你可能會喜歡
When I started learning cyber security back in 2020, I was overwhelmed with the resources. One of the main issues I faced at that time was the lack of free, structured content that could actually guide beginners step-by-step. That’s exactly why I started my YouTube channel.…
Here's how you can start learning bug bounty & web application penetration testing using my videos for free!! If you are complete beginner, here's how you can get started: 1. Recon: youtube.com/watch?v=i3-xJ-… 2. Open Redirection: youtube.com/watch?v=dDDEyQ… 3. Cross Site Scripting:…
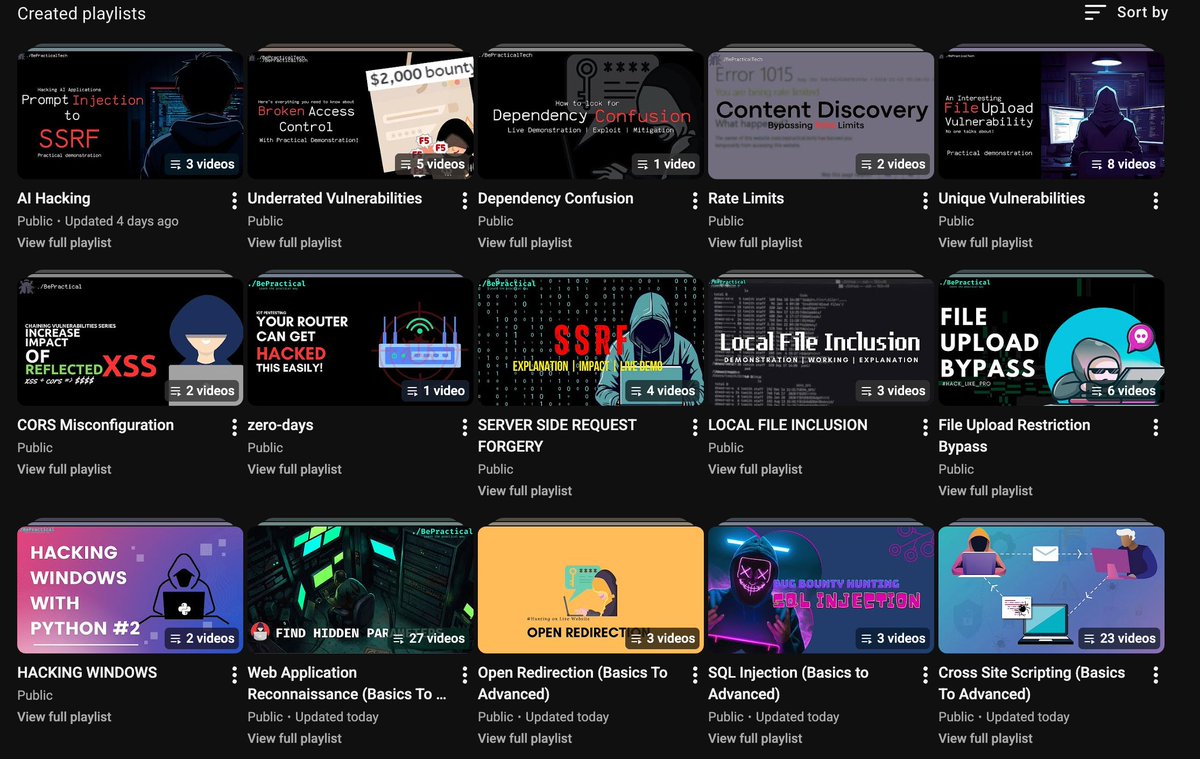
Want to learn bug bounty & cyber security for free? I've uploaded over 170+ videos that covers everything from recon, basic vulnerabilities to diving deep into the application like a real hacker! Check it out here: youtube.com/c/BePracticalT…
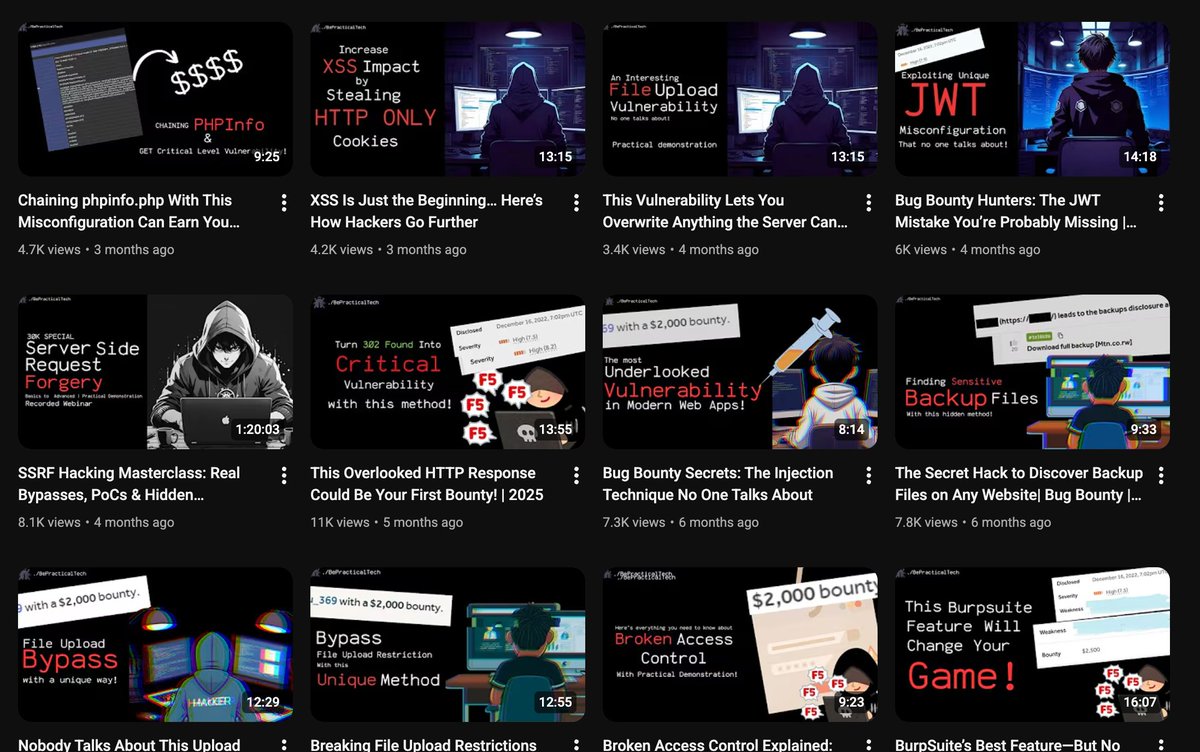
We’ve just reached 36K subs on our YouTube channel!! Thanks a lot for everyone who has supported me throughout this journey. I know for some this isn’t much but for me it’s more than I could ever imagine!!! Few yrs ago, I was learning from the same community where I am now…
It’s wild how a single AI prompt can quietly turn into a full SSRF attack without anyone noticing! I just released a new video where I break down this exact scenario — beginner-friendly, practically demonstrated, and focused purely on education. With so many apps rushing to…

This was one of my most engaged video in recently! If you are someone who gets stucked after seeing a nginx default page then this will be for you Watch this video and learn -> What is nginx -> How it works? -> How to recon on nginx based application? Click here:…
Hello @dhruv_rathee, I’ve recently discovered a high severity vulnerability in one of your AI fiesta’s asset. Please let me know how should I report it so that your team can fix it!
Ever wondered what it really takes to break into AI-powered applications? I’ve just launched a brand new playlist on my YouTube channel, and the first two videos are already live. If you’re serious about cybersecurity, learning how to test and secure AI-driven systems is no…
In case you missed it, I’ve recently dropped a new video showing how a single crafted prompt was able to bypass LLM security and trigger remote code execution. LLMs are still just mathematical models predicting the next token — not systems that understand intent. And that’s…

People assume LLM security is unbeatable because “the AI is smart.” But it’s not smart — it’s a pattern generator. And those patterns can be manipulated. I created a fully practical demo showing how one prompt slipped past all the safeguards and ended in RCE. The chain is…
You don’t need advanced tools to find high-impact bugs — you just need to understand how to look. When I started, I used to run scans endlessly, hoping something would pop. Most beginners do the same — they gather tons of data but miss what really matters. That’s exactly why I…
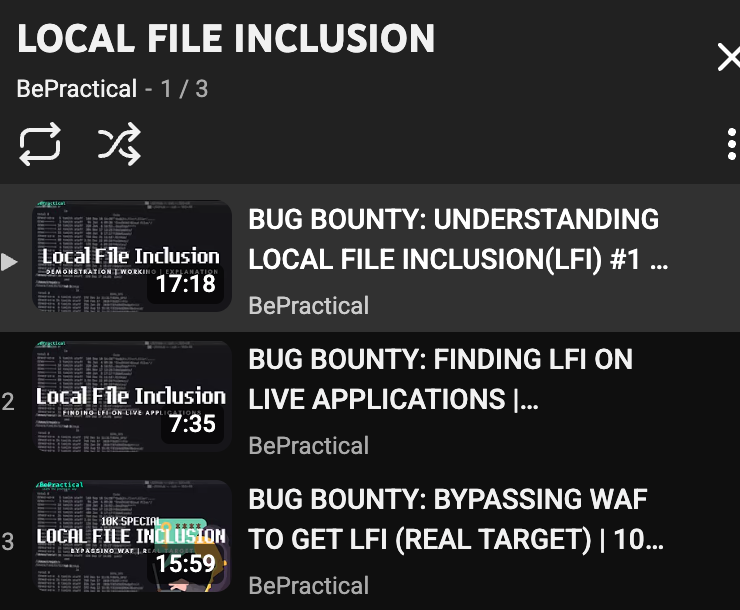
Here's how you can learn to find and exploit Local File Inclusion in real apps — step-by-step and without the fluff. I’ve created a short, beginner-friendly playlist with three fully practical videos that cover everything from understanding LFI to finding and exploiting it on…
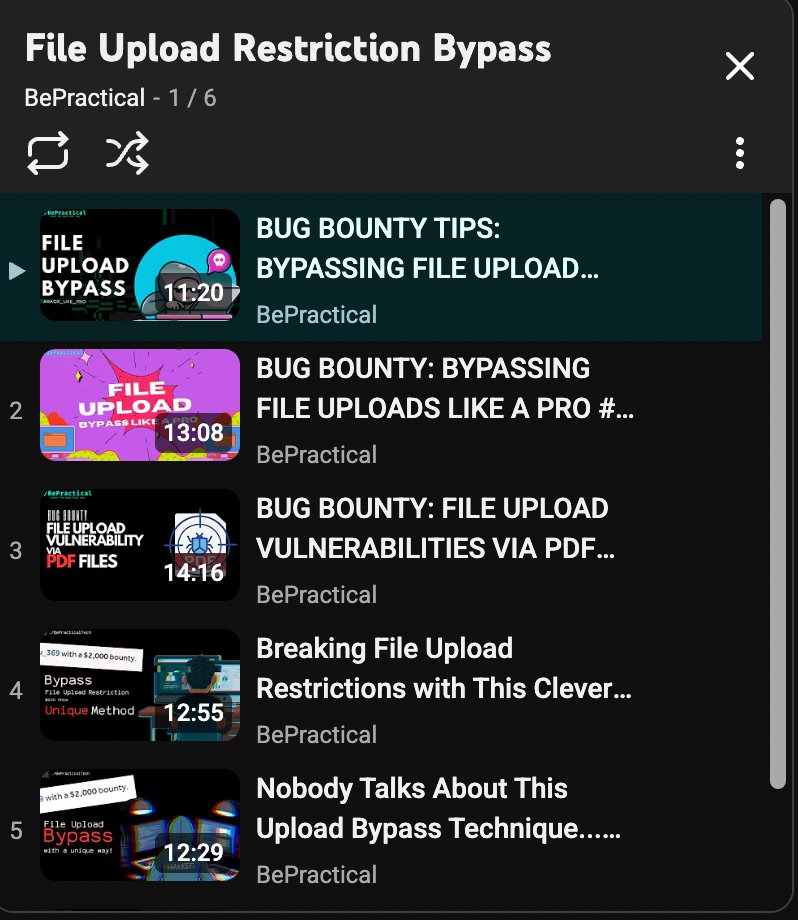
Want to master file upload flaws and actually bypass real-world restrictions? I made a hands-on YouTube playlist that walks through practical techniques and live demos to bypass file upload protections. Completely FREE. Watch the playlist youtube.com/watch?v=8Tq4EU…
XBOW raised $117M to build AI hacking agents. Now someone just open-sourced it for FREE. Strix deploys autonomous AI agents that act like real hackers - they run your code dynamically, find vulnerabilities, and validate them through actual proof-of-concepts. Why it matters:…
Everyone hunts for common bugs… but the real rewards often hide in the underrated ones. I’ve made a YouTube playlist — “Underrated Vulnerabilities” showing how to find impactful bugs most hackers miss. Practical. Real. Eye-opening. Watch here: youtube.com/watch?v=GZ5yaQ…

Want to learn XSS from scratch and turn it into real, practical skills? I made a 23-video YouTube playlist that takes you from basic payloads to advanced XSS chains — with live target demos. Completely FREE. Watch the playlist youtube.com/watch?v=1WFEVp…

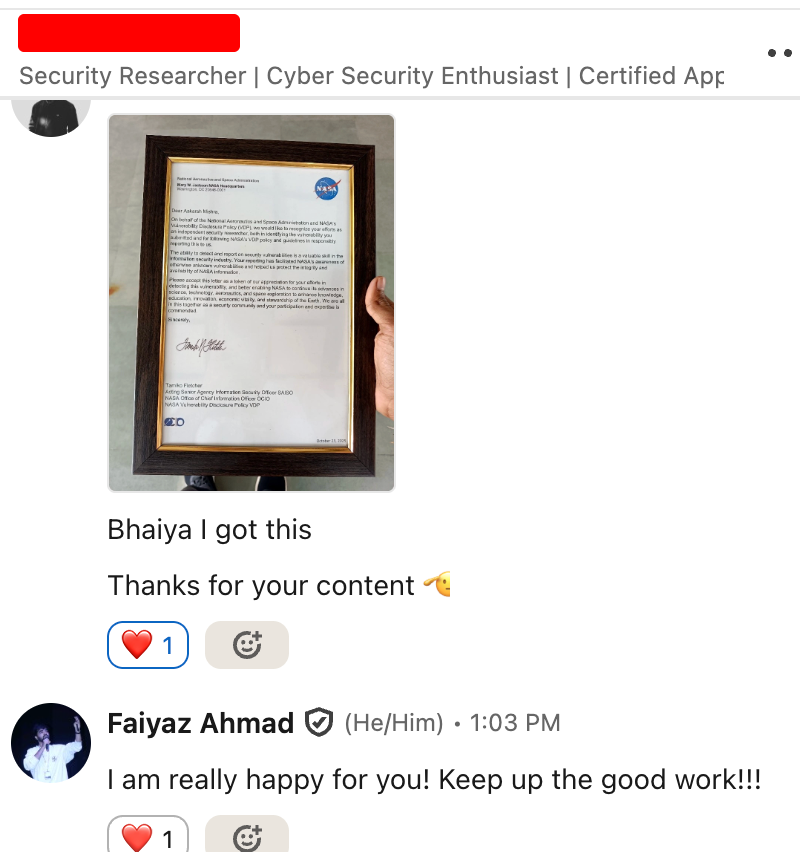
Just got a message from someone who watches my YouTube content — he found a vulnerability in NASA and got an acknowledgment letter from them! This honestly made my day. People like him are the reason I keep creating more content ❤️ Channel link: youtube.com/@BePracticalTe…
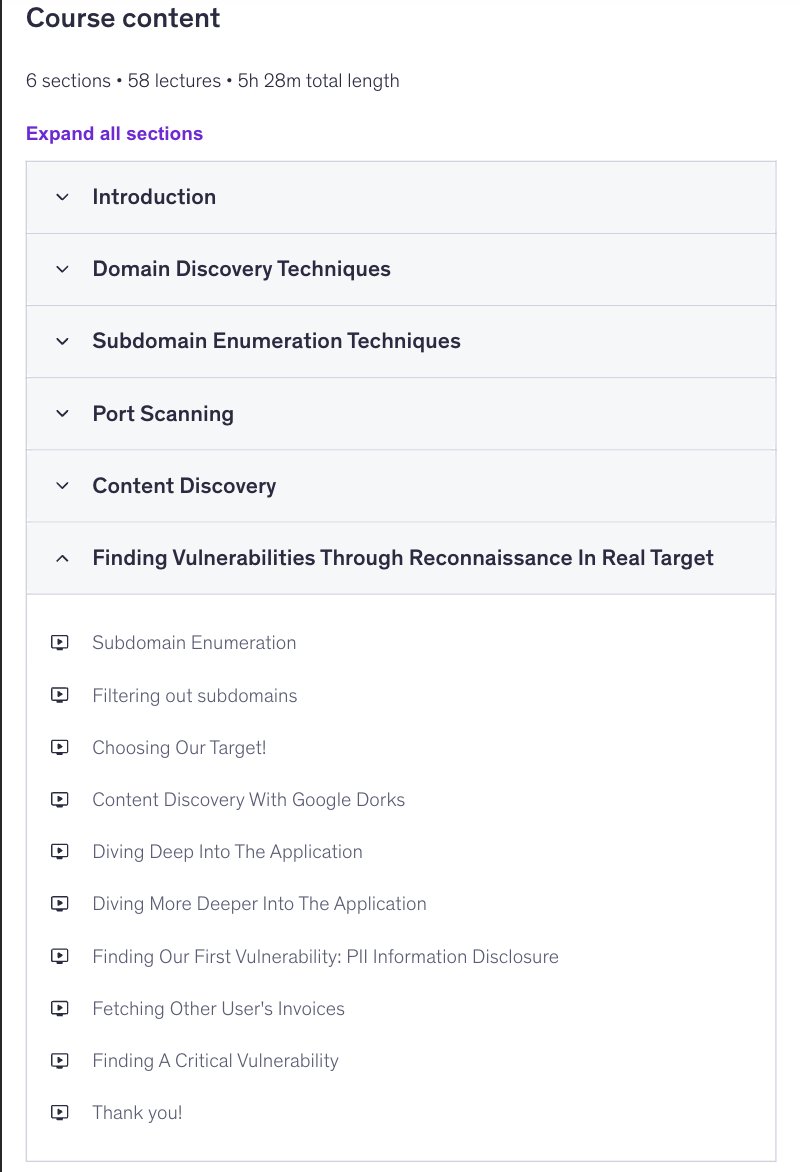
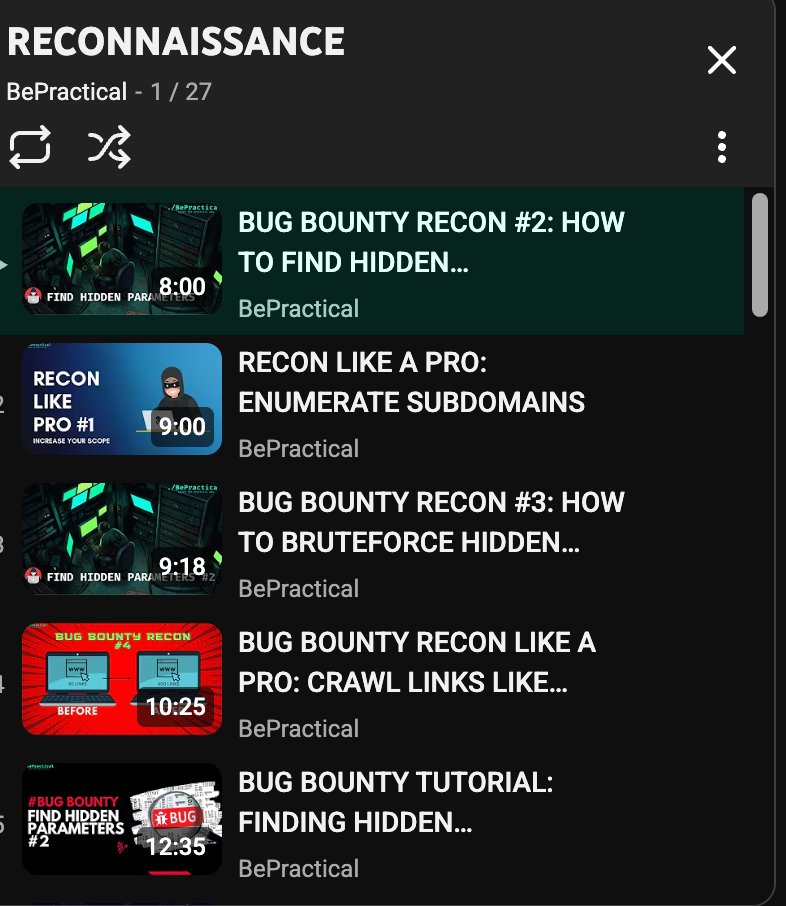
Want to learn interesting recon techniques for free? 27 bite-sized, demo-first videos for beginners — subdomains, content & param discovery, bypassing 403s, vhosts & monitoring. Start here: youtube.com/watch?v=HVz9WY…
Excited to share — my Web Recon Mastery course is now FREE for all Udemy Business members! 🎯 If you don’t have access, you can still grab it at the maximum discount using the link below — but hurry, the offer expires today! udemy.com/course/the-art…
United States 趨勢
- 1. Chris Paul 7,912 posts
- 2. Pat Spencer 2,677 posts
- 3. Kerr 5,651 posts
- 4. Podz 3,308 posts
- 5. Shai 15.7K posts
- 6. Seth Curry 4,984 posts
- 7. The Clippers 10.7K posts
- 8. Jimmy Butler 2,662 posts
- 9. Hield 1,595 posts
- 10. Carter Hart 4,122 posts
- 11. #DubNation 1,439 posts
- 12. Lawrence Frank N/A
- 13. #SeanCombsTheReckoning 5,213 posts
- 14. Mark Pope 1,973 posts
- 15. #AreYouSure2 133K posts
- 16. Kuminga 1,500 posts
- 17. Brandy 8,356 posts
- 18. Derek Dixon 1,315 posts
- 19. Elden Campbell N/A
- 20. Earl Campbell 1,179 posts
你可能會喜歡
-
 encodedguy - jsmon.sh
encodedguy - jsmon.sh
@3nc0d3dGuY -
 Gotcha1G
Gotcha1G
@Gotcha1G -
 Sourav Khan🇧🇩 🇵🇸
Sourav Khan🇧🇩 🇵🇸
@Br0k3n_1337 -
 Rahmat Qurishi
Rahmat Qurishi
@RahmatQurishi -
 Zhenwarx
Zhenwarx
@zhenwarx -
 Fares
Fares
@_2os5 -
 Imamul Mursalin
Imamul Mursalin
@d3f7ult -
 Deepak bug_vs_me
Deepak bug_vs_me
@bug_vs_me -
 Lu3ky13 ⚡️⚡️
Lu3ky13 ⚡️⚡️
@lu3ky13 -
 Ankit Singh
Ankit Singh
@AnkitCuriosity -
 Hammad 🇵🇰🇵🇸
Hammad 🇵🇰🇵🇸
@Hammad7361 -
 Jefferson Gonzales
Jefferson Gonzales
@gonzxph -
 SickSec 🇲🇦 🇵🇸
SickSec 🇲🇦 🇵🇸
@OriginalSicksec -
 Nihad
Nihad
@nihad_rekany -
 Naeem Ahmed Sayed 🇧🇩
Naeem Ahmed Sayed 🇧🇩
@0xNaeem
Something went wrong.
Something went wrong.











































































![hunter0x7's profile picture. [Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)