Joshua Nwibo
@talk_2_josh
Medical//Cybersecurity
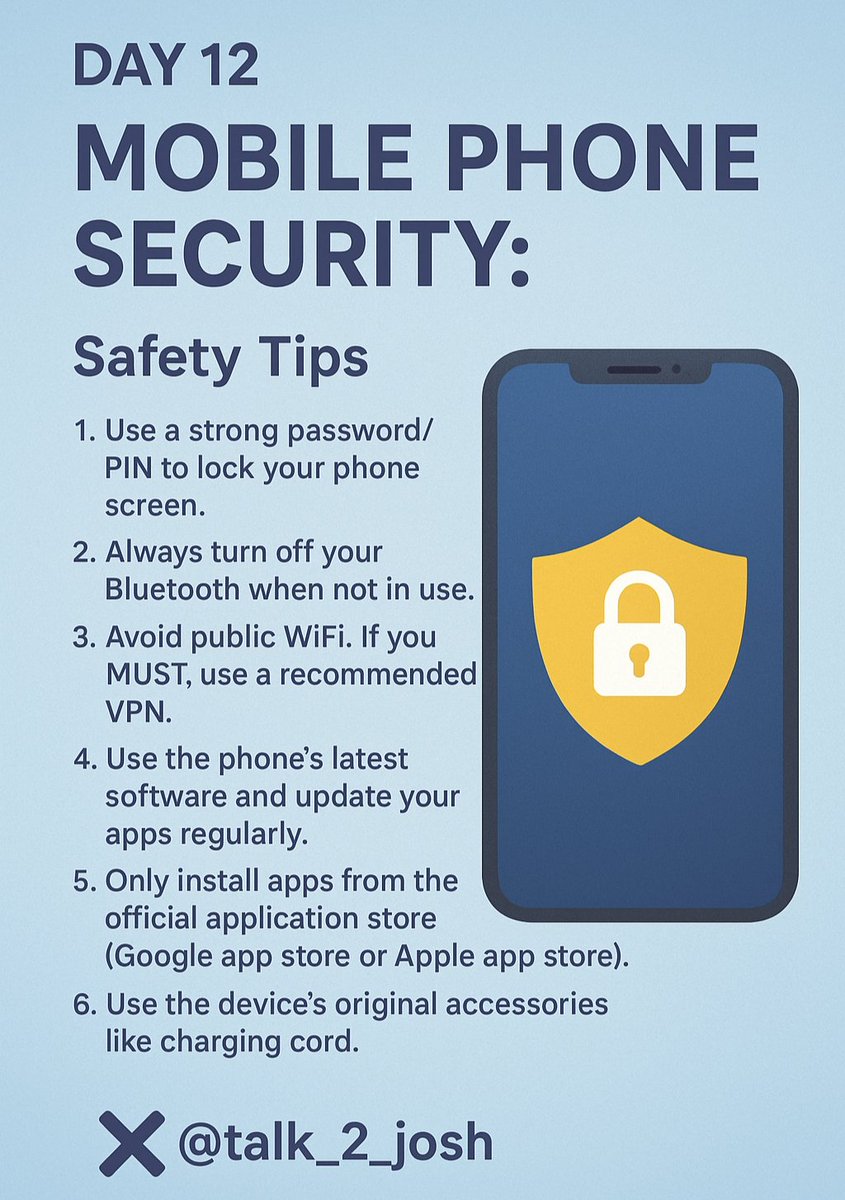
In todays interconnected world, mobile phone has become an extension of the body. Mobile phones have evolved to make life convenient, but there are associated risks. Cyber criminals are increasingly targeting the mobile phone for their exploits. Safety Tips 👇
DAY 9 OF CYBER AWARENESS PUBLIC WI-FI Most times you want to use public wifi (at hotels, airports,etc.) because they are FREE. They are often not secure, making your data vulnerable to threat actors. #CyberAwareness #OnlineSafety @AfriTechX

To stay safe and ensure that your devices function properly, always update them. Software update is a way of improving security of devices by patching vulnerabilities, enhancing performance by introducing new features. #CyberAwareness #OnlineSafety @AfriTechX

📌
Social Engineering: The Human Hacking Epidemic- A Thread 🧵 Social engineering exploits our natural tendencies, curiosity, fear, or kindness to bypass security. It’s not about cracking code; it’s about cracking people. In 2025, with remote work and digital overload, it’s more…

To stay safe and ensure that your devices function properly, always update them. Software update is a way of improving security of devices by patching vulnerabilities, enhancing performance by introducing new features. #CyberAwareness #OnlineSafety @AfriTechX

DAY 6 OF CYBER AWARENESS BACKUP: Safety Net Against Ransomware. Backups are the most effective way to recover from a ransomware attack. To serve as a true safety net, backups must be implemented and secured using specific strategies. #Cyberawareness #Onlinesafety @AfriTechX

📌📌
Ransomware Attack: Ransomware is a type of malicious software (malware) that encrypts a victim's files, making them inaccessible until a ransom is paid to the attacker. Process: 1. Attacker sends Phishing Email→ User receives a link and clicks. 2. Malware unpacks and…
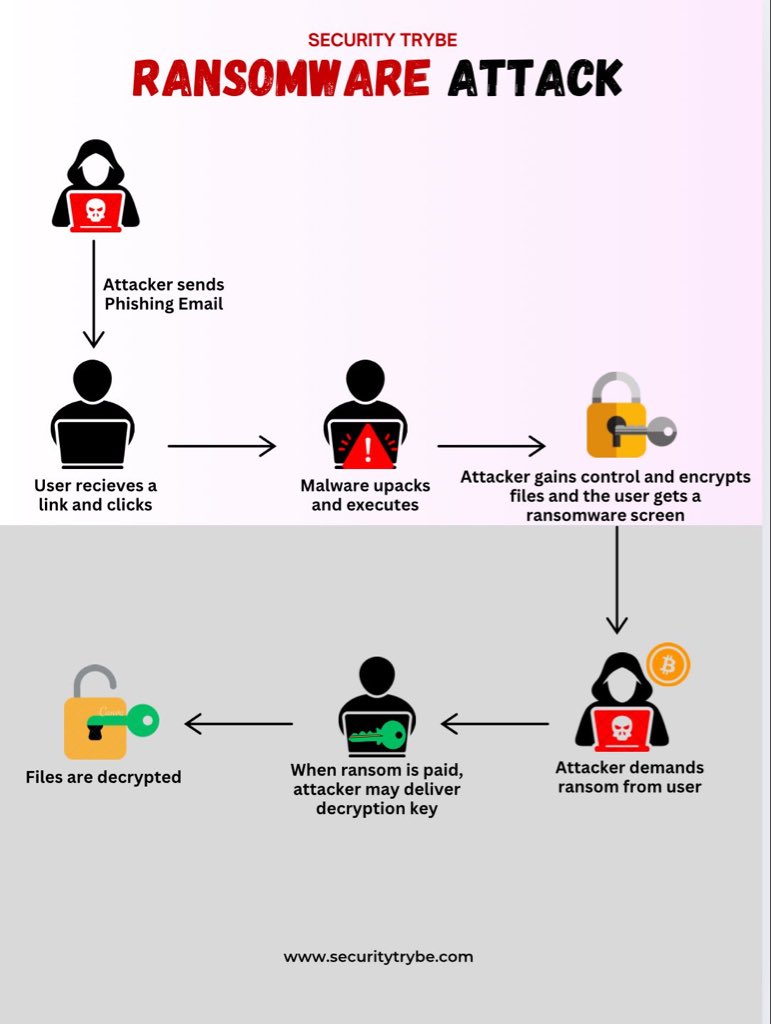
Ransomware Attack: Ransomware is a type of malicious software (malware) that encrypts a victim's files, making them inaccessible until a ransom is paid to the attacker. Process: 1. Attacker sends Phishing Email→ User receives a link and clicks. 2. Malware unpacks and…

Happy new week x.com/talk_2_josh/st…
It's week. Think before you post Internet never forgets Think before you post Internet never forgets Think before you post Internet never forgets Think before you post Internet never forgets Think before you post Internet never forgets.
It's week. Think before you post Internet never forgets Think before you post Internet never forgets Think before you post Internet never forgets Think before you post Internet never forgets Think before you post Internet never forgets.
DAY 6 OF CYBER AWARENESS BACKUP: Safety Net Against Ransomware. Backups are the most effective way to recover from a ransomware attack. To serve as a true safety net, backups must be implemented and secured using specific strategies. #Cyberawareness #Onlinesafety @AfriTechX

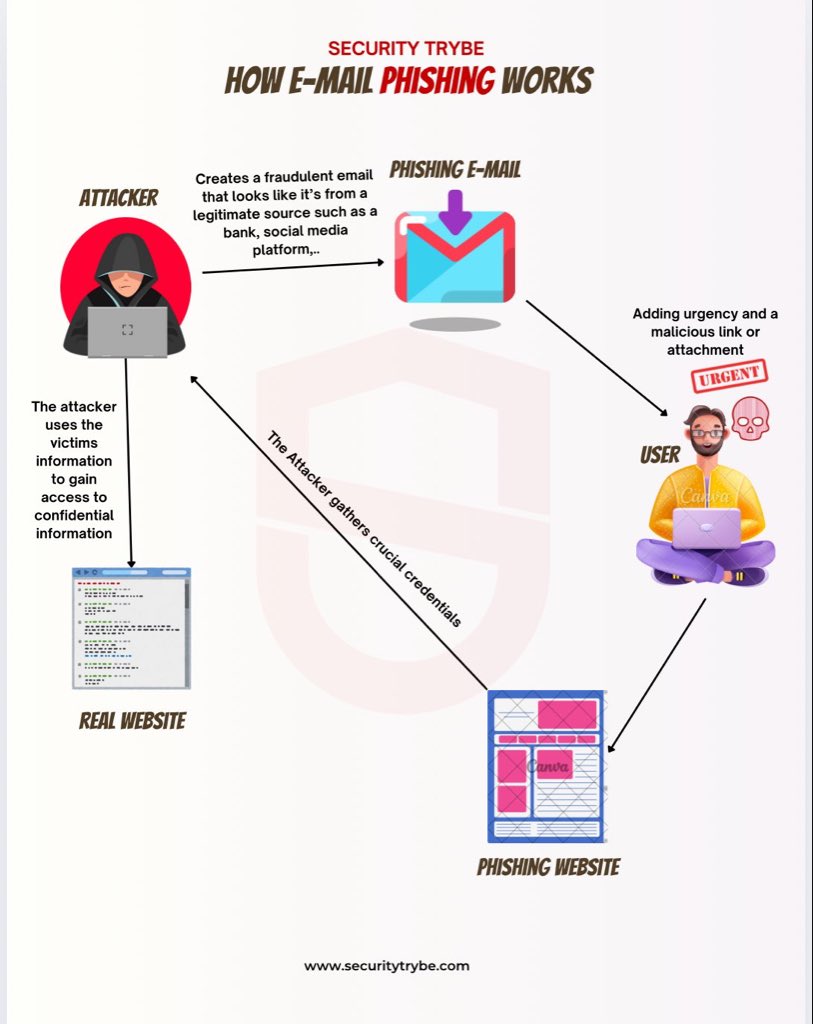
DAY 4 Phishing is a form of social engineering. The aim is to trick individuals into revealing sensitive personal or financial information such as passwords, credit card numbers or bank details. more ⬇️⬇️

DAY 2 OF CYBER AWARENESS To add to the list... 6. Do not use one password across all your accounts #cyberawarenessmonth #OnlineSafety

Stay cyber safe 🙏
United States Tendencias
- 1. Cowboys 67.3K posts
- 2. Fred Warner 7,403 posts
- 3. Panthers 68.1K posts
- 4. Ravens 62.2K posts
- 5. Zac Taylor 1,801 posts
- 6. Browns 60.7K posts
- 7. Dolphins 44.6K posts
- 8. #KeepPounding 7,168 posts
- 9. Eberflus 9,163 posts
- 10. Colts 54.3K posts
- 11. #FTTB 3,122 posts
- 12. Steelers 63.1K posts
- 13. Rico Dowdle 9,432 posts
- 14. Penn State 66.4K posts
- 15. Drake Maye 20.6K posts
- 16. Cam Ward 1,625 posts
- 17. James Franklin 49K posts
- 18. Chargers 52K posts
- 19. Herbert 15.5K posts
- 20. Pickens 16.8K posts
Something went wrong.
Something went wrong.