你可能會喜歡
We found a Remote Code Execution (RCE) vulnerability in @Ollama - one of the most popular AI inference projects on GitHub. Here is everything you need to know about #Probllama (CVE-2024-37032) 🧵👇

🔥 Curious how we exploited CVE-2025-49844 (RediShell)? From a 2-bit reset to 0-click RCE. Come see me at Hexacon 2025 - Paris, where I’ll share in-depth technical details on the exploitation. See you on Friday 👋 #Redis #Security #RediShell @hexacon_fr

In case you missed it: $4.5M in bounties (up to $300k per target!) are up for grabs for open source software in the zeroday.cloud competition 🤯 We've partnered with all major cloud providers to offer massive rewards and recognize vulnerability research excellence 🎯

Excited to be a part of #ZeroDayCloud on the floor at Black Hat Europe this year. Let's work together to help secure open-source.
Introducing ZERODAY.CLOUD🕵️♀️ Be the first to participate in the first-of-its-kind cloud hacking competition. 🤝 WIN PRIZES from our 4.5M$ prize pool. 💰 Register your exploit > zeroday.cloud @msftsecresponse @awscloud @googlecloud
Google Cloud is excited to be part of an event that focuses on OSS and will help improve security for all Cloud users:
Introducing ZERODAY.CLOUD🕵️♀️ Be the first to participate in the first-of-its-kind cloud hacking competition. 🤝 WIN PRIZES from our 4.5M$ prize pool. 💰 Register your exploit > zeroday.cloud @msftsecresponse @awscloud @googlecloud
For the first time ever, @awscloud, @msftsecurity, @googlecloud and @wiz_io Research are joining forces to launch zeroday.cloud at @BlackHatEvents EU! 🤯 Find critical vulns in open-source cloud software & get paid from our $4.5M prize pool👇 zeroday.cloud
Introducing ZERODAY.CLOUD🕵️♀️ Be the first to participate in the first-of-its-kind cloud hacking competition. 🤝 WIN PRIZES from our 4.5M$ prize pool. 💰 Register your exploit > zeroday.cloud @msftsecresponse @awscloud @googlecloud
🚨 New CTF challenge just dropped: This one's going to hurt your brain (in the best way) Our researcher @galnagli has created the *trickiest* puzzle yet in our Ultimate Cloud Security Championship. He packed half a dozen advanced bug bounty techniques into one mind-bending…

Fascinating talk by @benny_isaacs and Brakha about their beautiful exploit of a UAF vulnerability in the Redis Lua interpreter at the recent Pwn2Own. A must-watch! 🤩
📢 From 2-Bit Reset to 0-Click RCE in Redis: A Pwn2Own Edition by Benny Isaacs (@benny_isaacs) & Nir Brakha

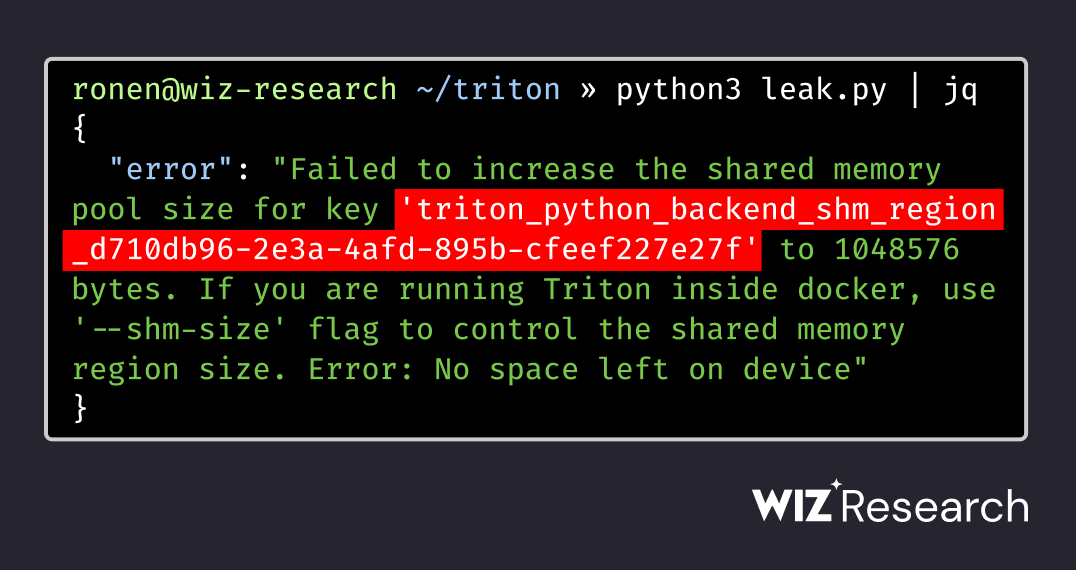
We (+@nirohfeld) found a critical vulnerability chain in NVIDIA's Triton Inference Server (CVE-2025-23319) that can lead to full Remote Code Execution (RCE). An unauthenticated attacker can remotely take over the server, a cornerstone of many AI/ML production environments. 🧵
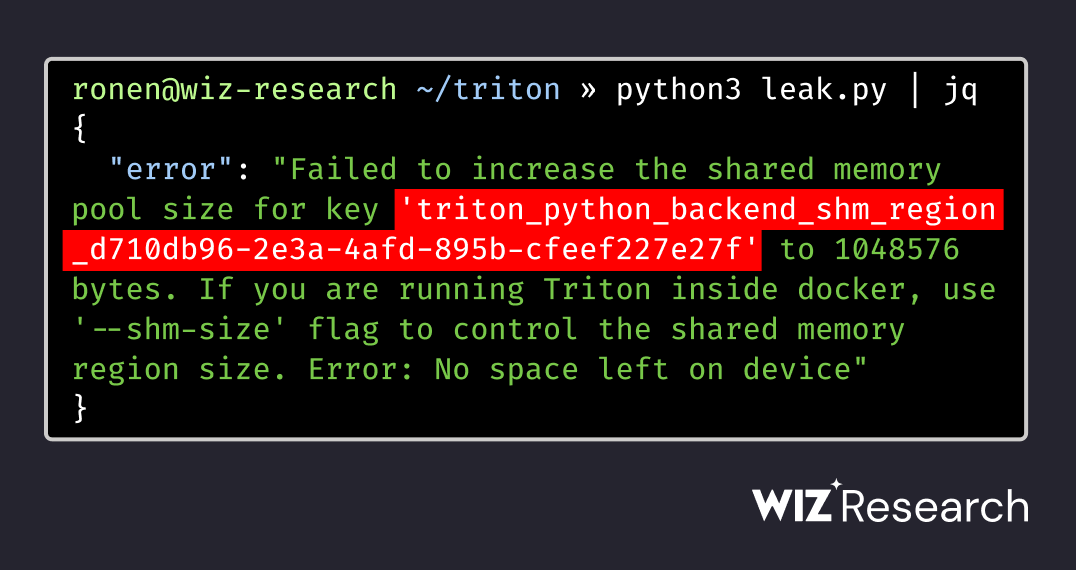
We (+@ronenshh) hacked NVIDIA's Triton AI server by abusing a single error message🚨 The result is unauthenticated RCE allowing attackers to compromise the server and steal proprietary AI models🤯 For more details & mitigations check out our blog @wiz_io wiz.io/blog/nvidia-tr…
When we asked @sagitz_ to create a container escape challenge, we honestly didn't believe he'd go this far 😲 The result is a really cool challenge that requires lots of creativity and solid technical skills. Think you got what it takes? 💫 cloudsecuritychampionship.com/challenge/2
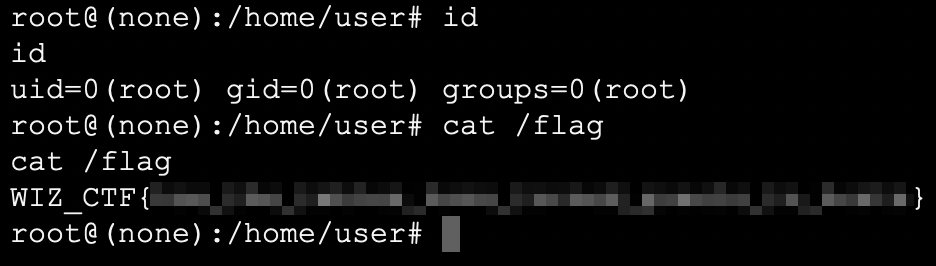
Are you up for a challenge? I authored a container security challenge for the @wiz_io Ultimate Cloud Security Championship 🤩 Put your skills to the test and try it out! 👇 cloudsecuritychampionship.com/challenge/2
🏆 Can you escape a container & become THE ULTIMATE CLOUD SECURITY CHAMPION? This month's scenario was crafted by @sagitz_ to explore container escape techniques, the same kind of risks we'll be diving into at @BlackHatEvents ! Challenge #2 👉 cloudsecuritychampionship.com/challenge/2

I hacked a popular vibe coding platform with a simple, straight-forward logic flaw - allowing access to private applications . Here’s how I did it 🧵

🚨 TraderTraitor: North Korea's cyber "traitor" inside the crypto world. This hacking crew hijacks dev workflows, poisons open-source, and compromises cloud environments — all to steal billions in crypto. Here's how they do it 🧵

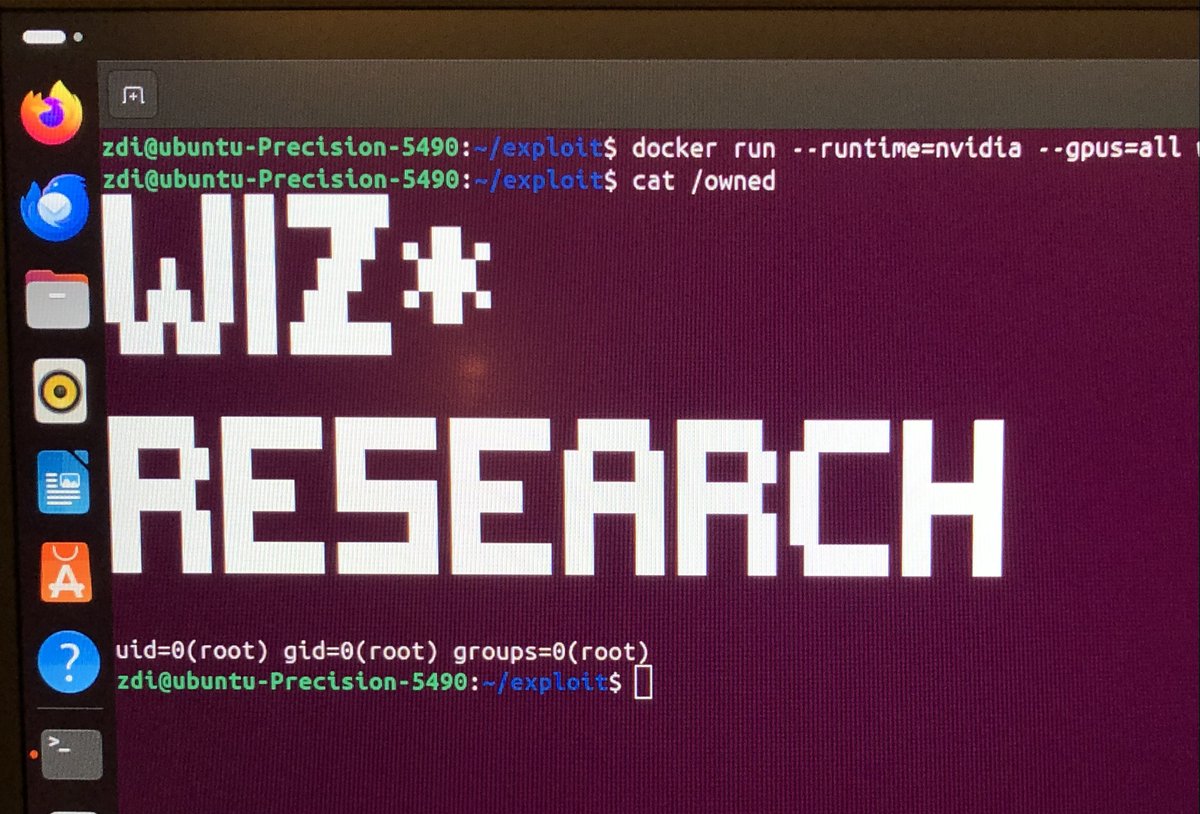
We found a new container escape affecting all container runtimes using @NVIDIA GPUs. The crazy part? The exploit is just three lines long 🤯 This is the story of #NVIDIAScape 🧵👇
Something I’m incredibly proud of is finally live. We've launched the Cloud Security Championship: a 12-month series of deep-dive challenges, each crafted by a different top Wiz researcher. The first challenge is up. Go! cloudsecuritychampionship.com
Most points in the AI category at the recent @thezdi Pwn2Own! 🥳
🏆 Wiz Research took 1st place in #Pwn2Own's first-ever AI category, competing against global teams targeting critical AI infrastructure. Huge thanks to our incredible research team! @nirohfeld, @shirtamari, @ronenshh, @benny_isaacs, @sagitz_ & Nir Brakha!

Amazing! Nir Ohfeld (@nirohfeld) Shir Tamari (@shirtamari) of Wiz Research used a External Initialization of Trusted Variables bug to exploit the #NVIDIA Container Toolkit. This unique bug earns them $30,000 and 3 Master of Pwn points.


Double whammy! Nir Ohfeld (@nirohfeld) Shir Tamari (@shirtamari) of Wiz Research kick off their Day 3 with an exploit of the NVIDIA Container Toolkit. They weren't confident, the their exploit hit on the first try. Off to the disclosure room with them. #Pwn2Own

United States 趨勢
- 1. Good Sunday 44.9K posts
- 2. Discussing Web3 N/A
- 3. Auburn 46.8K posts
- 4. #sundayvibes 3,946 posts
- 5. MACROHARD 7,822 posts
- 6. Gilligan's Island 5,145 posts
- 7. Brewers 66.5K posts
- 8. Wordle 1,576 X N/A
- 9. #SEVENTEEN_NEW_IN_TACOMA 38.5K posts
- 10. #MakeOffer 20K posts
- 11. QUICK TRADE 2,147 posts
- 12. Kirby 24.5K posts
- 13. #SVT_TOUR_NEW_ 30.6K posts
- 14. Boots 50.7K posts
- 15. FDV 5min 2,188 posts
- 16. #HawaiiFB N/A
- 17. Utah 25.1K posts
- 18. Holy War 1,990 posts
- 19. Dissidia 7,175 posts
- 20. mingyu 108K posts
你可能會喜歡
-
 Nir Ohfeld
Nir Ohfeld
@nirohfeld -
 Shir
Shir
@shirtamari -
 Check Point Research
Check Point Research
@_CPResearch_ -
 Wiz
Wiz
@wiz_io -
 Yuval Avrahami
Yuval Avrahami
@yuvalavra -
 ptr-yudai
ptr-yudai
@ptrYudai -
 Ami Luttwak
Ami Luttwak
@amiluttwak -
 Ronen Shustin
Ronen Shustin
@ronenshh -
 Connor McGarr
Connor McGarr
@33y0re -
 mj0011
mj0011
@mj0011sec -
 Ivan Fratric 💙💛
Ivan Fratric 💙💛
@ifsecure -
 Alex Plaskett
Alex Plaskett
@alexjplaskett -
 Nick Frichette
Nick Frichette
@Frichette_n -
 Bruno
Bruno
@bkth_ -
 Mikhail Klyuchnikov
Mikhail Klyuchnikov
@m1ke_n1
Something went wrong.
Something went wrong.








































































































































