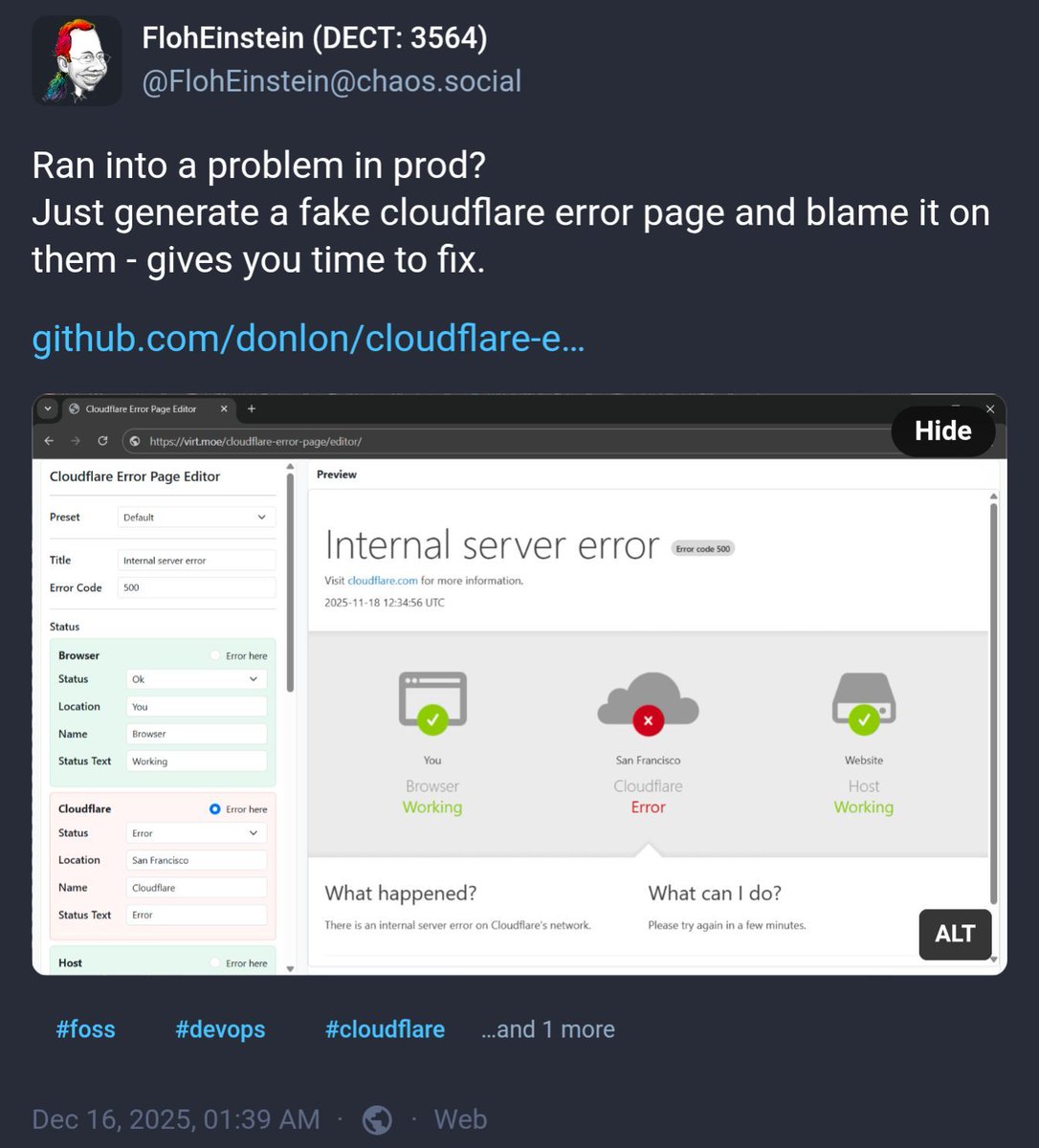
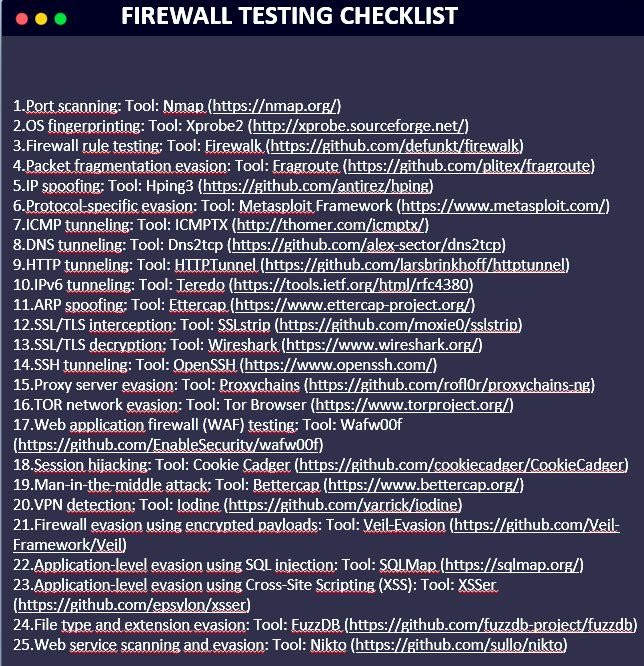
You might like
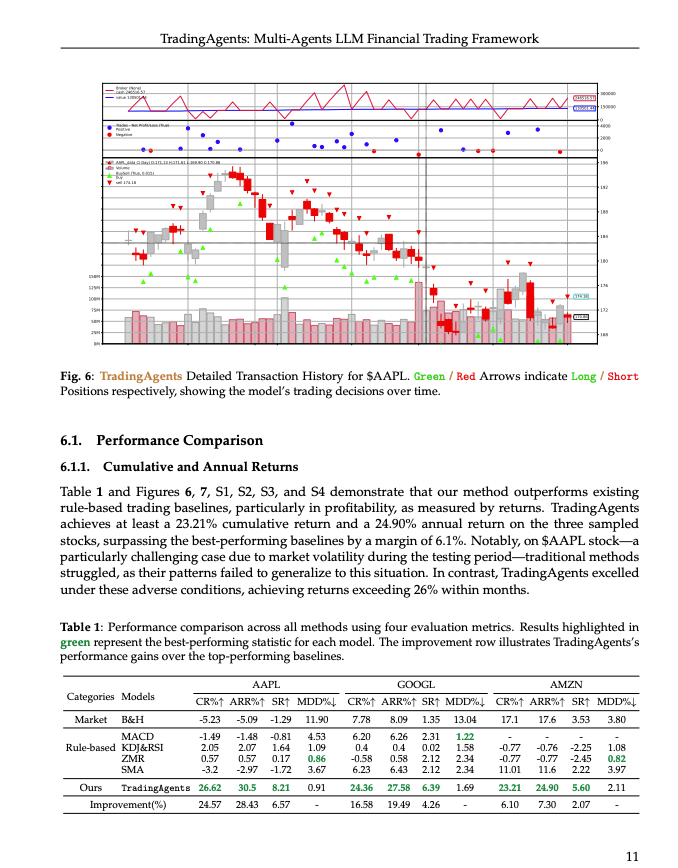
🚨BREAKING: A new open-source multi-agent LLM trading framework in Python It's called TradingAgents. Here's what it does (and how to get it for FREE): 🧵
Critical Vulnerabilities Uncovered in Mitel SIP Phones: Command Injection and File Upload Risks securityonline.info/critical-vulne…
securityonline.info
Critical Vulnerabilities Uncovered in Mitel SIP Phones: Command Injection and File Upload Risks
Two flaws in Mitel SIP phones—CVE-2025-47188 and CVE-2025-47187—enable remote command execution and file uploads, putting enterprise networks at risk.
Linux Security ( Defensive vs Offensive)


what is the purpose of this part of a towel?

Defensive Linux Security

deepseek r1 asked for 1 truly novel insight about humans

Linux find command examples
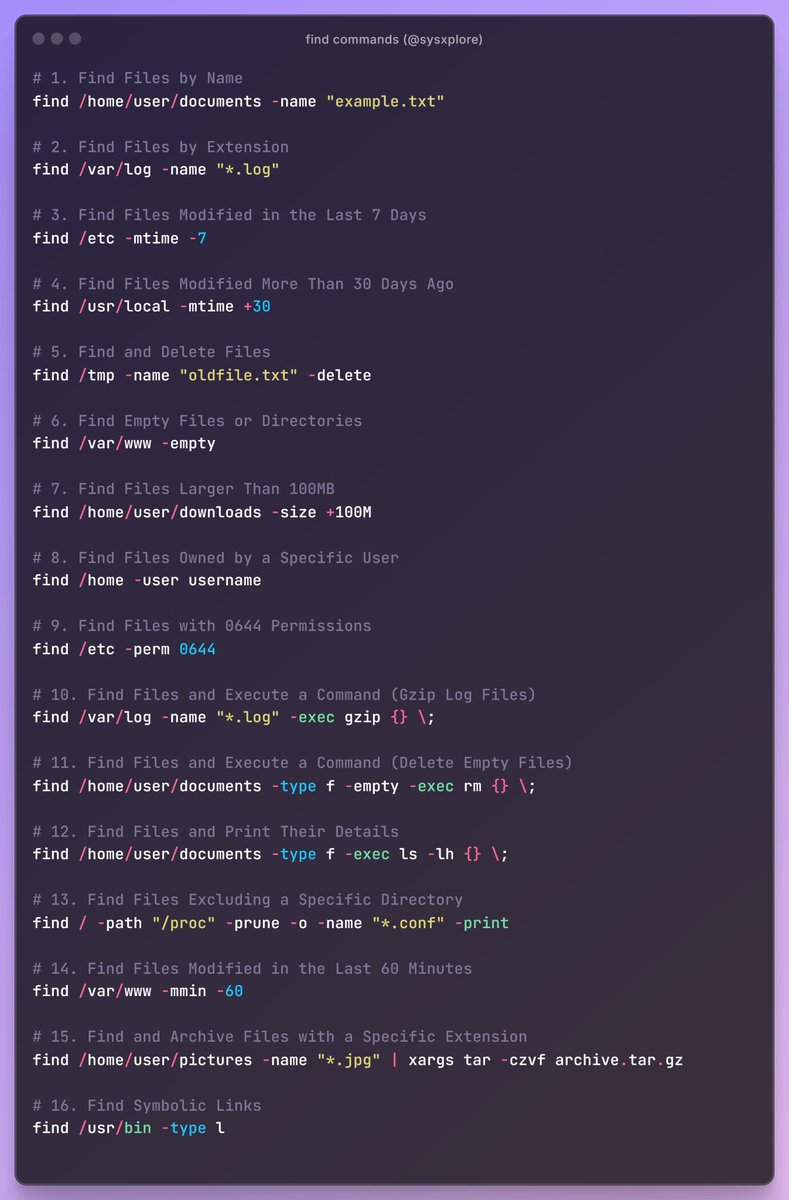
Linux find command - use cases

If this dude isn’t press secretary, it’s a mistake. Enough of the “it must be a woman” trend. Scott does not miss. He is the best of the best, with a track record of tangling with the worst of the worst.
Hello there 👋 If you're learning: - Linux - Networking - Containers - Kubernetes Subscribe to my "no news" newsletter to get in-depth learning materials straight to your inbox newsletter.iximiuz.com
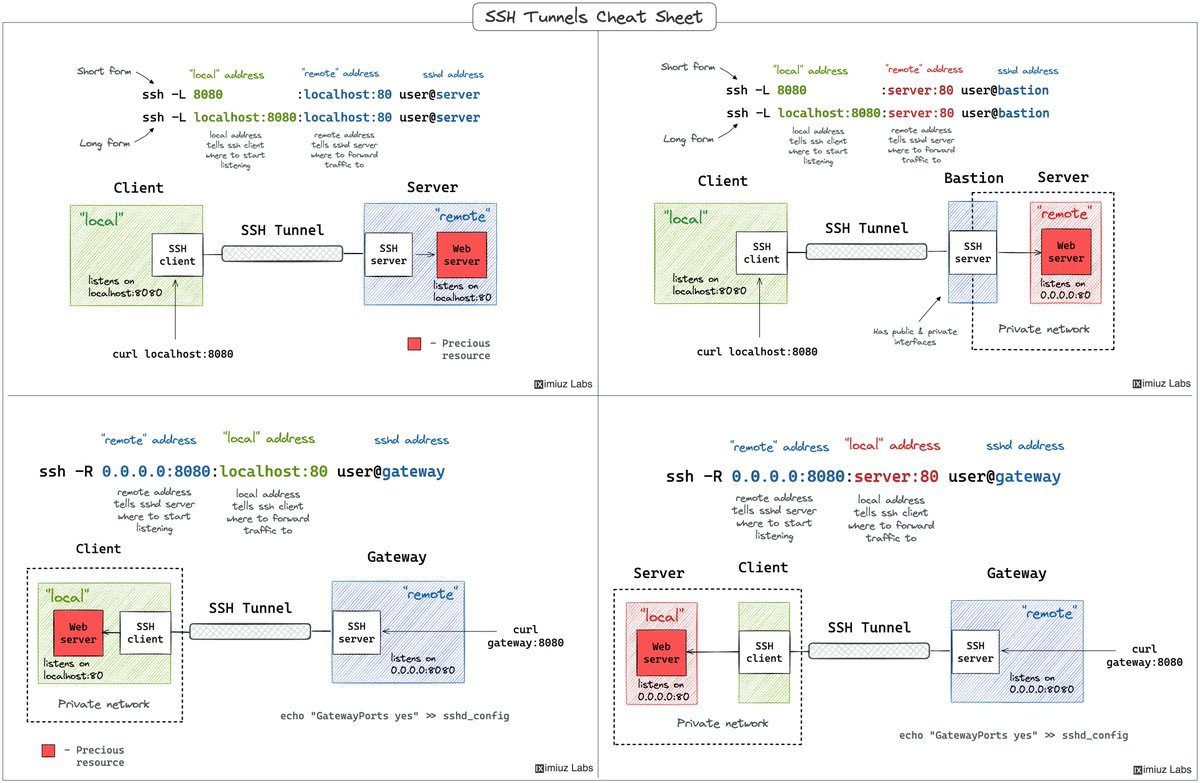
Cybersecurity Certifications Path🎯
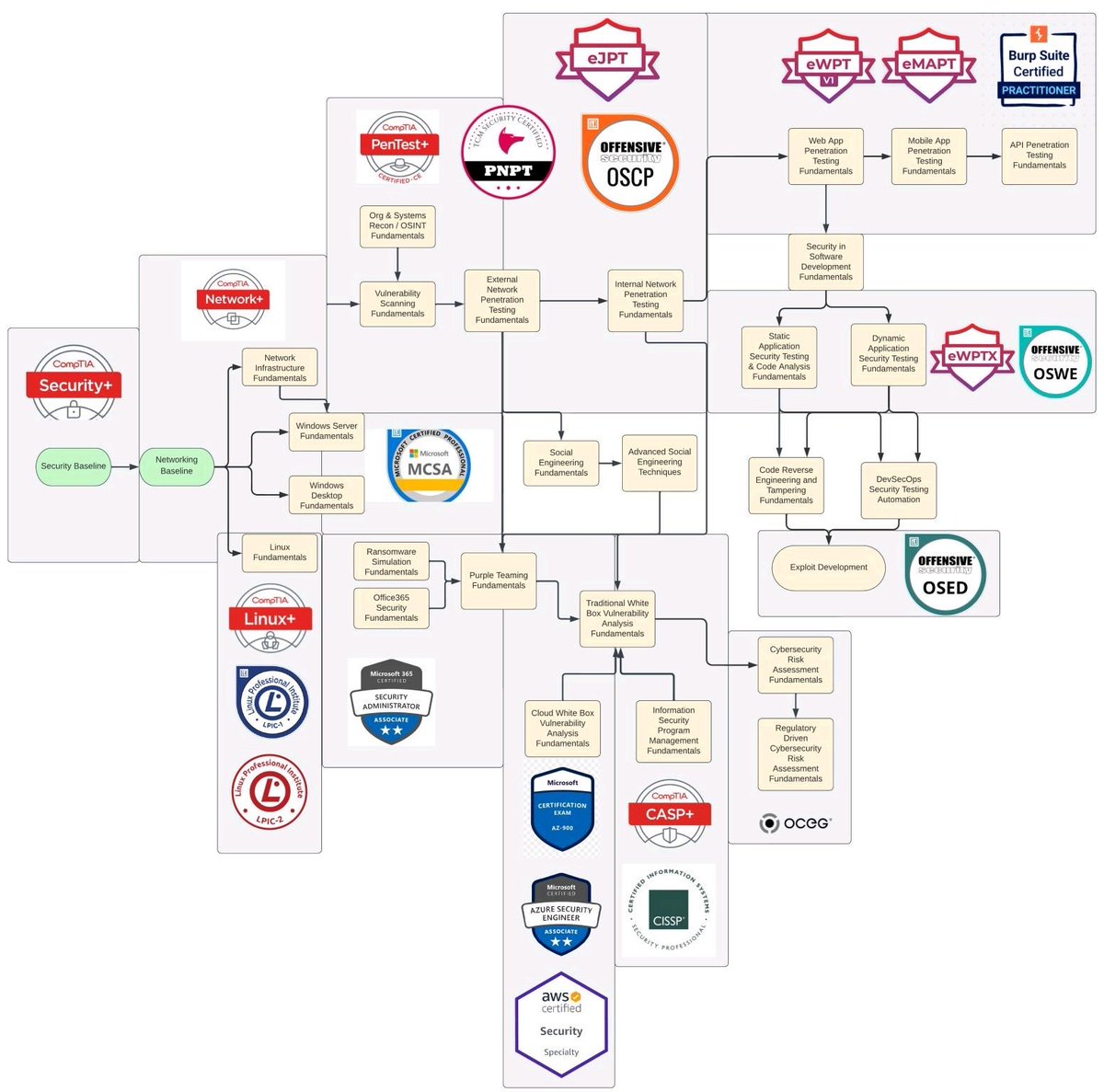
Basic Linux networking commands at a glance
Linux log parsing commands

United States Trends
- 1. Iceland N/A
- 2. TACO N/A
- 3. Speedway N/A
- 4. Davos N/A
- 5. Fermin N/A
- 6. Keon N/A
- 7. Ubisoft N/A
- 8. Jeanie N/A
- 9. The Art of the Deal N/A
- 10. Switzerland N/A
- 11. Gavin N/A
- 12. Pegula N/A
- 13. Ted Cruz N/A
- 14. Swiss N/A
- 15. Lewandowski N/A
- 16. Posey N/A
- 17. Lemonade N/A
- 18. Peralta N/A
- 19. Neto N/A
- 20. Dominguez N/A
Something went wrong.
Something went wrong.