
Noko18
@identity_failed
perpetual n00b
You might like
CyberSec Trends Q4/25🔮 ⬆️NPM/PyPi/VSCode supply chain attacks ⬆️Rust/Go hack tools/malware ↗️EDR Blinding ↗️Abuse of legit RMM tools ↗️Token persistence/cloud API abuse ↗️Malicious LNK files ↗️.NET Single File Host ↗️ClickFix & FileFix ↗️Phishing w/ Job Ads
CyberSec Trends Q1/25🔮 ⬆️Lumma Stealer ↗️EDR killers (vulnerable drivers) ↗️Abuse of legit remote access tools ↗️0days in Fortinet & Ivanti ↗️Token persistence/cloud API abuse ⬆️Sliver implants ⬆️Fake CAPTCHA pages ⬆️Malvertising
🆕 Checkout the blog between @NVISOsecurity & @TeamCymru all about #VShell, which has been used a lot over the last year (over 1,500 servers!), primarily used for long-term espionage activities 🌍🇨🇳 Including NetFlow Analysis 👀 🔗 nviso.eu/blog/nviso-ana…


You’ve heard of the Unix 2038 Problem. I bet you haven’t heard of the GPS 2038 problem. Every GPS navigation device in existence experiences an integer overflow every 19.6 years. Last time, it wiped out iPhones, NOAA weather buoys, and a number of flights in China:


🚨Microsoft 365 Copilot Prompt Injection Vulnerability Allows Attackers to Exfiltrate Sensitive Data Source: cybersecuritynews.com/copilot-prompt…

Life-time access is so back! From now on, individuals can get life-time access to all of our online courses. Learning how specific TTPs work, understanding coding, debugging and troubleshooting is much simpler with video-based content. Check it out - institute.sektor7.net/consumer…

🚨 M365 Copilot Prompt Injection Vulnerability Allows Attackers to Exfiltrate Sensitive Data Read more: cybersecuritynews.com/copilot-prompt… A sophisticated vulnerability in Microsoft 365 Copilot (M365 Copilot) that allows attackers to steal sensitive tenant data, including recent emails,…

Your cybersecurity expert tells you to use two-factor authentication? And they’re right. But until recently, any Android app could steal it just by scanning what’s on your screen. 🤣


“The threat actor exfiltrated files from our BIG-IP product development environment and engineering knowledge management platforms. These files contained some of our BIG-IP source code and information about undisclosed vulnerabilities we were working on in BIG-IP.”
⚠️ Breach Notification from F5 Networks: “In August 2025, we learned a highly sophisticated nation-state threat actor maintained long-term, persistent access to, and downloaded files from, certain F5 systems.” my.f5.com/manage/s/artic…
Hackers just turned GitHub into their command center. When police take down their servers, the malware just… reboots itself from GitHub. The twist? It hides configs inside images using steganography. This isn’t a glitch — it’s resilience by design. Read how it works →…

🚨 Hackers Use DFIR Tool 'Velociraptor' to Attack VMware ESXi and Windows Servers with Ransomware Read more: cybersecuritynews.com/dfir-tool-velo… Ransomware operators are actively exploiting Velociraptor, an open-source digital forensics and incident response (DFIR) tool, in their attacks.…

We are alarmed by reports that Germany is on the verge of a catastrophic about-face, reversing its longstanding and principled opposition to the EU’s Chat Control proposal which, if passed, could spell the end of the right to privacy in Europe. signal.org/blog/pdfs/germ…
.@volatility New Release: #volatility3 v2.26.2 - visit github.com/volatilityfoun… for details and downloads. #memoryforensics #dfir

HTML Smuggling Leads to Domain Wide Ransomware ➡️Initial Access: Thread-Hijacked Email > HTML Attachment ➡️Credentials: LSASS Access, SessionGopher ➡️Lateral Movement: RDP, PsExec ➡️C2: IcedID, Cobalt Strike ➡️Impact: Nokoyawa Ransomware thedfirreport.com/2023/08/28/htm…
CODE WHITE proudly presents #ULMageddon which is our newest applicants challenge at apply-if-you-can.com packaged as a metal festival. Have fun 🤘 and #applyIfYouCan

tl;dr chinas firewall censorship thingy has massive leak. shows code and political ambitions and stuff idk the significance because i dont study chinese network firewall sciency stuff. maybe one of you nerds is interested. its all available for download online now
The Great Firewall of China (GFW) today experienced the largest internal document leak in its history. More than 500GB of source code, work logs, and internal communications have been exposed, revealing details about the development and operation of the GFW. The leak originated…



> 500GB leak of Chinese firewall > Leaked source code > Leaked chat logs > Shows political ambitions and stuff > Look inside > Not made out of fire

We're hiring DFIR consultants (Senior & Principal) for Germany and KSA here at @Unit42_Intel Germany (must be german speaker) - jobs.smartrecruiters.com/PaloAltoNetwor… KSA (must be arabic speaker) - jobs.smartrecruiters.com/PaloAltoNetwor… Let me know if you have questions. Feel free to DM me ✌🏻#dfir
The PDF format is hard to parse - by design. Let's explore the internals of the PDF format to figure out how Adobe did this to us.

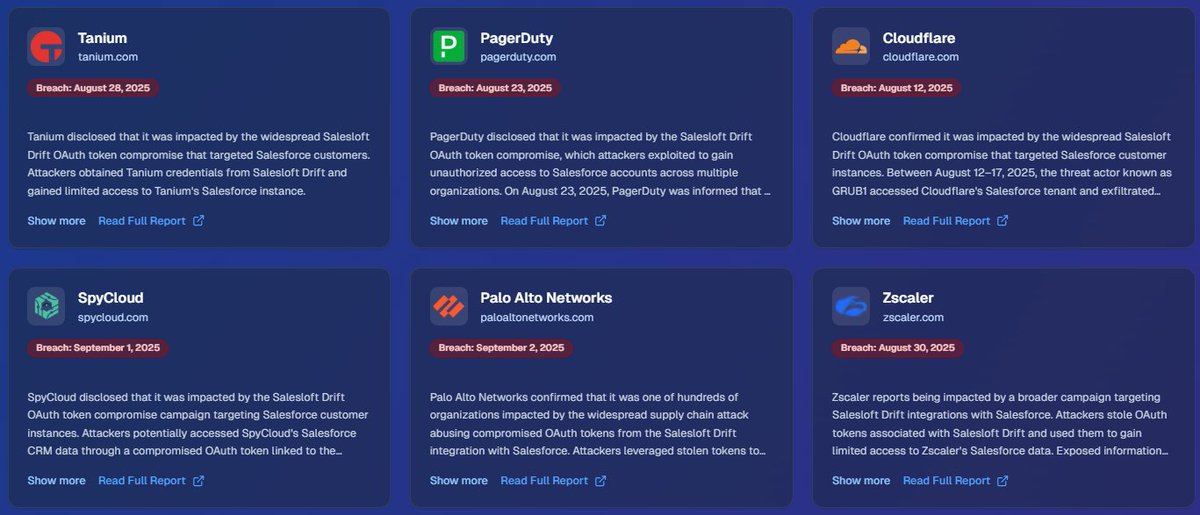
🚨Full list of organizations currently confirmed as victims of the massive Salesloft Drift OAuth token compromise targeting Salesforce integrations Context: In August 2025, UNC6395 exploited compromised OAuth tokens from Salesloft Drift’s Salesforce integration, bypassing MFA…



United States Trends
- 1. Jokic 25.4K posts
- 2. Lakers 53.6K posts
- 3. Epstein 1.65M posts
- 4. #AEWDynamite 49.9K posts
- 5. #River 4,873 posts
- 6. Clippers 14.3K posts
- 7. Nemec 3,296 posts
- 8. Shai 16.4K posts
- 9. #ReasonableDoubtHulu N/A
- 10. Thunder 42.2K posts
- 11. #NJDevils 3,100 posts
- 12. Markstrom 1,249 posts
- 13. Ty Lue 1,103 posts
- 14. #Blackhawks 1,600 posts
- 15. Nemo 8,764 posts
- 16. Lafferty N/A
- 17. Mikey 71.2K posts
- 18. Rory 8,068 posts
- 19. Steph 29.9K posts
- 20. Jordan Miller N/A
You might like
Something went wrong.
Something went wrong.































































































































































