DebugPrivilege
@DebugPrivilege
System Administrator | Ex-MSFT | Microsoft MVP in Windows and Devices | Interested in Security, Debugging, and Windows Internals. Tweets are my own.
คุณอาจชื่นชอบ
CISA has ordered federal agencies to patch a high-severity vulnerability in Broadcom's VMware Aria Operations and VMware Tools software, exploited by Chinese hackers since October 2024. bleepingcomputer.com/news/security/…
Over the years, we’ve seen AD attacks that leverage machine accounts (e.g. CVE-2022-26923), whether it’s for privilege escalation or persistence. I put together a blog post about hunting down these machine accounts of interest medium.com/@Debugger/mach…
I have released an OpenGraph collector for network shares and my first blogpost at @SpecterOps on the subject! You can now visualize attack paths to network shares in BloodHound 👀 specterops.io/blog/2025/10/3…
Amazon just announced 14,000 layoffs. Its CEO made over $40M last year. UPS announced 48,000 layoffs. Its CEO made over $24M last year. Intel announced 20,000 layoffs. Its new CEO's pay package is valued at nearly $69M. This is what I mean when I say the system is rigged.
Looks like I will become a farmer soon! Thanks @CISAJen
Ex-CISA head thinks AI might fix code so fast we won't need security teams theregister.com/2025/10/27/jen…
One skill I think everyone should consider mastering is know how to sell and market yourself. Technical skills are nice, but nowadays this is not setting you up for promotion usually. I had to learn it the hard way, so sharing some experiences here 😅
From L5 to 404: Job Not Found

How does everyone feels about AI and do you really think orgs are laying that many people off due to it? I have a feeling it’s not just that, but that the big tech firms have overhired a lot of people as well. Any thoughts?
Recent Layoff Announcements: 1. UPS: 48,000 employees 2. Amazon: Up to 30,000 employees 3. Intel: 24,000 employees 4. Nestle: 16,000 employees 5. Accenture: 11,000 employees 6. Ford: 11,000 employees 7. Novo Nordisk: 9,000 employees 8. Microsoft: 7,000 employees 9. PwC: 5,600…
Been working on some new project to hunt for interesting machine accounts in AD lingering around in an environment.

Can someone grab me a memory dump of the wsuservice.exe and w3wp when exploiting this CVE? Thnx
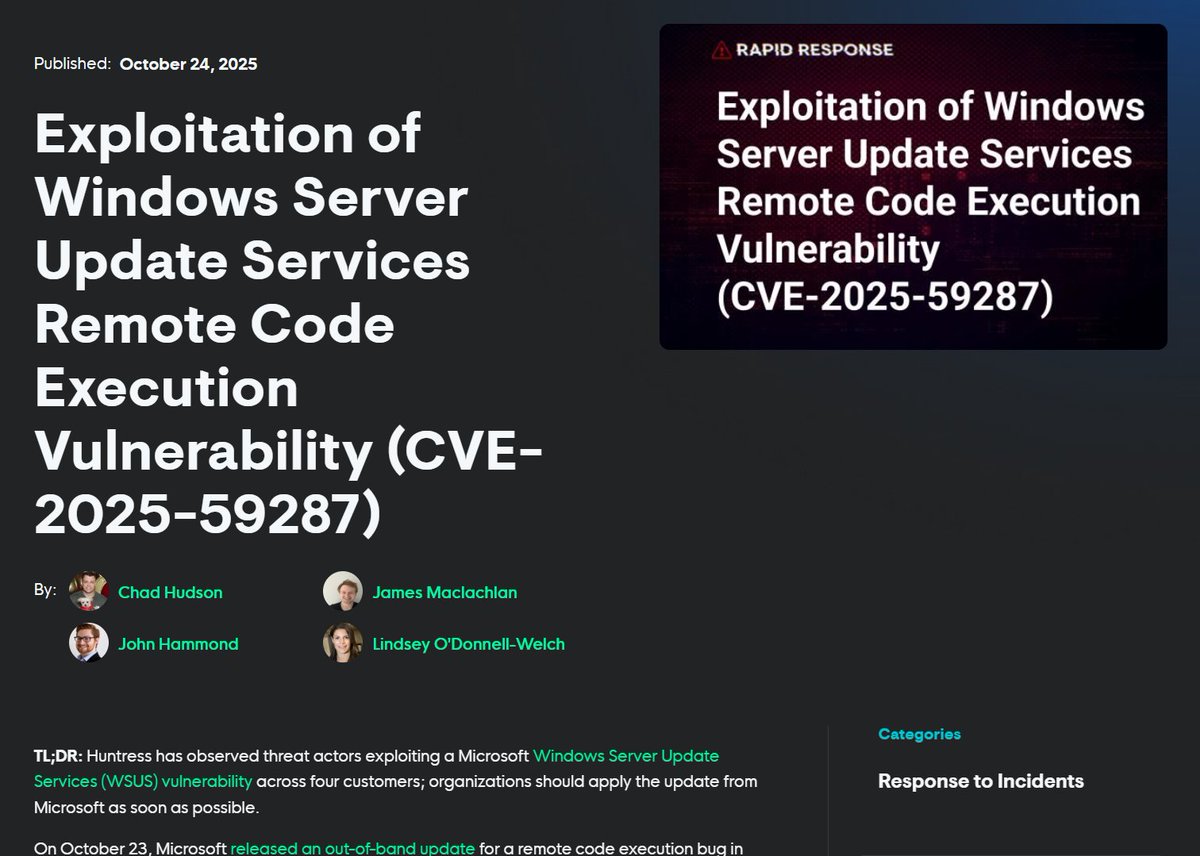
hey hi hello we've been seeing summa dat WSUS sussy baka CVE-2025-59287 remote code execution exploitation windows servers with WSUS ports 8530 & 8531 exposed ( -- why?) getting point-and-shoot popped from a POC already public huntress.com/blog/exploitat… prolly limited ITW…
The next decade of cyber conflict will decide how the world operates. If you want to work on technology that defines the future and makes real impact, come build it with us @XintraOrg xintra.org/jobs


New AD blog post soon of me helping a buddy of mine finding some leftovers during a pentest from years ago lol :P

When was the last time you scanned your AD to find pre-created machine accounts?

Think your Active Directory has “a few” service accounts? Think again. I wrote a super quick blog post on discovering (potential) service accounts via a PS script, how to clean them up, and some monitoring best practices when admins are misusing them. medium.com/@Debugger/we-h…
I hope this video assists those new to TTD. The full blog text is here: whiteknightlabs.com/2025/10/14/mic…
Didn’t read the blog? Watch the video instead. Alan Sguigna dives into WinDbg Time Travel Debugging (TTD) vs. Intel Processor Trace, showing where TTD shines in reverse engineering, exploit analysis, and system introspection. 📺 youtube.com/watch?utm_camp… #WinDbg #TTD #IntelPT

youtube.com
YouTube
WKL - WinDbg Time Travel Debugging (TTD) Functionality
I found it: “By September 2008 we had built a system that screened millions of crashes for security exploits. Along the way I felt like I joined the world’s smallest profession—that of an exploit failure engineer.” web.archive.org/web/2016081818…
Credential Guard was supposed to end credential dumping. It didn't. @bytewreck just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️ ghst.ly/4qtl2rm
United States เทรนด์
- 1. #IDontWantToOverreactBUT 1,303 posts
- 2. Clemens N/A
- 3. #maddiekowalski N/A
- 4. #MondayMotivation 38.3K posts
- 5. Bradley 7,815 posts
- 6. Phillips 505K posts
- 7. Mattingly 2,133 posts
- 8. Victory Monday 4,403 posts
- 9. 60 Minutes 141K posts
- 10. Howie 9,148 posts
- 11. Ben Shapiro 7,426 posts
- 12. Hobi 61.4K posts
- 13. Bonnies N/A
- 14. OpenAI 42.3K posts
- 15. No to Israel 20.7K posts
- 16. Carlos Delgado N/A
- 17. Jeff Kent N/A
- 18. Dale Murphy N/A
- 19. Happy Birthday Kim 1,424 posts
- 20. Donna Jean N/A
คุณอาจชื่นชอบ
-
 inversecos
inversecos
@inversecos -
 /r/netsec
/r/netsec
@_r_netsec -
 DirectoryRanger
DirectoryRanger
@DirectoryRanger -
 Nicolas Krassas
Nicolas Krassas
@Dinosn -
 The DFIR Report
The DFIR Report
@TheDFIRReport -
 S3cur3Th1sSh1t
S3cur3Th1sSh1t
@ShitSecure -
 ςεяβεяμs - мαℓωαяε яεsεαяςнεя
ςεяβεяμs - мαℓωαяε яεsεαяςнεя
@c3rb3ru5d3d53c -
 Grzegorz Tworek
Grzegorz Tworek
@0gtweet -
 Will Schroeder
Will Schroeder
@harmj0y -
 Dr. Nestori Syynimaa
Dr. Nestori Syynimaa
@DrAzureAD -
 Andrew Thompson
Andrew Thompson
@ImposeCost -
 Olaf Hartong
Olaf Hartong
@olafhartong -
 Mehmet Ergene
Mehmet Ergene
@Cyb3rMonk -
 Kostas
Kostas
@Kostastsale -
 Thomas Roccia 🤘
Thomas Roccia 🤘
@fr0gger_
Something went wrong.
Something went wrong.