#blockchainsecurityissues Suchergebnisse
Wow, that's concerning! A single user with so much power? #BlockchainSecurityIssues
Decentralization != Security. I suggest this site about the security budget issue and the risks of 51% attacks: budget.day
#BlockSafeChain pretends to secure user assets while silently draining deposits through hidden fees. Stay alert. Dm me for recovery assistance. #scam #cryptoscam #NFT #cryptorecovery

Big step for consumer UX, but the Terms of Use quietly highlight the elephant in the room regarding wallet architecture imo. Transaction Shield is a great safety net against scams, but the explicit exclusion of "Compromised wallets" (malware, phishing, stolen keys) is the…
Great resource for security researchers 🫡 Blockchain-Attack-Vectors provides a structured breakdown of exploit primitives, consensus-level risks, VM quirks, and smart-contract vulnerability categories. A solid reference for audit methodologies 👇 github.com/ImmuneBytes-Se…
🧭 The CSO story covered what happened. LinuxSecurity covers why it keeps happening. Registry weaknesses are the real problem to fix. #opensrc #netsec #linuxsec bit.ly/3X3Z8NQ

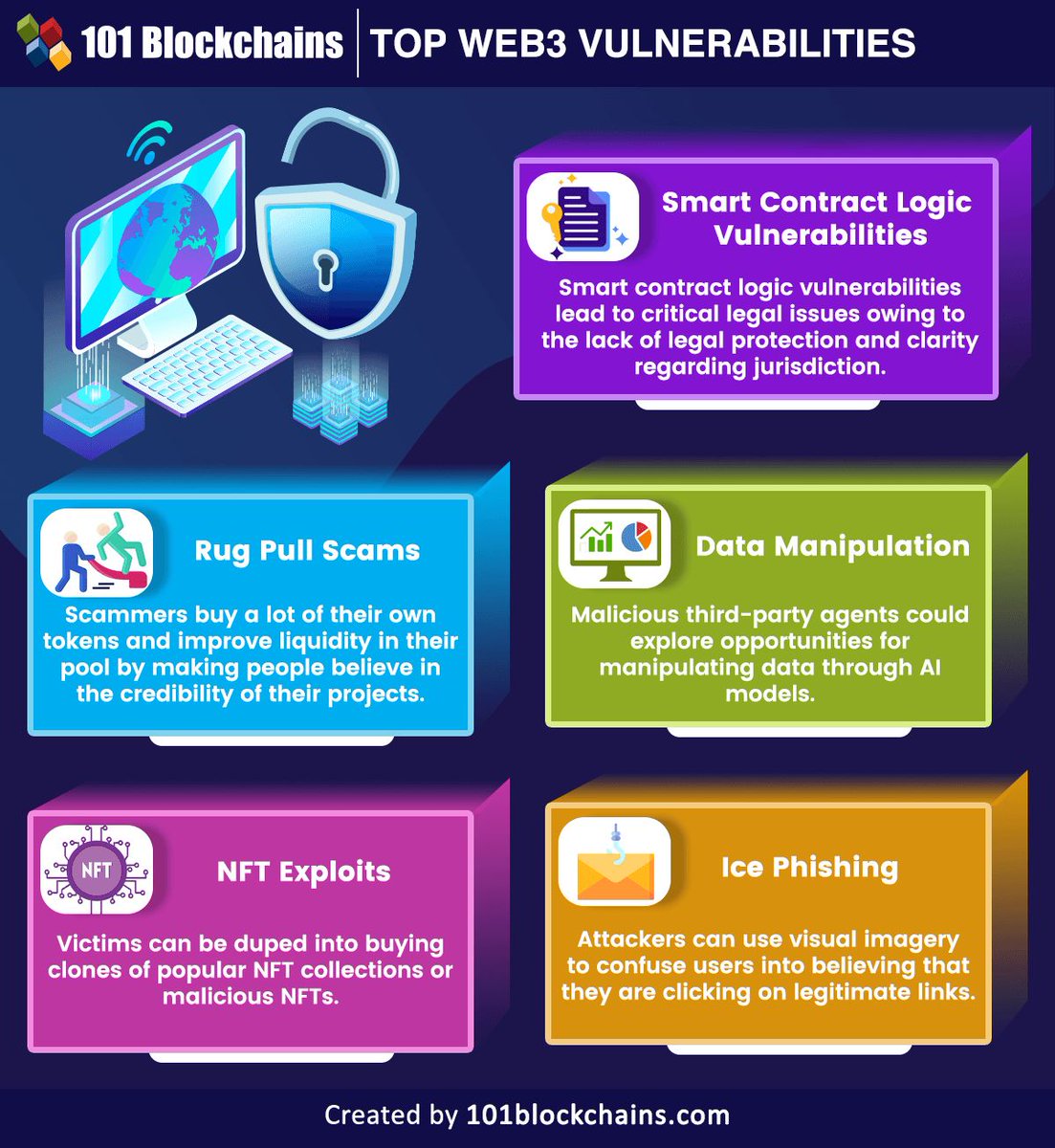
Web3 vulnerabilities are starting to become problematic issues for Web3 projects. Therefore, it is important to examine them to understand the challenges and solutions. Source @101Blockchains Link buff.ly/3vnWV5f rt @antgrasso #web3 #blockchain
the issue with this equation is bad actors will always have more economic incentive to find exploits [with ai compute] safe blockspace is the only feasible answer, designing a system that does not accept theft as a valid action
We're currently experiencing network issues preventing some Blockstream app users from logging into specific accounts. Our team is working on a fix. Funds are secure. Follow this post for updates.
2/ Key threats to watch: 📍 Malicious approvals 📍 Phishing & fake platforms 📍 Investment scams After a #hack, funds rarely stay in the first wallet attackers follow typical laundering patterns, visible on-chain.
💡 Why that matters: many blockchain hacks don’t come from the chain — they come from compromised endpoints: malware, ransomware, keyloggers, root-level attacks. @Abatis_ABTU closes that gap.

4/5 | 🐋 Security Security Headline: “We were hacked, withdrawals suspended.” Trust vanishes overnight.The Ledger Connect Kit Exploit and major bridge hacks (@CurveFinance, @Orbiter_Finance ) showed that even battle-tested protocols are vulnerable to supply chain attacks and…

For any complex, high value protocol like a cross chain P2P hub, the greatest security threat isn’t a simple coding error it’s the deliberate insertion of cleverly obfuscated vulnerabilities. Malicious developers can strategically embed backdoors deep within the smart contract…

The true structural story of @Ensofi_xyz lies in its strategic interoperability. As a Cross chain DeFi Hub , they associate with entities like Radiant Capital , which relies heavily on LayerZero for omnichain lending. This proves they are strategically plugging into the highest…

Key vulnerabilities include: - No comprehensive regulatory framework for crypto and stablecoins. - Potential to bypass exchange control laws. - Limited oversight of cross-border transactions #Stablecoins #CryptoRegulation
Beyond Is Solving The One Problem Everyone Ignores Until It’s Too Late Nobody cared about bridge security until more than 2.5b vanished in hacks over the past three years. every time it’s the same pattern: stolen keys, rogue validators, replayed signatures, or wrapped assets…
Every chain has strengths, but the data shows one thing clearly: Security is not solved yet. Attackers evolve faster than protocols. We’ll keep tracking, verifying, and exposing risks so users stay safe no matter the chain they’re on. Stay vigilant.
The issue in crypto has been that people have pretended there was security against physical attacks. Which led to teams building permissionless, decentralized TEE networks. Which simply does not bring any security. Only one dishonest actor is required to undermine all security.
The vulnerability was the cook() function, which batches multiple actions (borrow, repay, deposit) atomically. When attackers passed an undefined action (Action 0), it reset the needsSolvencyCheck flag to false, skipping the solvency verification entirely.
Smart contract security is not enough. We break down 3 patterns we’ve seen across countless audits: ⚠️ Split-call workflows ⚠️ State drift between chain & DB ⚠️ Business logic gaps between frontend & contract Each opens critical vulnerabilities.
Something went wrong.
Something went wrong.
United States Trends
- 1. Pat Spencer 2,008 posts
- 2. Jimmy Butler 2,280 posts
- 3. Podz 2,632 posts
- 4. Kerr 4,435 posts
- 5. Seth Curry 3,176 posts
- 6. Mark Pope 1,801 posts
- 7. Hield 1,310 posts
- 8. Derek Dixon 1,148 posts
- 9. #DubNation 1,287 posts
- 10. Carter Hart 3,568 posts
- 11. Brunson 7,230 posts
- 12. Connor Bedard 2,038 posts
- 13. Knicks 14.1K posts
- 14. Kentucky 29.4K posts
- 15. Caleb Wilson 1,078 posts
- 16. Celtics 15.9K posts
- 17. Jaylen Brown 8,439 posts
- 18. Notre Dame 38.3K posts
- 19. Bama 24.6K posts
- 20. Van Epps 129K posts