قد يعجبك
We were inspired by @notwhickey to scan #cobaltstrike beacons across the web. Here are some of our findings: quake.360.cn/quake/#/report… welcome to use our system,Click here to search:quake.360.cn/quake/#/search…

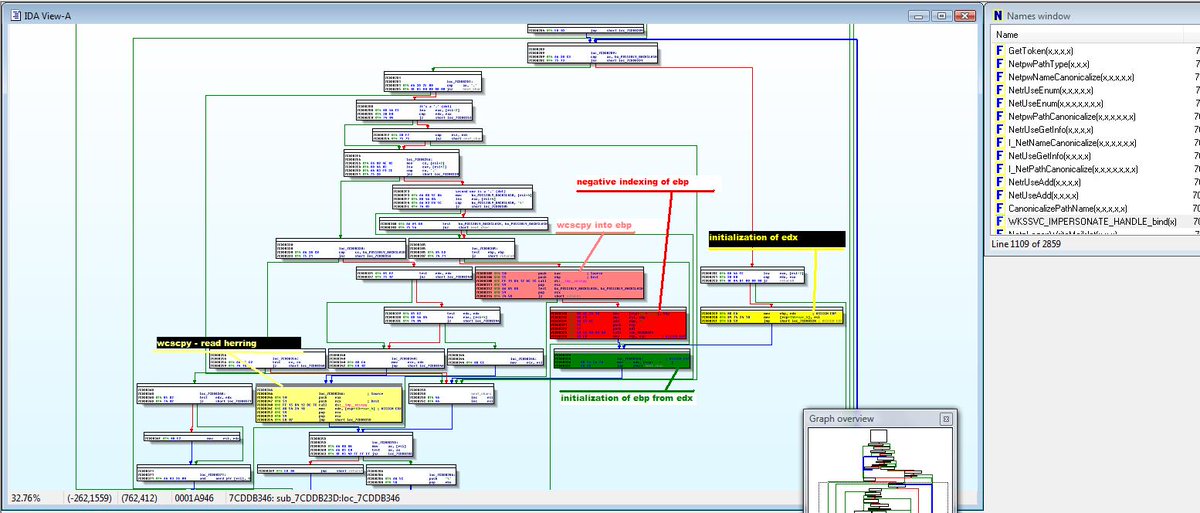
:) This one is very close, but It has too much hardcode.
Download here. github.com/360cert/slides…
@cyg0x7 Hi, could you please share the slides of your DEFCON 26 "Building a Cryptographic Backdoor in OpenSSL" talk?
It's quite intersting, something distinct from the previous exploit methods.
[oss-security] CVE-2018-5407: new side-channel vulnerability on SMT/Hyper-Threading architectures ift.tt/2PBxir9
Nice. @360CERT
The sample analysis of APT-C-27’s recent attack is just released! Let's take a look:) blog.360totalsecurity.com/en/the-sample-…
Quake is Quake, BRoyale is BRoyale.
Prove it :), @Quake isn't @FortniteGame . I get the hype, but please :/. I could make a bet for this one though :). Quake is Quake, BRoyale is BRoyale. It's not because you are very good in several BR games that you can be top at Starcraft. It's like sports. Gl though @Ninja

Hacker's hot-temper is the primary productive force in information security industry. 黑客的暴脾气是信息安全行业的第一生产力。
It has been 10 years since we reverse engineered the MS08-67 patch and published the FIRST public vuln PoC (which was used by the Confiker Worm authors). BUT, it has only been about a year since we got an angry email blaming us for the Confiker worm. dontstuffbeansupyournose.com/2008/10/23/loo…
writeup of CVE-2018-4242, UaF in AppleHV.
CVE-2018-1038: TotalMeltdown vulnerability Analysis translate.google.com/translate?sl=a…

New blog post - UEFI Ninja! Walks through a bit of work I did on UEFI and how I used #BinaryNinja to find protocols defined elsewhere in a firmware image. lightbulbone.com/posts/2018/03/…
CVE-2017-16995: Ubuntu LPE vulnerability Analysis translate.google.com/translate?sl=a…

see u guys in #syscan360 expert panel tomorrow, we’ll discuss all of the interesting research with our colleagues from unicorn team & cyber immunity lab




。。。。。。。。。。。。。
Kernels of iOS 11.0 with all debug symbols: github.com/Proteas/unstri…
github.com
GitHub - Proteas/unstripped-ios-kernels: Unstripped iOS Kernels
Unstripped iOS Kernels. Contribute to Proteas/unstripped-ios-kernels development by creating an account on GitHub.
My @offensive_con slides released! Include all 010 templates for Intel ACM and Boot Guard (KM + IBBM). All these details been REconstructed from AMI FW. Discovered few Intel Boot Guard bypasses: 2 SW + 1 HW. Never underestimate RE in your Threat Model!! github.com/REhints/Public…
Spectre & Meltdown Checker github.com/speed47/spectr… #meltdown #spectre #retpoline #grsecurity

We updated our Driver security guidance with a driver security checklist, which can help developers to eliminate known security flaws before their drivers are released ow.ly/PcT230idXW0
United States الاتجاهات
- 1. phil 35.6K posts
- 2. Columbus 194K posts
- 3. PHAN 56.6K posts
- 4. President Trump 1.2M posts
- 5. Middle East 296K posts
- 6. Cam Talbot N/A
- 7. #LGRW 1,799 posts
- 8. Thanksgiving 57.8K posts
- 9. #IndigenousPeoplesDay 15.8K posts
- 10. Brian Callahan 12.2K posts
- 11. Titans 36K posts
- 12. Macron 230K posts
- 13. #UFC323 4,799 posts
- 14. Azzi 10.3K posts
- 15. Cape Verde 24.4K posts
- 16. HAZBINTOOZ 7,433 posts
- 17. Vrabel 6,725 posts
- 18. Cejudo 1,368 posts
- 19. Marc 53.1K posts
- 20. #DonnaAdelson N/A
Something went wrong.
Something went wrong.