Bunları beğenebilirsin
Read about kernel sanitizers, powerful detection features that can uncover bugs in kernel-mode components, and how they enable Microsoft engineering teams to identify and fix vulnerabilities earlier in the software development cycle: msft.it/6014eCpbq
CVE-2022-23088: A new guest blog from @m00nbsd describes a 13-yr-old heap overflow in the Wi-Fi stack that allows network-adjacent attackers to execute code on affected installations of FreeBSD Kernel. Includes root cause & PoC. Read the details at zerodayinitiative.com/blog/2022/6/15…
Kernel RCE in #FreeBSD via WiFi frames: freebsd.org/security/advis… Also affects #pfSense / #OPNsense / etc
Dudes, you don't seem to have noticed there are some nicer big-ass vulns in that hypervisor. This one for example, host stack r/w overflow, full VM escape, and no, retguard does not mitigate it. #OpenBSD

OPENBSD_6_9 bluhm@ modified usr.sbin/vmd/virtio.c: vmd guests can trigger excessive log messages on the host by sending certain network packets. this is errata/6.9/001_vmd.patch.sig
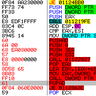
Ah lol so I'm not the only one who developed KASAN for #FreeBSD: cgit.freebsd.org/src/commit/?id… I didn't release my impl and rather piled up the vulns I found with it, old pic related. A lot of crazy kernel vulns.

The recent ICMPv6 stuff in Windows reminded me I still had similar BSD vulns in my garage, so here we go Remote use-after-free in #OpenBSD via ICMPv6: ftp.openbsd.org/pub/OpenBSD/pa… Remote use-after-free in #FreeBSD via ICMPv6: lists.freebsd.org/pipermail/free… RCE possible in the first one.
Trivial VM escape in #Bhyve: if you're a guest, allocate a GPA, use a VMLOAD+RDMSR probe to determine its HPA, use SKINIT to reinit the CPU core at that HPA. The CPU core restarts and executes your instructions in host mode. That's it, you're the host.

OPENBSD_6_9 bluhm@ modified usr.sbin/vmd/virtio.c: vmd guests can trigger excessive log messages on the host by sending certain network packets. this is errata/6.9/001_vmd.patch.sig
A new guest blog with an excellent analysis from @m00nbsd shows a fast and smooth privilege escalation exploit in #FreeBSD. His write-up includes PoC and a video demo. Read the details at bit.ly/3jAjnwW
by the way there's some real savage VM escape in #Bhyve, guest can take complete control of the host -- exploit is crazy, but easy!
and six months later some of them are still not fixed
I guess I should one day publish my "NetBSD Privileged Kernel" research on #NetBSD, here for example running the motherboard's SMM in a container to protect the kernel from firmware vulns and backdoors


reversing your bios is fun and all, until you realize there's a bugdoor in it

ah, so they finally found CVE-2019-5608, one less item in my collection I guess
my network security work in #NetBSD is still having an effect, it seems support.apple.com/en-us/HT210090

United States Trendler
- 1. #BUNCHITA 1,399 posts
- 2. #SmackDown 45.4K posts
- 3. Tulane 4,301 posts
- 4. Giulia 14.6K posts
- 5. Aaron Gordon 3,893 posts
- 6. Frankenstein 77.7K posts
- 7. Supreme Court 181K posts
- 8. #TheLastDriveIn 3,797 posts
- 9. Russ 13.7K posts
- 10. Connor Bedard 2,929 posts
- 11. #TheFutureIsTeal N/A
- 12. #OPLive 2,248 posts
- 13. Podz 3,018 posts
- 14. taylor york 7,858 posts
- 15. Caleb Wilson 5,760 posts
- 16. Northwestern 5,029 posts
- 17. Scott Frost N/A
- 18. Justice Jackson 5,570 posts
- 19. Tatis 2,069 posts
- 20. Keon 1,175 posts
Bunları beğenebilirsin
-
 Moshe Kol
Moshe Kol
@0xkol -
 Hex-Rays SA
Hex-Rays SA
@HexRaysSA -
 maxpl0it
maxpl0it
@maxpl0it -
 Alex Plaskett
Alex Plaskett
@alexjplaskett -
 G. Geshev
G. Geshev
@munmap -
 Alexander Popov
Alexander Popov
@a13xp0p0v -
 Karsten
Karsten
@gr4yf0x -
 stephen
stephen
@_tsuro -
 ohjin
ohjin
@pwn_expoit -
 Julio Merino
Julio Merino
@jmmv -
 OpenBSD
OpenBSD
@openbsd -
 Mathias Krause | @[email protected]
Mathias Krause | @[email protected]
@_minipli -
 John Aakerblom
John Aakerblom
@jaakerblom -
 Theori
Theori
@theori_io -
 Mike Larkin
Mike Larkin
@mlarkin2012
Something went wrong.
Something went wrong.