#informationsecurityassignmenthelp نتائج البحث
🚨 Nation-state affiliated threat actors have compromised F5’s systems & downloaded portions of its BIG-IP source code—posing serious risk to FCEB agencies. Follow the guidance in ED 26-01 immediately to protect systems from potential exploits. 🔗 go.dhs.gov/isY
In this modern world the most demanded skill is cyber security. I made a full guide of Cyber Security. To get it Just: Like ❤️ Repost 🔁 Comment "CYBER" ✉️ Follow me

⚠️ @CISAgov issued 11 NEW & 2️⃣ updated public #ICS Advisories. These advisories provide info about current security issues, vulnerabilities, & exploits surrounding ICS. More at go.dhs.gov/isA

Woah - this is huge. F5 says government hackers had ‘long-term’ access to its systems, stole code and customer data Breach impacts BIG-IP dev environment and knowledge management systems. Here's what we know:
🚨 F5 Nation-State Breach — Exposure of BIG-IP Source Code & Undisclosed Vulnerabilities 🚨 F5 Networks disclosed a major supply-chain breach: a suspected nation-state threat actor gained persistent access to internal engineering and development environments. The intrusion…
I've got students messaging me asking if cybersecurity is still a "safe" field to go into because of the advancements of AI Dawg, our career value has fucking EXPLODED. Are you fuckin' with me right now? - AI vibe coded slop as far as the eye can see - AI deep fakes as far as…
Can I get a GM☕️ @idOS_network Reply guys in the building, check this out quickly ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ ☟ In idOS, instead of plaintext data, sensitive data such as credentials are encrypted on the user's device before being sent. And so, once data leaves…

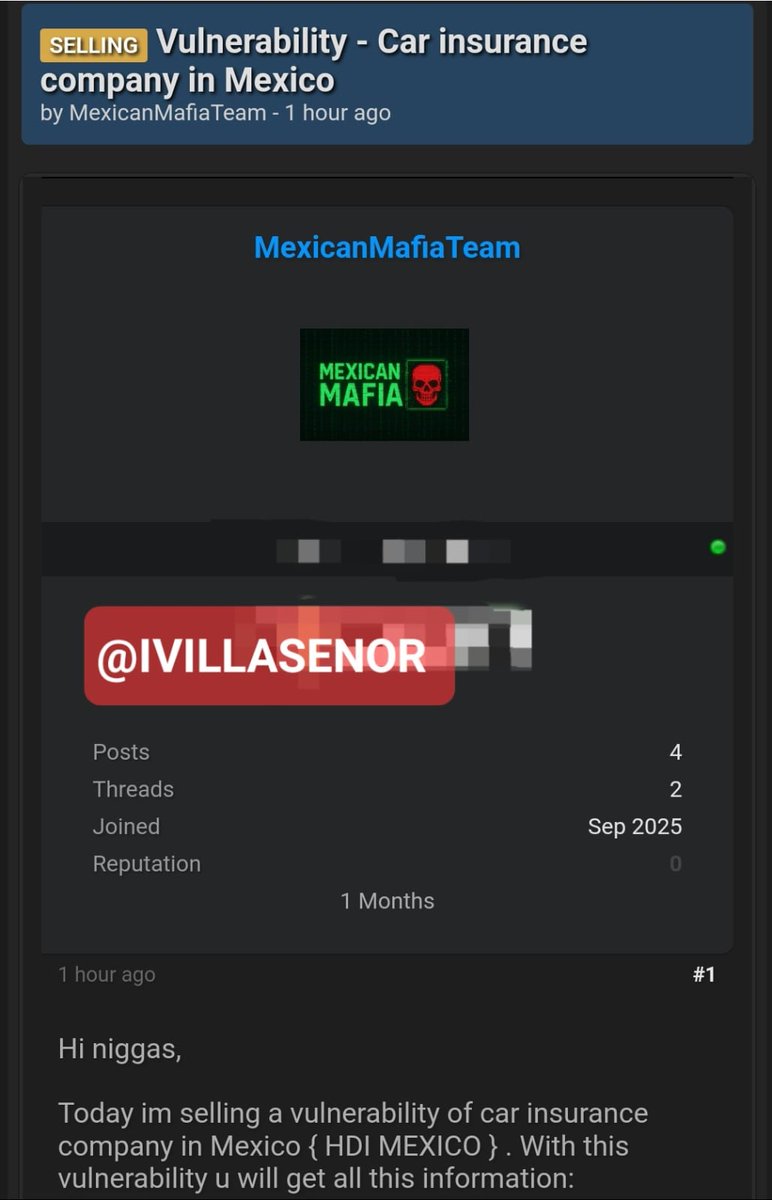
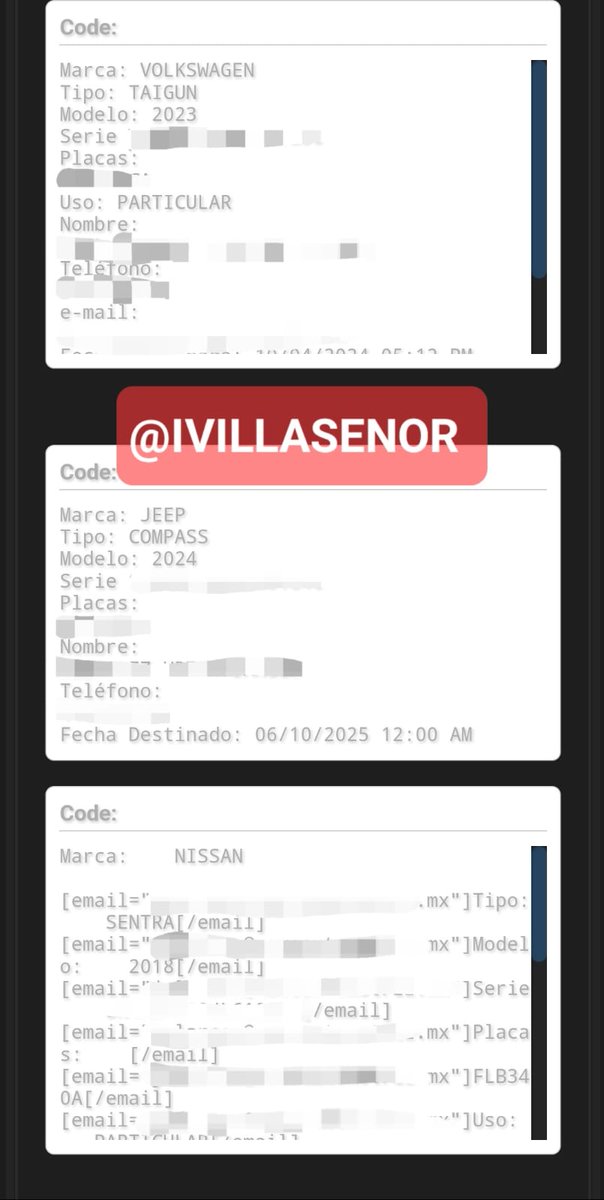
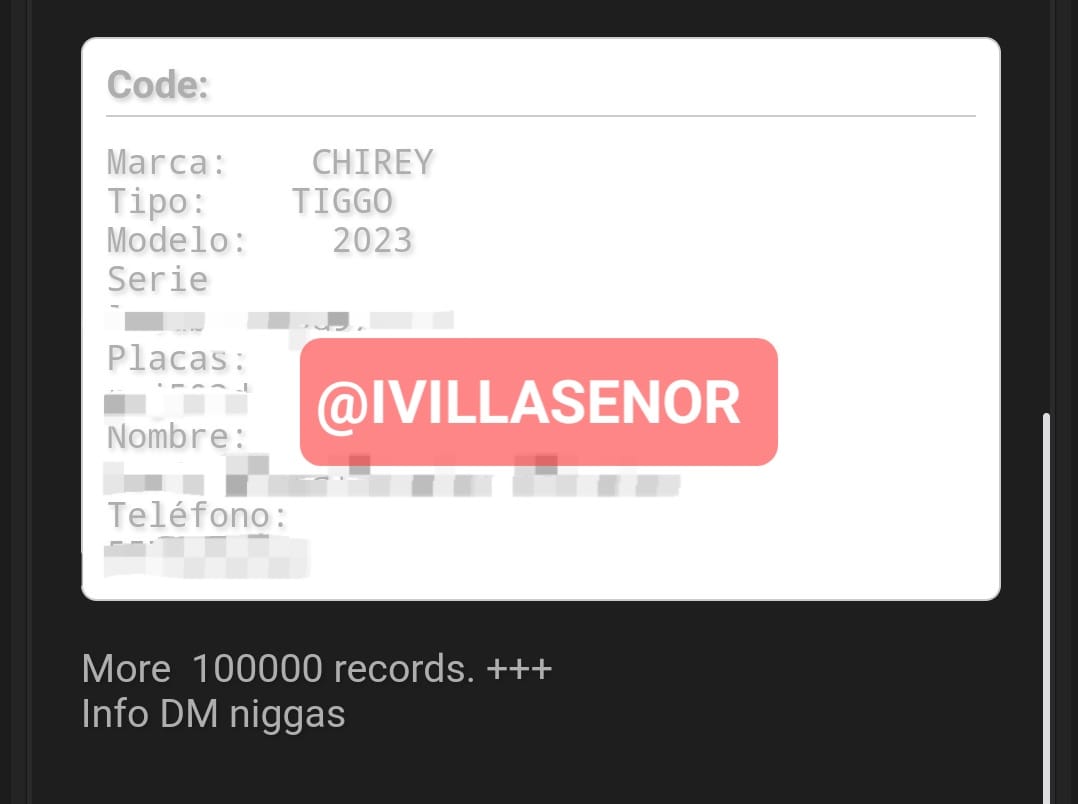
📍| «Me solicitaron investigar y contactar» Ante la venta de una vulnerabilidad para extraer los datos de todos los clientes de @HDISegurosMex, enviaron al equipo de "ciber seguridad" (SIC) a indagar. Un 'investigador' envió un mensaje al vendedor y en su tercer mensaje, al no…

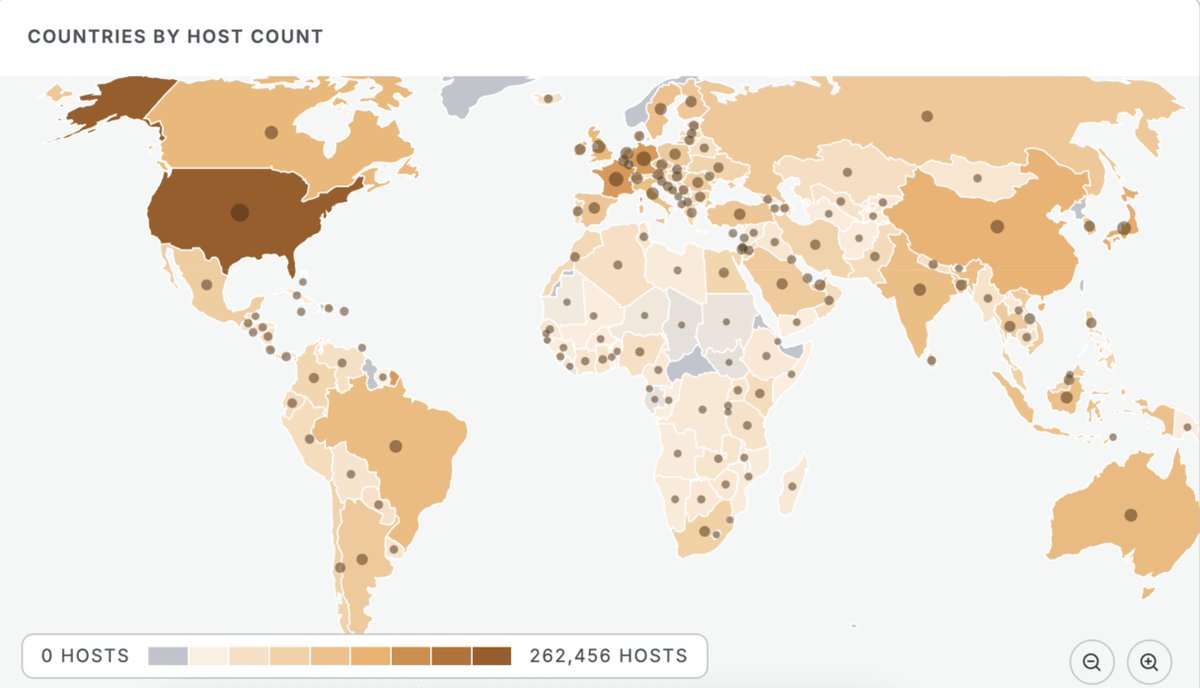
⛔️ | Peligran datos de todos los clientes mexicanos de HDI Seguros El grupo delictivo Mexican Mafia ha puesto a la venta una vulnerabilidad para extraer la información de automovilistas asegurados por @HDISegurosMex Los datos expuestos no son menores. De acuerdo con la…
You might be wondering, what security measures is @idOS_network implementing to make their one-fits-all KYC concept safe ? Let me explain to you like the 5-yr old you are 👇 Data Encryption on a personal level So idOS has a bunch of data of you and imagine some hacker breaks…

If you are interested say “I want” in the comment and I will send you a pdf copy
I beg you, in the name of God and everything you hold dear… if you’re still in your 20s, 30s, or 40s, get this book, read it from cover to cover, and apply every lesson it teaches.

Red Team Roadmap 🔴🎯 ├── Foundations │ ├── Networking Basics │ │ ├── TCP/IP & Protocol Exploitation │ │ ├── DNS & DHCP Attacks │ │ ├── Subnetting & Network Mapping │ │ └── Topology Enumeration │ ├── Operating…
Vtuber vs actual job 👩💻 I am senior cyber security specialist I do internal penetration testing, compliance, auditing, threat analysis, risk assessment, and basically anything blue team related. It is a career I worked very hard for. 13 years professional experience.


Vtuber vs actual job! ☀️ I’m a museum curator! I work with artifacts by repairing, cataloging, researching, and caring for them!


दिनांक 15/10/25 को 22वीं वाहिनी #SSB के समवाय भगवानपुर द्वारा उच्च प्राथमिक विद्यालय भगवानपुर में साइबर सुरक्षा जागरूकता कार्यक्रम आयोजित किया गया कार्यक्रम में छात्रों को ऑनलाइन धोखाधड़ी फर्जी लिंक गलत ऐप डाउनलोड एवं साइबर अपराध से बचाव के उपायों की जानकारी दी गई #ssbftrluckhnow




Good morning friends happy mornings Today I want to talk a little about @idOS_network approach to data security Data protection isn't just about encryption what matters is how, where, and with whom it is shared. In our system, every file is protected with advanced AES 256…
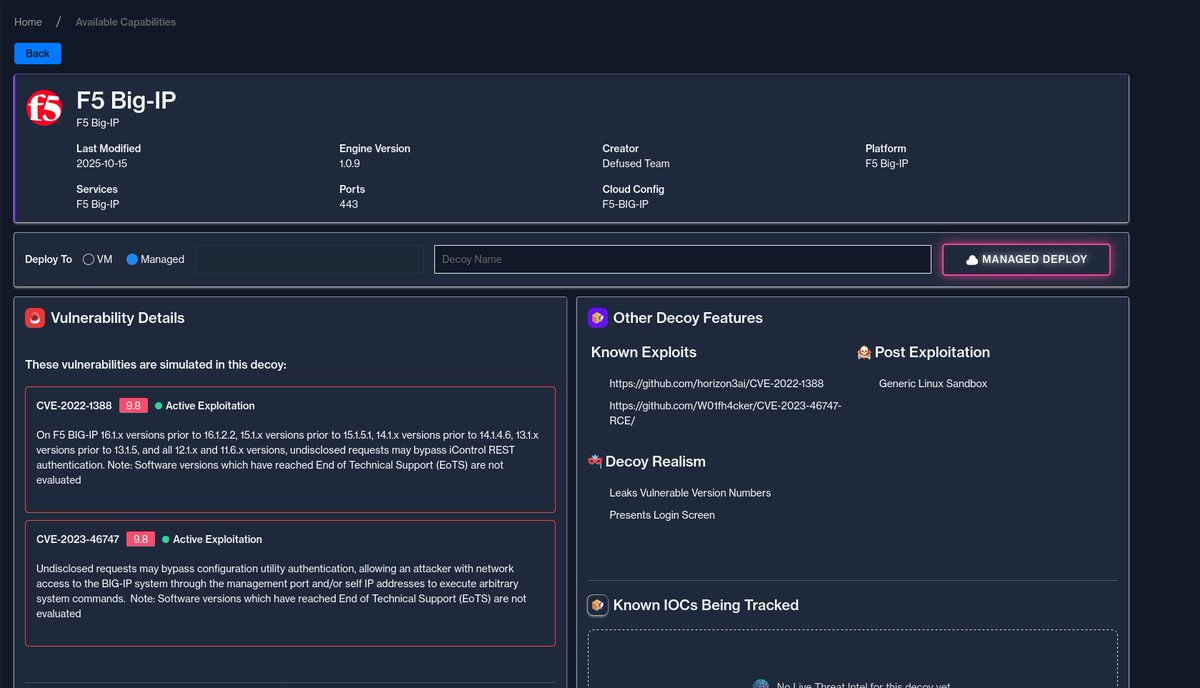
Breach Alert 🚨 A nation-state actor has exfiltrated BIG-IP source code and other sensitive data from F5. F5 has released multiple patches, but the impact remains unclear We have added the F5 Big-IP honeypot for Defused Free users for a limited time - take advantage! 🍯
What really bothers me is that neither F5’s statement nor the attestation letters from NCC Group or IOActive mention when the breach actually happened. They only say that F5 “learned” about it in August 2025. That’s not when it started. There must be forensic evidence pointing…
Earlier this week, we kicked off an engaging cybersecurity and digital safety training program for @kabuniversity administrators and staff, a crucial step toward empowering university leaders and administrators to champion cybersecurity best practices and foster a safer,…




i just Updated my XSS article: added some cleaner, more effective one-liners and integrated DalFox one-liners that support extra options. Check it out. infosecwriteups.com/find-xss-vulne…
Information Security is the practice of protecting information by easing information risks. The students who are learning this subject can opt for Information Security Assignment Help from experts of BookMyEssay. Visit: bit.ly/3CIUHg9 #informationsecurityassignmenthelp

#Network security is one of the most significant aspects to consider when working over the internet, LAN, or other techniques, no matter how small or big your trade is. bit.ly/3wvRFr8 #informationsecurityassignmenthelp #assignmenthelp #writingservices

✔️ Information Security and Cyber Security: A Review on the Difference 👉 Read more here: bit.ly/2YYqarj 🙂 Flat Offers on Your First Assignment! #InformationSecurityAssignmentHelp #HelpwithAssignment #AssignmentPaper #BuyAssignmentOnline

Complied List of Tips to Deal with the Cyber Security | You can buy assignment on information security subjects from BookMyEssay site. Read more here: bit.ly/2ZnEfym Ring at: +1(240)8399485 #informationsecurityassignmenthelp #helpwithassignmentwriting

#Network security is one of the most significant aspects to consider when working over the internet, LAN, or other techniques, no matter how small or big your trade is. bit.ly/3wvRFr8 #informationsecurityassignmenthelp #assignmenthelp #writingservices

✔️ Information Security and Cyber Security: A Review on the Difference 👉 Read more here: bit.ly/2YYqarj 🙂 Flat Offers on Your First Assignment! #InformationSecurityAssignmentHelp #HelpwithAssignment #AssignmentPaper #BuyAssignmentOnline

Complied List of Tips to Deal with the Cyber Security | You can buy assignment on information security subjects from BookMyEssay site. Read more here: bit.ly/2ZnEfym Ring at: +1(240)8399485 #informationsecurityassignmenthelp #helpwithassignmentwriting

Information Security is the practice of protecting information by easing information risks. The students who are learning this subject can opt for Information Security Assignment Help from experts of BookMyEssay. Visit: bit.ly/3CIUHg9 #informationsecurityassignmenthelp

Information Security is practice of preventing unauthorized access, use, disclosure, disruption or modification of information. Students can ask for information security assignment help from experts of BookMyEssay. Visit: bit.ly/3ofGGBu #informationsecurityassignmenthelp

Something went wrong.
Something went wrong.
United States Trends
- 1. Flacco 32.5K posts
- 2. Bengals 49K posts
- 3. Bengals 49K posts
- 4. Rodgers 28K posts
- 5. Ramsey 11.6K posts
- 6. Chase 89.6K posts
- 7. Tomlin 7,721 posts
- 8. Max Scherzer 7,761 posts
- 9. #TNFonPrime 3,362 posts
- 10. Ace Frehley 74K posts
- 11. DJ Turner 2,065 posts
- 12. Cuomo 61.1K posts
- 13. #HereWeGo 7,919 posts
- 14. #WhoDey 3,352 posts
- 15. #PITvsCIN 3,796 posts
- 16. #911onABC 15.3K posts
- 17. Zac Taylor 1,381 posts
- 18. Bolton 188K posts
- 19. Sliwa 27.5K posts
- 20. Metcalf 5,236 posts























