#kernel_security resultados de búsqueda
#Kernel_Security Oops! It's a kernel stack use-after-free: Exploiting NVIDIA's GPU Linux drivers blog.quarkslab.com/nvidia_gpu_ker… // This article details two bugs (CVE-2025-23300, CVE-2025-23280) in the NVIDIA Linux Open GPU Kernel Modules and demonstrates how they can be exploited. The…
#tools #reversing #Kernel_Security Using MCP for Debugging, Reversing, and Threat Analysis Part 0 - AI Meets WinDBG - svnscha.de/posts/ai-meets… ]-> MCP Server for WinDbg Crash Analysis - github.com/svnscha/mcp-wi… Part 1 - Setting up VS Code, MCP Server, and WinDbg crashdump analysis…
#reversing #Kernel_Security Driver Reverse Engineering 101 Part 1 - WDM - eversinc33.com/posts/driver-r… Part 2 - Unpacking a VMProtected Boot Driver - eversinc33.com/posts/driver-r… // A step-by-step method to unpack VMProtect v2-3 protected kernel drivers by restoring the IAT through…
#reversing #Kernel_Security #Hardware_Security "Training Solo: On the Limitations of Domain Isolation Against Spectre-v2 Attacks", 2025. ]-> Open-source tooling, test cases, and PoC exploits - github.com/vusec/training… // The paper presents three new Spectre attack variants that…
#Kernel_Security #Malware_analysis 1⃣ BombShell: The Signed Backdoor Hiding in Plain Sight on Framework Devices eclypsium.com/blog/bombshell… 2⃣ Singularity: Deep Dive into a Modern Stealth Linux Kernel Rootkit blog.kyntra.io/Singularity-A-… ]-> Full Source Code - github.com/MatheuZSecurit… 3⃣…
#exploit #Kernel_Security 1. CVE-2025-22056: The tragedy of Netfilter Tunnel - dawnslab.jd.com/CVE-2025-22056 2. CVE-2023-52922: UaF in CAN BCM subsystem leading to information disclosure - allelesecurity.com/use-after-free… 3. CVE-2025-22037: Remote NULL Deref in Linux KSMBD -…
#tools #Kernel_Security Linux Kernel Runtime Guard (LKRG), v.1.0. ]-> lkrg.org ]-> github.com/lkrg-org/lkrg // LKRG - kernel module that performs runtime integrity checking of the kernel and detection of security vulnerability exploits against the kernel,…
#Kernel_Security 1⃣. NT OS Kernel Information Disclosure Vulnerability (CVE-2025-53136, CVE-2024-43511) - crowdfense.com/nt-os-kernel-i… // A race condition in Windows' "NtQuerySystemInformation()" allows kernel address leaks and potential privilege escalation across recent versions…
#exploit #Kernel_Security Defeating KASLR by Doing Nothing at All googleprojectzero.blogspot.com/2025/11/defeat… // The Linux kernel's static, predictable linear mapping on Android devices undermines KASLR's effectiveness, enabling potential exploitation despite address randomization efforts
#exploit #Kernel_Security Ksmbd Vulnerability Research Part 1 - CVE-2024-50283, CVE-2024-50285, CVE-2024-50286 - blog.doyensec.com/2025/01/07/ksm… Part 2 - Fuzzing Improvements and Vulnerability Discovery - blog.doyensec.com/2025/09/02/ksm… Part 3 - Exploiting CVE-2025-37947 -…
#exploit #Kernel_Security OtterRoot: Netfilter Universal Root 1-day osec.io/blog/2024-11-2… ]-> PoC: github.com/otter-sec/Otte…
github.com
OtterRoot/universal/exploit.c at master · otter-sec/OtterRoot
Universal root exploit for the linux kernel. Contribute to otter-sec/OtterRoot development by creating an account on GitHub.
#Kernel_Security #Hardware_Security "Heracles: Chosen Plaintext Attack on AMD SEV-SNP", 2025. ]-> github.com/heracles-attack // In our case studies, we leak kernel memory, crypto keys, and user passwords, as well as demonstrate web session hijacking
#Kernel_Security Linux Kernel netfilter: ipset: Missing Range Check LPE ssd-disclosure.com/linux-kernel-n… // A vulnerability in Linux kernel's ipset allows out-of-bounds memory writes via crafted IP ranges, enabling privilege escalation and requiring immediate kernel updates
#Fuzzing #Kernel_Security #Mobile_Security Android Binder Fuzzing androidoffsec.withgoogle.com/posts/binder-f… ]-> fuzzer source code - github.com/lkl/linux/pull… ]-> example test case - github.com/lkl/linux/blob… ]-> Reproducing CVE-2023-20938 - github.com/lkl/linux/blob… ]-> libdevbinder (Linux/Android on…
#Infographics #Kernel_Security Linux Kernel Defence Map (v.6.10) github.com/a13xp0p0v/linu… // shows the relationships between vulnerability classes, exploitation techniques, bug detection mechanisms, and defence technologies
#exploit #Kernel_Security CVE-2025-38236: From Chrome renderer code exec to kernel with MSG_OOB googleprojectzero.blogspot.com/2025/08/from-c… ]-> PoC code - project-zero.issues.chromium.org/issues/4230239… // Chrome's Linux desktop renderer sandbox exposes kernel attack surface that is never legitimately used in the sandbox
#Whitepaper #Kernel_Security #Cyber_Education "Comprehensive Kernel Debugging for Windows Developers", SANS 2025. See also: ]-> Uncovering Hidden Threats: github.com/j00ru/windows-…
#reversing #Kernel_Security Driver Reverse Engineering 101 Part 1 - WDM - eversinc33.com/posts/driver-r… Part 2 - Unpacking a VMProtected Boot Driver - eversinc33.com/posts/driver-r… // A step-by-step method to unpack VMProtect v2-3 protected kernel drivers by restoring the IAT through…
#tools #reversing #Kernel_Security Using MCP for Debugging, Reversing, and Threat Analysis Part 0 - AI Meets WinDBG - svnscha.de/posts/ai-meets… ]-> MCP Server for WinDbg Crash Analysis - github.com/svnscha/mcp-wi… Part 1 - Setting up VS Code, MCP Server, and WinDbg crashdump analysis…
#exploit #Kernel_Security Defeating KASLR by Doing Nothing at All googleprojectzero.blogspot.com/2025/11/defeat… // The Linux kernel's static, predictable linear mapping on Android devices undermines KASLR's effectiveness, enabling potential exploitation despite address randomization efforts
#Kernel_Security Oops! It's a kernel stack use-after-free: Exploiting NVIDIA's GPU Linux drivers blog.quarkslab.com/nvidia_gpu_ker… // This article details two bugs (CVE-2025-23300, CVE-2025-23280) in the NVIDIA Linux Open GPU Kernel Modules and demonstrates how they can be exploited. The…
#reversing #Kernel_Security #Hardware_Security "Training Solo: On the Limitations of Domain Isolation Against Spectre-v2 Attacks", 2025. ]-> Open-source tooling, test cases, and PoC exploits - github.com/vusec/training… // The paper presents three new Spectre attack variants that…
#Kernel_Security #Malware_analysis 1⃣ BombShell: The Signed Backdoor Hiding in Plain Sight on Framework Devices eclypsium.com/blog/bombshell… 2⃣ Singularity: Deep Dive into a Modern Stealth Linux Kernel Rootkit blog.kyntra.io/Singularity-A-… ]-> Full Source Code - github.com/MatheuZSecurit… 3⃣…
#exploit #Kernel_Security Ksmbd Vulnerability Research Part 1 - CVE-2024-50283, CVE-2024-50285, CVE-2024-50286 - blog.doyensec.com/2025/01/07/ksm… Part 2 - Fuzzing Improvements and Vulnerability Discovery - blog.doyensec.com/2025/09/02/ksm… Part 3 - Exploiting CVE-2025-37947 -…
#Fuzzing #Kernel_Security #Mobile_Security Android Binder Fuzzing androidoffsec.withgoogle.com/posts/binder-f… ]-> fuzzer source code - github.com/lkl/linux/pull… ]-> example test case - github.com/lkl/linux/blob… ]-> Reproducing CVE-2023-20938 - github.com/lkl/linux/blob… ]-> libdevbinder (Linux/Android on…
#tools #Kernel_Security Linux Kernel Runtime Guard (LKRG), v.1.0. ]-> lkrg.org ]-> github.com/lkrg-org/lkrg // LKRG - kernel module that performs runtime integrity checking of the kernel and detection of security vulnerability exploits against the kernel,…
#Kernel_Security 1⃣. NT OS Kernel Information Disclosure Vulnerability (CVE-2025-53136, CVE-2024-43511) - crowdfense.com/nt-os-kernel-i… // A race condition in Windows' "NtQuerySystemInformation()" allows kernel address leaks and potential privilege escalation across recent versions…
#exploit #Kernel_Security Exploiting eneio64.sys Kernel Driver on Windows 11 by Turning Physical Memory R/W into Virtual Memory R/W xacone.github.io/eneio-driver.h… ]-> Exploit for eneio64.sys Kernel Driver // a walkthrough of designing a POC for exploiting CVE-2020-12446, a…
#Whitepaper #Kernel_Security #Cyber_Education "Comprehensive Kernel Debugging for Windows Developers", SANS 2025. See also: ]-> Uncovering Hidden Threats: github.com/j00ru/windows-…
#Kernel_Security Linux Kernel netfilter: ipset: Missing Range Check LPE ssd-disclosure.com/linux-kernel-n… // A vulnerability in Linux kernel's ipset allows out-of-bounds memory writes via crafted IP ranges, enabling privilege escalation and requiring immediate kernel updates
#Events #Research #Kernel_Security 34th USENIX Security Symposium: "System Register Hijacking: Compromising Kernel Integrity By Turning System Registers Against the System", 2025. ]-> Artifacts - zenodo.org/records/151464… // ..While all of our techniques present new avenues for…
#exploit #Kernel_Security CVE-2025-38236: From Chrome renderer code exec to kernel with MSG_OOB googleprojectzero.blogspot.com/2025/08/from-c… ]-> PoC code - project-zero.issues.chromium.org/issues/4230239… // Chrome's Linux desktop renderer sandbox exposes kernel attack surface that is never legitimately used in the sandbox
#Kernel_Security #Hardware_Security "Heracles: Chosen Plaintext Attack on AMD SEV-SNP", 2025. ]-> github.com/heracles-attack // In our case studies, we leak kernel memory, crypto keys, and user passwords, as well as demonstrate web session hijacking
#Kernel_Security DEF CON 33: "Infecting the Boot to Own the Kernel: Bootkits and Rootkits Development". ]-> UEFI Bootkit - github.com/TheMalwareGuar… ]-> Kernel-Mode Rootkit - github.com/TheMalwareGuar… ]-> Every resource you need to develop Bootkits/Rootkits - github.com/TheMalwareGuar……
github.com
GitHub - TheMalwareGuardian/Abyss: Windows UEFI Bootkit
Windows UEFI Bootkit. Contribute to TheMalwareGuardian/Abyss development by creating an account on GitHub.
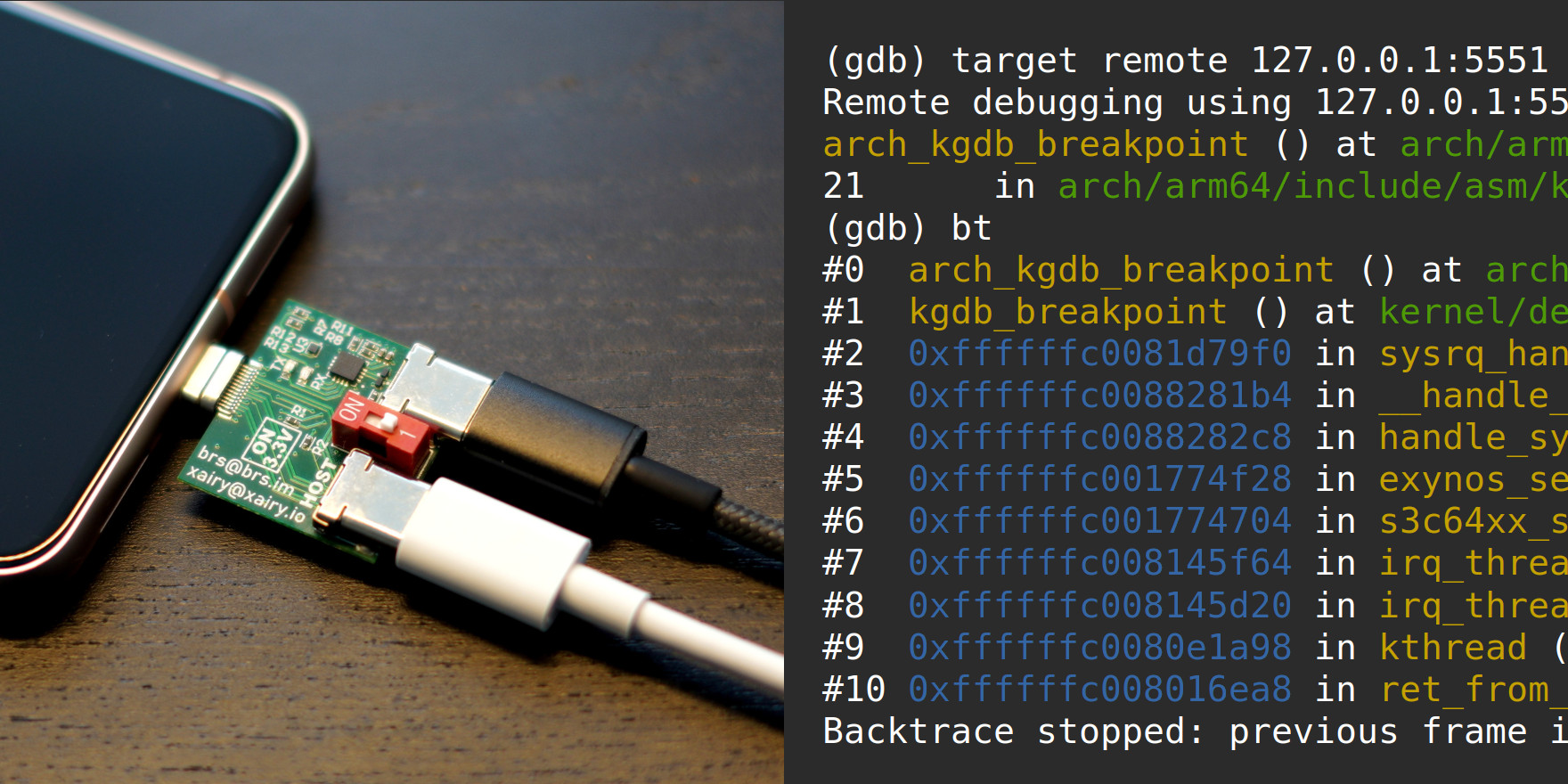
#reversing #Kernel_Security Debugging the Pixel 8 kernel via KGDB xairy.io/articles/pixel… // The instructions cover building and flashing a custom Pixel 8 kernel to enable KGDB, breaking into KGDB either via ADB by relying on /proc/sysrq-trigger or purely over a serial…
#Events #Fuzzing #Kernel_Security "Bypassing Kernel Barriers: Fuzzing Linux Kernel in Userspace with Linux Kernel Library", LSSNA 2025. ]-> A collection of user-space Linux kernel specific guided fuzzers based on LKL - github.com/atrosinenko/kb… ]-> Linux Security Summit North…
#exploit #Kernel_Security 1. CVE-2025-22056: The tragedy of Netfilter Tunnel - dawnslab.jd.com/CVE-2025-22056 2. CVE-2023-52922: UaF in CAN BCM subsystem leading to information disclosure - allelesecurity.com/use-after-free… 3. CVE-2025-22037: Remote NULL Deref in Linux KSMBD -…
Something went wrong.
Something went wrong.
United States Trends
- 1. Comet 26.6K posts
- 2. Amorim 48.4K posts
- 3. Ugarte 12.5K posts
- 4. Sun Belt Billy N/A
- 5. West Ham 18.3K posts
- 6. Manchester United 46.7K posts
- 7. #MUFC 20.8K posts
- 8. Sac State N/A
- 9. #MUNWHU 7,533 posts
- 10. Brennan Marion 1,401 posts
- 11. Cunha 16.8K posts
- 12. Eurovision 166K posts
- 13. Mainoo 12.6K posts
- 14. Buster Faulkner 1,514 posts
- 15. Fame 53.3K posts
- 16. Dalot 12K posts
- 17. Brian Cole 56.1K posts
- 18. Obamacare 27.3K posts
- 19. Ingram 2,266 posts
- 20. Dorgu 5,862 posts