#Linux File System
Linux file system explained. The Linux file system used to resemble an unorganized town where individuals constructed their houses wherever they pleased. However, in 1994, the Filesystem Hierarchy Standard (FHS) was introduced to bring order to the Linux file system. By…
#API Security 🚀🚀🚀
Top 12 Tips for API Security - Use HTTPS - Use OAuth2 - Use WebAuthn - Use Leveled API Keys - Authorization - Rate Limiting - API Versioning - Whitelisting - Check OWASP API Security Risks - Use API Gateway - Error Handling - Input Validation – Subscribe to our weekly…
Top 5 Kafka use cases Kafka was originally built for massive log processing. It retains messages until expiration and lets consumers pull messages at their own pace. Let’s review the popular Kafka use cases. - Log processing and analysis - Data streaming in recommendations -…
Instagram System Design Overview - Clients (iOS, Android, Web). - Microservices for varied functionalities. - Databases: MySQL, Cassandra, Redis. - Object storage (Amazon S3) & CDN for media. - Caching with Memcached/Redis - Scaling, load balancing, auto-scaling. - Asynchronous…
#ACID in Database
The acronym ACID in the context of DB transactions stands for Atomicity, Consistency, Isolation, and Durability. This post is going to make each term crystal clear. ✅Atomicity (A) Atomic means something that cannot be broken down. It’s the same thing that our Physics…
Caching 101: The Must-Know Caching Strategies Fetching data is slow. Caching speeds things up by storing frequently accessed data for quick reads. But how do you populate and update the cache? That's where strategies come in. 🔍 Read Strategies: Cache Aside (Lazy Loading) -…

#Kubernetes Service Types
Top 4 Kubernetes Service Types in one diagram. The diagram below shows 4 ways to expose a Service. In Kubernetes, a Service is a method for exposing a network application in the cluster. We use a Service to make that set of Pods available on the network so that users can…

Data Pipelines Overview. The method to download the GIF is available at the end. Data pipelines are a fundamental component of managing and processing data efficiently within modern systems. These pipelines typically encompass 5 predominant phases: Collect, Ingest, Store,…
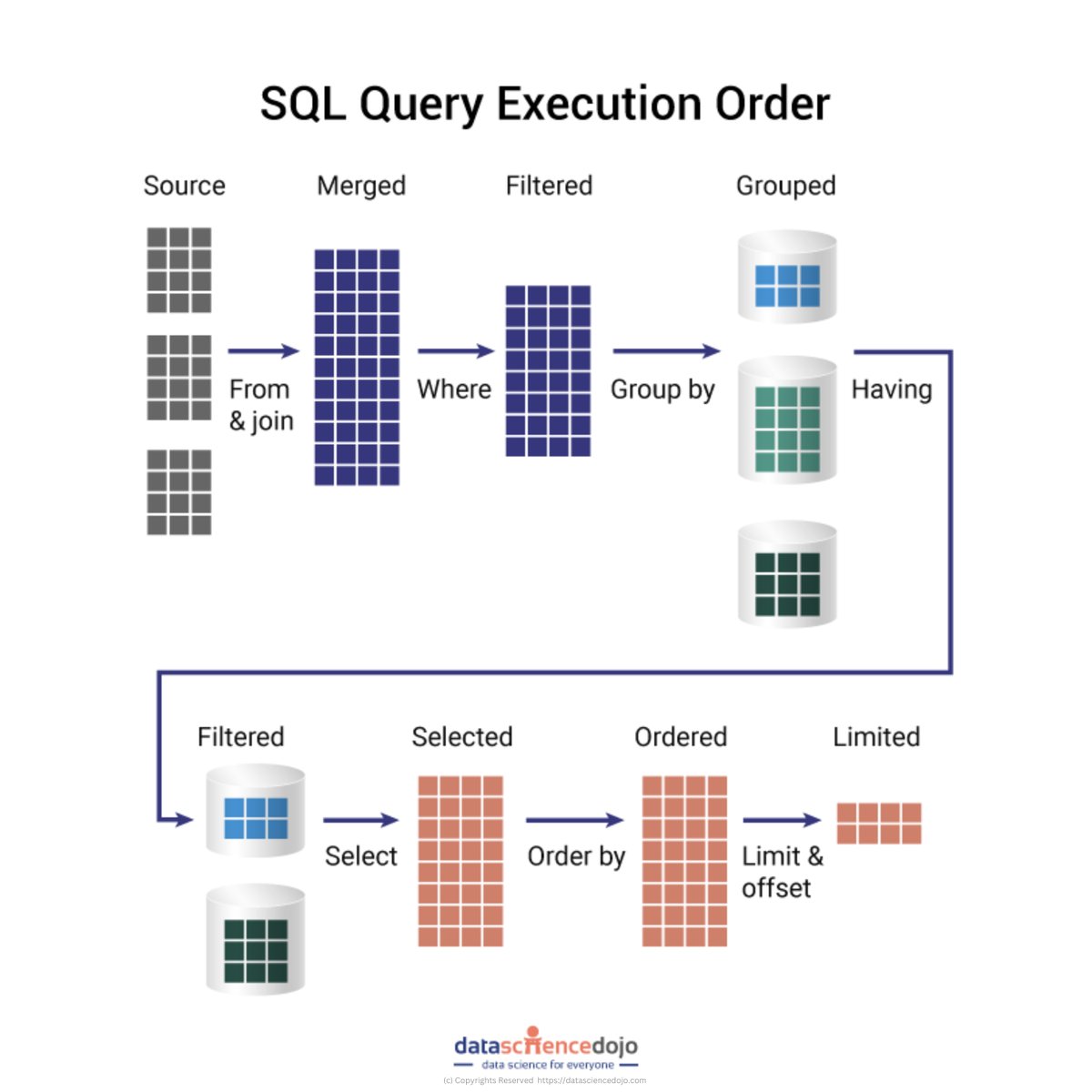
#SQL Query Execution
GraphQL Explained GraphSQL is a query language for databases that leverages the power of graph structures. 📊 It's all about relationships, making complex data queries a breeze. GraphQL itself is not tied to a specific transport protocol like HTTP. It's a query language and…
𝗛𝗼𝘄 𝗚𝗜𝗧 𝗪𝗼𝗿𝗸𝘀 Git is a distributed version control tool that facilitates monitoring changes made to your code over time. Git makes it simple to track changes to your codebase and collaborate on projects with others. It was authored by Linus Torvalds in 2005 for…

Authentication in REST APIs acts as the crucial gateway, ensuring that solely authorized users or applications gain access to the API's resources. Some popular authentication methods for REST APIs include: 1. Basic Authentication: Involves sending a username and password with…
#Docker Containers >Docker Containers contain binaries, libraries & configuration files along with the application itself They don’t contain a guest OS which makes the containers lightweight #JavaProgramming #Java #InterviewQuestions #100daysofcoding #Coding
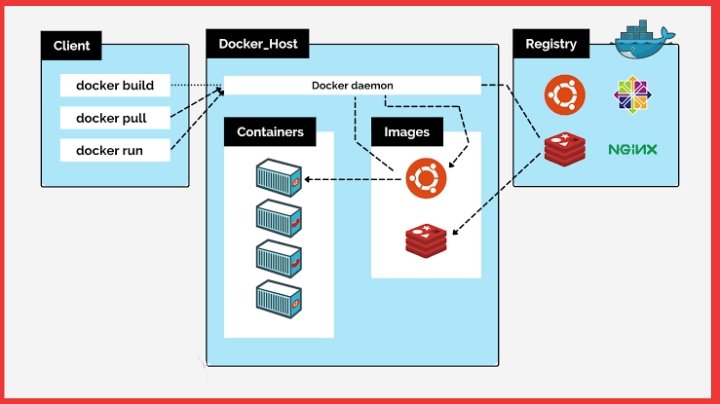
#Docker Docker uses virtualization to deliver software in packages called containers #Containers are isolated from one another and bundle their own software, libraries & configuration files #JavaProgramming #Java #InterviewQuestions #100daysofcoding #Coding

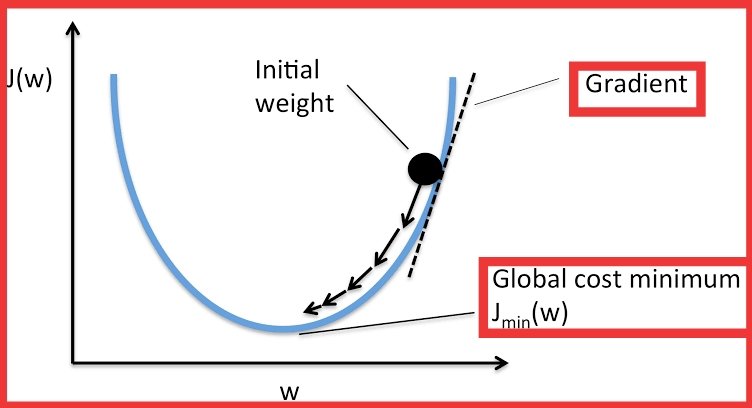
#GradientDescent >Used in machine learning to minimize a cost function >Algorithm is run with training data & errors on the predictions are used to update the parameters #MachineLearning #AI #JavaProgramming #Java #Python #NeuralNetworks #100daysofcoding #Coding
#SQL Joins >Inner Join >Left Outer Join >Right Outer Join >Cross Join >Full Outer Join #JavaProgramming #DBMS #Database #Java #InterviewQuestions #Concepts #coding #100daysofcoding

#AI vs #ML vs ##NN vs #DL >AI is a bigger concept covering all the other three >Machine Learning is a subset of AI >NN is a subset of ML >DL is a subset of NN #JavaProgramming #SQL #Java #InterviewQuestions #Concepts #DBMS #100daysofcoding #Coding

There are three main ways to train LLMs >casual language >sentence classification >token classification #LLM #llms #largelanguagemodel #GenerativeAI #Java #Sorting #InterviewQuestions #JavaProgramming #Concepts #coding #100daysofcoding

#MachineLearning Algorithms 🚀🚀🚀 #DataStructure #AI #JavaProgramming #Java #Python #NeuralNetworks #100daysofcoding #Coding

United States 트렌드
- 1. Tulane 13.5K posts
- 2. Gunther 23.2K posts
- 3. #SmackDown 34.9K posts
- 4. Cocona 77.3K posts
- 5. North Texas 7,459 posts
- 6. #ROHFinalBattle 18.1K posts
- 7. fnaf 2 62.4K posts
- 8. Anthony Davis 2,208 posts
- 9. LA Knight 10.9K posts
- 10. Boise State 3,616 posts
- 11. #GCWSay N/A
- 12. UNLV 4,338 posts
- 13. #OPLive 2,673 posts
- 14. #TNAFinalResolution 7,575 posts
- 15. Trouba 1,163 posts
- 16. Meek 8,423 posts
- 17. Flag Day 3,035 posts
- 18. 5 YEARS WITH MC WONYOUNG 6,412 posts
- 19. Athena 10.5K posts
- 20. Dizzy 6,418 posts
Something went wrong.
Something went wrong.