You might like
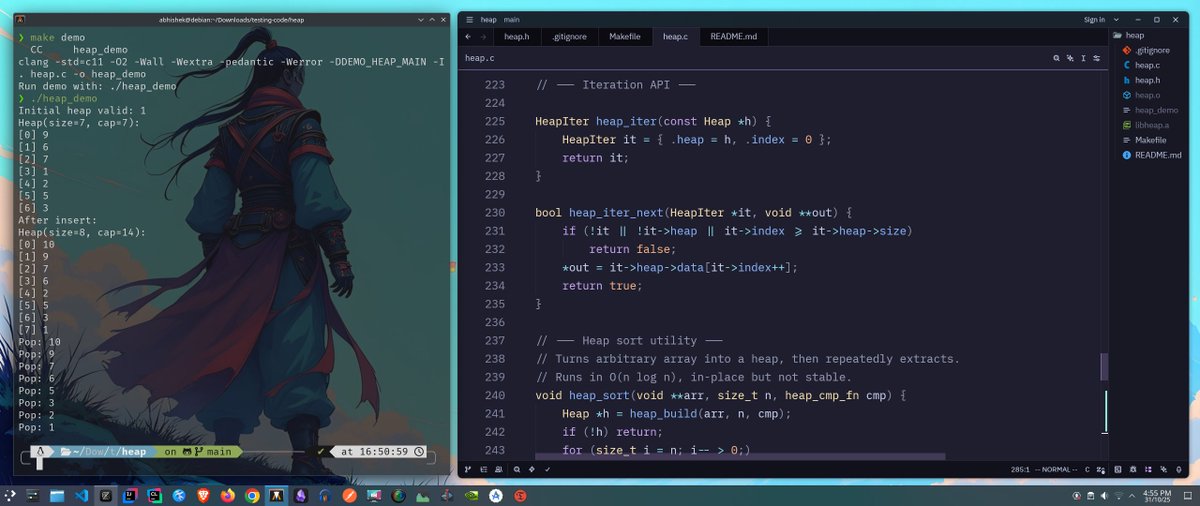
I Built my own binary heap in pure C from scratch. I Implemented these features in this project : -Generic heap that stores void* elements -Custom comparator function (heap_cmp_fn) → supports min-heap or max-heap -heap_create() → create an empty heap -heap_build() → build a…
This is my debut hour-long talk on exploiting a heap-overflow in Llama.cpp RPC, when I was fifteen at ZeroCon. Enjoy:) research.pwno.io/llama-paradox

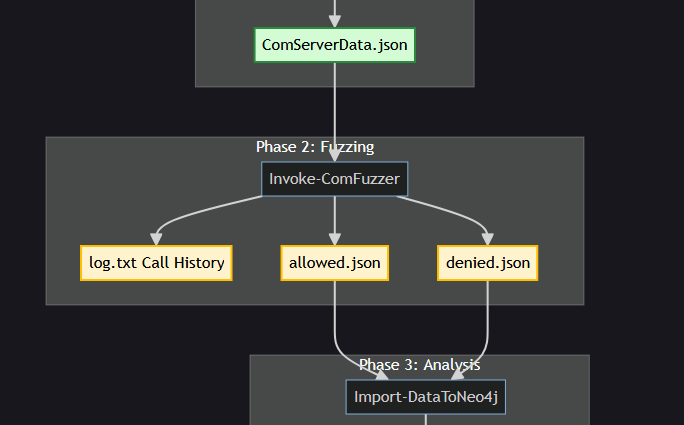
Automating COM/DCOM vulnerability research incendium.rocks/posts/Automati…
Lesson 16: x86 Course (Part 16: Heap) - This tutorial will address the heap. #ReverseEngineering github.com/mytechnotalent…
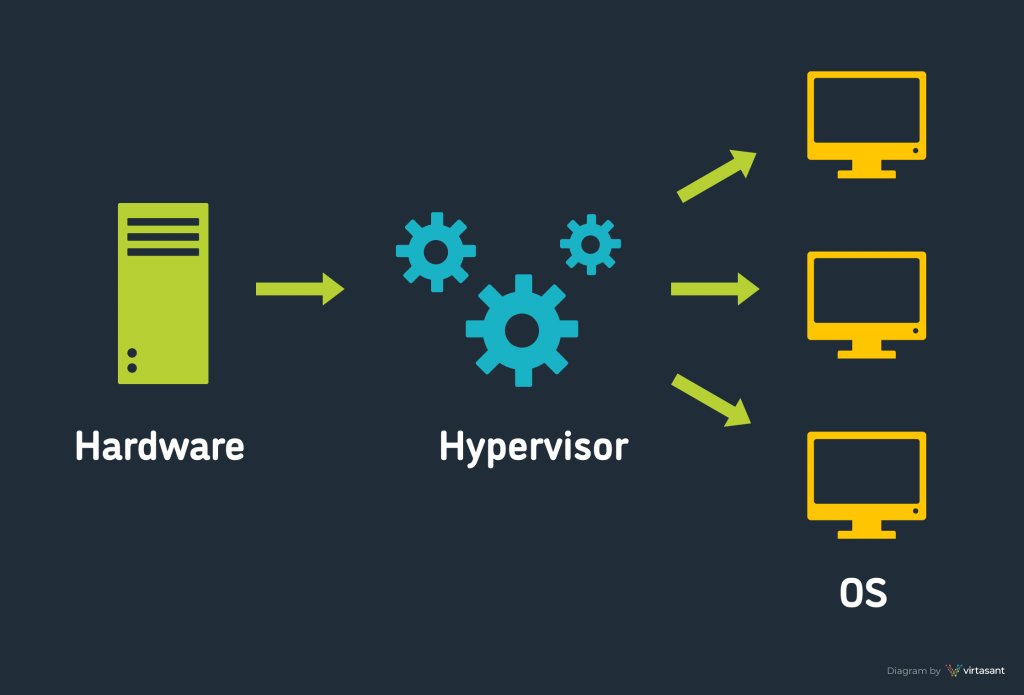
Detecting Hypervisor-assisted Hooking TL;DR: This post will describe the concept of hypervisor-assisted hooking and a few simple approaches to detect such hooks. momo5502.com/posts/2022-05-…
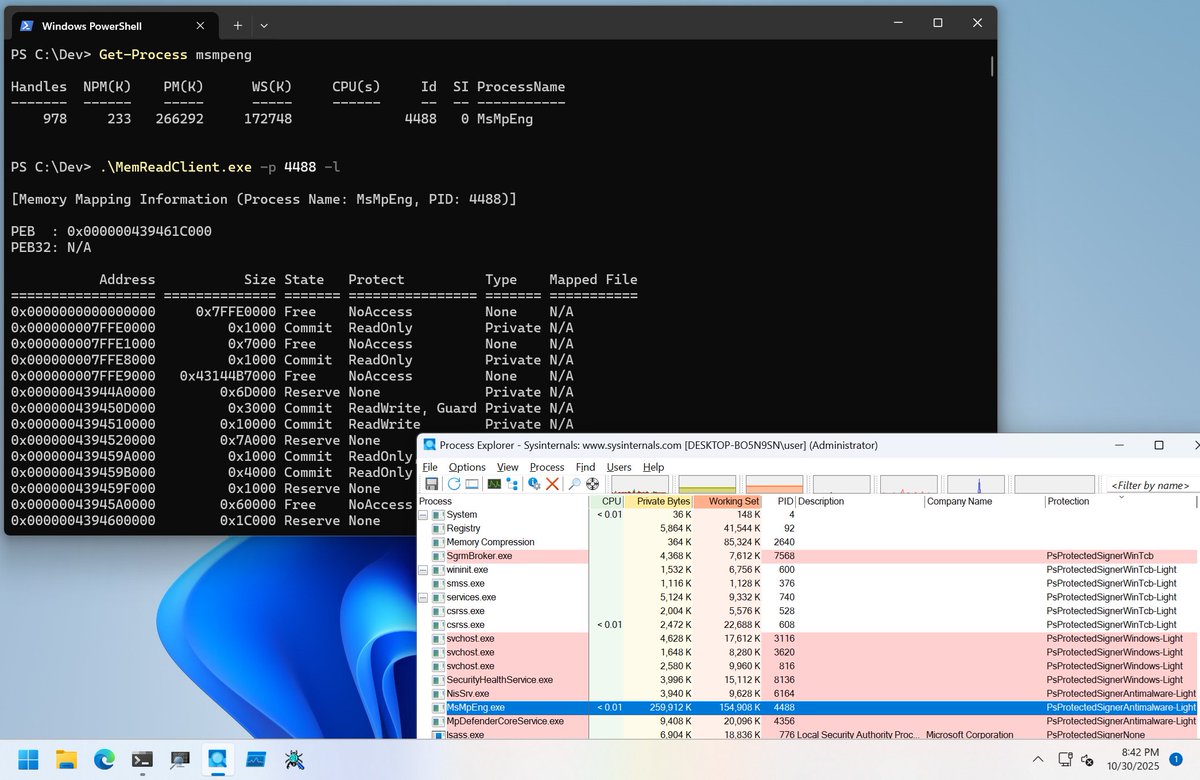
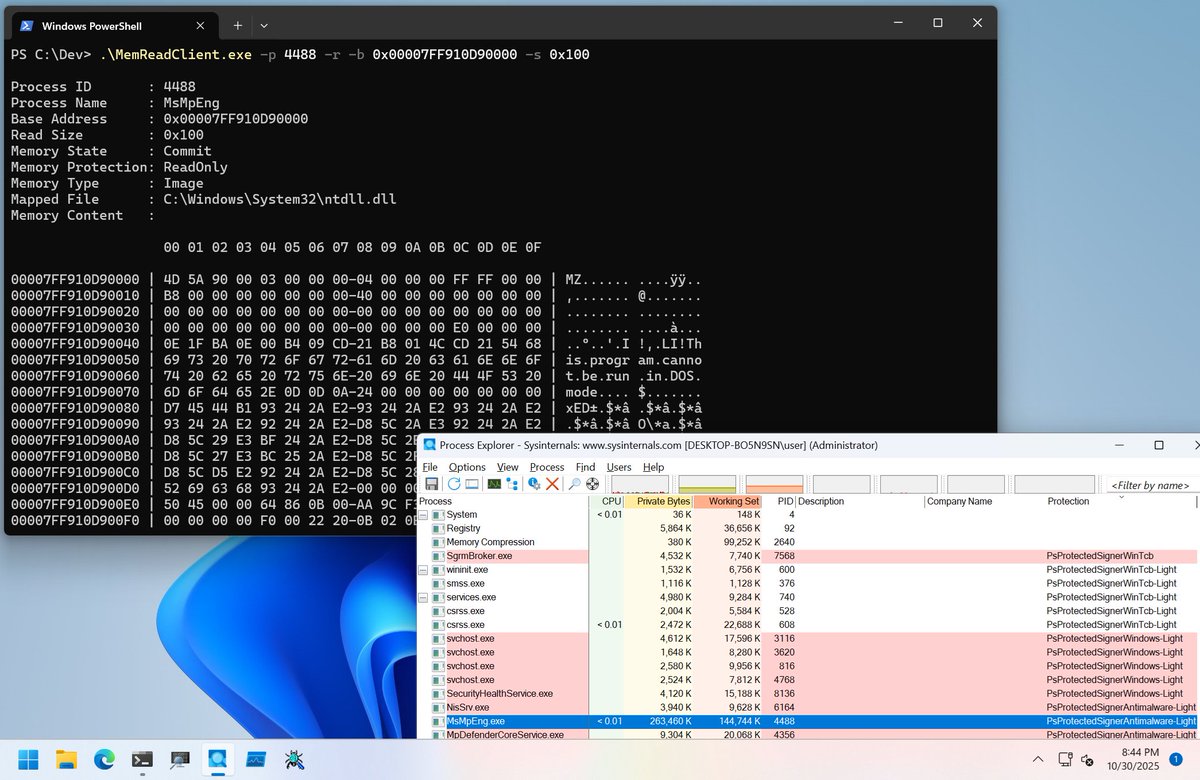
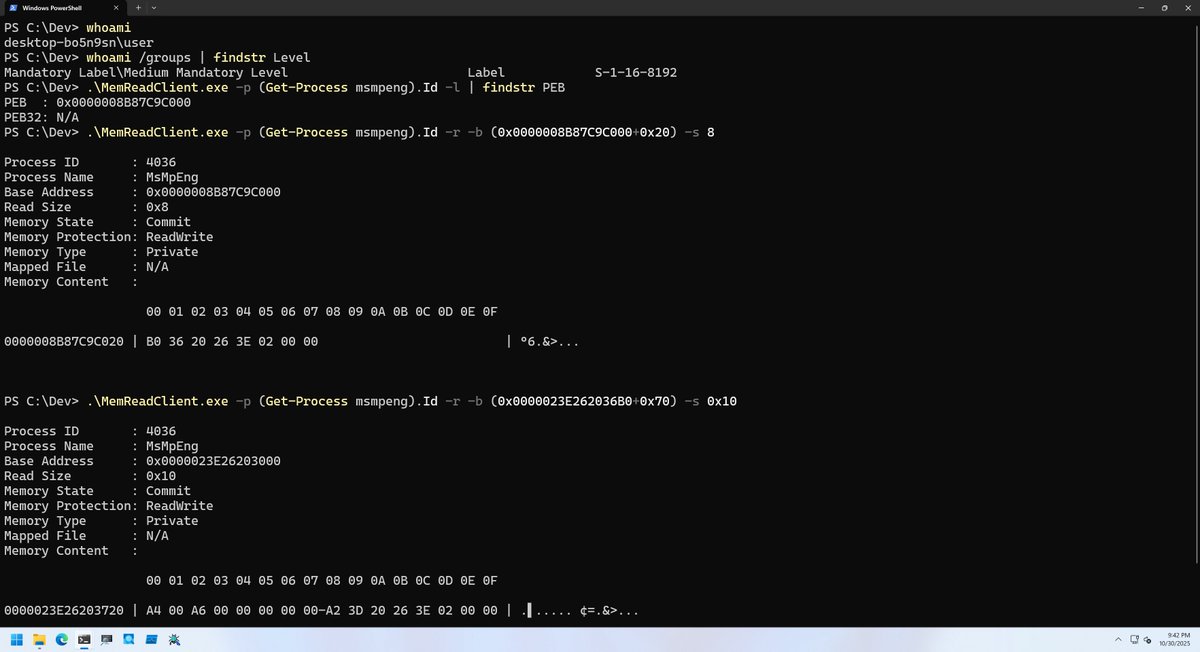
Added a kernel driver to read arbitrary process memory (including Protected Process). Also implemented a functionality to query memory mapping information. github.com/daem0nc0re/Vec…

New research from @jdu2600: a clean loader-lock escape using the PEB's PostProcessInitRoutine. Read the analysis and PoC code 📃 preludesecurity.com/blog/escaping-…
Chained 6 vulnerabilities to get RCE on @UnitreeRobotics days ago. They pushed V1.1.11 a day later "patching" (not really) the RCE. The @pwnoio boys are unstoppable, new RCE using the same primitive. Crazy blog dropping soon 🔥🔥🔥 @retr0reg


[1day1line] CVE-2025-49844: RCE Vulnerability in Redis Caused by Use After Free via Lua Script hackyboiz.github.io/2025/10/29/new… Today's 1day1line: CVE-2025-49844, a Use After Free RCE vulnerability discovered in Redis. The vulnerability is caused by unpinned chunks accessed via Lua…
hyper-reV: A powerful memory introspection & reverse engineering hypervisor leveraging Hyper-V. Read/write guest memory, SLAT hooks, and hide pages, all while evading detection. Supports Intel/AMD, tested on Win10/11. Check it out: github.com/noahware/hyper… #HyperV…
Blog post about my recent CVE-2025-58726, aka “The Ghost Reflection” is out, read it here: semperis.com/blog/exploitin… 🙃
Small update on "printerbugnew:" added a description of how to exploit CVE-2025-54918: DCs running 2025 allow reflection RPC->LDAPS - from a standard user to DA before patch😃 github.com/decoder-it/pri…
Wonka is a sweet Windows tool that extracts Kerberos tickets from the Local Security Authority (LSA) cache. github.com/Shac0x/Wonka
Today I am releasing a new blog post on VSM "secure calls" + the SkBridge project to manually issue them!! This blog talks about how VTL 0 requests the services of VTL 1 and outlines common secure call patterns!!! Blog: connormcgarr.github.io/secure-calls-a… SkBridge: github.com/connormcgarr/S…

Excellent crash course from Raphael Mudge on PIC shellcode development vimeo.com/1100089433

vimeo.com
Vimeo
PIC Development Crash Course
Interested in an alternative approach to sleep masking for you malware? Check-out our latest blog post "Function Peekaboo: Crafting self masking functions using LLVM" by @saab_sec mdsec.co.uk/2025/10/functi…

📚 AD Domain-Join Owning PoC Compromising the Active Directory through domain-join account attacks in 2025. Read: shelltrail.com/research/activ…

Program synthesis is the solution you’re looking for. Try to play around with msynth of @mr_phrazer github.com/mrphrazer/msyn…
Here are some new posts on #flareon12 ## Challenge 6 - Chain of Demands blog.0wl.sg/docs/y2025/oct… # Mainly focusing on Deobfuscation with Binja ## Challlenge 7 - The Boss Needs Help blog.0wl.sg/docs/y2025/oct… ## Challenge 8 - FlareAuthenticator blog.0wl.sg/docs/y2025/oct…
blog.0wl.sg
20251025120557 - BLG - Flare-on 12 Chall 8 - Deobfuscating Indirect Calls and Jumps with Binja
Just like the post for Challenge 7, this entry documents the journey to de-obfuscate this challenge. Note that this isn’t a challenge walkthrough but a process of creating a de-obfuscator using...
👑 Writing To Memory From Kernel Mode Go beyond user-land. Learn to use the powerful MmCopyVirtualMemory function to safely read and write to memory from the highest privilege level, bypassing security checks and defenses. 🚀 Master Kernel-level Hacking: youtu.be/EaxaQYESDlM
United States Trends
- 1. #NXXT_NEWS N/A
- 2. #TheGamingAwards N/A
- 3. Good Thursday 35.7K posts
- 4. Nano Banana Pro 5,100 posts
- 5. #WeekndTourLeaks N/A
- 6. #TikTokCouplesAreFake N/A
- 7. #thursdayvibes 3,088 posts
- 8. Nnamdi Kanu 99.6K posts
- 9. FINAL DRAFT FINAL LOVE 82.5K posts
- 10. Happy Friday Eve N/A
- 11. The Hunger Games 62.8K posts
- 12. Haymitch 7,548 posts
- 13. Reaping 56.1K posts
- 14. FAYE SHINE IN ARMANI 197K posts
- 15. Dick Cheney 8,035 posts
- 16. Unemployment 27.7K posts
- 17. Ray Dalio 2,207 posts
- 18. Crockett 67.3K posts
- 19. Janemba 2,105 posts
- 20. Transgender Day of Remembrance 2,229 posts
Something went wrong.
Something went wrong.