reverend wayne ³³º¹
@tacodestroyer
father. husband. photographer. taco lover. security dude. #SecKC #PancakeCoin
You might like
Be me. Go on vacation for 10 days. Come home to play @CallofDuty. Upgrade to latest version. Instant shadowban. Wtf?
Oh man, an F-15 pilot friend gave me permission to share this video of him filming his buddy sending it. That maniacal laughter is universal among anyone who has seen this in person, even other fighter pilots. How can I NOT go to the base today to watch this. 🤘😀🤙
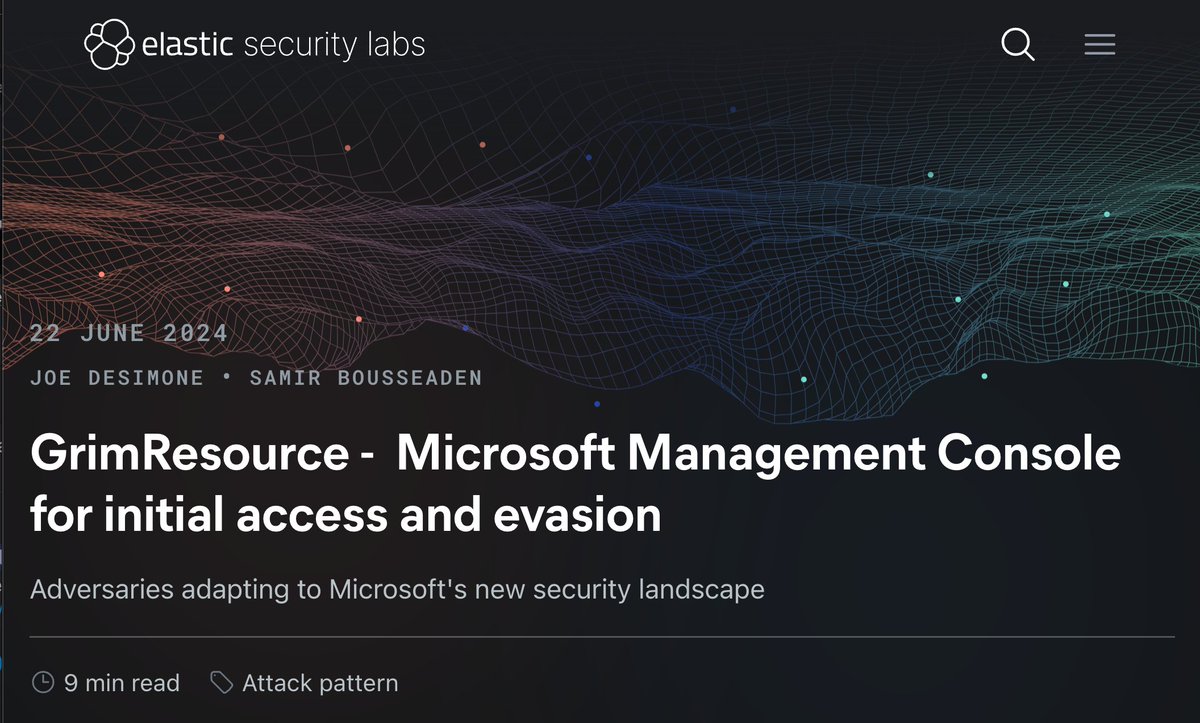
CyberSec Trends Q4/24🔮 ⬆️EDR killers (vulnerable drivers) ⬆️Auxiliary execution files .lnk .msc .rdp ⬆️Abuse of legit remote access tools ⬆️Token/cloud API abuse ⬆️ADCS exploitation ⬆️Fake CAPTCHAs: copy&paste PowerShell ⬆️TA using systems out of EDR scope for persistence


New ShellcodePack version coming out soon with: - Custom AMSI bypass to weaponize .NET assemblies - Obfuscated Python Shellcode launchers - File timestamp spoofing - Updated EDR bypass profiles #redteam

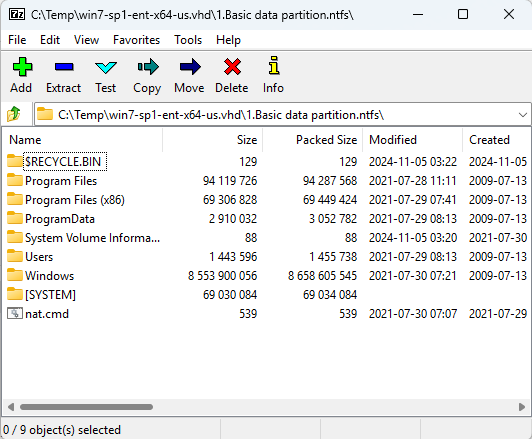
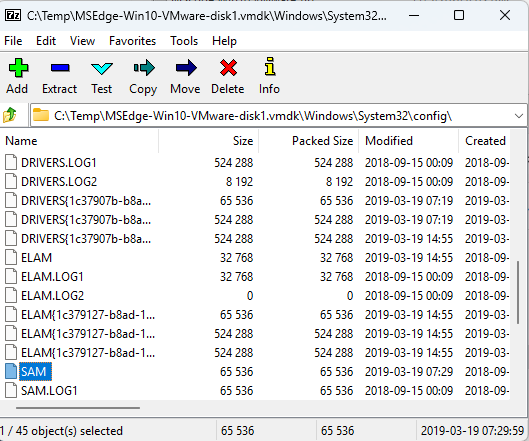
Did you know that 7z can browse .VHD and .VMDK files? You can open them right up, and even directly browse ntfs filesystems. On a pentest and find a bunch of disk images? Copy the SAM/SECURITY/SYSTEM hives directly from the images, no mounting, copying, or fussing around.
Please don’t touch that, It’s my emotional support Any Any Any Allow rule
Our talk from @defcon is now available! In the presented research, we document every EDR bypass technique used in the wild along with how to detect it using new memory forensics techniques and @volatility plugins. Feedback appreciated! youtube.com/watch?v=PmqvBe… #DFIR
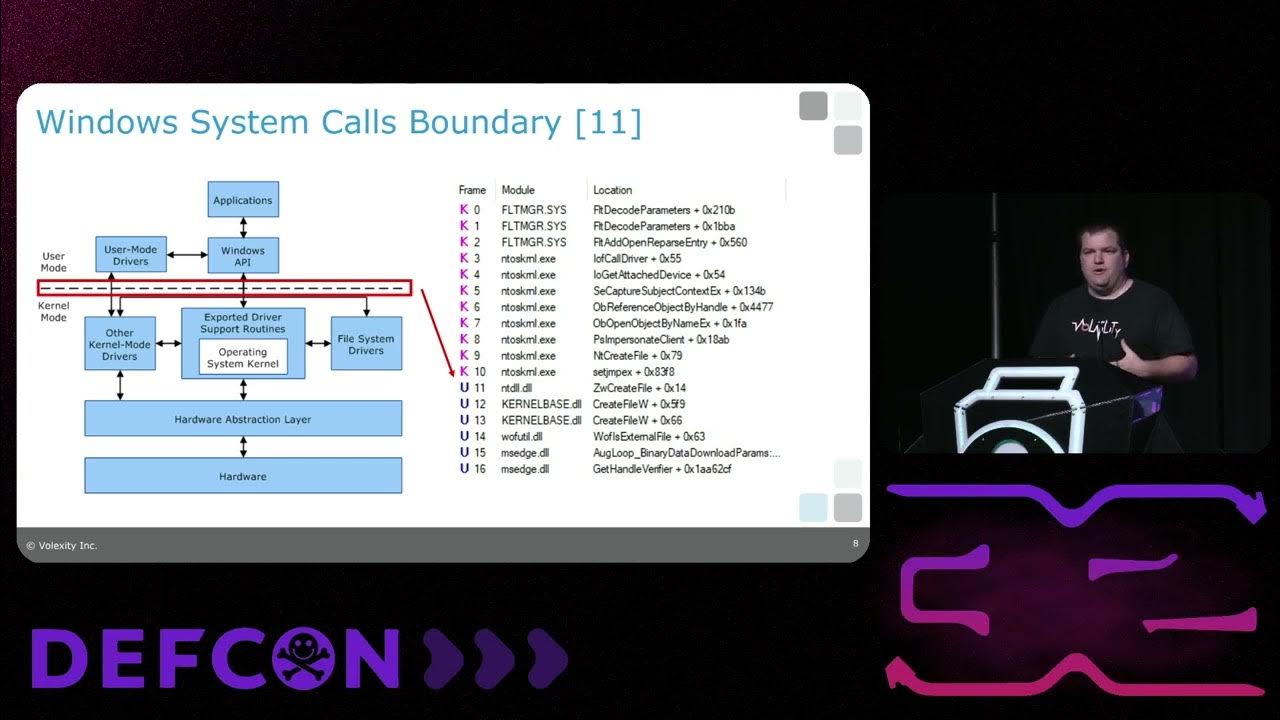
youtube.com
YouTube
DEF CON 32 - Defeating EDR Evading Malware with Memory Forensics -...
I'm finally going to give the back story of the infamous zWarDial tool along with other security stories at @saintcon Tomorrow [Thursday @ 1:30 PM MDT] "The Bug Bounty Battlefield: A Choose Your Own Adventure Story on Why I Stopped Reporting Bugs" #saintcon 1/2
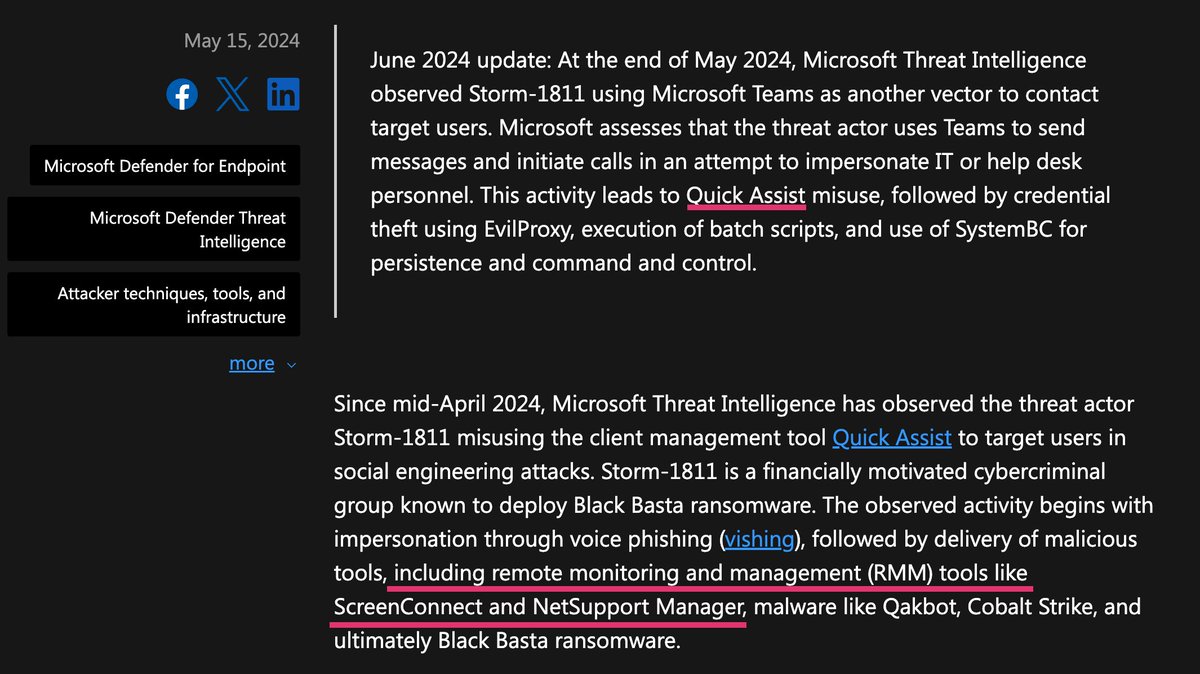
Hey folks--you might have seen a @BrianKrebs article on @zoom_us security that referenced #SecKC and @surbo this morning. You should know that we will NOT be releasing the #zWarDial to the public. If you see this tool offered, it is malware. krebsonsecurity.com/2020/04/war-di…

This is awesome. Our teams have fake tenants as honeypots that look like real ones—they contain realistic-looking data with realistic-looking users. But they’ve taken honeypots to a whole new level. They’re not just waiting for someone to fall into the trap. They actively search…
Finding Windows Defender Exclusions via MpCmdRun.exe Links in next post!👇

A new version of my pentest template will be released later this fall. New tips, techniques, and resources are being added. Most importantly I am moving my notes away from Joplin to Obsidian. Here is a sneak peek of what the new template will look like:

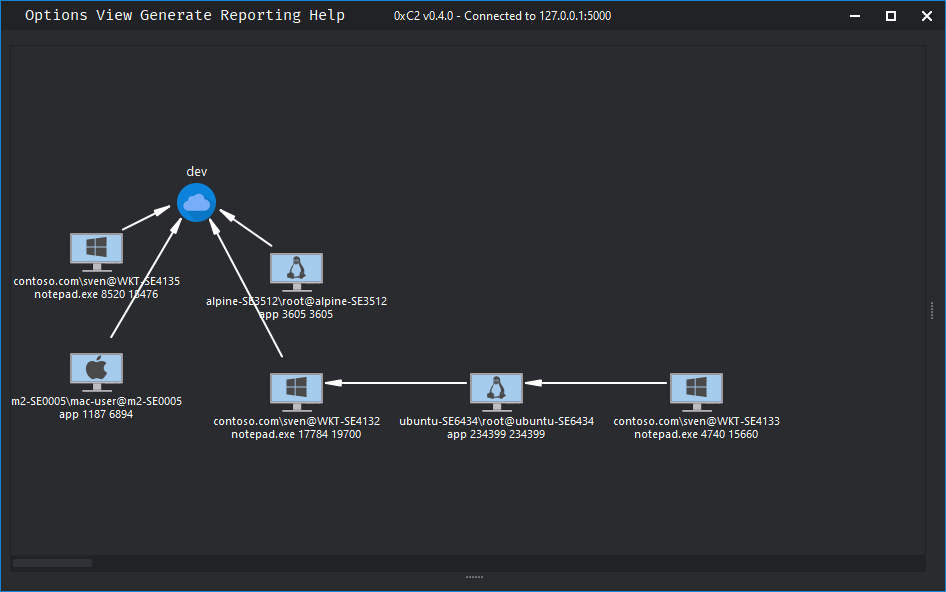
Over a year ago, I left my position at WithSecure to start a new journey, create something new, and do my own thing. Today, I'm excited to publicly announce what I've been working on all this time. Introducing 0xC2, a cross-platform C2 framework targeting Windows, Linux, and…
Great intro to #reverse #engineering blog by @0x6D6172636F along with some amazing #ascii art! x86re.com

Meet MV Ocean Trader — a one-of-a-kind shadowy Special Operations mothership literally designed to hide in plain sight 👀 Operating AIS dark, under commercial guise & hoisting false flags, it can launch drones, helos, boats, & SEALS. Much is classified, but here’s what we know:

TIL: that intel i3,i5, i7 and i9 processors are all the same, all made the same, on the same wafer. But depending on how many defects (therefore how many sections actually work) they just rename them. So your i3 processor is an i9 with many defects less for an i5 and less for i7
10: Whatever damages incur from your use of the product, they're on you. Even if CrowdStrike could have prevented it. Never use the product in sensitive environments, such as aircraft navigation systems (you can't make this stuff up), nuclear facilities, etc.

My team at Red Siege has written, instructed and developed some awesome training over the last year with zero involvement from me. Unfortunately, even though they don't work for SANS and I have had zero input or part in their courses, SANS has told me that unless they stop…
We often argue about which log source is the most important, how about which events? What are your top 5 and why? 4624 - need those logons 4688 - process creation of course 1006 - Defender AV detection 4104 - PowerShell script block logging 4697 - service installation events
United States Trends
- 1. Good Sunday 58.6K posts
- 2. Klay 25.4K posts
- 3. McLaren 107K posts
- 4. #sundayvibes 4,686 posts
- 5. Lando 138K posts
- 6. #FelizCumpleañosPresidente 3,226 posts
- 7. #FelizCumpleañosNico 3,489 posts
- 8. For the Lord 30.2K posts
- 9. Ja Morant 11.6K posts
- 10. #AEWFullGear 73.2K posts
- 11. Tottenham 42.1K posts
- 12. Oscar 129K posts
- 13. Max Verstappen 68.2K posts
- 14. Piastri 78.7K posts
- 15. #LasVegasGP 234K posts
- 16. Childish Gambino 2,779 posts
- 17. South Asia 38.9K posts
- 18. Arsenal 167K posts
- 19. Swerve 6,921 posts
- 20. Hangman 11K posts
Something went wrong.
Something went wrong.