ANY.RUN
@anyrun_app
Empowering businesses with proactive security solutions: Interactive Sandbox, TI Lookup and Feeds. Sign up: https://app.any.run/?utm_source=x#register
You might like
👨💻 #ANYRUN’s solutions integrate with leading SOAR, SIEM, TIP, and EDR solutions, giving your SOC the visibility and speed to uncover hidden threats and respond faster. Boost detection, reduce MTTR, and cut workload with seamless integrations: any.run/cybersecurity-…

🚨 Expose Evasion Tricks in Linux Malware Many #Linux botnets and cryptominers hide by replacing system utilities like ps, ls, or netstat. This allows attackers to control what the system reports and conceal malicious activity. ⚠️ Two core techniques make infected systems look…
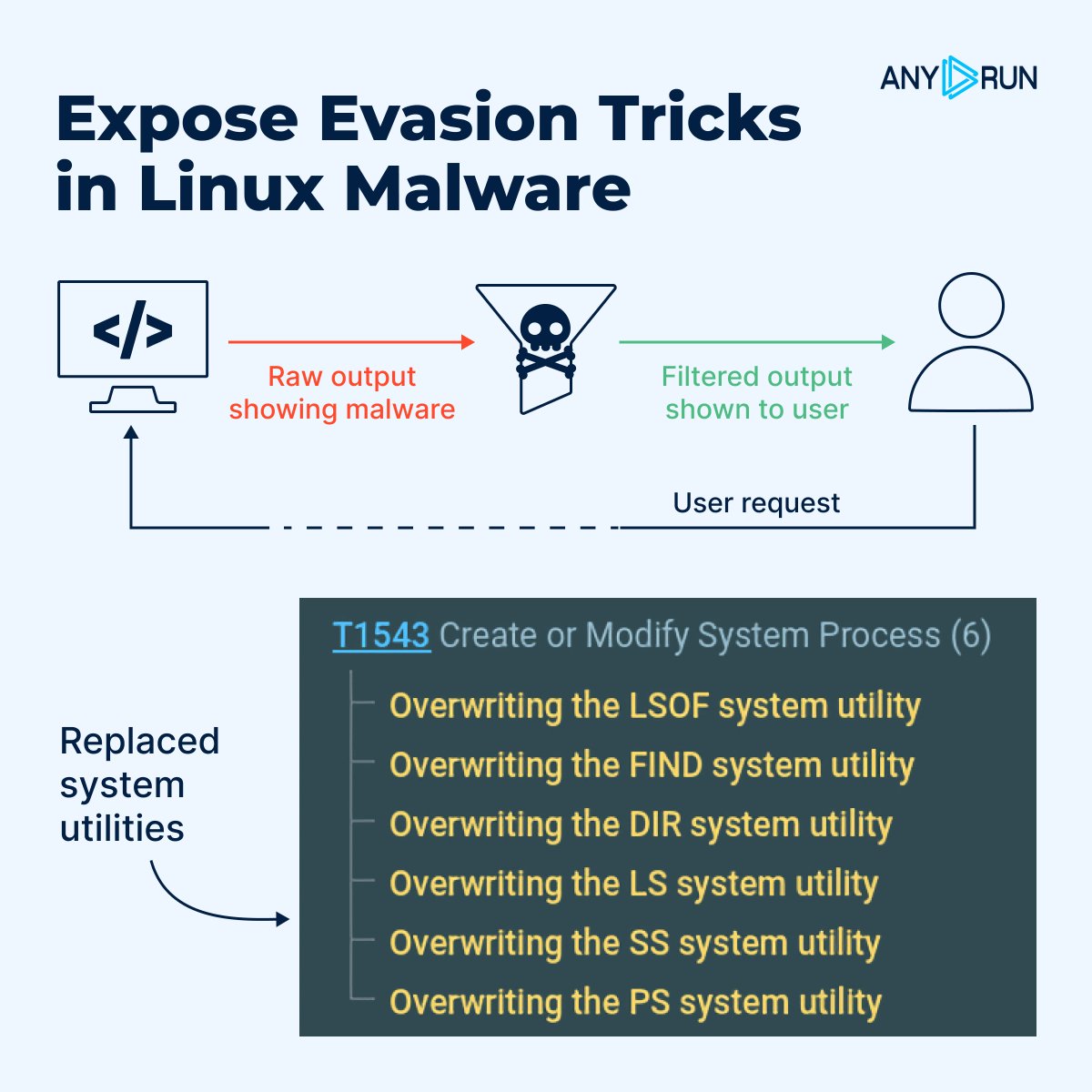
⚠️ #XWorm in PNG files, #JSGuLdr’s three-stage loader, Linux #ransomware, Android RATs; November was packed with multi-layered attacks. See the full analysis of the month’s major threats and key detection takeaways for SOC teams 👇 any.run/cybersecurity-…
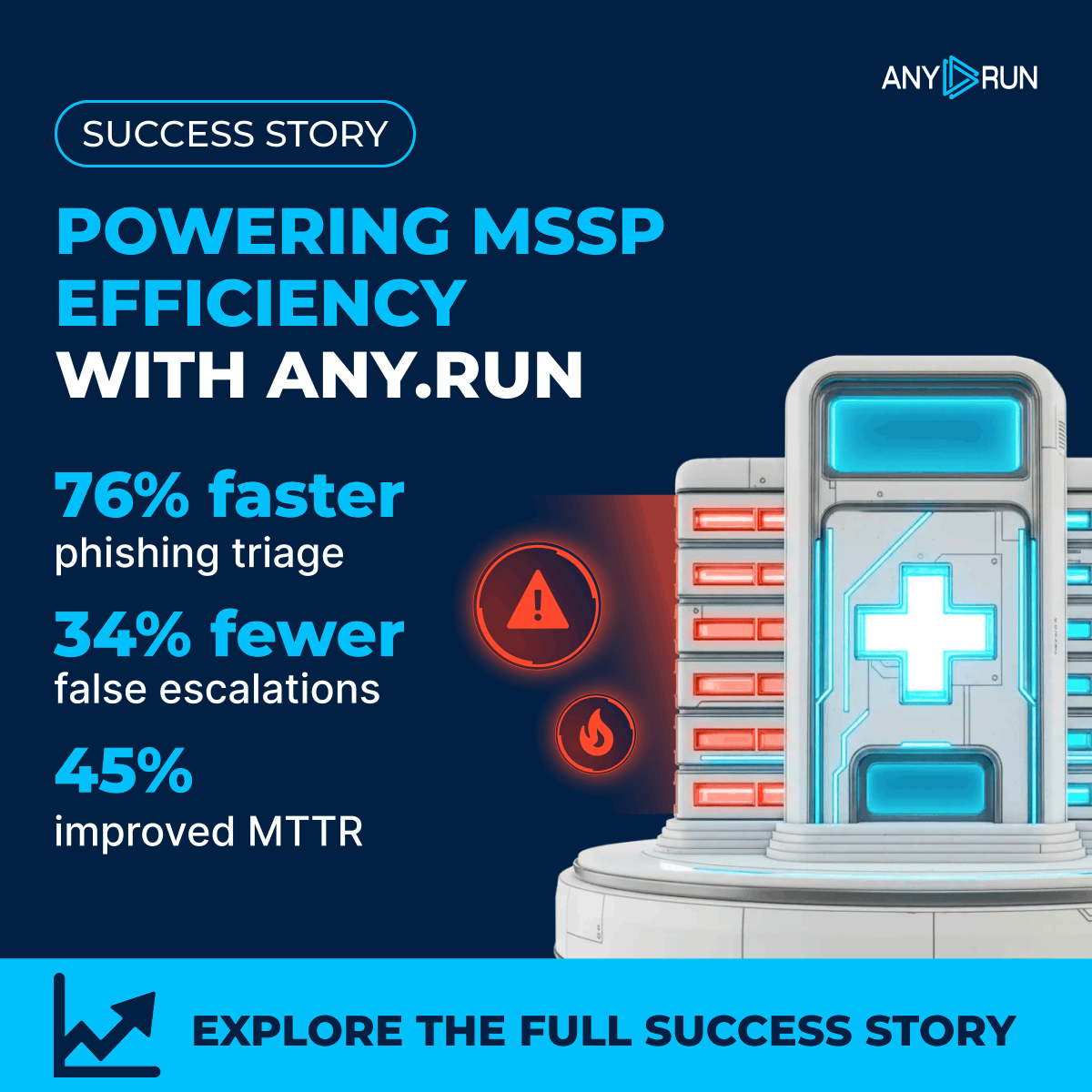
🏥 More clients meant more pressure for this healthcare MSSP: slow MTTR, manual checks, and constant escalations. #ANYRUN helped them shift to proactive defense, but don’t just take our word for it. See the full success story told by the SOC leader: any.run/cybersecurity-…
🚩 When you deal with hundreds of alerts, how do you spot the ONE that matters? We broke down how threat intelligence turns 15-min investigations into 30-second decisions thanks to actionable context. See how you can use it 👇 any.run/cybersecurity-…
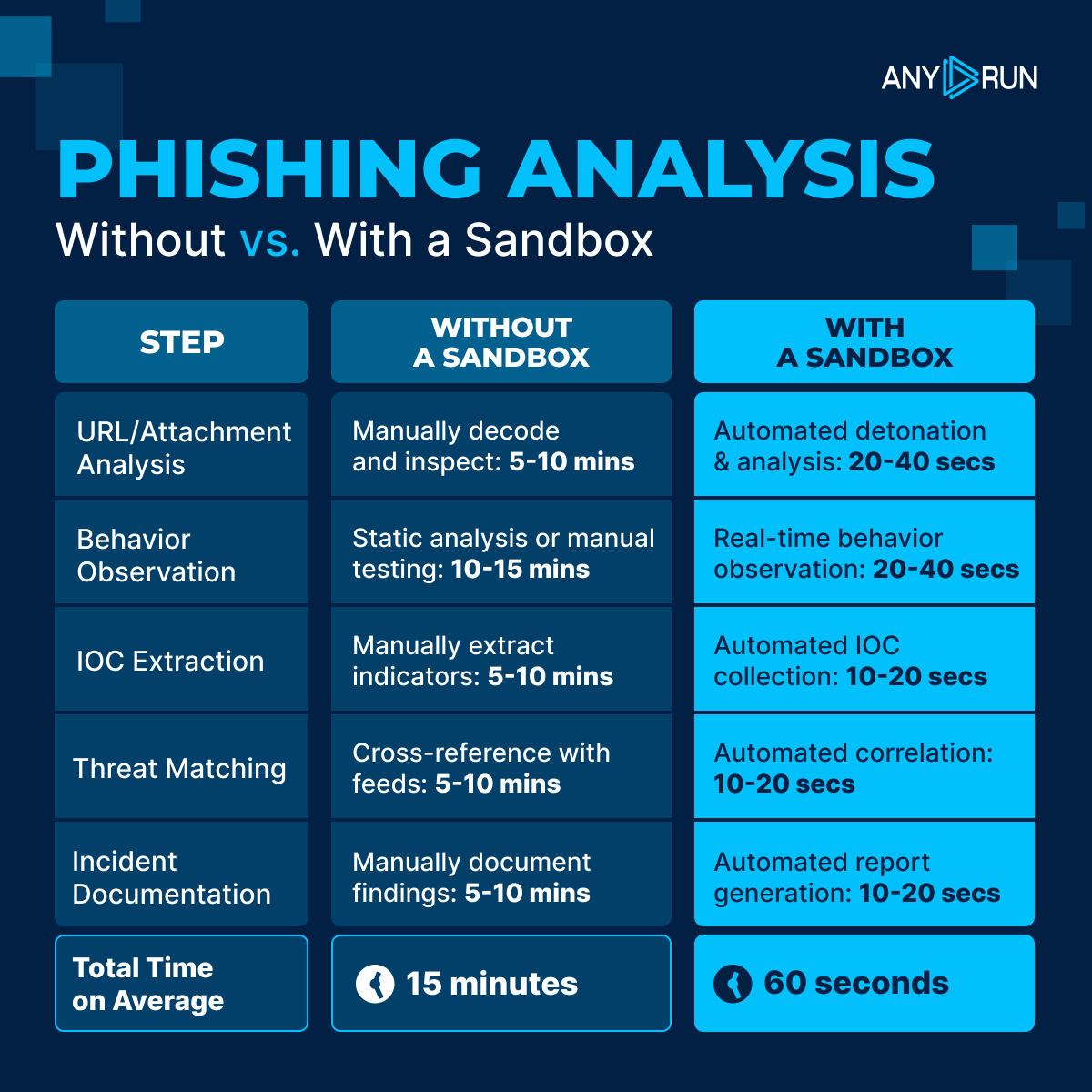
🎣 Manual #phishing analysis slows teams down. #ANYRUN's Sandbox turns a 15-minute workflow into a 60-second analysis, giving SOCs up to 3x higher investigation throughput. ⚡️ See how it levels up your investigations: any.run/cybersecurity-…
🚨 Our new TI Report outlines cross-platform threats that SOCs should track right now: 🔹 #BTMOB RAT abuses Accessibility Services to target banking apps 🔹 #PDFChampions is delivered through malvertising, a highly effective initial infection vector 🔹 #Efimer combines phishing…
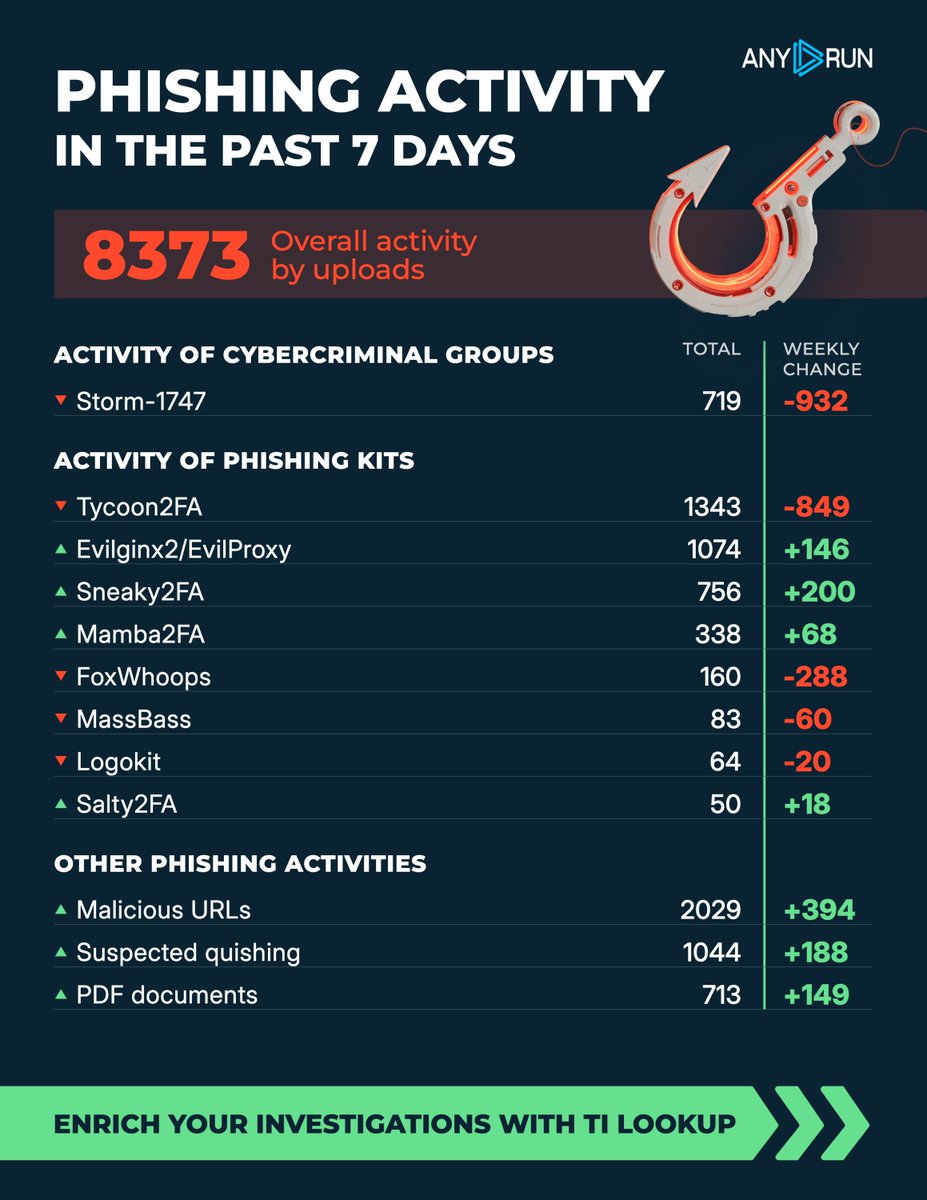
Phishing activity in the past 7 days 🐟 Track latest #phishing threats in TI Lookup: intelligence.any.run/analysis/looku… #TopPhishingThreats
⚠️ #DoubleTrouble is an Android banking trojan leveling up mobile cybercrime with dual-stage attacks. It uses MFA interception and modular spyware to target European users. 👨💻 Here’s how it works and how to detect & stop it: any.run/malware-trends…

📢 Live tomorrow! #ANYRUN’s experts will demonstrate how to: ✅ Reduce MTTR by 21 minutes per incident ✅ Ensure early detection of new attacks ✅ Eliminate alert fatigue ✅ Achieve a 3x performance boost Register and bring your team: anyrun.webinargeek.com/soc-leader-s-p…

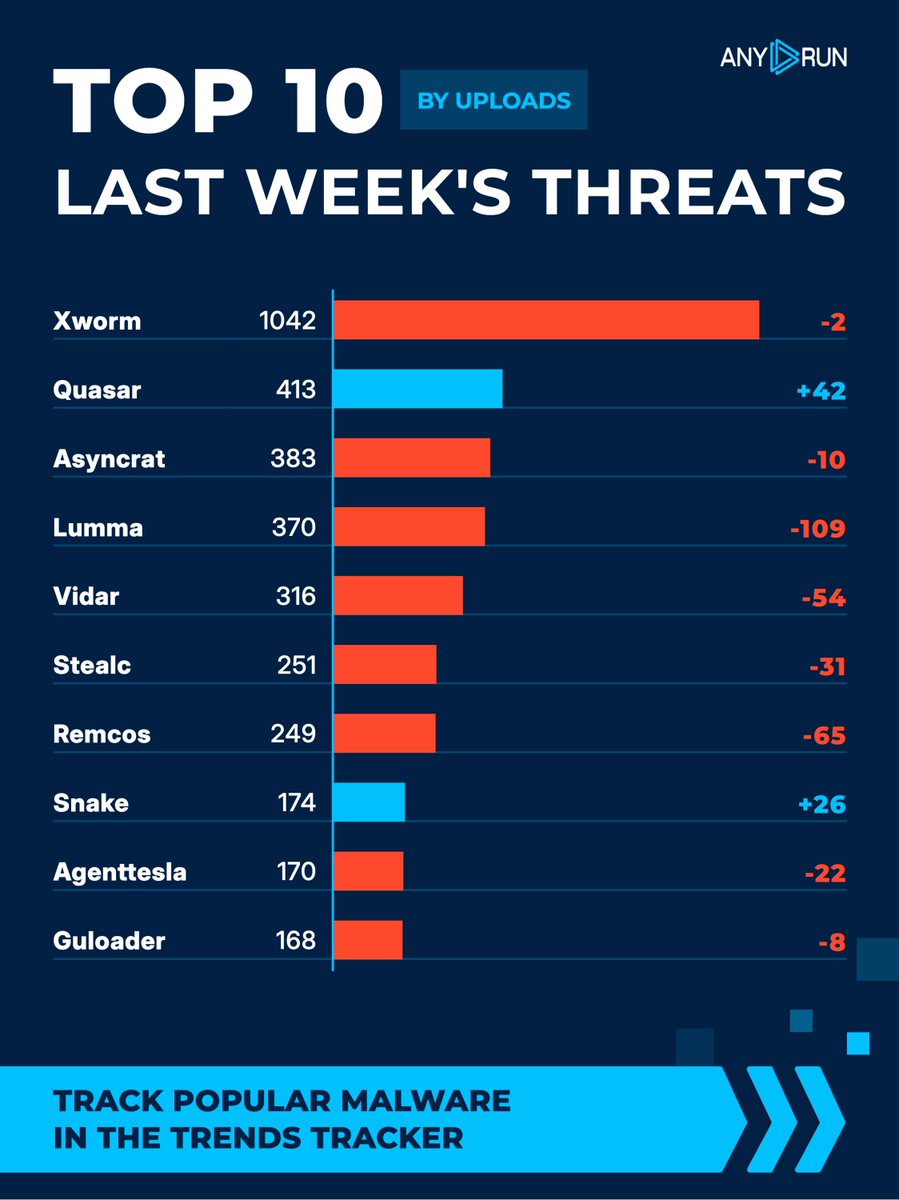
Top 10 last week's threats by uploads 🌐 ⬇️ #Xworm 1042 (1044) ⬆️ #Quasar 413 (371) ⬇️ #Asyncrat 383 (393) ⬇️ #Lumma 370 (479) ⬇️ #Vidar 316 (370) ⬇️ #Stealc 251 (282) ⬇️ #Remcos 249 (314) ⬆️ #Snake 174 (148) ⬇️ #Agenttesla 170 (192) ⬇️ #Guloader 168 (176) Explore malware in…
📢 Join us live! Explore 3 actionable steps to cut MTTR by 21 minutes, detect new attacks earlier, eliminate alert fatigue, and boost SOC performance 3x. 📅 November 25 Register and bring your team: anyrun.webinargeek.com/soc-leader-s-p…

💡 When alerts overwhelm your SOC, it's time to automate. #ANYRUN’s Sandbox combines automation with interactivity to detonate multi-stage phishing, beat evasion, and deliver verdicts in seconds. See how it gives your team a measurable advantage 👇 any.run/cybersecurity-…
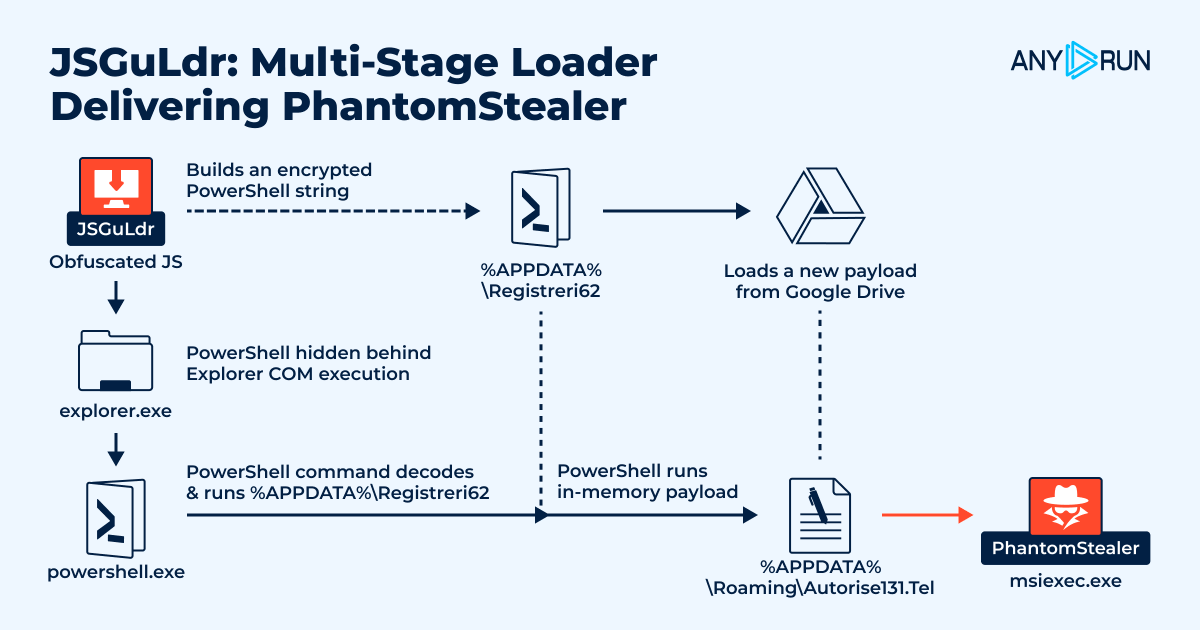
🚨 𝗝𝗦𝗚𝘂𝗟𝗱𝗿: 𝗠𝘂𝗹𝘁𝗶-𝗦𝘁𝗮𝗴𝗲 𝗟𝗼𝗮𝗱𝗲𝗿 𝗗𝗲𝗹𝗶𝘃𝗲𝗿𝗶𝗻𝗴 𝗣𝗵𝗮𝗻𝘁𝗼𝗺𝗦𝘁𝗲𝗮𝗹𝗲𝗿 TL;DR: We identified #JSGuLdr, a multi-stage JavaScript-to-PowerShell loader used to deliver #PhantomStealer. A JScript file triggers PowerShell through an Explorer COM call,…
⏱️ Can a full phishing chain really be analyzed in ~60 seconds? See our new breakdown on sandbox vs. manual workflows and how analysts get to the verdict faster. Here is how you can speed up detection in your SOC 👇 any.run/cybersecurity-…
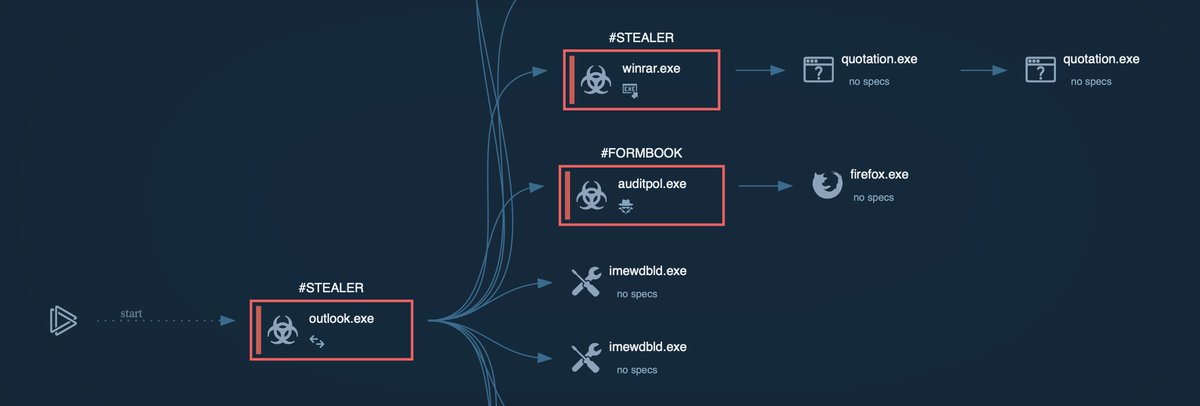
⚠️ Just one email targeting a US state agency exposed a full FormBook infection chain. Spoofed headers, failed SPF checks, and C2 activity become visible in seconds. 👨💻 See how attacks on government institutions were uncovered and analyzed using #ANYRUN: any.run/cybersecurity-…
⚠️ Rundll32, certutil, mshta; attackers abuse them to load payloads without raising alerts. Security teams using real-time analysis expose these #LOLBin tactics fast. Here’s how to achieve it inside your SOC 👇 any.run/cybersecurity-…
United States Trends
- 1. Thanksgiving 425K posts
- 2. National Guard 66.1K posts
- 3. #InfoSecVPN N/A
- 4. Bayern 161K posts
- 5. Mbappe 83.8K posts
- 6. Frank Ragnow 1,824 posts
- 7. Arsenal 294K posts
- 8. D.C. 218K posts
- 9. Kimmich 4,923 posts
- 10. Lennart Karl 4,647 posts
- 11. Denzel 4,175 posts
- 12. Patrick Morrisey N/A
- 13. Olympiacos 18.9K posts
- 14. Golesh 3,112 posts
- 15. Camp Haven 7,652 posts
- 16. Wine 41K posts
- 17. #ARSBAY 3,896 posts
- 18. Anthony Rendon N/A
- 19. Pizza 49.2K posts
- 20. Fani Willis 22.6K posts
You might like
-
 MalwareHunterTeam
MalwareHunterTeam
@malwrhunterteam -
 ATT&CK
ATT&CK
@MITREattack -
 abuse.ch
abuse.ch
@abuse_ch -
 proxylife
proxylife
@pr0xylife -
 Unit 42
Unit 42
@Unit42_Intel -
 blackorbird
blackorbird
@blackorbird -
 Arkbird
Arkbird
@Arkbird_SOLG -
 Cryptolaemus
Cryptolaemus
@Cryptolaemus1 -
 The DFIR Report
The DFIR Report
@TheDFIRReport -
 Check Point Research
Check Point Research
@_CPResearch_ -
 ExecuteMalware
ExecuteMalware
@executemalware -
 RedDrip Team
RedDrip Team
@RedDrip7 -
 James
James
@James_inthe_box -
 Karsten Hahn
Karsten Hahn
@struppigel -
 Dee
Dee
@ViriBack
Something went wrong.
Something went wrong.