kiddo
@kiddo_pwn
Independent Security Researcher | Pwn2Own 24🇮🇪 25🏎️🇮🇪
내가 좋아할 만한 콘텐츠
My very first blog post is live: kiddo-pwn.github.io/blog/2025-11-3… During research, I've run into and documented a simple universal SQLite Injection RCE trick. Enjoy! N-day Analysis about Synology Beestation RCE (CVE-2024-50629~50631) by legendary DEVCORE 🎃 🍊 Thanks to @u1f383…
My HEXACON talk video is out! It covers a small race condition in the Linux kernel’s io_uring. I recommend watching it at 1.25× speed since I’m still not great at speaking 😅 youtube.com/watch?v=Ry4eOg… Here is the slide! u1f383.github.io/slides/talks/2…
Enjoyed every minute 😄 Hyunwoo Kim (@v4bel) & Wongi Lee (@_qwerty_po) – Race Condition Symphony: From Tiny Idea to Pwnie 🐧🎶 #POC2025

Great talk! Loved it 😄 Mikhail Evdokimov (@konatabrk) – PerfektBlue: Universal 1-click Exploit to Pwn Automotive Industry — Mercedes-Benz, Volkswagen, Škoda, and others 🚗 #POC2025

Master of JSE Samuel Groß (@5aelo) – JavaScript Engine Security in 2025: New Bugs, New Defenses 🌐 #POC2025


I’m first-solver of all challenges today! Go and enjoy getting these SWAGs! 😉

Are you enjoying POC Conference?🎉 We’re running the Squid Game booth located next to the elevator in the VIP room — come check it out! You can try out some traditional Korean games like jegichagi (like hacky sack) and DDakji-chigi (paper tile flipping), as well as an LLM prompt…



Huge thanks for the keynote 💙 It was fantastic. Brian Gorenc (@MaliciousInput) – From Buffer Overflows to Breaking AI: Two Decades of ZDI Vulnerability Research 🎤 #POC2025


There are countless tutorials, blog posts, and workshops on how to exploit a vulnerability. What’s missing is the thought process — how you approach a target, form hypotheses, and ultimately discover a bug. That mindset can’t be fully taught; you have to develop it yourself ;)

For the past 3 years, participating in #Pwn2Own had been a dream for me. I could have never asked for a better debut! All of that would not have been possible without my teammate -and buddy - @kiddo_pwn. His work throughout this time has been outstanding! A huge thanks to all of…

I'm just grateful to continue participating in Pwn2Own - big thanks to @thezdi for me to pursue the independent research 🔥 I'm honored to place 4th as a two-member team among such talented teams - special thanks to my mate @freddo_1337, and congrats to all the other teams🎉…
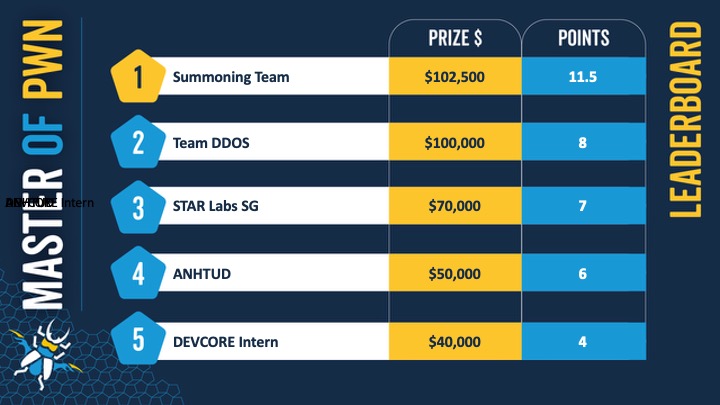
$1,024,750 - 73 unique bugs - a week of amazing research on display. #Pwn2Own Ireland had it all. Success. Failure. Intrigue. You name it. Congratulations to the Master of Pwn winners @SummoningTeam! Their outstanding work earned them $187,500 and 22 point. See you in Tokyo for…

We have another collision! Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS used a single bug to exploit the QNAP TS-453E, but the bug has been previously seen in the contest. Their work still earns them $10,000 and 2 Master of Pwn points. #Pwn2Own


Boom! Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS completed their exploit of the QNAP TS-453E NAS device. They are off to the disclosure room to provide details. #Pwn2Own
I look a bit nervous to chain 8 bugs 😱
Did someone say Bug of the Day? Check out the final results from Day 1 of Trend @thezdi's #Pwn2Own Ireland: spr.ly/6014AALa8
That brings Day 1 of #Pwn2Own Ireland 2025 to a close. We didn't have a single failure today as we awarded $522,500 for 34 unique 0-day bugs. The race for Master of Pwn is heating up, but there's still two days of exploitation to go. Stay tuned for more results! #P2OIreland
💥 BOOM! Team DDOS (@kiddo_pwn & @freddo_1337) get us started right! They needed two attempts, but they successfully demonstrated their SOHO Smashup of the QNAP Qhora-322 + QNAP TS-453E. They head off to the disclosure room to discuss details. #Pwn2Own #P2OIreland
DAMN… so we’re the one-and-only team who succeeded SOHO SMASHUP this year? … Why not? 😎 We’re team DDOS ¯\_(ツ)_/¯ Let me shout-out my amazing buddy @freddo_1337, who put in serious effort to make it happen 😌🔥
Confirmed! Team DDOS (@kiddo_pwn & @freddo_1337) used an octo-symphony of 8(!) different bugs to complete their SOHO Smashup of the QNAP Qhora-322 + TS-453E. They earn themselves $100,000 and 10 Master of Pwn points. #Pwn2Own #P2OIreland

First H1 report! CVE-2025-27212: Pre-auth RCE affecting 6 Ubiquiti Doorcam series is now public (CVSS 9.8 ^_^) Shoutout to my friend @da2Rim for making this research possible and owning a 5-digit bounty 😁 community.ui.com/releases/Secur…

Today @rapid7 is disclosing 8 new printer vulnerabilities affecting 742 models across 4 vendors. After 13 months of coordinated disclosure with Brother Industries, Ltd, we're detailing all issues including a critical auth bypass. Full details here: rapid7.com/blog/post/mult…
United States 트렌드
- 1. Penn State 18.4K posts
- 2. #twitchrecap 12.1K posts
- 3. Romero 21.6K posts
- 4. #TADCFriend 1,482 posts
- 5. Slay 19.5K posts
- 6. Pat Kraft 2,122 posts
- 7. Paul Dano 1,051 posts
- 8. Zion 9,384 posts
- 9. Fulham 44.4K posts
- 10. #GivingTuesday 31.3K posts
- 11. Lewandowski 27.4K posts
- 12. Larry 61K posts
- 13. Adam Thielen 3,859 posts
- 14. Sabrina Carpenter 42.2K posts
- 15. Tarantino 7,380 posts
- 16. Alek Manoah N/A
- 17. Pedri 57.1K posts
- 18. Newcastle 32.8K posts
- 19. Franklin 66K posts
- 20. Rashford 10.6K posts
Something went wrong.
Something went wrong.