Daniel Púa | @[email protected]
@devploit
Head of Security @Freepik · CTF Player 🇪🇸 (@ripp3rsCTF / SFPE) · @hackandbeers Málaga Organizer · Sharing real-world infosec, no hype. Opinions my own.
내가 좋아할 만한 콘텐츠
DEFCON Quals 2025 - Memory Bank CTF Challenge Writeup - devploit blog.0xdev.eu/posts/defcon-q…
rep+: A Lightweight Alternative to Burp Suite for Quick Browser Testing bscript.substack.com/p/rep-a-lightw…
A security-first MCP server empowering AI agents to orchestrate Ghidra, Radare2, and YARA for automated reverse engineering. github.com/sjkim1127/Reve…
i just Updated my XSS article: added some cleaner, more effective one-liners and integrated DalFox one-liners that support extra options. Check it out. infosecwriteups.com/find-xss-vulne…
I started learning some cheat/anticheat stuff some time ago and wrote some rust code that might be interesting,so today I am making it public uwudrv:A Windows kernel driver + bootkit to support usermode processes trying to read/write other processes memory github.com/segura2010/uwu…
Successfully adding an entire feature with a single prompt feels like a getting a headshot in counterstrike. Got a nice update to Turbo Intruder coming soon!
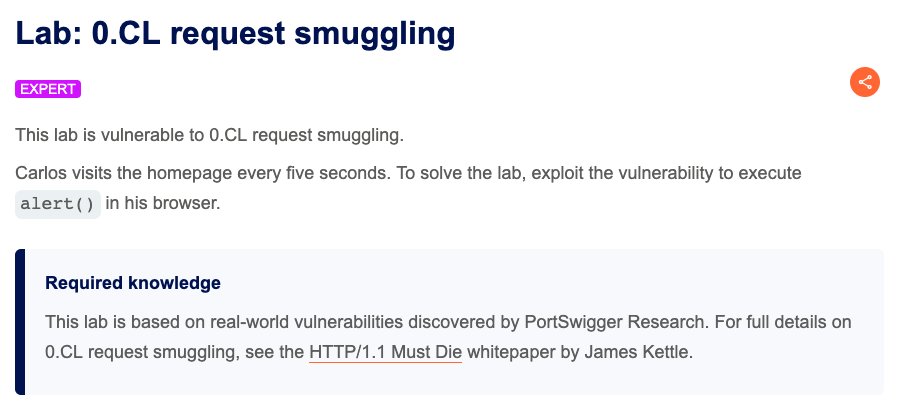
It's been great to see people 'enjoying' the 0CL @WebSecAcademy lab! Tune in this Friday at 11AM PT to watch me livestream the solution with @offby1security - registration link below 👇
Tildar a @Cloudflare de pirata, con o sin comillas, es una vergüenza. @el_pais debéis corregir ese despropósito
ActiveScan++ can now detect multiple advanced unicode exploits just dropped at #BHUSA including confusables, codepoint overflows, case-conversion and combining diacritics! Thanks to researchers @ryancbarnett & @4ng3lhacker for contributing this awesome update.

We should split programming courses in two. In one of them you learn to code and it’s forbidden to use AI. In the other one you have to build an ambicious project in a way that guarantees that you use AI. We need people who know how to code and people who know how to build
the more ambitious you are, the harder it is to feel proud of anything you’ve done
There seem to be two types of engineers. Those who want to solve the problem and those who want to understand the problem. What type are you?
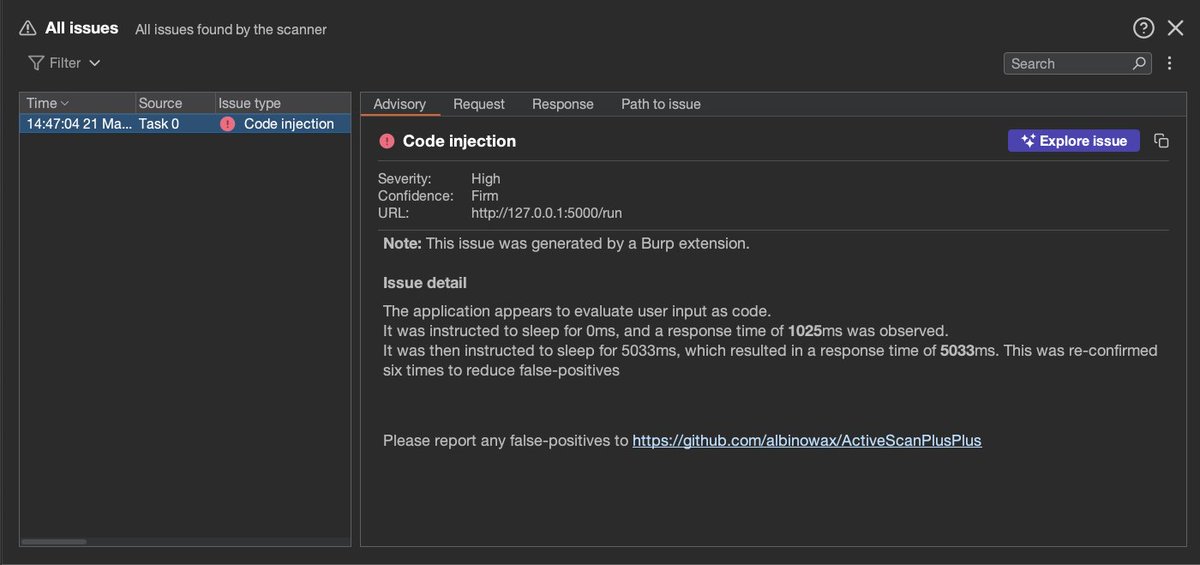
Active Scan++ just got sharper - we’ve added new checks for OS command injection, powered by our latest ASCII Control Characters research. Install via Extensions -> BApp Store
Super excited to share reconftw_ai 🎉 A new tool that reads reconftw results and uses a local LLM (Ollama) to generate actionable reports: bughunter, executive, or brief. It’s lightweight, fast, and helps turn raw recon into insights. Give it a spin! github.com/six2dez/reconf…

United States 트렌드
- 1. #doordashfairy 1,176 posts
- 2. Vanity Fair 67.4K posts
- 3. Susie Wiles 134K posts
- 4. Mustapha Kharbouch 31.7K posts
- 5. Mick Foley 34.8K posts
- 6. Mary and Joseph 2,240 posts
- 7. Olive Garden 1,363 posts
- 8. Larian 12.1K posts
- 9. Brookline 10.8K posts
- 10. Penguins Christmas Party Time N/A
- 11. Snowslingers N/A
- 12. Christensen 6,038 posts
- 13. Michelea Ponce 37.2K posts
- 14. Brand New Day 11.2K posts
- 15. Firefox 6,001 posts
- 16. $TSLA 51.7K posts
- 17. Kay Flock 1,465 posts
- 18. Carville 3,796 posts
- 19. Cardiff 29.4K posts
- 20. Spielberg 30K posts
내가 좋아할 만한 콘텐츠
-
 Alfonso Muñoz, Phd
Alfonso Muñoz, Phd
@mindcrypt -
 BitUp Alicante Ciberseguridad
BitUp Alicante Ciberseguridad
@bitupalicante -
 Honey_SEC
Honey_SEC
@Honey_SEC -
 Eduardo Sánchez
Eduardo Sánchez
@eduSatoe -
 Sec/Admln Cybersecurity Conference
Sec/Admln Cybersecurity Conference
@secadm1n -
 Antonio Sanz
Antonio Sanz
@antoniosanzalc -
 Raul Renales | EA4ITQ
Raul Renales | EA4ITQ
@RaulRenales -
 Nacho Brihuega
Nacho Brihuega
@n4xh4ck5 -
 cr0hn
cr0hn
@ggdaniel -
 Víctor García
Víctor García
@takito1812 -
 Hackron
Hackron
@Hackr0n -
 Luis Vacas de Santos
Luis Vacas de Santos
@CyberVaca_ -
 Cloureiro80
Cloureiro80
@cloureiro80 -
 h-c0n
h-c0n
@h_c0n -
 Joel GM
Joel GM
@JoelGMSec
Something went wrong.
Something went wrong.