
Crusaders of Rust
@cor_ctf
A European and American Security Research Group
You might like
Watch XOR’s talk CUDA de Grâce: Owning AI Cloud Infrastructure with GPU exploits Kernel + driver bugs aren’t just a LPE problem, they’re a cloud problem. With the explosion of AI in the cloud, NVIDIA’s GPU drivers have become a valuable attack surface youtu.be/Lvz2_ZHj3lo
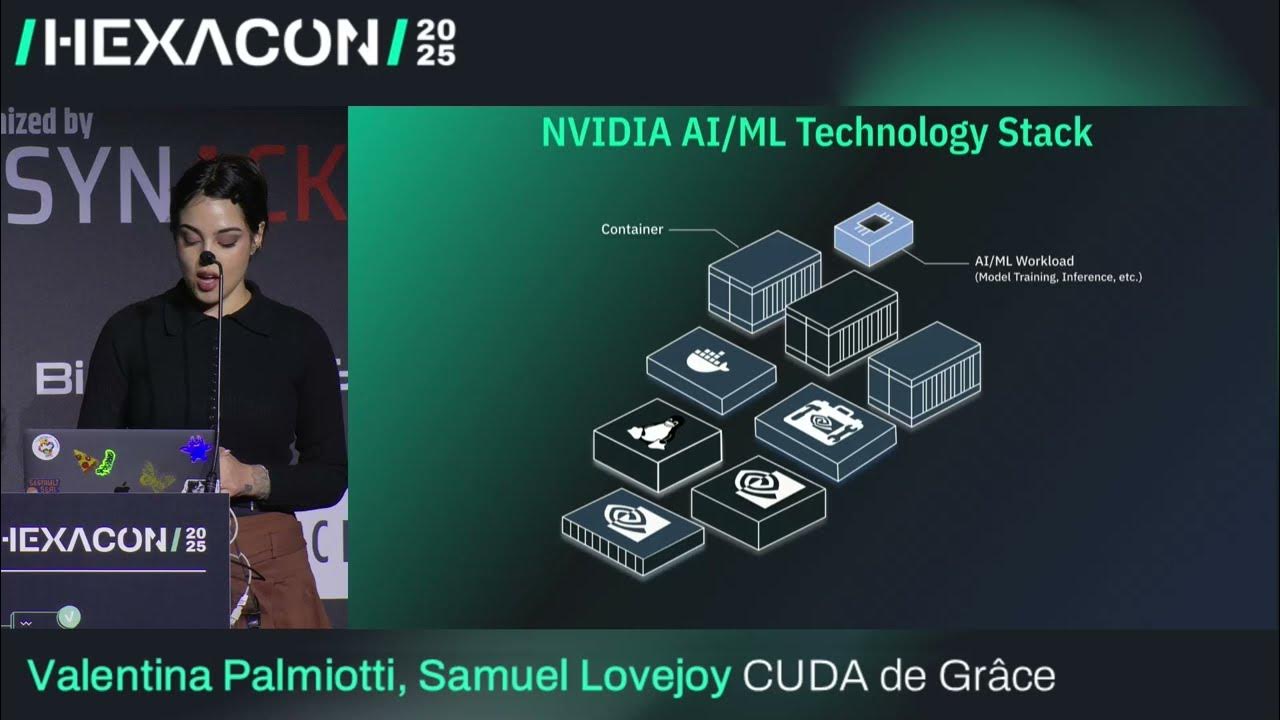
youtube.com
YouTube
HEXACON 2025 - CUDA de Grâce by Valentina Palmiotti & Samuel Lovejoy
My HEXACON talk video is out! It covers a small race condition in the Linux kernel’s io_uring. I recommend watching it at 1.25× speed since I’m still not great at speaking 😅 youtube.com/watch?v=Ry4eOg… Here is the slide! u1f383.github.io/slides/talks/2…
Our @hexacon_fr talk is out on Youtube now😎 youtu.be/C-52Gwmce3w Follow the slides at: storage.googleapis.com/static.cor.tea…

youtube.com
YouTube
HEXACON 2025 - An RbTree Family Drama by William Liu & Savino Dicanosa
If you missed HEXACON 2025 or want to rewatch some of the talks, they’re now available on our YouTube channel 📽️ Enjoy the content, and see you in 2026! youtube.com/playlist?list=…
We at CoR (+ @u1f383) had a great experience at @hexacon_fr this weekend Met many skilled VR people, the venue was amazing, and the speaker gifts were simply🔥 Best offensive security conference we have seen so far - thanks again to the organizers for the opportunity!

An RbTree Family Drama: Exploiting a Linux Kernel 0-day Through Red-Black Tree Transformations by William Liu and Savino Dicanosa

Wanna learn how to perform OOP in functional programming all in Google Sheets? Come check out our team member @MaxCai33447144 research, which he made into a corCTF 2025 challenge! cor.team/posts/corctf-2…
We have a🔥presentation ready for Hexacon. Come grab a beer with us afterwards! See everyone in Paris🇫🇷🫡
📢 An RbTree Family Drama: Exploiting a Linux Kernel 0-day Through Red-Black Tree Transformations by William Liu & Savino Dicanosa

Say hello to Eternal Tux🐧, a 0-click RCE exploit against the Linux kernel from KSMBD N-Days (CVE-2023-52440 & CVE-2023-4130) willsroot.io/2025/09/ksmbd-… Cheers to @u1f383 for finding these CVEs + the OffensiveCon talk from gteissier & @laomaiweng for inspiration!
Check out our teammate's retrospective on his kernel fuzzing summer: willsroot.io/2025/09/syz-su… It covers a net/sched fuzzing quirk (inspiring HangBuzz101 in corCTF), and summarizes the kernelCTF adventures of our team. Another really cool exploit write-up will drop this Sunday 👀
For corCTF2025 our teammate D3vil (syst3mfailure.io) wrote an Android kernel pwn. Congrats to @u1f383 for the only solve! Make sure to read his writeup!
Last weekend, I participated in corCTF and solved the Android Pwn challenge - corphone. It was a great challenge, and I learned a lot from it. Here's my write-up :) u1f383.github.io/android/2025/0…
We recently claimed the cos-113 slot with an exploit for CVE-2024-58240😎 A backport for an exploitable UAF was missed for 6.1.x for the past 1.5 years🧐 Maybe when we have healed from our recent 100k bug bounty typo will we tell the full story🤪

Per tradition, corCTF rev is just VM rev. Check out these 2 author writeups about VM rev from @MaxCai33447144, our new reverse engineer lead! cor.team/posts/corctf-2… cor.team/posts/corctf-2…
Come check out our author writeup for corctf-challenge-dev-2 from Drakon: cor.team/posts/corctf-2… Timing side-channel attack against Chromium extensions😎
corCTF 2025 has ended! Congrats to the top 5: 1. @FlatNetworkOrg 2. @r3kapig @ProjectSEKAIctf 3. The Amazing Digital Orange 4. @TheRomanXpl0it 5. STM Thank you to all of our players and sponsors! @osec_io, Research Innovations, @ret2systems, @trailofbits, @vector35, @googlecloud

24 hours left in corCTF! Come play if you haven't already, and let's see if there are any big moves in the final day 👀 Our final challenge wave will be dropping shortly.

Online Safety Act getting in your way? Win £50 or a year of NordVPN in misc/england. Come play corCTF 2025, only 42 more hours to go!

corCTF 2025 begins in an hour! Come register at 2025.cor.team 😎 We have everything from easy challenges to an AMD uarch attack, a web service 0-day, and an Android LPE exploit👀
On your marks, set, pwn in 24 hours!🚩 Come register for corCTF 2025 at 2025.cor.team 😎, our prize pool is over 10k USD🤑

United States Trends
- 1. #ALLOCATION 104K posts
- 2. The BIGGЕST 491K posts
- 3. #JUPITER 104K posts
- 4. Kanata 18.3K posts
- 5. #GMMTVxTPDA2025 69.2K posts
- 6. Lakers 49.6K posts
- 7. Dillon Brooks 7,482 posts
- 8. Hololive 14.8K posts
- 9. Giants 87.1K posts
- 10. Bron 25.6K posts
- 11. Patriots 135K posts
- 12. Dart 37.1K posts
- 13. #WWERaw 73.5K posts
- 14. #AvatarFireAndAsh 3,349 posts
- 15. Suns 19.8K posts
- 16. STEAK 10.6K posts
- 17. Drake Maye 24.8K posts
- 18. James Cameron 5,055 posts
- 19. Collin Gillespie 2,139 posts
- 20. Pats 16.3K posts
You might like
-
 organizers
organizers
@0rganizers -
 Linux Kernel Security
Linux Kernel Security
@linkersec -
 ptr-yudai
ptr-yudai
@ptrYudai -
 kylebot
kylebot
@ky1ebot -
 r3kapig
r3kapig
@r3kapig -
 Dataflow Security
Dataflow Security
@dfsec_com -
 thehackerscrew
thehackerscrew
@thehackerscrew1 -
 VIE
VIE
@vie_pls -
 justCatTheFish
justCatTheFish
@justCatTheFish -
 [email protected]
[email protected]
@Zardus -
 Samuel Tang
Samuel Tang
@mystiz613 -
 Interrupt Labs
Interrupt Labs
@InterruptLabs -
 zayne (zeyu) zhang
zayne (zeyu) zhang
@zeyu1337 -
 Rawsec
Rawsec
@rawsec_cyber -
 strellic
strellic
@Strellic_
Something went wrong.
Something went wrong.
















































































































