Akash Trehan
@cod3maxx
Kernel Security R&D @ Microsoft. Prev: CS@IIT Bombay. RA @CarnegieMellon SCS. Team @shellphish. Loves Reverse Enginering, SE, Netsec, CTF, Psychology and Pizza
내가 좋아할 만한 콘텐츠
Doing this 10 AM PST tomorrow. See y'all there!!😄
Don't forget to tune in tomorrow for the February #WIPWebcast for a behind-the-scenes look at all things storage. 💾 🗓️ February 24 | 6 PM UTC | 10 AM PST Follow us on Twitch now: twitch.tv/windowsinsider

The product I've been working on for a couple of years is now available for developers to help secure their data on Windows! 😊
New blog on VBS enclaves on Windows 11 just dropped: techcommunity.microsoft.com/t5/windows-os-…
Excited for my product release at BUILD 2024!!
“Previously available to Windows security features only, VBS enclaves are now available to third-party application developers” Very cool. Waiting for more details :)
Hahahaha @SRazaB24 🔥🔥
Razbaaaa hai Punjabi! 🤌 #SherSquad, how good is @SRazaB24's Punjabi? 🤔 #LSGvPBKS #JazbaHaiPunjabi #SaddaPunjab #TATAIPL
We love you KKKK...Curran! ❤️ #PBKSvKKR #JazbaHaiPunjabi #SaddaPunjab #TATAIPL @CurranSM
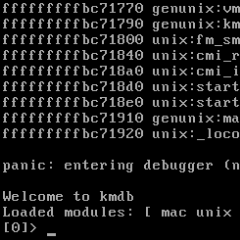
We found a way to defeat pointer authentication (and forge kernel pointers from userspace) on the Apple M1 via a new hardware attack. Here’s how it works- pacmanattack.com
A great example of growth mindset at a Startup!
In 2020, we pivoted @AkitaSoftware from a security company to an API dev tools company and completely changed how we operate. It's fashionable for founders to blog about their year, so here are our lessons from getting developers to use our stuff. akitasoftware.com/blog/2020/12/2…
Join me tomorrow at 10 AM PST | 6 PM GMT | 11:30 PM IST ✌️ @windowsinsider @Microsoft @Windows @windowsblog @windowsdev
Don't forget to join us tomorrow at 5 PM GMT | 10 AM PST for the November episode of the #WIPWebcast! 🔥🔥 We'll be looking at modern disk management and file recovery features with their engineers. Join us on our Twitch: msft.it/6016p8HPE

I featured in a podcast! 🎙 Listen as I talk to Chad Clarke about my journey with software engineering and life at Microsoft on his podcast "Behind the Business" Available on Spotify, Apple podcast and Google podcast. Go listen! open.spotify.com/episode/75tzlV…
We're still in stealth mode but you can get a sneak peek 🕵🏻♀️ of what we're working on here! Video from #CollisonConf last month--@jeanqasaur speaks at 11:45. (We opened for @JustinTrudeau with the same talk!) vimeo.com/343133648

i love getting pitches for talks with privacy advocates from people who use pixel-tracking programs to see if i opened their email
Curious to read this Harvard paper from last year. CAs and decentralisation coming together? What? #MicrosoftResearch

#Adobe Issues Emergency #Security Updates to Patch Two Critical Flaws in Acrobat and Reader Software (for Windows and macOS) thehackernews.com/2019/01/adobe-… —Arbitrary Code Execution (CVE-2018-16011) —Privilege Escalation (CVE-2018-19725)

Happy New Year guys!! I hope you have the best one ever! And that you absolutely crush 2019 as I plan to. Cheers! 🎉
United States 트렌드
- 1. #StrangerThings5 166K posts
- 2. Thanksgiving 636K posts
- 3. Reed Sheppard 3,705 posts
- 4. Afghan 258K posts
- 5. robin 73.2K posts
- 6. Podz 3,339 posts
- 7. BYERS 32.8K posts
- 8. holly 53.2K posts
- 9. National Guard 631K posts
- 10. Gonzaga 8,082 posts
- 11. Dustin 85.6K posts
- 12. #AEWDynamite 21.1K posts
- 13. Amen Thompson 1,452 posts
- 14. Michigan 77.1K posts
- 15. Erica 13.8K posts
- 16. Tini 8,227 posts
- 17. Rahmanullah Lakanwal 97.8K posts
- 18. Jonathan 69K posts
- 19. hopper 13.2K posts
- 20. Will Richard 2,080 posts
Something went wrong.
Something went wrong.