Sarah Yoder
@sarah__yoder
Incident Response @Mandiant. Former MITRE ATT&CKer.
Potrebbero piacerti
Earlier this year, I worked one the most interesting and complex IRs of my career. The malware and techniques from that case turned out to be key TTPs observed in multiple subsequent UNC5221 cases! cloud.google.com/blog/topics/th…
🔥new blog detailing 0day exploitation of Ivanti appliances as well as newly observed malware families tracked as PHASEJAM and DRYHOOK. We also detail activity related to the previously observed SPAWN malware ecosystem tied to China nexus cluster UNC5337. cloud.google.com/blog/topics/th…
Today, @Mandiant published #MTrends2024, the 15th edition of the report. This report has everything - Frontline Intel Metrics, Hot Zero-Day Summer, Attackers Living on the Edge, insights into☁Threats, evolution of 🎣... Get your copy here: cloud.google.com/security/resou…
it's always dns and/or caching until you're behind a corporate ssl inspection appliance. then it's always ssl certificates.
Check out @Mandiant’s latest hardening and remediation guide for orgs impacted by the recent ConnectWise #ScreenConnect vulns (CVE-2024-1708 and CVE-2024-1709) mandiant.com/resources/blog…
LockBit ransomware gang disrupted by global operation dlvr.it/T2zG6G
Every single known Lockbit ransomware group website is either offline or displaying a seized by EUROPOL page. It appears law enforcement has seized and/or taken down, at minimum, 22 Tor sites, in what is labeled 'Operation Cronos'.


Lockbit when they're compromised

🔥new @Mandiant blog off the press digging further into our findings from Ivanti CS exploitation. Part 2 covers some new malware families, more on ZIPLINE, updates to attribution, and a bit on mitigation bypassing and new post-ex TTPs. mandiant.com/resources/blog…
UNC4990 - The first malicious threat actor Mandiant has tracked that's based out of Italy - employs some tactics we haven't seen before. mandiant.com/resources/blog…

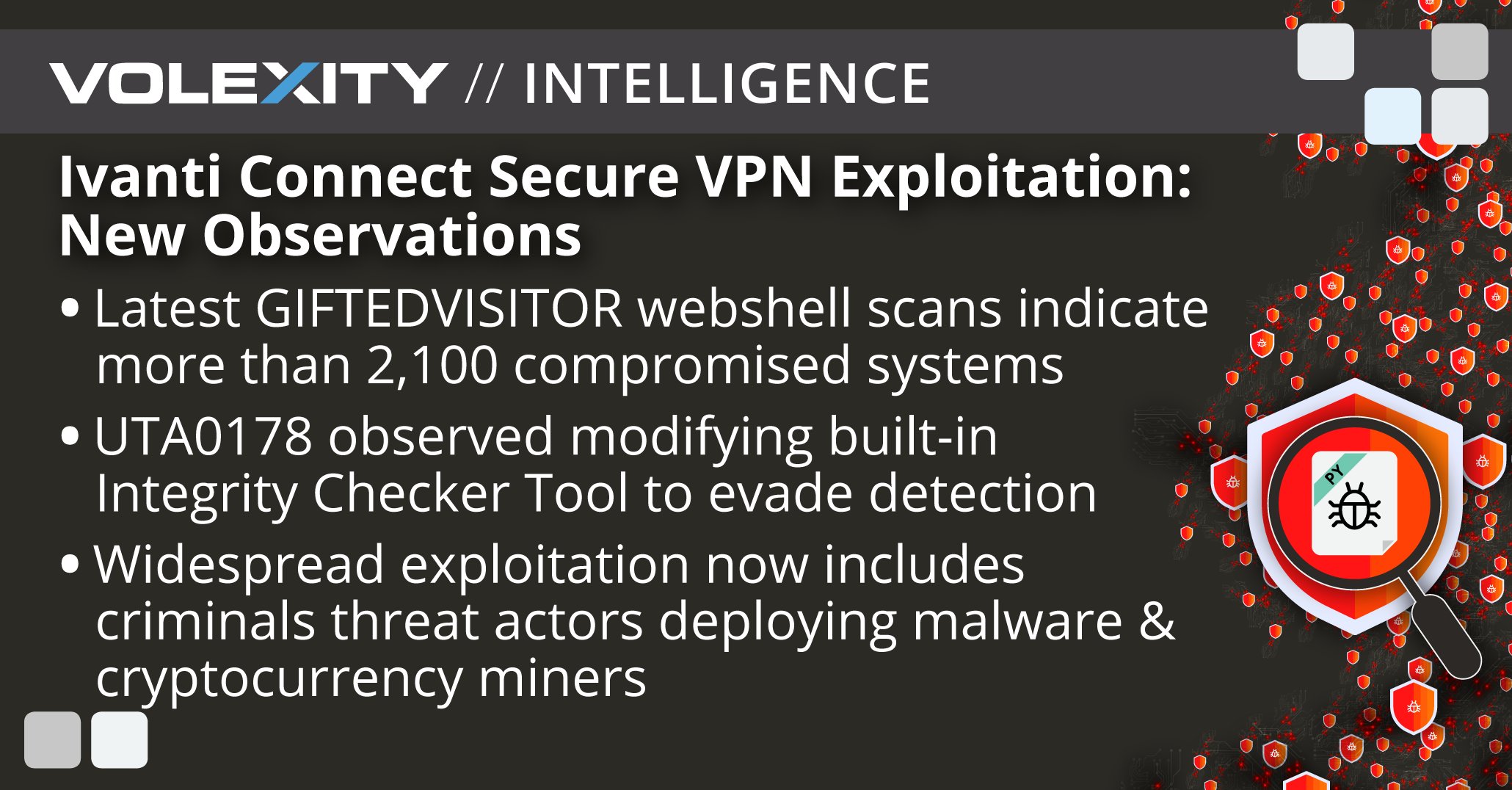
.@Volexity shares new observations on cont'd widespread exploitation of Ivanti Connect Secure VPN vulnerabilities. Now, 2100+ compromised devices & UTA0178 observed modifying built-in Integrity Checker Tool to evade detection. Details: volexity.com/blog/2024/01/1… #dfir #threatintel
Every single known Lockbit ransomware group website is either offline or displaying a seized by EUROPOL page. It appears law enforcement has seized and/or taken down, at minimum, 22 Tor sites, in what is labeled 'Operation Cronos'.


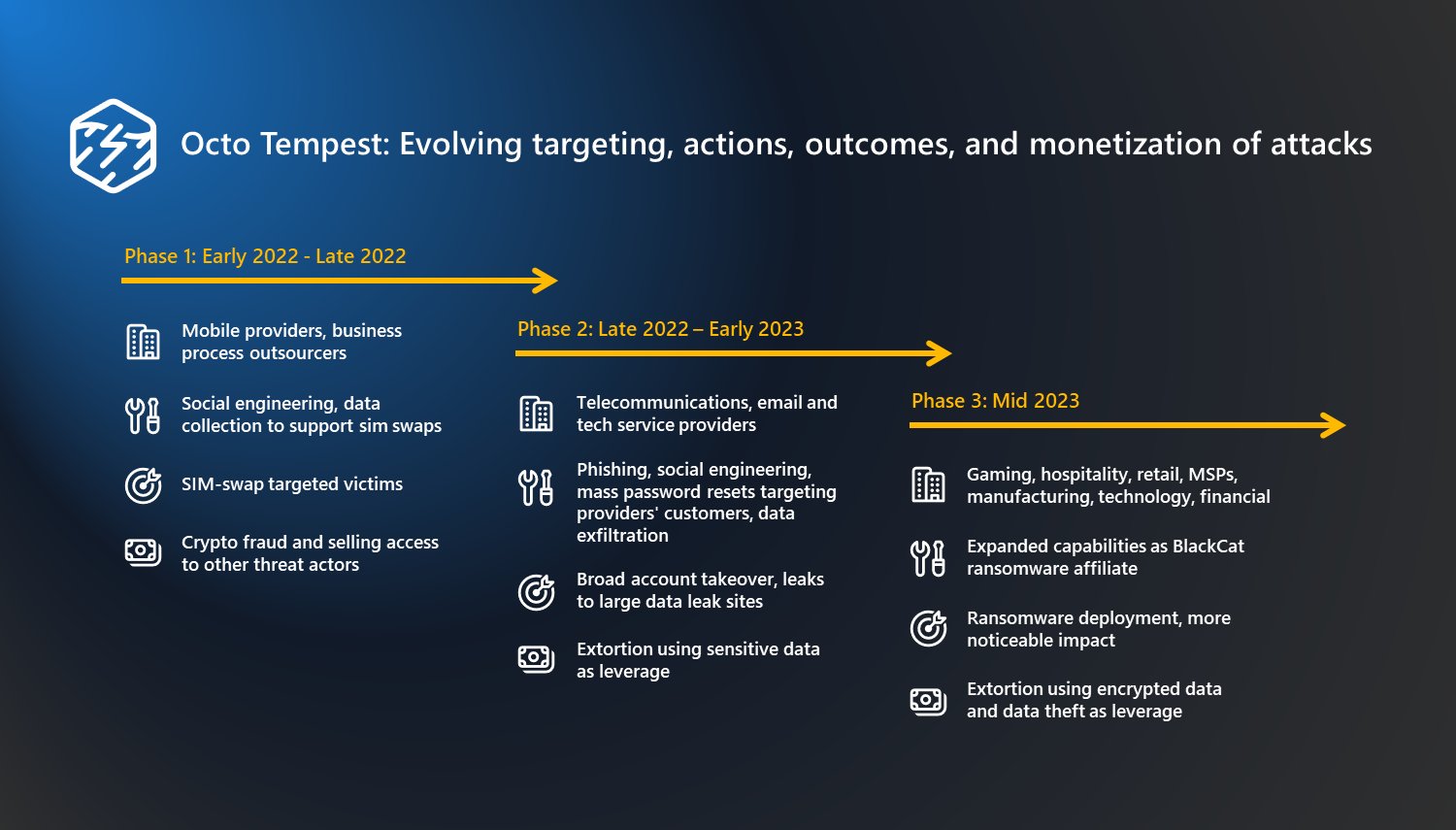
The financially motivated threat actor tracked by Microsoft as Octo Tempest, whose evolving campaigns leverage tradecraft not seen in typical threat models, represents a growing concern for organizations. Get TTPs and protection info: msft.it/60129Lhkw
🚨 NetScaler vulnerability CVE-2023-4966 is being actively exploited. It can lead to VDI session hijacking, including MFA bypass. There are no logs on the appliance to monitor for exploitation. Upgrade now and investigate your environment! mandiant.com/resources/blog… #DFIR
Our blog on UNC3944, a threat actor involved in several recent attacks on the hospitality sector and other industries. Includes actor methods and mitigations. mandiant.com/resources/blog…
🎯#Qakbot Botnet Takedown in Operation Duck Hunt! 💻 700,000 Victim Computers 💰 $8.6m in cryptocurrency seized by DOJ 💰 Qakbot has earned $58m in ransoms 🔒 Qakbot used by Conti, ProLock, Egregor, REvil, MegaCortex, and Black Basta ransomware groups justice.gov/usao-cdca/pr/q…
Today we launched a 🔎 scanning tool for orgs to search their Citrix netscalers for evidence of CVE-2023-3519 post-exploration. You can run this direct on the ADC or against a forensic image. With public POCs out there expect more exploitation! mandiant.com/resources/blog… #DFIR
United States Tendenze
- 1. $NVDA 76.8K posts
- 2. Jensen 24.7K posts
- 3. Peggy 38.5K posts
- 4. GeForce Season 5,803 posts
- 5. NASA 54.5K posts
- 6. #ใครในกระจกEP5 9,430 posts
- 7. Sumrall 2,426 posts
- 8. #YIAYalpha N/A
- 9. Stargate 7,116 posts
- 10. #WickedWaysToMakeABuck N/A
- 11. Martha 20K posts
- 12. Arabic Numerals 4,223 posts
- 13. #WWESuperCardNewSeason 1,156 posts
- 14. Kwame 6,564 posts
- 15. Comey 58.2K posts
- 16. Saba 11K posts
- 17. Poverty 54.3K posts
- 18. #2Kgiveaway 1,154 posts
- 19. Sam Harris N/A
- 20. Judge Smith 2,893 posts
Potrebbero piacerti
-
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 Adam Pennington
Adam Pennington
@_whatshisface -
 Toni Gidwani
Toni Gidwani
@t_gidwani -
 Dan Perez
Dan Perez
@MrDanPerez -
 Ryan K
Ryan K
@meansec -
 Andreas Sfakianakis / @[email protected]
Andreas Sfakianakis / @[email protected]
@asfakian -
 Jose Rodriguez 🇵🇪
Jose Rodriguez 🇵🇪
@Cyb3rPandaH -
 J⩜⃝mie Williams
J⩜⃝mie Williams
@jamieantisocial -
 nick
nick
@3dRailForensics -
 Matthew Dunwoody
Matthew Dunwoody
@matthewdunwoody -
 Frank Duff
Frank Duff
@FrankDuff -
 Drunk Binary
Drunk Binary
@DrunkBinary -
 Steve Stone
Steve Stone
@stonepwn3000 -
 Dr. Ch33r10
Dr. Ch33r10
@Ch33r10 -
 Mark Parsons
Mark Parsons
@markpars0ns
Something went wrong.
Something went wrong.