Charles Shirer
@bsdbandit
A Hacker who is A Lover of People, and Life @RetroTwinz @Secbsd, @GrumpyHackers, @NovaHackers, @deadpixelsec @hacknotcrime Advocate @PositivelyBlue_ OSCP, OSWP
You might like
Interesting read on job displacement with AI probably isn't the case. "But here’s what a new MIT study just revealed: 95% of companies investing in AI are getting exactly zero return on investment." "Yale University’s Budget Lab just dropped a bombshell report analyzing U.S.…
github.com/dafthack/Graph… pew pew pew in PowerShell. These TTPs work 60% of the time, every time.
New Issue of Executive Offense! - Slides for Attacking AI (talk version) - Slides for Modern Recon (talk version) - Links for some very cool presos from @WWHackinFest and... GIVING AWAY 2 ARCANUM BADGES: repost this post and fill the form out at the bottom of the newsletter…

New video! Proud to announce Collector, a powerful new extension for @burpsuite that provides solutions for the collection, tracking, and handling of any kind of "token". Watch here: youtu.be/SsjlL1N1qgM Try out Collector: github.com/Tib3rius/Colle…

Here is a tip for noobs for reverse engineering malware stuff Tip 1. When you get a file and you think it might be spooky, you need to determine what kind of file it is. You cannot rely on file extensions. The easiest and most ghetto way (the way I do it) is opening the file…
ADCSDevilCOM 📍 A C# tool for requesting certificates from ADCS using DCOM over SMB. This tool allows you to remotely request X.509 certificates from CA server using the MS-WCCE protocol over DCOM and It bypasses the traditional endpoint mapper requirement by using SMB…
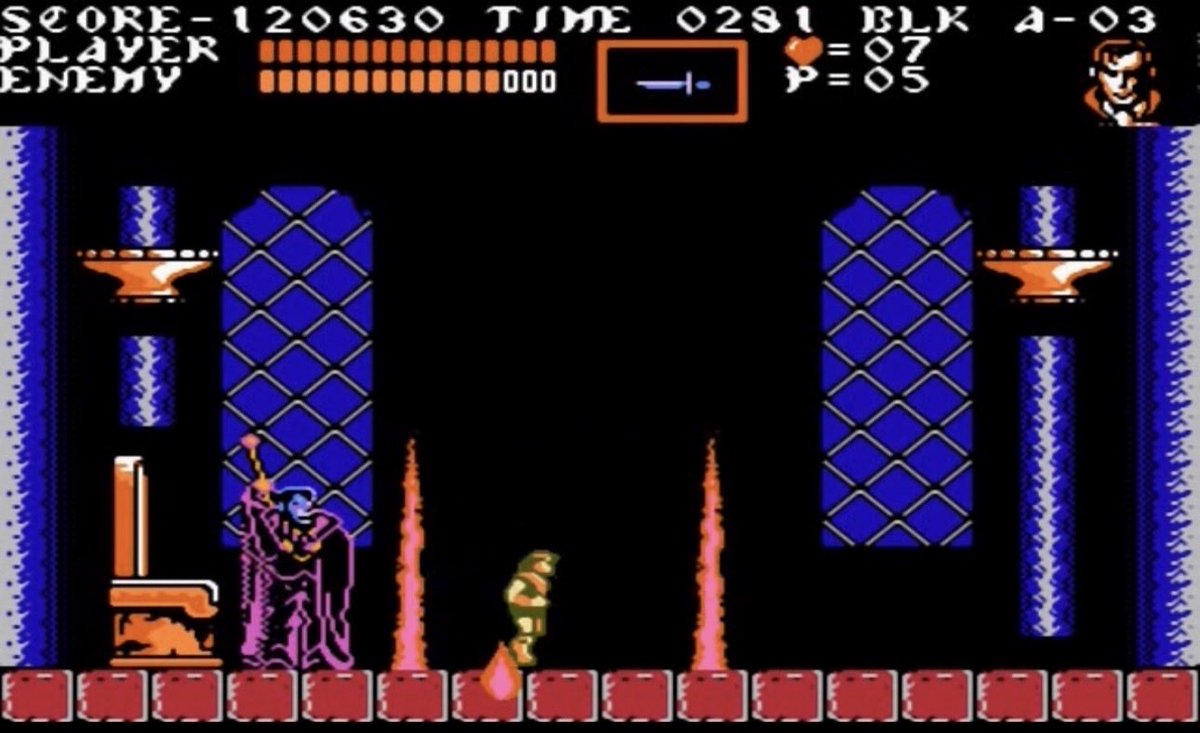
In honor of Halloween and waiting on the trick-or-treaters, I’m taking it back to Castlevania three I just had to pause it at this spot because I don’t know if I’m gonna make it back here again 😂😂😂😂 flashback to 1990 Owwww yip yip
I bet at least 80% of Entra admins would blindly grant RoleManagement.ReadWrite.All to an Enterprise app that was purchased by their company Most wouldn't even know what that means - and in doing so, they practically give Global Admin level permissions to the application vendor
Yeah, not long ago an app requested app role RoleManagement.ReadWrite.All - and by using Graph logs in a dev tenant I found out that the ONLY reason was that the automated onboarding process had to assign a non-GA Entra role to a service principal. 😵💫 «How ‘bout no»
Can we eliminate the C2 server entirely and create truly autonomous malware? On the Dreadnode blog, Principal Security Researcher @0xdab0 details how we developed an entirely local, C2-less malware that can autonomously discover and exploit one type of privilege escalation…

Pretty big deal/breakthrough on the LLM training side. Self improving language models. venturebeat.com/ai/self-improv…
Casually dropped new recon updates too at @WWHackinFest Thanks for the amazing feedback from everyone!

So, here's the deal--If you're a pen tester who says, "I don't pen test for AI injection flaws," it's like saying that you don't test for SQLi, or XSS, or command injection. You are missing the boat on some of the most important vulns today. It's like saying in 2004, "We don't…
There is someone exposing IRGC (Islamic Revolutionary Guard Corps) stuff on GitHub. I'm not a IRGC geopolitical nerd, so I can't assess the value of the content. However, if you know what the fuck is going on, maybe you'll find it interesting: github.com/KittenBusters/…
InstagramPrivSniffer: Views Instagram private account's media without login GitHub: github.com/obitouka/Insta…

Red teaming(in InfoSec)originally meant breaking into organizations and demonstrating real impact by testing assumptions, technologies, and processes with minimal restrictions before frameworks like MITRE ATT&CK and the rise of purple teaming. Over time, some people began using…
United States Trends
- 1. Luka 63.7K posts
- 2. Clippers 18.4K posts
- 3. Happy Thanksgiving Eve N/A
- 4. Lakers 49.4K posts
- 5. #DWTS 96K posts
- 6. Good Wednesday 18.6K posts
- 7. #LakeShow 3,560 posts
- 8. Jaxson Hayes 2,504 posts
- 9. Kris Dunn 2,715 posts
- 10. Collar 46K posts
- 11. Kawhi 6,369 posts
- 12. Robert 139K posts
- 13. Reaves 12.7K posts
- 14. Jordan 116K posts
- 15. Ty Lue 1,618 posts
- 16. Alix 15.2K posts
- 17. TOP CALL 14.6K posts
- 18. Elaine 46.3K posts
- 19. Colorado State 2,504 posts
- 20. Zubac 2,305 posts
You might like
-
 Marcus J. Carey
Marcus J. Carey
@marcusjcarey -
 Black Hills Information Security
Black Hills Information Security
@BHinfoSecurity -
 strandjs - [email protected]
strandjs - [email protected]
@strandjs -
 gabsmashh
gabsmashh
@gabsmashh -
 Nicole Beckwith
Nicole Beckwith
@NicoleBeckwith -
 Ted James, SQL Agent Man
Ted James, SQL Agent Man
@deepeddyinfosec -
 Tanya Janca | Shehackspurple
Tanya Janca | Shehackspurple
@shehackspurple -
 corgi
corgi
@corg_e -
 Joe B. - BlindHacker
Joe B. - BlindHacker
@TheBlindHacker -
 Accidental CISO
Accidental CISO
@AccidentalCISO -
 Lina
Lina
@d0rkph0enix -
 InfoSecSherpa 🏔️
InfoSecSherpa 🏔️
@InfoSecSherpa -
 Bryson 🦄
Bryson 🦄
@brysonbort -
 Phillip Wylie
Phillip Wylie
@PhillipWylie -
 Lisa Forte
Lisa Forte
@LisaForteUK
Something went wrong.
Something went wrong.