おすすめツイート
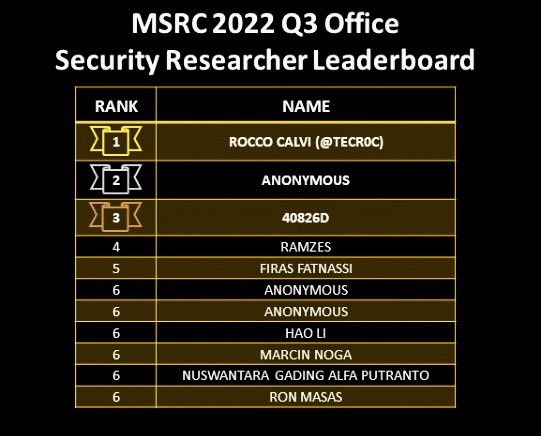
Achieved top position on MSRC Q3 Office Security Researcher Leaderboard ;-D congrats to all the outstanding researchers recognised in this quarter! Thanks @msftsecresponse 🙏🏼
Dataflow Security has officially opened a position for a Web Security Researcher. dfsec.com/careers/
Apparently @offensive_con worked their asses off to get their talks up on YouTube Go check them out And here's the coolest talk, my talk: youtu.be/LAIr2laU-So?si… And with that, the full chain used to exploit the S24 is released. Yay!

youtube.com
YouTube
OffensiveCon25 - Ken Gannon- Chainspotting 2: The Unofficial Sequel...
Vulnerability research is a marathon, not a sprint. Many start out strong but can't keep up the motivation when the going gets tough and the bugs are not flowing. Don't rush it. Be consistent. Keep your pace. You'll get there.
Excited to be back at POC by @POC_Crew in South Korea 🇰🇷 ! Looking forward to reconnecting with old friends and meeting new faces in the industry #POC2024

I've written a post on SELinux and some public bypasses for Android kernel exploitation. It's especially relevant for Samsung and Huawei devices due to their use of hypervisors. Check it out here: klecko.github.io/posts/selinux-…
We at @dfsec_com are currently looking for a senior Linux kernel researcher, feel free to DM if you’re curious :)
The time has come, and with it your reading material for the week. Phrack #71 is officially released ONLINE! Let us know what you think! phrack.org/issues/71/1.ht…

Just arrived at @defcon If you're around and want to meet up, hit me up. Would love to connect with some fellow hackers 🏴☠️

Excited to be at #BHUSA and #DEFCON! Looking to connect with top vulnerability researchers who are passionate about bug hunting. DM me if you’re around!

You Can't Spell WebRTC without RCE - Part 2 blog post, which turns the vulnerabilities we injected in Part 1 into remote code execution on iOS 16.4! Follow along with @__comedian to learn more about the iOS shared cache, Corellium, and ROP in ARM64! margin.re/2024/07/you-ca…
My new Project Zero blog post, Driving Forward in Android Drivers is live! 🥳 googleprojectzero.blogspot.com/2024/06/drivin…
Love the story @Laughing_Mantis! Bug hunting truly is a roller coaster, and your tweet captures exactly why it’s so much fun! It’s also a great reminder that persistence is key in this work :-D
Since I'm 6 drinks in for 20 bucks, let me tell you all about the story of how the first Microsoft Office 2007 vulnerability was discovered, or how it wasn't. This was a story I was gonna save for a book but fuck it, I ain't gonna write it anyways.
Thanks to events like Pwn2Own or our V8CTF (~= exploit bounty program), we now have more data about the types of bugs exploited in V8. Based on that, we've gathered some basic statistics: docs.google.com/document/d/1nj…
The libarchive e8 vulnerability is actually really cool, but the ZDI advisory doesn't explain why it's so wild lol. For some reason, I know about RAR filters, so let me provide the background. 🧵 1/n
PHP just fixed one of my RCE vulnerabilities, which affects XAMPP by default. Check to see if you are affected and update now! 🔥 blog.orange.tw/2024/06/cve-20…
#OffensiveCon24 videos are now up! youtube.com/playlist?list=…
United States トレンド
- 1. #AEWDynamite 18.4K posts
- 2. Giannis 76K posts
- 3. #Survivor49 2,324 posts
- 4. Claudio 28.1K posts
- 5. Jamal Murray 4,577 posts
- 6. #TheChallenge41 1,725 posts
- 7. #SistasOnBET 1,875 posts
- 8. Kevin Overton N/A
- 9. Ryan Nembhard 2,728 posts
- 10. Achilles 5,036 posts
- 11. Will Wade N/A
- 12. #iubb 1,175 posts
- 13. Bucks 50.2K posts
- 14. Jericho Sims N/A
- 15. Kevin Knight 1,894 posts
- 16. Tyler Herro 1,624 posts
- 17. Steve Cropper 4,149 posts
- 18. Dark Order 1,629 posts
- 19. Yeremi N/A
- 20. Wiggins 4,696 posts
おすすめツイート
-
 Interrupt Labs
Interrupt Labs
@InterruptLabs -
 starlabs
starlabs
@starlabs_sg -
 Jordy Zomer
Jordy Zomer
@pwningsystems -
 Flashback Team
Flashback Team
@FlashbackPwn -
 sakura
sakura
@eternalsakura13 -
 Orange Tsai 🍊
Orange Tsai 🍊
@orange_8361 -
 [email protected]
[email protected]
@0xdea -
 Bien 🇻🇳
Bien 🇻🇳
@bienpnn -
 SinSinology
SinSinology
@SinSinology -
 Dohyun Lee
Dohyun Lee
@l33d0hyun -
 reverseame
reverseame
@reverseame -
 Samuel Groß
Samuel Groß
@5aelo -
 Alex Plaskett
Alex Plaskett
@alexjplaskett -
 kmkz
kmkz
@kmkz_security -
 kylebot
kylebot
@ky1ebot
Something went wrong.
Something went wrong.