#handledcyberattackssuccessfully search results
Top 5 Security Threats in E-Commerce 👉lttr.ai/ezsU #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Top 5 Security Threats in E-Commerce 👉lttr.ai/jCq4 #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Top 5 Security Threats in E-Commerce ▸ lttr.ai/Wtpq #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

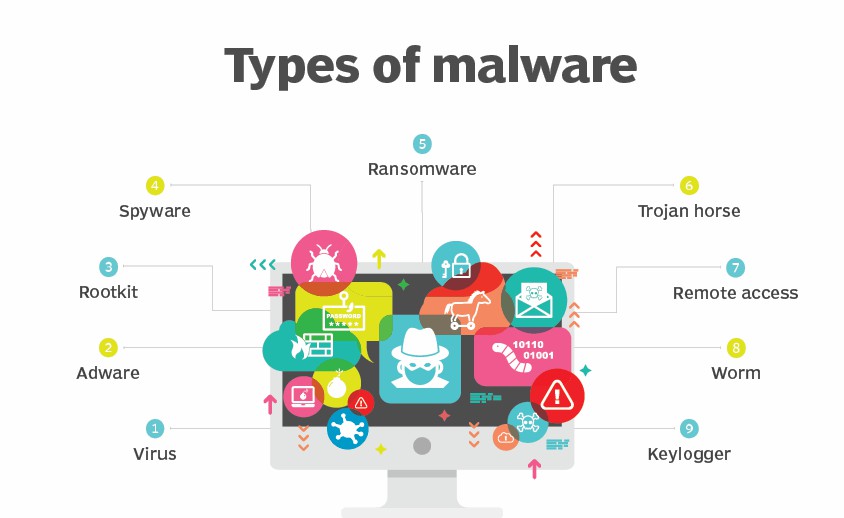
Malware is basically a kind of software to gain access to or damage a computer network developed by cyber-criminals. Read more 👉 lttr.ai/ajqP #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Top 5 Security Threats in E-Commerce Read the full article: Top 5 Security Threats in E-Commerce ▸ lttr.ai/h3Rj #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Credit card fraud is probably a classic security fraud that e-commerce sites have been facing for a very long time. Read more 👉 lttr.ai/WyZs #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

It's normally a cyber assault undertaken by rivals to leave the network source permanently or temporarily useless for its intended users. Read more 👉 lttr.ai/XAog #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud
54% of companies have experienced at least one or more successful security attacks. Read the full article: Top 5 Security Threats in E-Commerce ▸ lttr.ai/eeGg #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Wikipedia defines Bots as – “a software application that runs automated tasks (scripts) over the internet. Read the full article: Top 5 Security Threats in E-Commerce ▸ lttr.ai/mLXh #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Wikipedia defines Bots as – “a software application that runs automated tasks (scripts) over the internet. Read the full article: Top 5 Security Threats in E-Commerce ▸ lttr.ai/mLXh #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Top 5 Security Threats in E-Commerce 👉lttr.ai/jCq4 #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Top 5 Security Threats in E-Commerce 👉lttr.ai/ezsU #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

It's normally a cyber assault undertaken by rivals to leave the network source permanently or temporarily useless for its intended users. Read more 👉 lttr.ai/XAog #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Credit card fraud is probably a classic security fraud that e-commerce sites have been facing for a very long time. Read more 👉 lttr.ai/WyZs #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Top 5 Security Threats in E-Commerce ▸ lttr.ai/Wtpq #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Top 5 Security Threats in E-Commerce 👉lttr.ai/ezsU #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Top 5 Security Threats in E-Commerce 👉lttr.ai/jCq4 #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Malware is basically a kind of software to gain access to or damage a computer network developed by cyber-criminals. Read more 👉 lttr.ai/ajqP #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Top 5 Security Threats in E-Commerce ▸ lttr.ai/Wtpq #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Top 5 Security Threats in E-Commerce Read the full article: Top 5 Security Threats in E-Commerce ▸ lttr.ai/h3Rj #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Credit card fraud is probably a classic security fraud that e-commerce sites have been facing for a very long time. Read more 👉 lttr.ai/WyZs #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

54% of companies have experienced at least one or more successful security attacks. Read the full article: Top 5 Security Threats in E-Commerce ▸ lttr.ai/eeGg #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

It's normally a cyber assault undertaken by rivals to leave the network source permanently or temporarily useless for its intended users. Read more 👉 lttr.ai/XAog #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Wikipedia defines Bots as – “a software application that runs automated tasks (scripts) over the internet. Read the full article: Top 5 Security Threats in E-Commerce ▸ lttr.ai/mLXh #AdvancedMalware #e-Commerce #HandledCyberAttacksSuccessfully #CreditCardFraud

Something went wrong.
Something went wrong.
United States Trends
- 1. #GMMTV2026 4.12M posts
- 2. #csm221 1,274 posts
- 3. #OurCosmicClue_Wooyoung 19.6K posts
- 4. Good Tuesday 37.8K posts
- 5. MILKLOVE BORN TO SHINE 646K posts
- 6. Happy Thanksgiving 18.1K posts
- 7. Thankful 50.2K posts
- 8. #LUNÉSelcaDay 1,463 posts
- 9. Mark Kelly 239K posts
- 10. #LUNÉJidoriDay 1,225 posts
- 11. Mainz Biomed N/A
- 12. Alan Dershowitz 4,736 posts
- 13. Hegseth 114K posts
- 14. Taco Tuesday 13.4K posts
- 15. WILLIAMEST MAGIC VIBES 153K posts
- 16. Praying for Pedro N/A
- 17. Gone in 60 N/A
- 18. University of Minnesota N/A
- 19. Enron 2,011 posts
- 20. Frank Gore N/A



