dappdata.link 🇺🇦
@dappdata_link
Securing the Web3 ecosystems. DM for audits
คุณอาจชื่นชอบ
Decompiling #EVM #Ethereum or any other contract like @0xPolygon or @BNBCHAIN DApps directly from the browser. A tiny work in progress sample. Follow us for more! 💪
What is a sandwich attack in DeFi? Explained with an example✅ Sandwich attack is a Front-Running type of attack and is very common on decentralized exchanges...👇🧵
Тhis is my favorite resource👌 github.com/SunWeb3Sec/DeF…
🎉Secureum RACE-18 Results🎉 💨Number of Runners: 215 ⚖️Median Score: 3.3/8 🥇Top Score: 7.3/8 🙏Designer: @Montyly 🤝Top-16 receive free tickets, sponsored by @CertoraInc, to @summit_defi's DeFi Security Summit 2023 in Paris on July 15-16. 🏆Top 32 Leaderboard🏆

Secureum RACEs are smart contract security quizzes. Participation is free & requires one-time registering at forms.gle/iL2uQvGZrDq5Uu…. RACE-18 is designed by Secureum mentor @Montyly. Details on Discord.
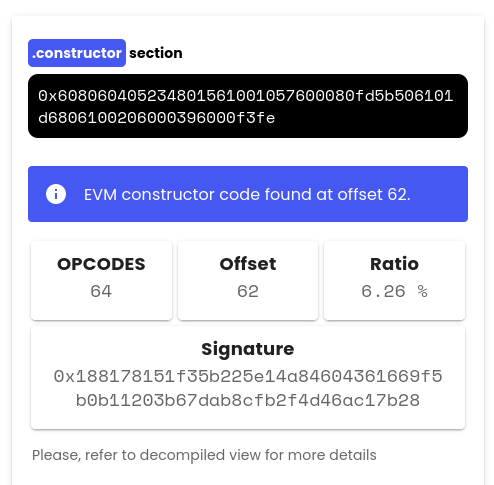
Look what I've been created! A visual representation of EVM based contracts in Graphview. This is just an empty constructor view 👇
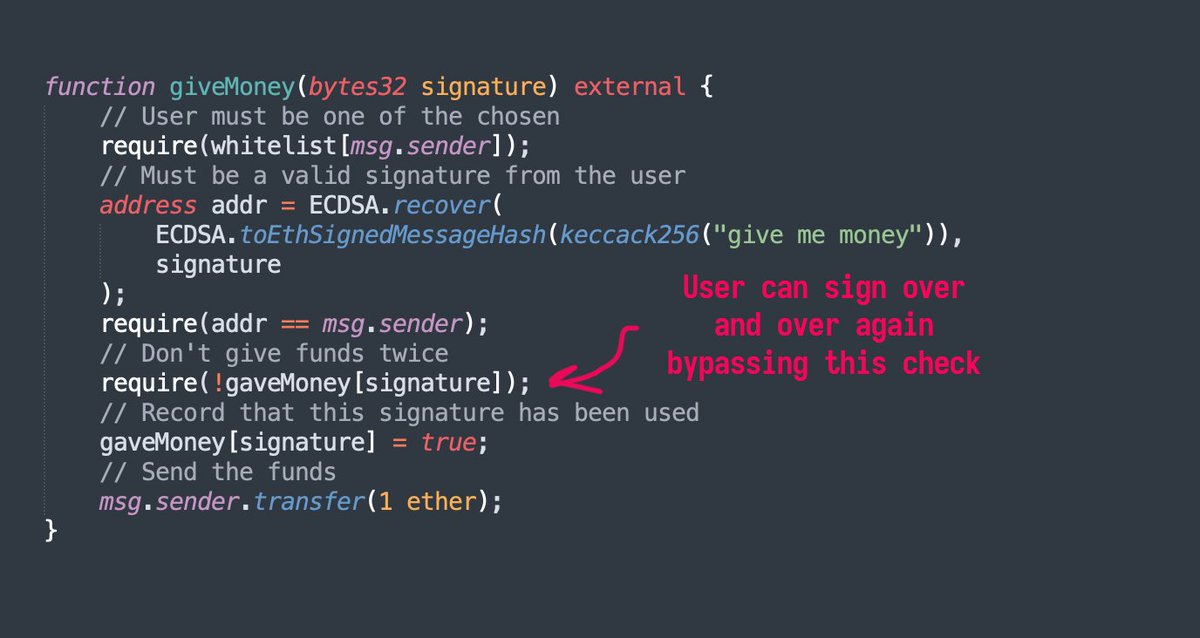
Here’s how signature malleability attacks work. Two attacks. If a user signs the same message multiple times, they get a different signature each time. If your code uses a signature as an identifier for blocking actions, users can repeat that action. 1/3
Fastest EVM symbolic execution algorithm is almost ready. For example, It's able to resolve proxy contracts in microseconds, generating pseudocode too. 💪
TLDR: Building a high precision EVM decompiler 💪
Smart Contract Development and Auditor Roadmap. After youtube.com/watch?v=xv9Omz… by @ProgrammerSmart in step 2, do YT course youtube.com/watch?v=gyMwXu… by @PatrickAlphaC

Interesting post about EVM internals and bytecode restructuring #evm #bytecode #ETH curiousstuff.eu/post/part-2-bu…
curiousstuff.eu
Part 2: Building Ethereum EVM decompiler from scratch. Getting Code Blocks
A series of post about how to design a Solidity EVM decompiler from scratch. Part 2
Our code block finding algorithm is ready. The best thing, it supports recursive calls out of the box. And can be used with ALL EVM compatible Blockchains. 💪
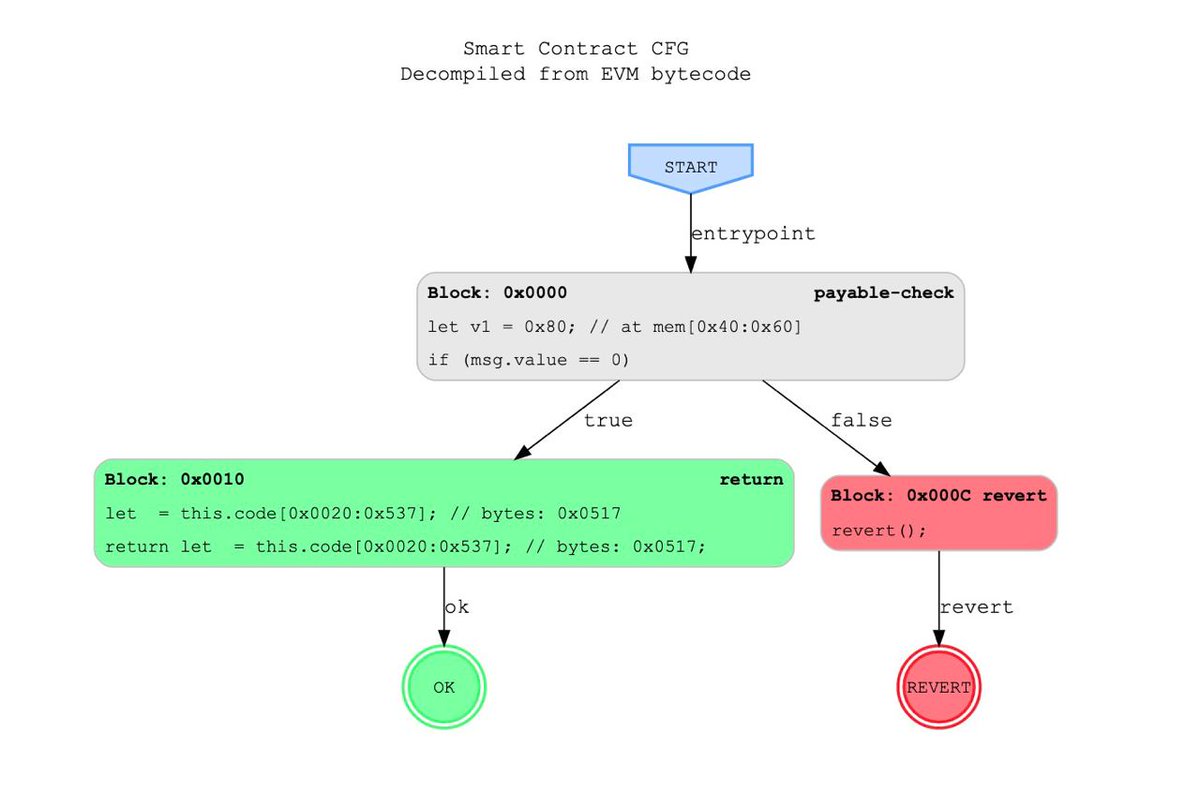
Reverse engineering a high precision #EVM CFG is kind of a challenge. But it's the first step of a successful decompiler 💪
Bitcoin is Bitcoin Crypto, web3, NFTs, DAOs, rollups, snarks, airdrops, permissionless finance... ...are Ethereum
United States เทรนด์
- 1. FIFA 444K posts
- 2. Mark Pope N/A
- 3. #ROHFinalBattle 3,031 posts
- 4. #JingleBellJohn N/A
- 5. Frank Gehry 7,037 posts
- 6. Hep B 19.2K posts
- 7. Vizio N/A
- 8. Matt Campbell 12.1K posts
- 9. #UFC326 1,596 posts
- 10. Iowa State 10.3K posts
- 11. Jordan Walsh 3,703 posts
- 12. The EU 240K posts
- 13. Hisense 1,270 posts
- 14. HOLD THE LINE 6,289 posts
- 15. Brandon Garrison N/A
- 16. Warner Bros 276K posts
- 17. Zags N/A
- 18. Gonzaga 2,420 posts
- 19. #Mundial2026 50.8K posts
- 20. Burden 27.3K posts
Something went wrong.
Something went wrong.