ReverseThatApp
@ReverseThatApp
Developer/Develop tweak and patch iOS binary/ Reverse Engineering iOS apps (arm, arm64)/ Learning kernel!!
Bunları beğenebilirsin
my first post on @hackernoon get more reading time than Medium one (100 views vs 1k6) 😂, more to come soon hackernoon.com/bypassing-ssl-… #iOSSecurity #MobileSecurity
hackernoon.com
Bypassing SSL Pinning with LLDB on AppStore iOS apps [A Step by Step Guide] | HackerNoon
Imagine that you want to inspect the app to see what’s information exchange between mobile app and server, you can think about using simple proxy tools to sniff requests and responses or more...
Really enjoyed #flareon12 — especially challenges 7, 8, and the brutal but fun final challenge (9). 🧠🔥 Thanks to @Mandiant for another amazing RE CTF. #CTF #ReverseEngineering #CyberSecurity

We present appledb_rs, an open-source tool to analyze Apple IPSWs without storing full images. Extraction, indexing, API, and web interface to speed up your security research 🔍 🔗 Full article available here: synacktiv.com/en/publication… 📂 Source code: github.com/synacktiv/appl…
github.com
GitHub - synacktiv/appledb_rs: Apple artifacts database - Mirror of https://github.com/cocool97/a...
Apple artifacts database - Mirror of https://github.com/cocool97/appledb_rs - synacktiv/appledb_rs
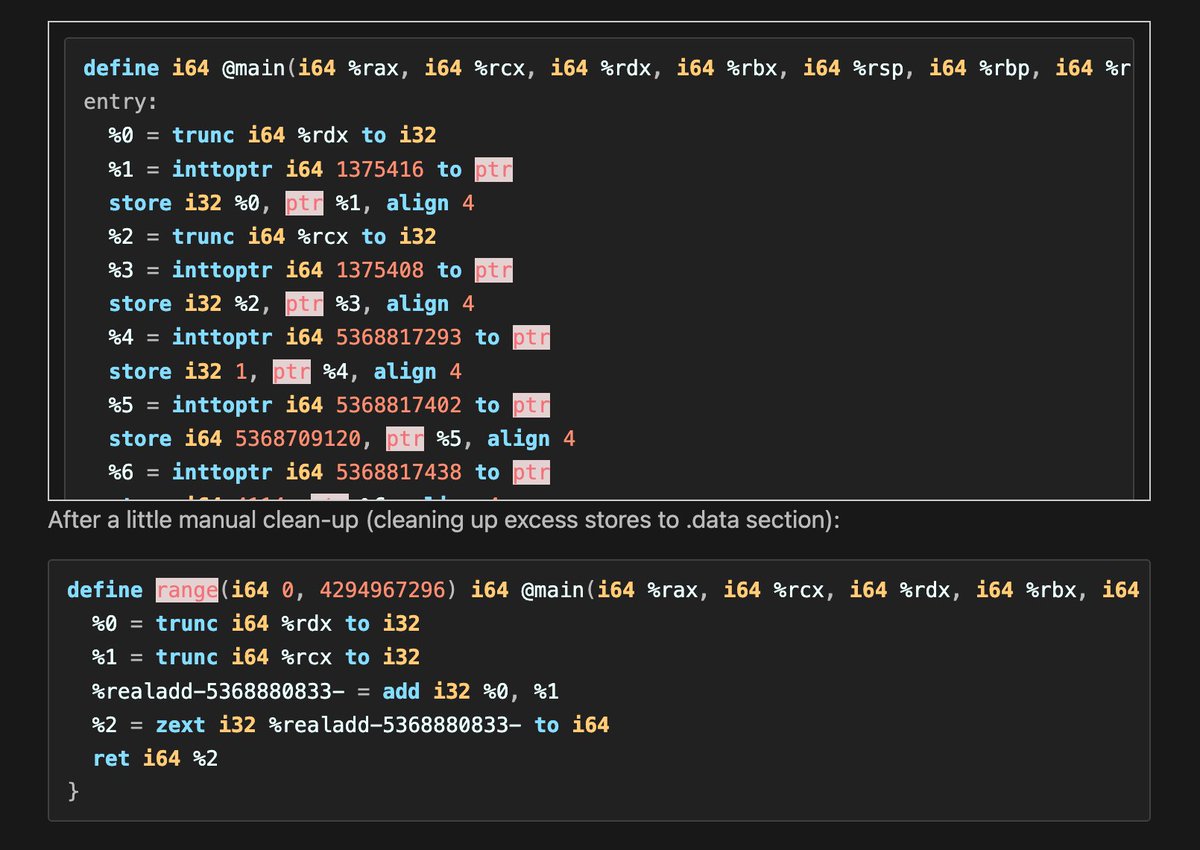
Devirtualizing VMProtect and Themida nac-l.github.io/2025/01/25/lif… #infosec #reverseengineering

#flareon12 pre-register now at flare-on12.ctfd.io The puzzles are unleashed tomorrow.
Community Write-Ups from 8kSec Mobile Security Battlegrounds Our free Mobile Security Labs have inspired some excellent technical deep dives. Below is a running list of community write-ups that detail their techniques, tooling, and exploitation steps. 🤖Android Labs @f0rk3b0mb…



FLARE-On 12 is about to blow up your weekends: security.googlecloudcommunity.com/news-announcem… #flareon12
The 12th Annual Flare-On Challenge kicks off Sept 26 at 8PM EST! Reverse engineering pros, from Windows to Web3 (with a YARA twist), it's your time to shine. 🏆 Get ready → bit.ly/4ofb5g8 #FlareOn12

zero‑click iMessage exploit? 🕵️♂️ I diffed iOS 18.3 vs 18.3.1, uncovered the logic flaw and dropped RE walkthrough and forensic tips so you can trace it too. jaybird1291.github.io/blog-cyber/en/…


Thanks to a lot of work put in by @mrexodia, IDACode has finally gotten an official update again after 3 years of inactivity! It features stability improvements as well as IDA 9 compatibility improvements! Thanks a lot to everyone involved <3 github.com/ioncodes/idaco…
github.com
GitHub - ioncodes/idacode: An integration for IDA and VS Code which connects both to easily execute...
An integration for IDA and VS Code which connects both to easily execute and debug IDAPython scripts. - ioncodes/idacode
Just released a short writeup for the A9 version of the Trigon exploit, which involves getting code execution on a coprocessor before exploiting the kernel - enjoy! alfiecg.uk/2025/07/16/Tri…
🤩 GuidedHacking's Anti-Cheat Development Course 🚀 COMING SOON!!

Unrestrict the restricted mode for USB on iPhone. A first analysis @citizenlab #CVE-2025-24200 👉 blog.quarkslab.com/first-analysis…

macOS Malware Development (Part 2) : 0x00sec.org/t/macos-malwar… Part 1 : 0x00sec.org/t/macos-malwar… Executing Mach-Os In-Memory : 0x00sec.org/t/executing-ma… Ref : Inside a Hello World executable on OS X : adrummond.net/posts/macho The Mystery of Mach-O Object Structure :…
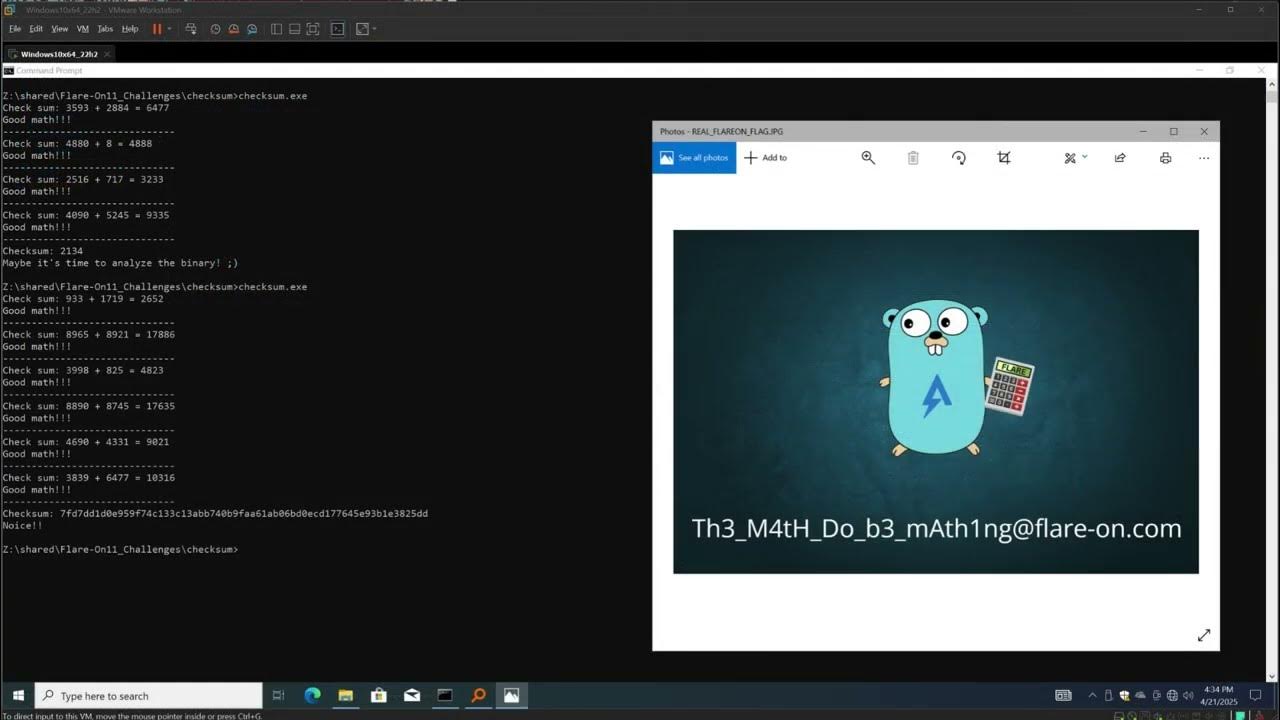
Using LLMs to play Flare-On 11. Much more fun compared to pre-LLMs era. youtu.be/w232BOBfoeA
youtube.com
YouTube
Flare-On 11 -vs- LLMs (1-5 solutions)
Trigon: developing a deterministic kernel exploit for iOS alfiecg.uk/2025/03/01/Tri…
Here we can see @AnthropicAI's claude (Sonnet 3.7 model) talking to IDA pro to reverse engineer a CTF task I made for @PotluckCTF, it does pretty well! It manages to get a grasp of the entire custom VM instruction set, file format, syscall interface etc.🤓 The MCP server is…
Introdution for beginners to embedded devices reverse engineering Ghidra setup: voidstarsec.com/blog/ghidra-de… Tools: voidstarsec.com/blog/intro-to-… Firmware extraction: voidstarsec.com/blog/uart-uboo… Credits @voidstarsec #cybersecurity

Lifting Binaries, Part 0: Devirtualizing VMProtect and Themida: It's Just Flattening? by Naci nac-l.github.io/2025/01/25/lif…


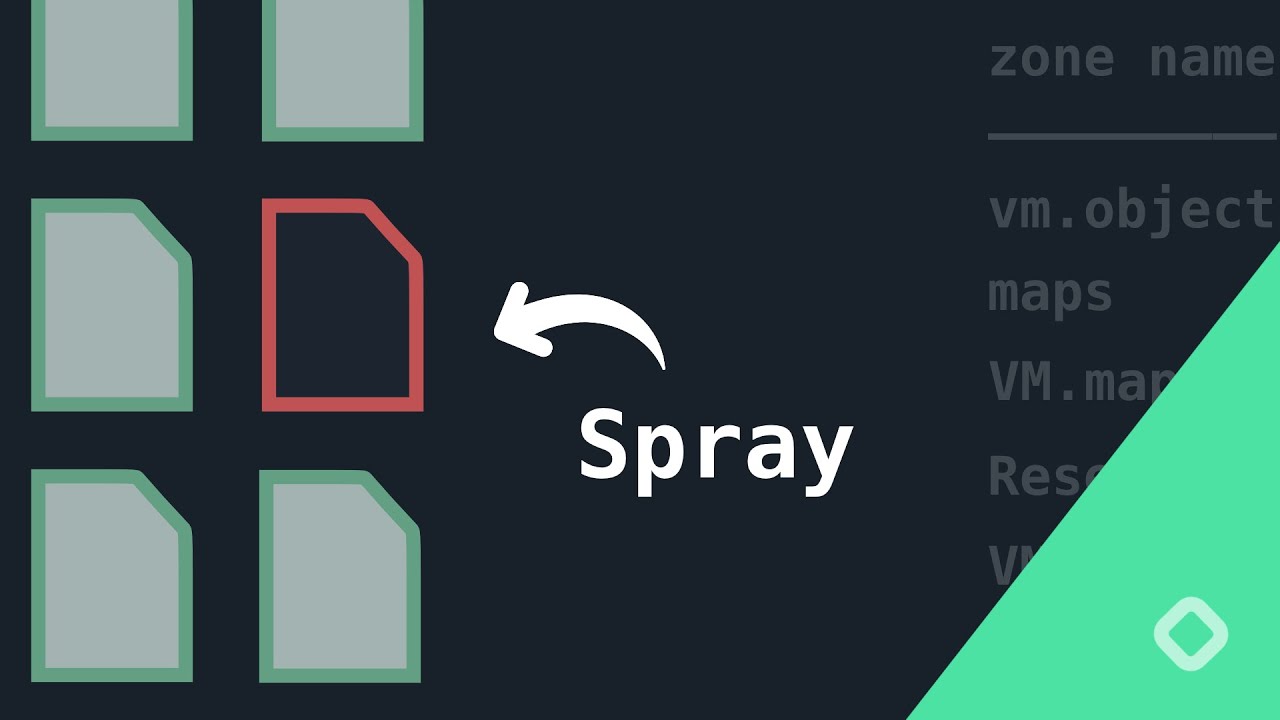
Exploiting the iOS Kernel by Spraying IOSurfaces #MobileSecurity #iOSsecurity by @bellis1000 youtube.com/watch?v=Y-UI4d…
youtube.com
YouTube
But How Does a Kernel Exploit Actually Work?
It's an amazing journey, learned many stuffs and cant wait for the next year 😎 #flareon11

United States Trendler
- 1. Butker 4,712 posts
- 2. Baker 43.8K posts
- 3. Lions 50.8K posts
- 4. Lions 50.8K posts
- 5. Goff 7,540 posts
- 6. #OnePride 2,787 posts
- 7. 49ers 40.3K posts
- 8. #TNABoundForGlory 15K posts
- 9. Ty Dillon N/A
- 10. #BNBdip N/A
- 11. Bucs 13.6K posts
- 12. Dan Campbell 1,424 posts
- 13. Packers 36.2K posts
- 14. #DETvsKC 1,279 posts
- 15. #SNFonNBC N/A
- 16. Fred Warner 15.6K posts
- 17. Denny 4,793 posts
- 18. Flacco 13.2K posts
- 19. George Springer 3,009 posts
- 20. Byron 6,417 posts
Bunları beğenebilirsin
-
 Jiska
Jiska
@naehrdine -
 Bruno Rocha
Bruno Rocha
@rockbruno_ -
 Dinesh Shetty
Dinesh Shetty
@Din3zh -
 [email protected]
[email protected]
@CodeColorist -
 JF
JF
@J4NF4 -
 b1ack0wl
b1ack0wl
@b1ack0wl -
 Govind Sharma
Govind Sharma
@ApkUnpacker -
 Bas vT
Bas vT
@AppleDry05 -
 EvilPenguin
EvilPenguin
@EvilPenguin_ -
 Raffaele Sabato
Raffaele Sabato
@syrion89 -
 Mobile Security
Mobile Security
@Nethanella -
 Bayani_cipher
Bayani_cipher
@st3am3dric31 -
 C0deRevenant
C0deRevenant
@Fury_1511 -
 j9h
j9h
@j9hand
Something went wrong.
Something went wrong.