
Rohit
@rajwansi_rohit
IIT Bombay EE'23 Tupac Hackurr
You might like
NATS vs Kafka: Why NATS might be your secret weapon 🚀 Kafka = distributed log with complex broker management, ZooKeeper/KRaft, partition rebalancing headaches. NATS = pure messaging with zero dependencies, single binary, runs in 10MB RAM. Key differences: Kafka persists…

Mai Hara tabhi jeet ke bhi Aetha na, Jaha haara waha judge ban baitha Raa..
After you've spent years doing backend engineering, you realise that everything is a wrapper: - an API endpoint is a wrapper over a controller - a controller is a wrapper over business logic - a business logic is a wrapper over a service class - a service class is a wrapper over…
You're a backend developer. Someone asks you: "Why should we use caching like Redis instead of querying the database every time?" How do you answer? Here are the 5 clearest reasons 👇
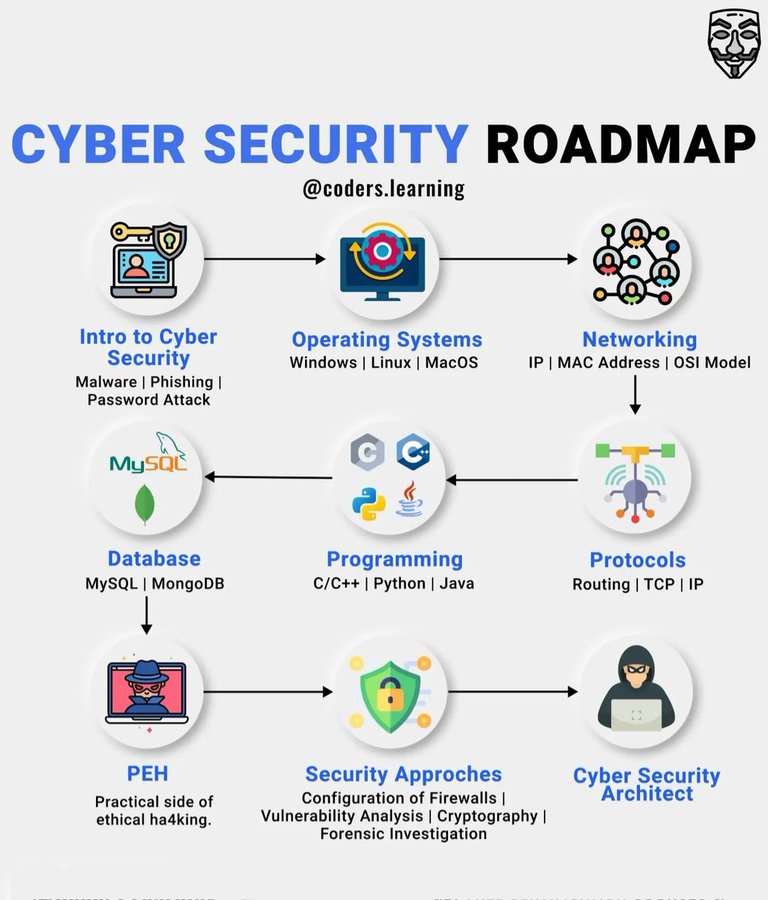
Free Online Cybersecurity Courses and Certifications in 2025. Here are 15 FREE courses to help you master Cybersecurity 👇👇 1. IBM Cybersecurity Analyst Professional Certificate 🔗imp.i384100.net/Y9x7eO 2. Microsoft Cybersecurity Analyst Professional Certificate 🔗…
𝗛𝗧𝗧𝗣 𝘃𝘀 𝗛𝗧𝗧𝗣𝗦: 𝗪𝗵𝗮𝘁'𝘀 𝘁𝗵𝗲 𝗱𝗶𝗳𝗳𝗲𝗿𝗲𝗻𝗰𝗲? The difference is encryption. HTTP sends data in plain text. HTTPS wraps that data in TLS encryption. When you visit a site over HTTP, anyone monitoring the network can read everything: passwords, credit card…

☁️ AWS Roadmap → Beginner to Job-Ready 1️⃣ Start Here EC2 • S3 • IAM • VPC • CloudWatch (These 5 are 80% of real AWS work) 2️⃣ Hands-On Basics • Launch EC2 • Create S3 buckets • Set IAM Roles • Build a basic VPC 3️⃣ Serverless Skills • Lambda functions • API Gateway •…
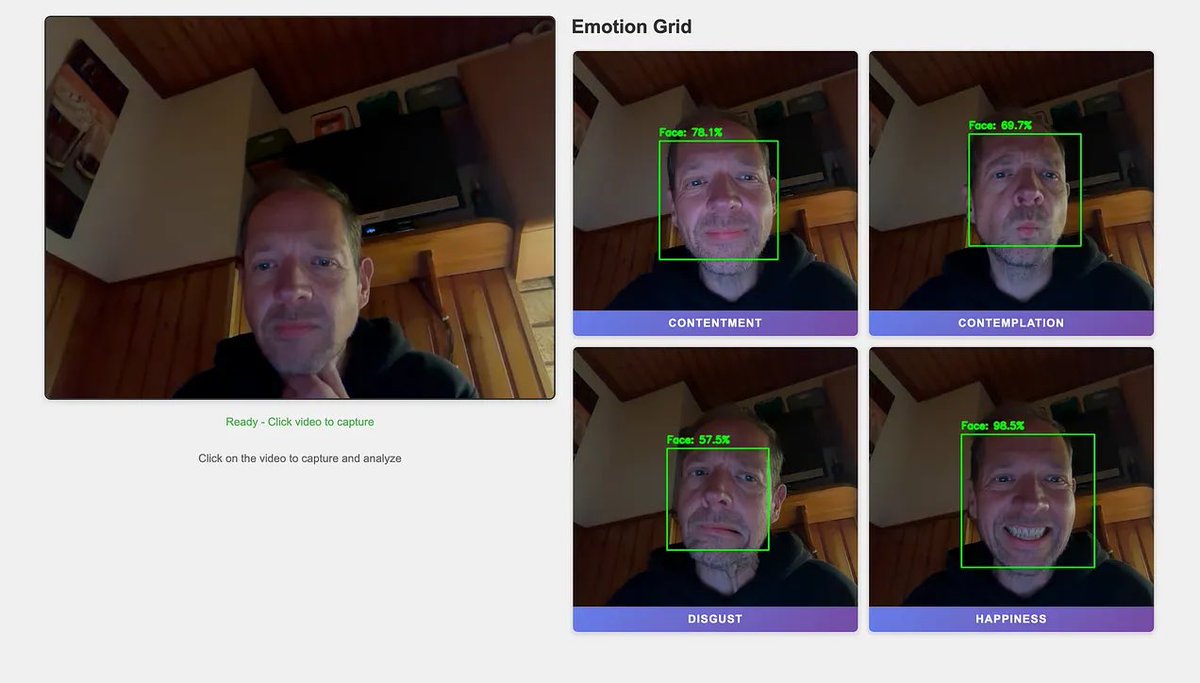
Built a fun real-time AI demo this week: Webcam → #JavaCV face detection → #LangChain4j multimodal emotion analysis → Live overlay in the browser. buff.ly/Xa9Mwpa #Java #Quarkus
The following are the materials I used to pass my CISSP; Udemy Courses 1. CISSP Domain 1 and 8 2025 certifications boot camp by Thor Pedersen - Lead trainer at ThorTeaches . After taking each courses, I took the easy-mid practice questions, hard practice questions and complex…
Alice and Bob are good friends and want to exchange messages securely. Alice receives a message from Bob. What key does Alice use to decrypt the encrypted message she received? A. Bob’s public key B. Bob’s private key C. Alice’s private key D. Alice’s public key
You don’t need microservices. You need paying customers. Scaling problems are good problems because they mean success. Too many teams over-engineer before they have real demand. Before breaking things into microservices, ask: • Do we have performance bottlenecks, or just…

Did You Know? When you hit "Delete" on a file, it doesn't actually leave your hard drive. The OS just deletes the entry in the "Table of Contents" and marks that space as "Available." The actual data sits there, 100% intact and readable, until a new file happens to overwrite…
SSL management in k8s is a must-know workflow for DevOps engineers. In every project, You will have to deal with TLS certificates. It could be public or internal certificates. One of the best ways to manage SSL in Kubernetes is by using cert-manager. It automates the…

Can’t speak for AWS but I fixed the cold start issue in GCP by having my Cloud Run using request-based pricing + min 0 instances + a scheduled empty request every 10 minutes to keep the instance warm yet as no real request went it, not to be charged for it being up
We went serverless to reduce costs. Lambda, API Gateway, DynamoDB. Clean architecture. Modern stack. Six months later: - Cold starts were killing user experience - DynamoDB was 3x more expensive than RDS would have been - Debugging required piecing together logs from 12…
I’ve gotten > 5 free certs this year. I did this by: 1. Interning at a company that partners with the certification company (CompTIA Partner, Google Cloud Partner) 2. Entering voucher giveaways from @AZGingerHacker and testforless.store/security (Ian Neil)
testforless.store
Security+ | Testforless
Security+ | Testforless
There are so many free resources and ways to get free certifications. Workforce development programs. Certification vendors like Microsoft, Oracle, Amazon, Salesforce, ServiceNow etc giving free certs. Individuals giving away free certs.
In college, I always struggled with ACID properties in DBMS. I knew the full form. Atomicity, Consistency, Isolation, Durability. But honestly, none of it made sense to me back then. I only understood it properly years later, while working on real systems at Cisco. Let me…
What is salting and why do we salt passwords?
My favorite XSS payloads: - <svg onload="a=domain,b=confirm,c=window,c.onerror=b;throw a"> - <svg id=javascript:alert(1) onload=location=id> - <0 name="<svg/onload=alert()>"> - <cool/onpointermove=(confirm)(1)>MoveMouseHere Sorry, I forgot the original source for credit.
Candidates are often confused when asked: Whats the difference between rate limiting and throttling? The difference is actually very simple. 1. Rate Limiting This sets a fixed maximum number of requests. If you go beyond that limit, the extra requests are blocked. Example: 100…
United States Trends
- 1. FIFA 363K posts
- 2. The WET 117K posts
- 3. FINALLY DID IT 438K posts
- 4. Paraguay 28.3K posts
- 5. Brazil 80.5K posts
- 6. Argentina 232K posts
- 7. Frank Gehry 4,462 posts
- 8. Portugal 105K posts
- 9. Hep B 15.9K posts
- 10. Matt Campbell 11.2K posts
- 11. Warner Bros 246K posts
- 12. Morocco 68.6K posts
- 13. Croatia 25.4K posts
- 14. Iowa State 9,529 posts
- 15. #Mundial2026 41.5K posts
- 16. Group L 18.1K posts
- 17. Infantino 75.8K posts
- 18. #USMNT 1,443 posts
- 19. Ghana 85.4K posts
- 20. Sherman 4,694 posts
You might like
-
 Jay Sawant
Jay Sawant
@jaisawant309 -
 Navneet Prabhat
Navneet Prabhat
@NavneetPrabhat -
 Durgesh Ahire
Durgesh Ahire
@Ah1re_Durgesh -
 Rikin Shah
Rikin Shah
@theSHAHshow18 -
 Kritin Garg
Kritin Garg
@GargKritin -
 NCC IIT Bombay
NCC IIT Bombay
@NCC_IIT_Bombay -
 Narayan Rangaraj
Narayan Rangaraj
@NarayanRangaraj -
 Ipsit Mantri
Ipsit Mantri
@SriIpsit -
 Ganesh Ramakrishnan
Ganesh Ramakrishnan
@ganramkr -
 Industrial & Systems Engineering IIT Kharagpur
Industrial & Systems Engineering IIT Kharagpur
@DeptISEIITKGP -
 Rohit Chaudhary
Rohit Chaudhary
@eRohitChaudhary -
 Chinmay Bharti
Chinmay Bharti
@chhinna00 -
 Ayush Nopany
Ayush Nopany
@AyushNopany -
 shades.ai
shades.ai
@shaxxanx
Something went wrong.
Something went wrong.





























































































