Security4all
@security4all
Cyber security specialist, based in APAC. My tweets are my own.
You might like
2nd round of #JSAC2026 Call for Presentations and Workshops is now open until 17 Nov 2025. We look forward to your submissions. ^YU jsac.jpcert.or.jp/en/cfp.html
After a long hiatus into the world of ITWs, I present my research on Mangyongdae and its importance to the #DPRK Cyber-Warfare machine. Included are new ITW indicators, alongside analysis of recent developments within the district. We also found Unit 91. cyberbladesecurity.com/the-pyongyang-…
We’re excited to share how we do attribution within @Unit42_Intel and I’m extremely proud of the team for putting in the work behind the scenes to make this happen. unit42.paloaltonetworks.com/unit-42-attrib…
Hopefully yall enjoy small charts of #NorthKorean IT worker accounts. Today, it's a post-minions assessment.
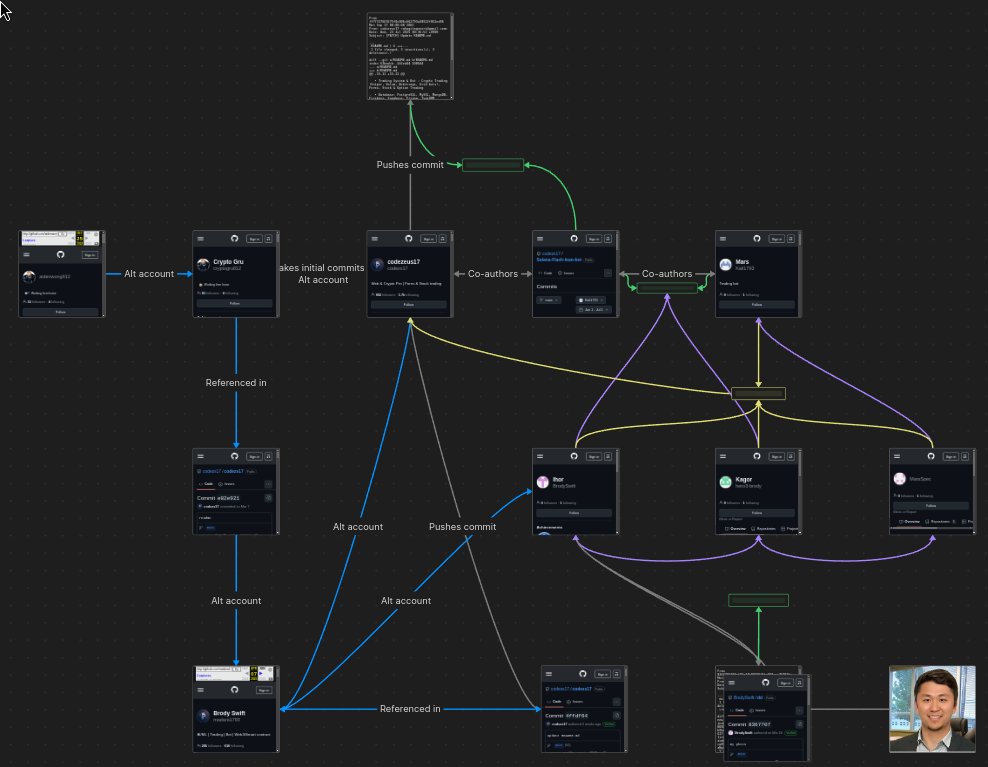
🇰🇵Kim Pyong Hyok🇰🇵 Works blockchain. Has Japanese clients. Uses Freelancer[.]com. Has the scariest email ever. Tags with Hermes. Emai: seatiger9847 @ gmail Hermes000000 Tanaka Brandon Maxim Isayev
![browsercookies's tweet image. 🇰🇵Kim Pyong Hyok🇰🇵
Works blockchain. Has Japanese clients. Uses Freelancer[.]com. Has the scariest email ever. Tags with Hermes.
Emai: seatiger9847 @ gmail
Hermes000000
Tanaka Brandon
Maxim Isayev](https://pbs.twimg.com/media/GwgjrsbbEAEZyOL.jpg)
![browsercookies's tweet image. 🇰🇵Kim Pyong Hyok🇰🇵
Works blockchain. Has Japanese clients. Uses Freelancer[.]com. Has the scariest email ever. Tags with Hermes.
Emai: seatiger9847 @ gmail
Hermes000000
Tanaka Brandon
Maxim Isayev](https://pbs.twimg.com/media/GwgjxRLboAAX0QI.png)
![browsercookies's tweet image. 🇰🇵Kim Pyong Hyok🇰🇵
Works blockchain. Has Japanese clients. Uses Freelancer[.]com. Has the scariest email ever. Tags with Hermes.
Emai: seatiger9847 @ gmail
Hermes000000
Tanaka Brandon
Maxim Isayev](https://pbs.twimg.com/media/Gwgl31RbEAUNpAw.png)
Microsoft is sharing details from ongoing investigations of threat actors exploiting vulnerabilities targeting on-premises SharePoint servers. Linen Typhoon, Violet Typhoon, and Storm-2603 have been observed exploiting the vulnerabilities: msft.it/6015sE1p5
Excited to see another threat intel focused conference taking place in Europe, and it’s organized by threat analyst in the field! The CFP is opened until Sept 1st. Looking forward to see your amazing research! #What_is_SOS #StateOfStatecraft
State of Statecraft (SOS) is a new security and intelligence conference purposed to bring together observers of espionage, sabotage, influence, and other unique forms of covert statecraft to share their work with a community hyper-focused on tackling state-sponsored ops.

📣 Researchers, analysts, and strategists — The #StateOfStatecraft CFP is OPEN! Share your work on espionage, intelligence, and global affairs. ⏳ Submit before the deadline: stateofstatecraft.com/cfp #InternationalRelations #Strategy #OSINT
State of Statecraft (SOS) is a new security and intelligence conference purposed to bring together observers of espionage, sabotage, influence, and other unique forms of covert statecraft to share their work with a community hyper-focused on tackling state-sponsored ops.

Check out our new book, now available: Cyber GRU. Russian military intelligence in cyberspace lab52.io/blog/new-book-… #Russia #GRU

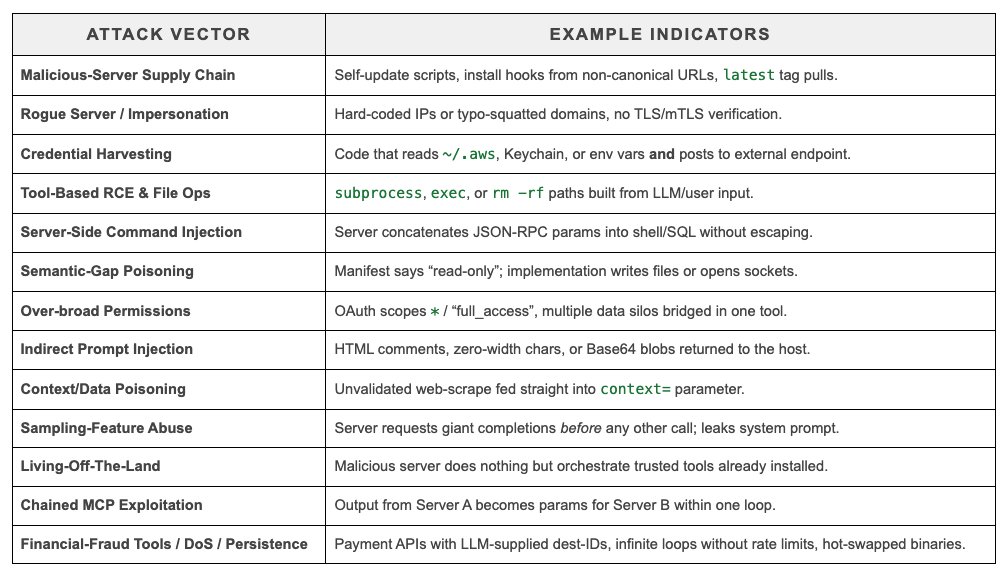
⚠️ VirusTotal flagged 1,408 potentially malicious MCP servers! They ran an audit using Gemini 2.5 Flash + Code Insight: - They collected 17,845 projects via GitHub API - Scored them based on real implementation signals - Analyzed them with LLMs to detect vulnerable or malicious…
Don't let your data fall into the wrong hands. Nation-Sponsored cybersecurity activity presents a real threat to organizations of all sizes. Safeguard your networks: go.dhs.gov/wzx

🚨 GangExposed just dropped another bomb on the ransomware world. They’ve released profile photos of 15 members of the notorious Conti ransomware group, including their lead negotiator Arkady Valentinovich Bondarenko. This follows recent leaks that exposed: •“gg” — the central…

We’ve analyzed thousands of leaked internal chats from Conti, Trickbot, and Black Basta—three of the most destructive ransomware groups to date. Key insights from our investigation: •428 hospitals targeted by Conti during the pandemic •Real-world identities of key leaders like…
=^._.^= New blog post: Katz Stealer - a credential and data stealer with everything a modern infostealer needs: process hollowing, UAC bypass, headless browser injection, and a mild dislike for CIS locales We broke it down from gzip to clipboard exfil, mapped the infection…




BREAKING: Internal #DeepSeek database publicly exposed 🚨 Wiz Research has discovered "DeepLeak" - a publicly accessible ClickHouse database belonging to DeepSeek, exposing highly sensitive information, including secret keys, plain-text chat messages, backend details, and logs.

I’m not sure people realize what they actually need to do. Once a 0day goes public and at least one threat actor has used it to exploit thousands of devices - and then a list of affected systems leaks - PATCHING IS NOT ENOUGH. If you take security seriously, you must run a…
🚨New blog:APT32 used GitHub to distribute a Cobalt Strike exploit plugin containing a Trojan, targeting cybersecurity professionals. ThreatBook identified this attack event in November 2024 and located the attacker's GitHub account.threatbook.io/blog/id/1100 #APT32 #OceanLotus
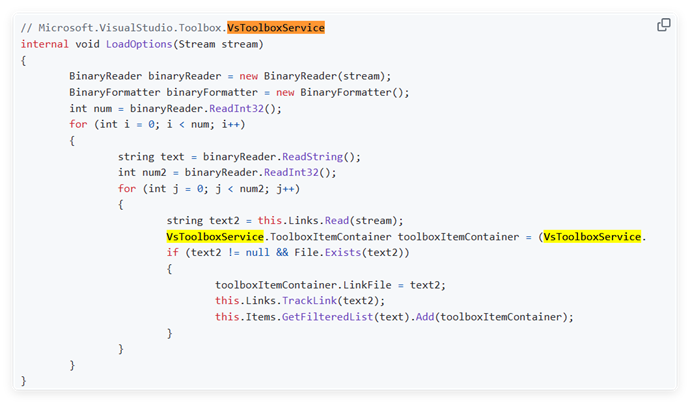

Very interesting screenshot in the latest FBI arrest of the main LockBit developer “Rostislav Panev” Source code for LockBit builders for #Proxmox and #Nutanix, which have not been observed in the wild AFAIK 🧐 justice.gov/opa/media/1381…

Full program for #JSAC2025 has been just published! Check it out on the event website! ^YU jsac.jpcert.or.jp/en/timetable.h…
🆒 New Blog! Cyber Threat Intelligence for Autodidacts 🔗 blog.bushidotoken.net/2024/10/cyber-…


United States Trends
- 1. Good Sunday 57K posts
- 2. Klay 24.7K posts
- 3. McLaren 103K posts
- 4. #sundayvibes 4,508 posts
- 5. Lando 135K posts
- 6. #FelizCumpleañosPresidente 3,019 posts
- 7. #FelizCumpleañosNico 3,174 posts
- 8. #AEWFullGear 72.8K posts
- 9. For the Lord 29.8K posts
- 10. Ja Morant 11.2K posts
- 11. Oscar 127K posts
- 12. Piastri 76.1K posts
- 13. Max Verstappen 66.9K posts
- 14. #LasVegasGP 231K posts
- 15. Childish Gambino 2,639 posts
- 16. Tottenham 40.4K posts
- 17. South Asia 38K posts
- 18. Arsenal 163K posts
- 19. Samoa Joe 5,640 posts
- 20. Swerve 6,861 posts
You might like
-
 Security BSides
Security BSides
@SecurityBSides -
 Core Impact
Core Impact
@_CoreImpact -
 Help Net Security
Help Net Security
@helpnetsecurity -
 Ron Gula
Ron Gula
@RonGula -
 BruCON
BruCON
@brucon -
 Erin Jacobs
Erin Jacobs
@SecBarbie -
 Kevin Johnson - Same on the Blue site. :)
Kevin Johnson - Same on the Blue site. :)
@secureideas -
 Ryan Dewhurst
Ryan Dewhurst
@ethicalhack3r -
 Danny Quist
Danny Quist
@OpenMalware -
 Christophe Veltsos
Christophe Veltsos
@DrInfoSec -
 Web Security News
Web Security News
@WebSecurityNews -
 Chris Nickerson
Chris Nickerson
@indi303 -
 Joshua Wright
Joshua Wright
@joswr1ght -
 Marius Avram
Marius Avram
@securityshell -
 edskoudis
edskoudis
@edskoudis
Something went wrong.
Something went wrong.
























































































































































