#dataencryptionalgorithms 検索結果
As the world becomes more digital we are quietly losing something precious yes it is Privacy , @zama_fhe solves this with Fully Homomorphic Encryption data can be computed, analyzed, and used without ever being seen. Finally, transparency doesn’t mean exposure. A new era is…

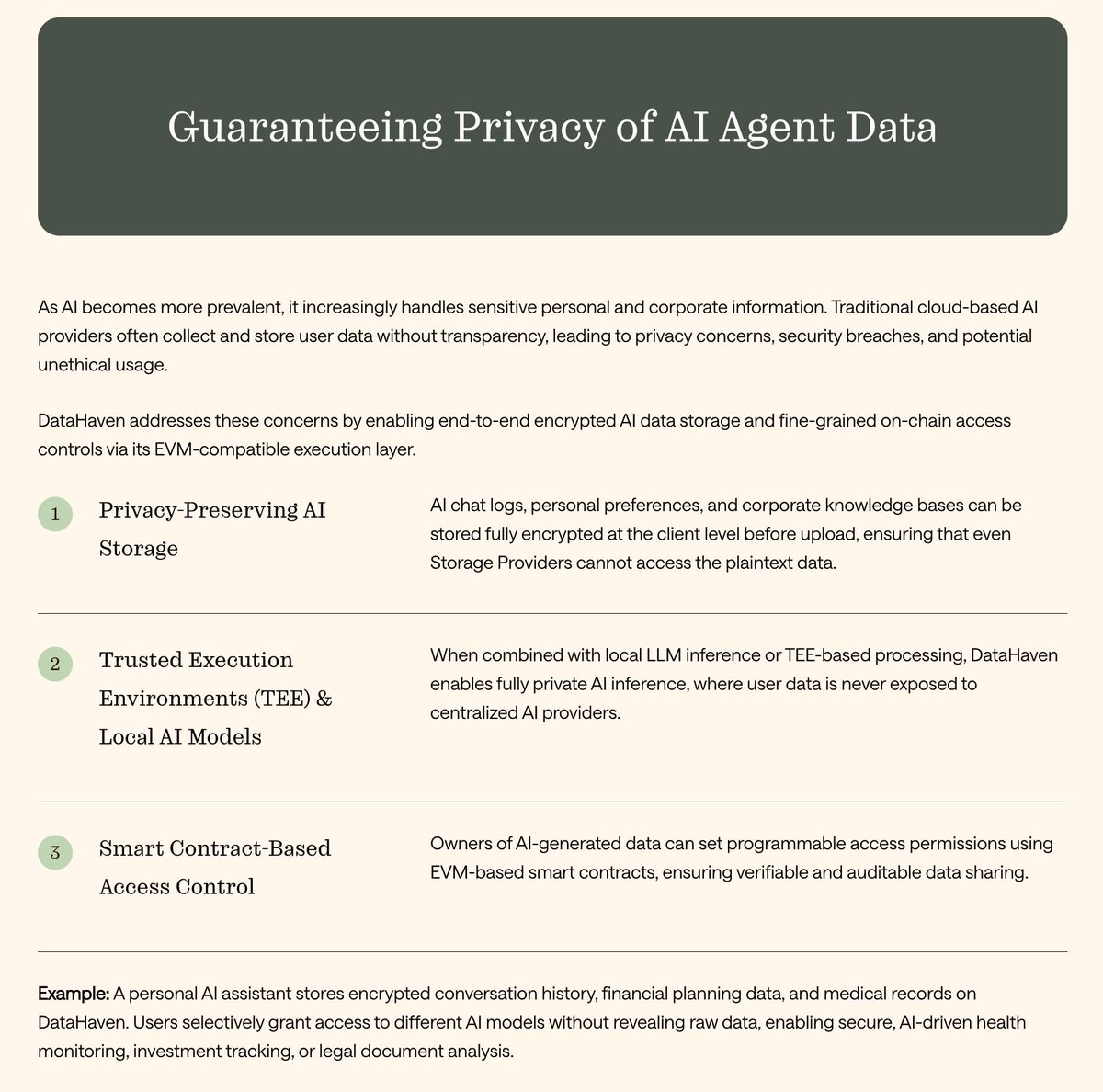
🔐 DataHaven guarantees AI agent privacy with client-side encryption, smart-contract access control & verifiable storage.Your chats, models & datasets stay encrypted, tamper-proof, and owned by you, not by centralized servers. Build, deploy & scale AI agents @DataHaven_xyz
The Holy Grail of Cryptography is here. Fully Homomorphic Encryption (FHE) lets you compute on data without ever seeing it. This is how @zama_fhe is building a confidential future where privacy is guaranteed.

There’s a subtle detail in how idOS handles encryption that makes me trust it more than 90% of Web3 apps I’ve used. Instead of storing data in plaintext or relying on some shared backend, you decrypt your own data locally and re encrypt it for each specific recipient. The…

The Future of Blockchain Security Begins with @quranium_org .” I’ve spent some time exploring quranium.org — and honestly, it’s not just another blockchain project. It feels like a vision built for a world we haven’t fully stepped into yet — the quantum era. Let me…



Ten protocol은 어떤 프라이버시 데이터를 보호 할 수 있을까? 텐프로 전문가 @KM53894님이 분석한 내용에 따르면 @tenprotocol은 기존의 다른 L2와 다르게 '기밀성'에 집중하고 있다고 함. '기밀성'은 어떤 데이터들에 적용될까 1. 거래 데이터 TEE 기반 end to end 암호화로 송금자/수신자 주소,…

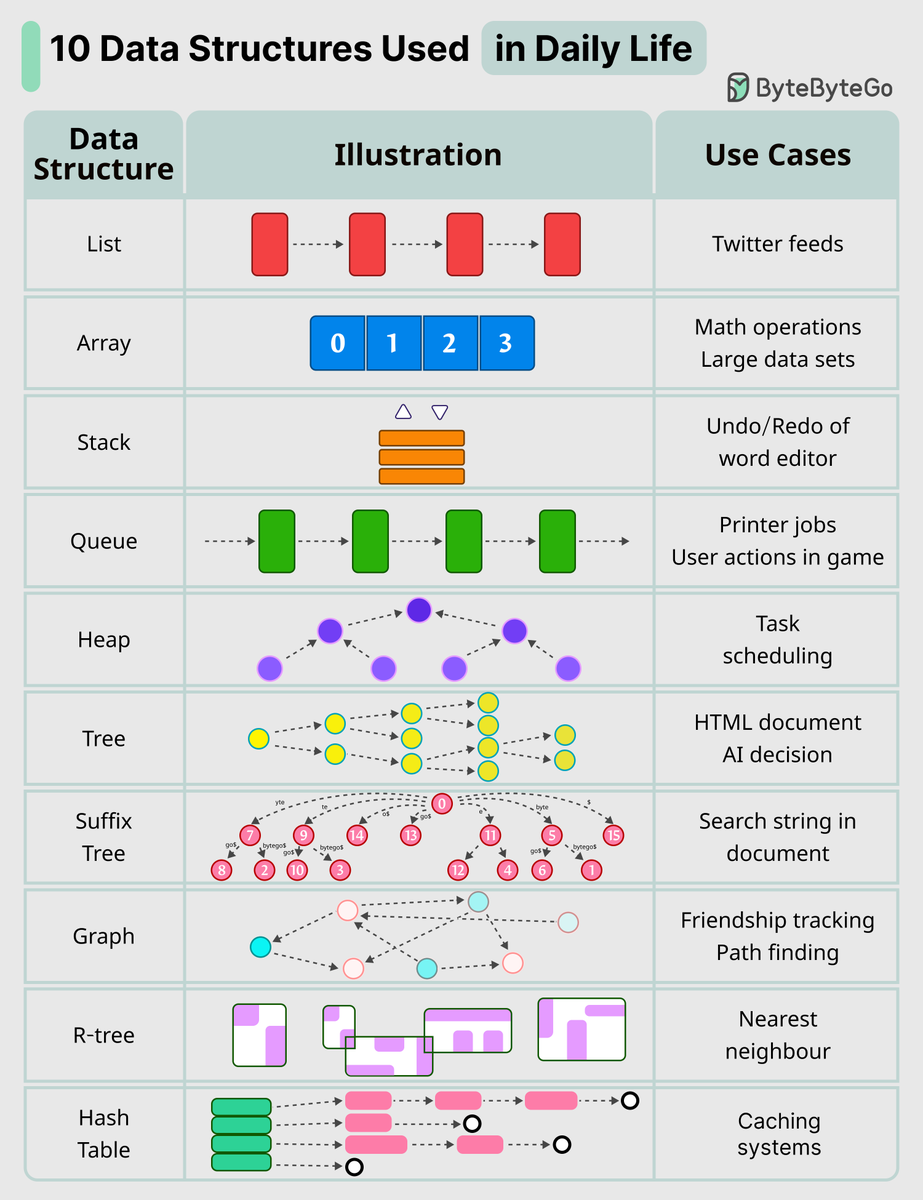
10 Key Data Structures We Use Every Day - list: keep your Twitter feeds - stack: support undo/redo of the word editor - queue: keep printer jobs, or send user actions in-game - hash table: cashing systems - Array: math operations - heap: task scheduling - tree: keep the HTML…
... @zama_fhe enables Encrypted Search onchain, allowing smart contracts to search and filter encrypted data without ever decrypting it. Instead of exposing user data or leaking metadata like most privacy systems today, Zama lets both the data and the queries remain fully…

With @zama_fhe, the rules of digital reality change: •Data stays encrypted, even while being computed. •Transparency without exposure. •Privacy not as an add-on, but as the foundation.
FHE-Native Application Architecture (Part 1) The "HTTPZ agents + ZK handoff + FHE feature store" trio. Short, clear, actionable. 1) The skeleton of the architecture (control plane / data plane) Data plane (encrypted area): Packed features with TFHE (feature store), FHE…
LayerAI: A Privacy-Preserving Framework for Decentralized Data Contribution 🧬 LayerAI introduces a modular architecture that combines LayerVPN and Data Capsules to enable secure, user-controlled participation in AI data networks. LayerVPN encrypts and anonymizes all network…
📌 5 Mining Algorithms 📌Odocrypt 📌UTXO Model 📌Community Governance Quantum Defense 🛡️ 📌Redundant and adaptive protection 📌Regularly evolving algorithm 📌Easier migration to quantum-safe cryptography #Digibyte #DGB $DGB 🛡️

Some talks about @zama_fhe ------------- ◇ Fully Homomorphic Encryption (FHE) has been theoretically accepted since 2009, but it is still very difficult to use in practice. ● High costs of computation, the cost of bootstrapping, large ciphertext sizes, difficulties with…
Why choose @zama_fhe • Web3 wasn't very private 'cause everything was out there for everyone to see. • But Fully Homomorphic Encryption, or FHE, fixes that by letting you use encrypted data in smart contracts, so you get both openness and privacy. • That means we can…

This new DeepMind research shows just how broken vector search is. Turns out some docs in your index are theoretically incapable of being retrieved by vector search, given a certain dimension count of the embedding. Plain old BM25 from 1994 outperforms it on recall. 1/4

We already know how encryption works inside @idOS_network but when does your data actually get encrypted? It happens at every stage: When verification providers issue your credentials, they encrypt them before writing to idOS. When you manually add info through the dashboard,…

7 Data Encryption Algorithms for 2023 Read More:- buff.ly/3EX5G7M #dataencryption #dataencryptionalgorithms #datasecurity #TheTechTrend
5 Data Encryption Algorithms for 2023 tinyurl.com/yy8rbtte #DataEncryption #QuantumEncryption #DataEncryptionAlgorithms #HomomorphicEncryption #PostQuantumCryptography #AI #AINews #AnalyticsInsight #AnalyticsInsightMagazine

Something went wrong.
Something went wrong.
United States Trends
- 1. #MondayMotivation 29.2K posts
- 2. Good Monday 39.8K posts
- 3. Jamaica 68K posts
- 4. Victory Monday 1,352 posts
- 5. SNAP 609K posts
- 6. #MondayVibes 2,439 posts
- 7. Category 5 17.6K posts
- 8. #MondayMood 1,284 posts
- 9. Milei 611K posts
- 10. Hurricane Melissa 41.2K posts
- 11. Tomlin 14.2K posts
- 12. Walter Reed 1,978 posts
- 13. MRIs N/A
- 14. eunwoo 50.6K posts
- 15. Cameroon 16.1K posts
- 16. #BacktoLife 30.1K posts
- 17. GameStop 60.1K posts
- 18. Hochul 24K posts
- 19. Ron Paul N/A
- 20. Tanzania 61.6K posts