#urlnormalizationattack search results
URL Normalization Turns a Harmless Request into a Cache-Poisoned XSS Attack Link: bashoverflow.com/url-normalizat… #webcachepoisoning #urlnormalizationattack #urlnormalization #cachepoisoningattack #cachebasedXSS #bugbounty

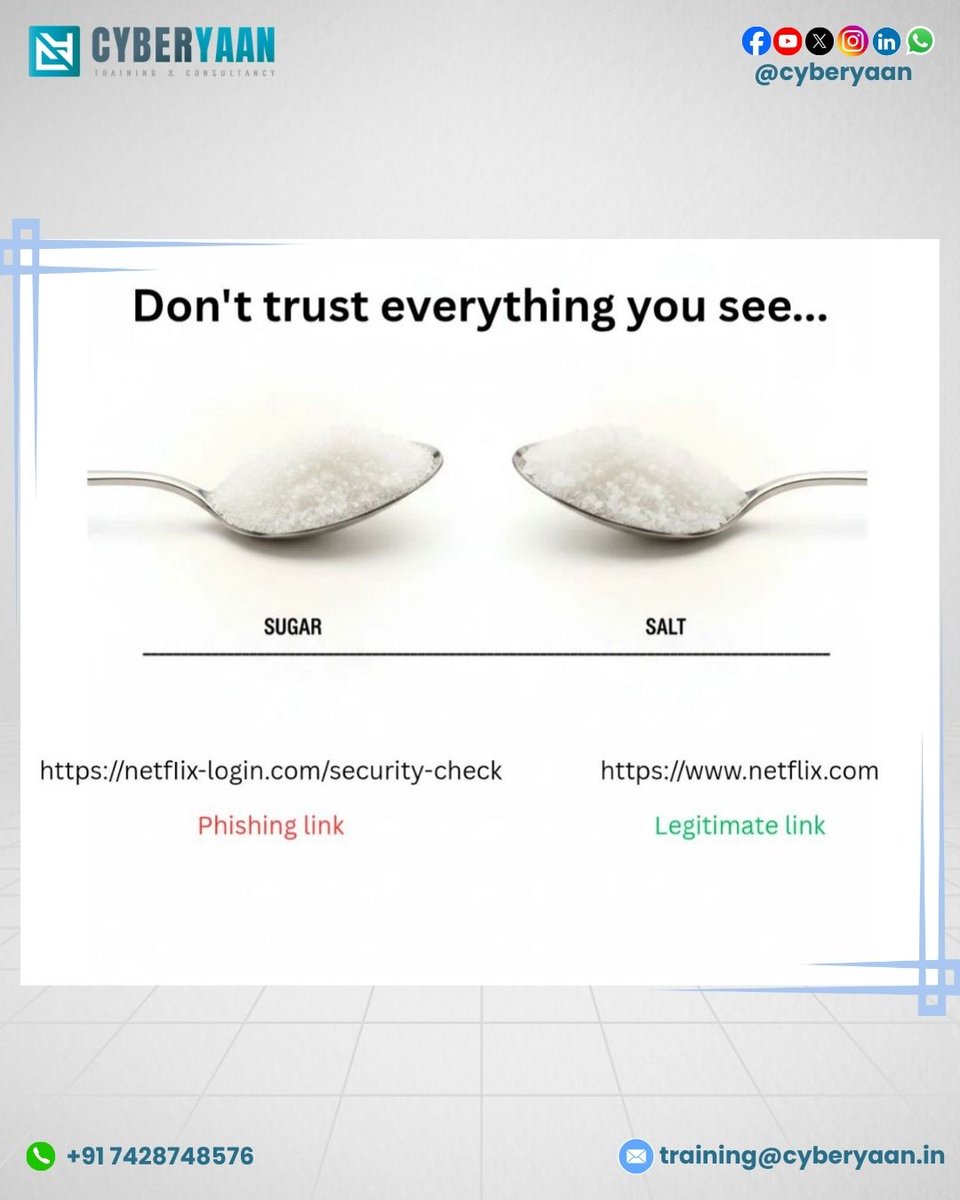
A Tiny Change in a URL Can Lead to a Big Cyberattack. Just like sugar and salt look almost the same, phishing links often look identical to genuine websites. ❌ Example of a Phishing Link lnkd.in/eja4_Acp ✔️ Example of a Legitimate Link netflix.com #CyberYaan
I completed the Web Security Academy lab: Exploiting origin server normalization for web cache deception @WebSecAcademy portswigger.net/web-security/w…
Attack of the Day: Directory Listing: your files, on display. Misconfigured web servers reveal file indexes, leaking data and helping attackers map targets. Keep those doors locked, or I’ll be finding more than your house keys
怎么防?手敲真的官方域名,被重定向到利用 Punycode 技巧的钓鱼域名。如图这个视频,感谢 @roffett_eth 提供。 比如: plasma .to 变成 plasmą .to balancer .fi 变成 bǎlancer .fi 这种同形攻击(Homograph…
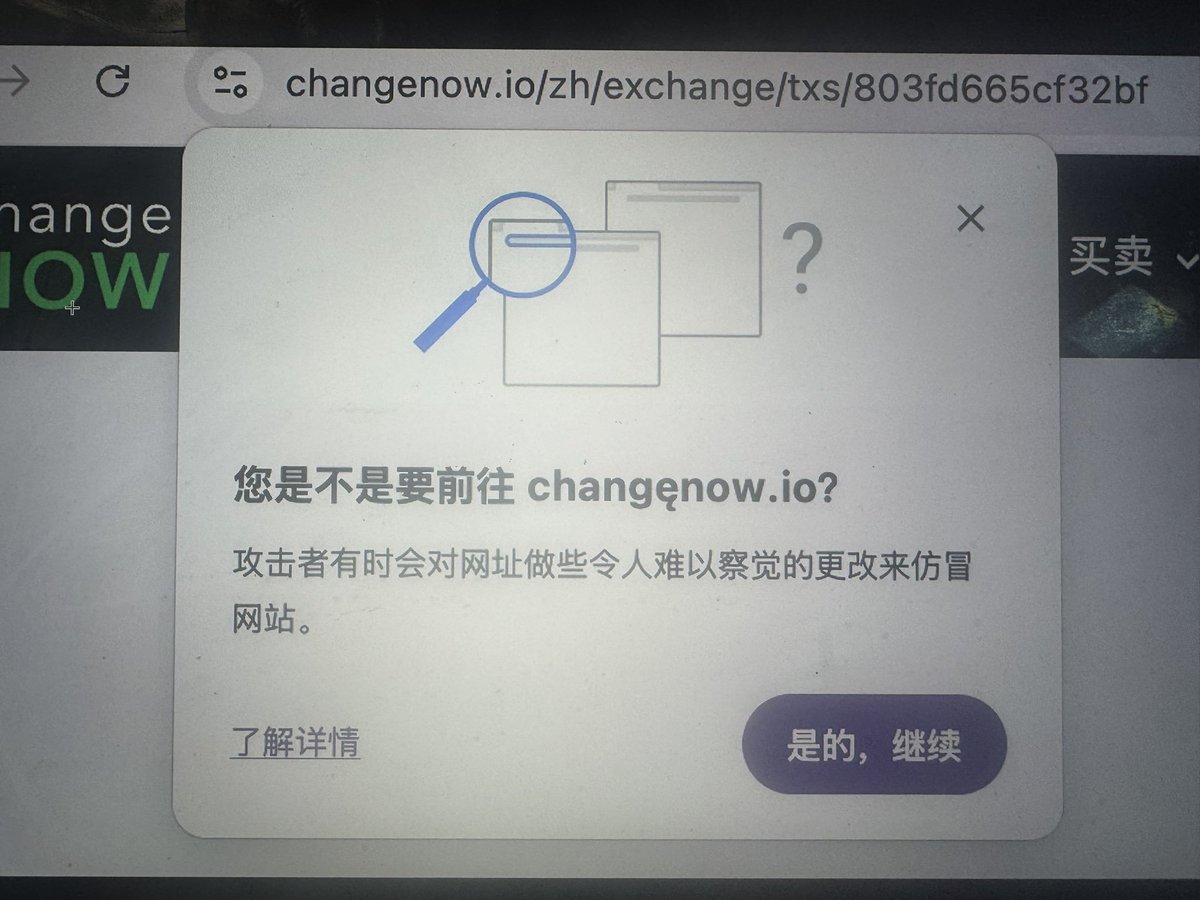
⚠️一位玩家发来的截图,不过他相信 Chrome,点击“是的,继续”,然后进入了假冒 @ChangeNOW_io 的钓鱼网站(注意截图里的字母 e,在黑手册我提过 Punycode 这种钓鱼方式),然后被盗 2 万多刀资产... 这就是 Chrome 的坑了,推荐机制没做好,给用户推荐了钓鱼网站...用户本来是访问真网站的...😭
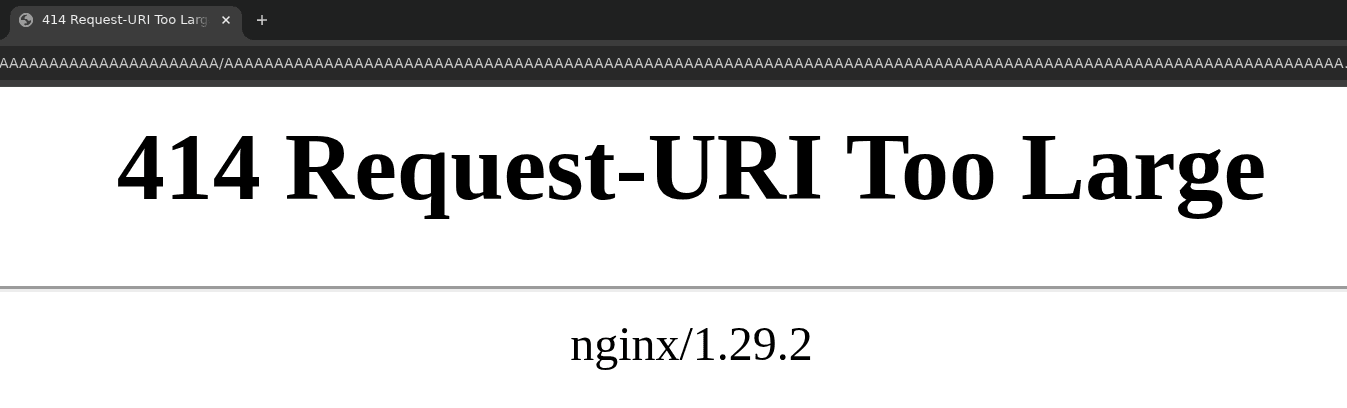
Servers with strict URL and header size limits can be exploited using 414 and 431 status codes to escalate XSS and intercept tokens through redirect chains. Demonstrated attacks target Salesforce and Gunicorn redirect flows by exceeding their limits. #Sa… ift.tt/Hm71eMF
Even a fully correctly spelled domain name is potentially malicious because of unicode domain squatting cloudsecurityalliance.org/blog/2025/07/2…
Actually it is. More specifically, it’s a false-positive TLD-based auto-linking bug, where the sloppy parser mistakes a string that is semantically part of an enumerated list's structure for a URL because of “.Run”. A bug-free system would catch this unintended link.
I built an repo that demonstrates exactly how this attack works, and more importantly how to fix it. github.com/ColeMurray/git…
Watering-hole attack analysis. Attackers compromise a media site, hide malicious JS behind Basic auth, pop a fake "maintenance" page and force-download an LZH archive (bonus: link to legit Lhaplus so victims unpack happily). Excellent breakdown by @jpcert_en Source:…

The attackers convinced users to paste base64-encoded commands in Terminal, which then installed payloads capable of stealing browser credentials, cryptocurrency wallets and system files. Investigators linked more than 85 spoofed domains to the same infrastructure, anchored by…
[SANS Internet Storm Center] Unicode: It is more than funny domain names., (Wed, Nov 12th). When people discuss the security implications of Unicode, International Domain Names (IDNs) are often highlighted as a risk. However, while visible and often... ow.ly/apac106qpL9
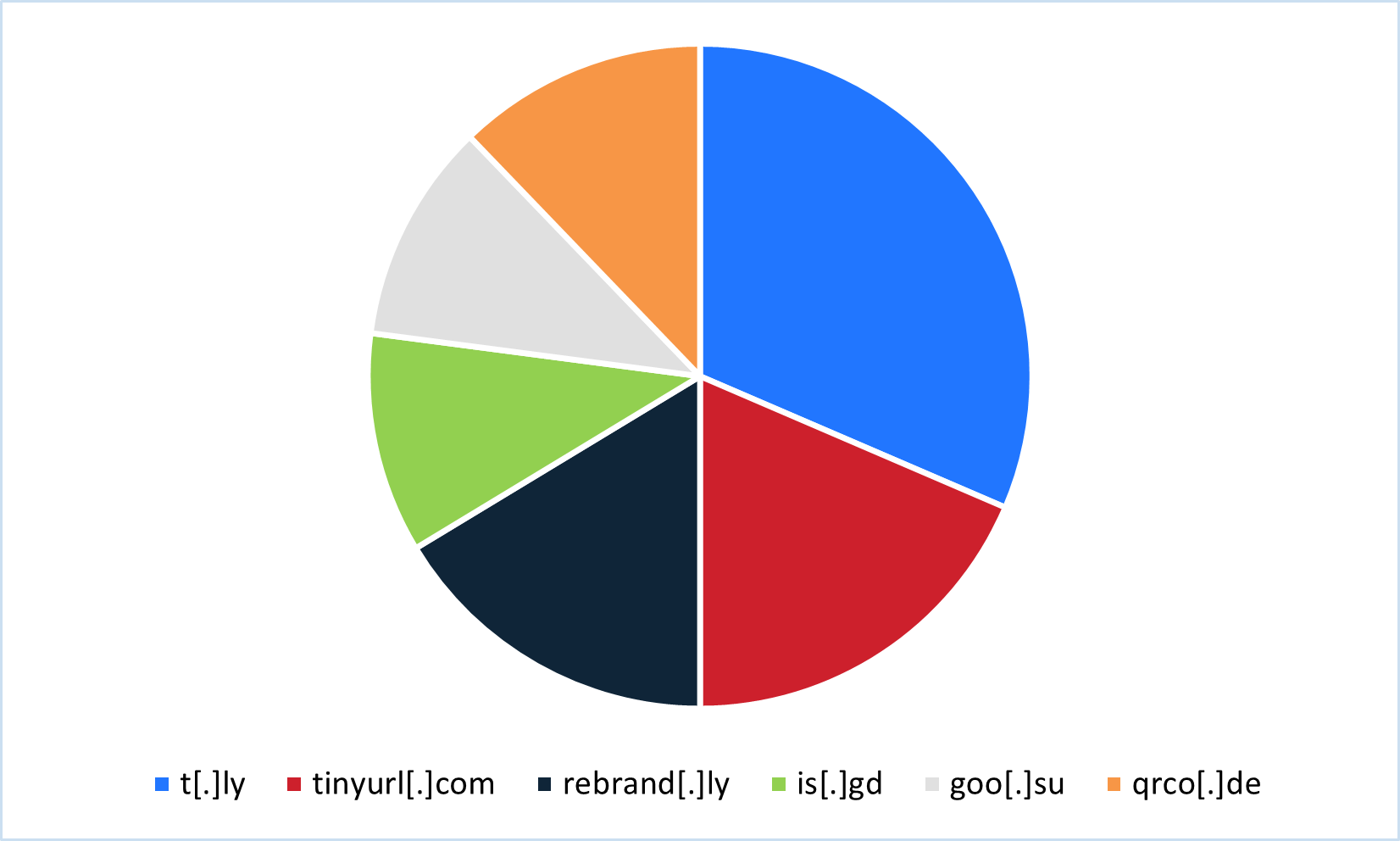
Between July 2024 and June 2025, hackers exploited popular URL shorteners like t.ly, tinyurl.com, and rebrand.ly to spread malware and phishing campaigns using free tiers, APIs, and QR codes. #URLAbuse #Malware… ift.tt/lhdPjZk
Thanks for pointing this out. That URL is actually the default secure @supabase auth domain. It looks strange because @supabase auto generates random project URLs, but I assure you, it is legitimate. That said, your feedback is totally fair. We’re switching to a custom branded…
Attack of the Day: Insecure Deserialization: poisoned objects, bad outcomes. Untrusted serialized data gets processed and triggers arbitrary code or logic abuse. Keep those doors locked, or I’ll be finding more than your house keys
This isn't just phishing; it's a masterclass in social engineering that weaponizes trust. When the URL and CAPTCHA are real, our traditional defenses are blind. A serious escalation. 🤔
Parsing URLs in JS shouldn’t require regex archaeology. The URL Pattern API finally fixes it. I broke it down with real examples! Watch here👇 youtu.be/UYBb72lwyGA

youtube.com
YouTube
URL Pattern API in 100 seconds
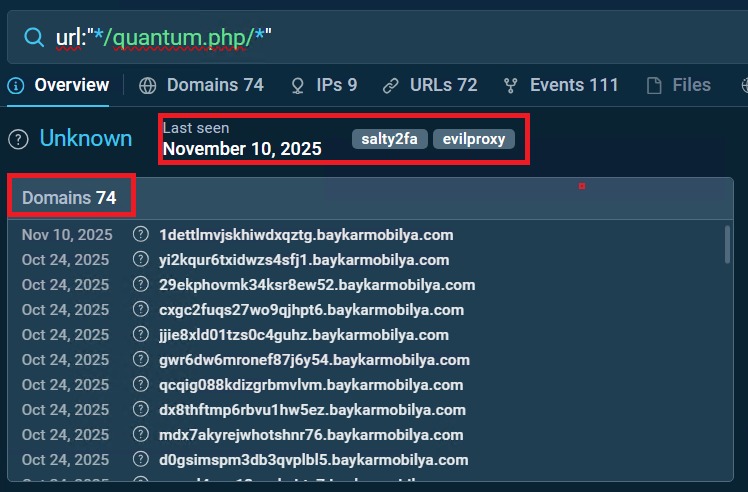
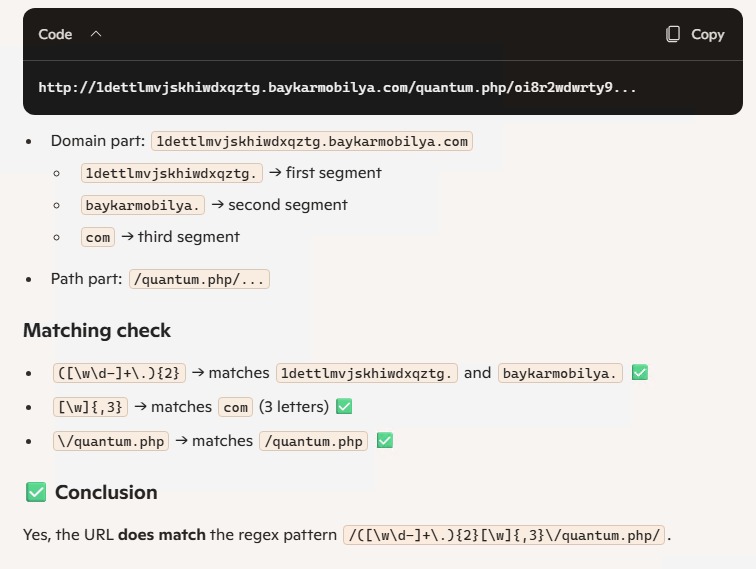
Quantum Route Redirect (QRR) Tool blog.knowbe4.com/quantum-route-… Cybercriminals are increasingly leveraging a technique known as Quantum Route Redirect (QRR) to scale global phishing campaigns. As highlighted in the KnowBe4 blog, attackers embed the following technical pattern into…
Clicking "Login with X" triggers this redirect chain. Notice that last redirect? The victim ends up on the real api_x_com, which looks completely legitimate. But check the URL: /oauth/authorize?oauth_token=4_rpxgAAAAAB5bruAAABmpJekHU That oauth_token, it belongs to the…

🚨 The Hidden Dangers in Your URL: How Parameter Manipulation and JWT Attacks Are Breaching Top Websites undercodetesting.com/the-hidden-dan… Educational Purposes!
URL Normalization Turns a Harmless Request into a Cache-Poisoned XSS Attack Link: bashoverflow.com/url-normalizat… #webcachepoisoning #urlnormalizationattack #urlnormalization #cachepoisoningattack #cachebasedXSS #bugbounty

Something went wrong.
Something went wrong.
United States Trends
- 1. Cowboys 34.8K posts
- 2. Nimmo 10.5K posts
- 3. Colts 39.4K posts
- 4. Giants 85.6K posts
- 5. Chiefs 80.1K posts
- 6. Mets 17K posts
- 7. Semien 7,292 posts
- 8. Gibbs 17.8K posts
- 9. #FlyEaglesFly 10.6K posts
- 10. Turpin 3,120 posts
- 11. Jerry Jeudy 4,395 posts
- 12. Jameis 42.8K posts
- 13. Trevor Lawrence 1,520 posts
- 14. Lions 62.2K posts
- 15. Shedeur 46.6K posts
- 16. Steelers 54.4K posts
- 17. JJ McCarthy 8,878 posts
- 18. Geno 8,244 posts
- 19. Bears 72.2K posts
- 20. Tomlin 8,653 posts