.secai.ai/research/seacu…](https://pbs.twimg.com/media/Gqa5rxIWMAApT9W.jpg)
![SecAI_AI's tweet image. The #Konni #APT group used #compromised websites to deliver information.
#IOC:
bergaeroworks[.]co[.]za
sitisrlweb[.]com
seacura[.]com
i.secai.ai/research/berga…
i.secai.ai/research/sitis…
i.secai.ai/research/seacu…](https://pbs.twimg.com/media/Gqa5rxPXkAAR_0w.jpg)
Last chance to meet us at @GISECGlobal! The @SecAI_AI Booth at P48 is open for one more day. Find out how AI-powered threat intelligence can give your security team a critical edge. See you there!

The #Kimsuky #APT group used the #BabyShark trojan to connect to its C2 server via a revoked TLS certificate. #sha256: 8503a57fa9e3424cc1cb39f8cd15419840eaa73277e9fe383a1bebb518ef9ede(RemoteControl.dll) #C2: first.pokerstarus.kro[.]kr i.secai.ai/research/poker… Domain resolved to IP…
![SecAI_AI's tweet image. The #Kimsuky #APT group used the #BabyShark trojan to connect to its C2 server via a revoked TLS certificate.
#sha256: 8503a57fa9e3424cc1cb39f8cd15419840eaa73277e9fe383a1bebb518ef9ede(RemoteControl.dll)
#C2: first.pokerstarus.kro[.]kr
i.secai.ai/research/poker…
Domain resolved to IP…](https://pbs.twimg.com/media/GqVn_owbcAA-Q3B.jpg)
![SecAI_AI's tweet image. The #Kimsuky #APT group used the #BabyShark trojan to connect to its C2 server via a revoked TLS certificate.
#sha256: 8503a57fa9e3424cc1cb39f8cd15419840eaa73277e9fe383a1bebb518ef9ede(RemoteControl.dll)
#C2: first.pokerstarus.kro[.]kr
i.secai.ai/research/poker…
Domain resolved to IP…](https://pbs.twimg.com/media/GqVn_pOaAAAR8Rz.jpg)
![SecAI_AI's tweet image. The #Kimsuky #APT group used the #BabyShark trojan to connect to its C2 server via a revoked TLS certificate.
#sha256: 8503a57fa9e3424cc1cb39f8cd15419840eaa73277e9fe383a1bebb518ef9ede(RemoteControl.dll)
#C2: first.pokerstarus.kro[.]kr
i.secai.ai/research/poker…
Domain resolved to IP…](https://pbs.twimg.com/media/GqVn_ovbIAAs8EH.png)
![SecAI_AI's tweet image. The #Kimsuky #APT group used the #BabyShark trojan to connect to its C2 server via a revoked TLS certificate.
#sha256: 8503a57fa9e3424cc1cb39f8cd15419840eaa73277e9fe383a1bebb518ef9ede(RemoteControl.dll)
#C2: first.pokerstarus.kro[.]kr
i.secai.ai/research/poker…
Domain resolved to IP…](https://pbs.twimg.com/media/GqVn_osbIAAHJ-s.jpg)
Day 2 at @GISECGlobal! Stop by Booth P48 to see why @SecAI_AI Investigator is making waves in Threat Intel. We're giving away 15-day Pro access codes—grab yours and see the power for yourself.
The #Konni #APT group used the #compromised site to download files. #IOC: deliberatecollaboration[.]com i.secai.ai/research/delib…
![SecAI_AI's tweet image. The #Konni #APT group used the #compromised site to download files.
#IOC: deliberatecollaboration[.]com
i.secai.ai/research/delib…](https://pbs.twimg.com/media/GqUD-WJbcAAek43.jpg)
![SecAI_AI's tweet image. The #Konni #APT group used the #compromised site to download files.
#IOC: deliberatecollaboration[.]com
i.secai.ai/research/delib…](https://pbs.twimg.com/media/GqUD-WKbAAIaY3y.png)
Just 1 more day to @GISECGlobal! Come find @SecAI_AI at Booth P48 to have an hands-on experience of faster, smarter threat investigations powered by AI. Plus, try your luck at our onsite Lucky Draw! 🎁 See you then!

New #phishing assets of #Kimsuky #APT group: 158.247.247[.]157 i.secai.ai/research/158.2… mexc-signin.kro[.]kr i.secai.ai/research/mexc-… yourinfo.kro[.]kr i.secai.ai/research/youri… 141.164.53[.]3 i.secai.ai/research/141.1… userdoc-sign.kro[.]kr i.secai.ai/research/userd……
![SecAI_AI's tweet image. New #phishing assets of #Kimsuky #APT group:
158.247.247[.]157
i.secai.ai/research/158.2…
mexc-signin.kro[.]kr
i.secai.ai/research/mexc-…
yourinfo.kro[.]kr
i.secai.ai/research/youri…
141.164.53[.]3
i.secai.ai/research/141.1…
userdoc-sign.kro[.]kr
i.secai.ai/research/userd……](https://pbs.twimg.com/media/GpuxBGCbsAAOsVs.jpg)
![SecAI_AI's tweet image. New #phishing assets of #Kimsuky #APT group:
158.247.247[.]157
i.secai.ai/research/158.2…
mexc-signin.kro[.]kr
i.secai.ai/research/mexc-…
yourinfo.kro[.]kr
i.secai.ai/research/youri…
141.164.53[.]3
i.secai.ai/research/141.1…
userdoc-sign.kro[.]kr
i.secai.ai/research/userd……](https://pbs.twimg.com/media/GpuxBFGaYAIKFdj.jpg)
![SecAI_AI's tweet image. New #phishing assets of #Kimsuky #APT group:
158.247.247[.]157
i.secai.ai/research/158.2…
mexc-signin.kro[.]kr
i.secai.ai/research/mexc-…
yourinfo.kro[.]kr
i.secai.ai/research/youri…
141.164.53[.]3
i.secai.ai/research/141.1…
userdoc-sign.kro[.]kr
i.secai.ai/research/userd……](https://pbs.twimg.com/media/GpuxBF7aEAADcWr.jpg)
![SecAI_AI's tweet image. New #phishing assets of #Kimsuky #APT group:
158.247.247[.]157
i.secai.ai/research/158.2…
mexc-signin.kro[.]kr
i.secai.ai/research/mexc-…
yourinfo.kro[.]kr
i.secai.ai/research/youri…
141.164.53[.]3
i.secai.ai/research/141.1…
userdoc-sign.kro[.]kr
i.secai.ai/research/userd……](https://pbs.twimg.com/media/GpuxCPgaEAAF54i.png)
The #Konni #APT group uses the #compromised site holosformations[.]fr to download files. C2: 49.12.47[.]155:443 i.secai.ai/research/holos… i.secai.ai/research/49.12… Hash: 869705fd4dd777d4ab5c662806b42fe43bff6b58e085a64804486326b35fee47 It is related to #ChatGPT, uses an #AutoIt…
![SecAI_AI's tweet image. The #Konni #APT group uses the #compromised site holosformations[.]fr to download files.
C2: 49.12.47[.]155:443
i.secai.ai/research/holos…
i.secai.ai/research/49.12…
Hash: 869705fd4dd777d4ab5c662806b42fe43bff6b58e085a64804486326b35fee47
It is related to #ChatGPT, uses an #AutoIt…](https://pbs.twimg.com/media/GpSrSRiaAAAeA-h.png)
![SecAI_AI's tweet image. The #Konni #APT group uses the #compromised site holosformations[.]fr to download files.
C2: 49.12.47[.]155:443
i.secai.ai/research/holos…
i.secai.ai/research/49.12…
Hash: 869705fd4dd777d4ab5c662806b42fe43bff6b58e085a64804486326b35fee47
It is related to #ChatGPT, uses an #AutoIt…](https://pbs.twimg.com/media/GpSrSRhbYAgpNLk.png)
![SecAI_AI's tweet image. The #Konni #APT group uses the #compromised site holosformations[.]fr to download files.
C2: 49.12.47[.]155:443
i.secai.ai/research/holos…
i.secai.ai/research/49.12…
Hash: 869705fd4dd777d4ab5c662806b42fe43bff6b58e085a64804486326b35fee47
It is related to #ChatGPT, uses an #AutoIt…](https://pbs.twimg.com/media/GpSrSRibYAAVtvM.png)
![SecAI_AI's tweet image. The #Konni #APT group uses the #compromised site holosformations[.]fr to download files.
C2: 49.12.47[.]155:443
i.secai.ai/research/holos…
i.secai.ai/research/49.12…
Hash: 869705fd4dd777d4ab5c662806b42fe43bff6b58e085a64804486326b35fee47
It is related to #ChatGPT, uses an #AutoIt…](https://pbs.twimg.com/media/GpSrSRobYAE2165.png)
New #phishing assets of the #Kimsuky #APT group: 210.114.14.234 i.secai.ai/research/210.1… secinput.n-e[.]kr i.secai.ai/research/secin… secuinput.r-e[.]kr i.secai.ai/research/secui… secinput.o-r[.]kr i.secai.ai/research/secin… 158.247.243.223 i.secai.ai/research/158.2… updateinfo.r-e[.]kr…
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
210.114.14.234
i.secai.ai/research/210.1…
secinput.n-e[.]kr
i.secai.ai/research/secin…
secuinput.r-e[.]kr
i.secai.ai/research/secui…
secinput.o-r[.]kr
i.secai.ai/research/secin…
158.247.243.223
i.secai.ai/research/158.2…
updateinfo.r-e[.]kr…](https://pbs.twimg.com/media/GpI0YbFWkAAWhX_.jpg)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
210.114.14.234
i.secai.ai/research/210.1…
secinput.n-e[.]kr
i.secai.ai/research/secin…
secuinput.r-e[.]kr
i.secai.ai/research/secui…
secinput.o-r[.]kr
i.secai.ai/research/secin…
158.247.243.223
i.secai.ai/research/158.2…
updateinfo.r-e[.]kr…](https://pbs.twimg.com/media/GpI0YbEWcAAcQce.png)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
210.114.14.234
i.secai.ai/research/210.1…
secinput.n-e[.]kr
i.secai.ai/research/secin…
secuinput.r-e[.]kr
i.secai.ai/research/secui…
secinput.o-r[.]kr
i.secai.ai/research/secin…
158.247.243.223
i.secai.ai/research/158.2…
updateinfo.r-e[.]kr…](https://pbs.twimg.com/media/GpI0ZMjWsAAKHS4.jpg)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
210.114.14.234
i.secai.ai/research/210.1…
secinput.n-e[.]kr
i.secai.ai/research/secin…
secuinput.r-e[.]kr
i.secai.ai/research/secui…
secinput.o-r[.]kr
i.secai.ai/research/secin…
158.247.243.223
i.secai.ai/research/158.2…
updateinfo.r-e[.]kr…](https://pbs.twimg.com/media/GpI0ZM3XgAE-c5E.jpg)
Recently, the #Konni #APT group has used a large number of #compromised websites to transmit information of infected hosts. ausbildungsbuddy[.]de i.secai.ai/research/ausbi……absongkhla[.]com i.secai.ai/research/abson… beldy[.]ma i.secai.ai/research/beldy… go2kgstan[.]com…
![SecAI_AI's tweet image. Recently, the #Konni #APT group has used a large number of #compromised websites to transmit information of infected hosts.
ausbildungsbuddy[.]de i.secai.ai/research/ausbi……absongkhla[.]com i.secai.ai/research/abson…
beldy[.]ma
i.secai.ai/research/beldy…
go2kgstan[.]com…](https://pbs.twimg.com/media/GoujmwuaYAASNgF.png)
![SecAI_AI's tweet image. Recently, the #Konni #APT group has used a large number of #compromised websites to transmit information of infected hosts.
ausbildungsbuddy[.]de i.secai.ai/research/ausbi……absongkhla[.]com i.secai.ai/research/abson…
beldy[.]ma
i.secai.ai/research/beldy…
go2kgstan[.]com…](https://pbs.twimg.com/media/GoujnyDa8AAb0NF.jpg)
![SecAI_AI's tweet image. Recently, the #Konni #APT group has used a large number of #compromised websites to transmit information of infected hosts.
ausbildungsbuddy[.]de i.secai.ai/research/ausbi……absongkhla[.]com i.secai.ai/research/abson…
beldy[.]ma
i.secai.ai/research/beldy…
go2kgstan[.]com…](https://pbs.twimg.com/media/GoujnyKbkAAsQiD.jpg)
![SecAI_AI's tweet image. Recently, the #Konni #APT group has used a large number of #compromised websites to transmit information of infected hosts.
ausbildungsbuddy[.]de i.secai.ai/research/ausbi……absongkhla[.]com i.secai.ai/research/abson…
beldy[.]ma
i.secai.ai/research/beldy…
go2kgstan[.]com…](https://pbs.twimg.com/media/GoujnyQbMAExpwn.jpg)
New #phishing assets of the #Kimsuky #APT group: #IOC: 158.247.202[.]109 portiondoc.o-r[.]kr i.secai.ai/research/158.2… i.secai.ai/research/porti…
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group: #IOC:
158.247.202[.]109
portiondoc.o-r[.]kr
i.secai.ai/research/158.2…
i.secai.ai/research/porti…](https://pbs.twimg.com/media/Gok55LGWwAAStQn.jpg)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group: #IOC:
158.247.202[.]109
portiondoc.o-r[.]kr
i.secai.ai/research/158.2…
i.secai.ai/research/porti…](https://pbs.twimg.com/media/Gok55KfXAAAxEPz.jpg)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group: #IOC:
158.247.202[.]109
portiondoc.o-r[.]kr
i.secai.ai/research/158.2…
i.secai.ai/research/porti…](https://pbs.twimg.com/media/Gok58WYWAAAmcNB.jpg)
🚀 The new version of SecAI is live! We’ve made major upgrades to help you analyze IPs and domains more effectively: ✅ Clear Verdicts – Malicious, Suspicious, Unknown, or Benign — based on multi-source intelligence 🏷️ Multi-layered Labels – Threat types, malware linkage,…


Looking forward to @RSAConference 2025? Stop by booth #Booth N-6570 to meet our team and check out our TI-enriched and AI-driven cybersecurity solutions. You're just one step away from levelling up your security operation. If you don't have a pass. Don't worry! Here is the…

New #phishing assets of the #Kimsuky #APT group: #IOC: 158.247.192[.]105 ips-check.o-r[.]kr i.secai.ai/research/158.2… i.secai.ai/research/ips-c…
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
#IOC:
158.247.192[.]105
ips-check.o-r[.]kr
i.secai.ai/research/158.2…
i.secai.ai/research/ips-c…](https://pbs.twimg.com/media/GoGBSGfbcAAWCmv.png)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
#IOC:
158.247.192[.]105
ips-check.o-r[.]kr
i.secai.ai/research/158.2…
i.secai.ai/research/ips-c…](https://pbs.twimg.com/media/GoGBSGfbwAArqbr.png)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
#IOC:
158.247.192[.]105
ips-check.o-r[.]kr
i.secai.ai/research/158.2…
i.secai.ai/research/ips-c…](https://pbs.twimg.com/media/GoGBfCibwAAIcip.jpg)
![SecAI_AI's tweet image. New #phishing assets of the #Kimsuky #APT group:
#IOC:
158.247.192[.]105
ips-check.o-r[.]kr
i.secai.ai/research/158.2…
i.secai.ai/research/ips-c…](https://pbs.twimg.com/media/GoGBfCdacAANqiB.jpg)
The #Kimsuky #APT group also registered other #phishing assets. #IOC: 158.247.242[.]169 i.secai.ai/research/158.2…
![SecAI_AI's tweet image. The #Kimsuky #APT group also registered other #phishing assets.
#IOC: 158.247.242[.]169
i.secai.ai/research/158.2…](https://pbs.twimg.com/media/GnlJ2ppboAA8054.jpg)
![SecAI_AI's tweet image. The #Kimsuky #APT group also registered other #phishing assets.
#IOC: 158.247.242[.]169
i.secai.ai/research/158.2…](https://pbs.twimg.com/media/GnlJ2pmaMAAnUve.jpg)
The #Kimsuky #APT group used phishing sites to collect account credentials, but the sites has not been resolved to any IP addresses. #IOC: post.blogalarm.kro[.]kr nid-info.checkmyblog.kro[.]kr i.secai.ai/research/bloga… i.secai.ai/research/check…
![SecAI_AI's tweet image. The #Kimsuky #APT group used phishing sites to collect account credentials, but the sites has not been resolved to any IP addresses.
#IOC:
post.blogalarm.kro[.]kr
nid-info.checkmyblog.kro[.]kr
i.secai.ai/research/bloga…
i.secai.ai/research/check…](https://pbs.twimg.com/media/GndX6eIbAAAPFlM.jpg)
![SecAI_AI's tweet image. The #Kimsuky #APT group used phishing sites to collect account credentials, but the sites has not been resolved to any IP addresses.
#IOC:
post.blogalarm.kro[.]kr
nid-info.checkmyblog.kro[.]kr
i.secai.ai/research/bloga…
i.secai.ai/research/check…](https://pbs.twimg.com/media/GndX7epbUAAWx6V.jpg)
![SecAI_AI's tweet image. The #Kimsuky #APT group used phishing sites to collect account credentials, but the sites has not been resolved to any IP addresses.
#IOC:
post.blogalarm.kro[.]kr
nid-info.checkmyblog.kro[.]kr
i.secai.ai/research/bloga…
i.secai.ai/research/check…](https://pbs.twimg.com/media/GndX7eqbwAA1gGN.jpg)
The #Kimsuky #APT group used phishing sites to collect account credentials, but the sites has not been resolved to any IP addresses. #IOC: post.blogalarm.kro[.]kr nid-info.checkmyblog.kro[.]kr i.secai.ai/research/bloga… i.secai.ai/research/check…
![SecAI_AI's tweet image. The #Kimsuky #APT group used phishing sites to collect account credentials, but the sites has not been resolved to any IP addresses.
#IOC:
post.blogalarm.kro[.]kr
nid-info.checkmyblog.kro[.]kr
i.secai.ai/research/bloga…
i.secai.ai/research/check…](https://pbs.twimg.com/media/GndX6eIbAAAPFlM.jpg)
![SecAI_AI's tweet image. The #Kimsuky #APT group used phishing sites to collect account credentials, but the sites has not been resolved to any IP addresses.
#IOC:
post.blogalarm.kro[.]kr
nid-info.checkmyblog.kro[.]kr
i.secai.ai/research/bloga…
i.secai.ai/research/check…](https://pbs.twimg.com/media/GndX7epbUAAWx6V.jpg)
![SecAI_AI's tweet image. The #Kimsuky #APT group used phishing sites to collect account credentials, but the sites has not been resolved to any IP addresses.
#IOC:
post.blogalarm.kro[.]kr
nid-info.checkmyblog.kro[.]kr
i.secai.ai/research/bloga…
i.secai.ai/research/check…](https://pbs.twimg.com/media/GndX7eqbwAA1gGN.jpg)
United States Trends
- 1. Veterans Day 54.1K posts
- 2. Good Tuesday 26.8K posts
- 3. SoftBank 6,954 posts
- 4. United States Armed Forces N/A
- 5. #tuesdayvibe 1,500 posts
- 6. Armistice Day 9,750 posts
- 7. #Talus_Labs N/A
- 8. Bond 60.5K posts
- 9. Vets 12.7K posts
- 10. Islamabad 36.1K posts
- 11. World War 39.3K posts
- 12. 600,000 Chinese 9,422 posts
- 13. Benítez 15K posts
- 14. JOONGDUNK BRIGHT SKIN 322K posts
- 15. Allora 32.7K posts
- 16. 600k Chinese 5,357 posts
- 17. Jordan Love 16K posts
- 18. Berkeley 88.7K posts
- 19. #Army 1,512 posts
- 20. Window 53.6K posts
Something went wrong.
Something went wrong.