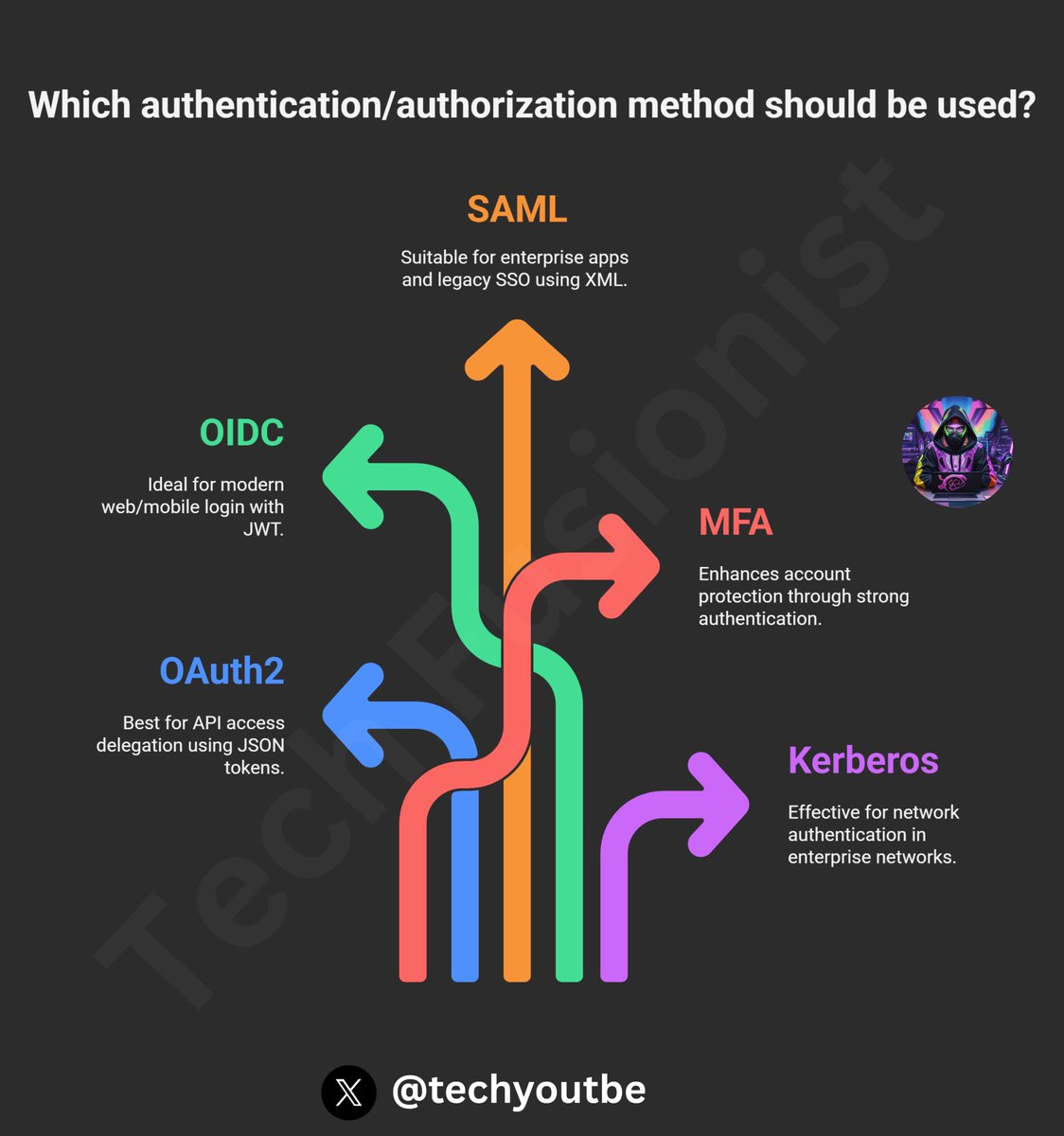
#userauthorizationmethods search results
GOOD MORNING WEB3 ☕️ “Log in with Google” made the internet easy, but it also made users the product. Every click, every signin, every permission flows through centralized servers that learn more about you than you ever intended to share. @idOS_network is building what that…

HTTP is supposed to be stateless, but sometimes... it isn't! Some servers create invisible vulnerabilities by only validating the first request on each TCP/TLS connection. I've just published a Custom Action to help you detect & exploit this - here's a narrated demo:
OAuth Attack Persistence – Hackers Maintain Access After Password Resets cybsec.world/oauth-attack-p…

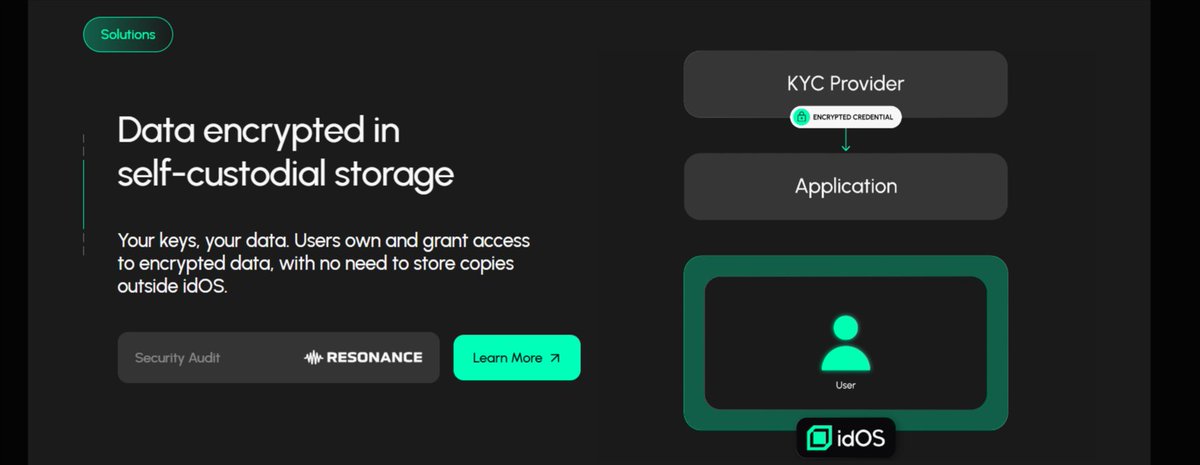
Did you know that with @idOS_network = You can decide who has access to your data = Decide how long such access is granted = Decide to withdraw (revoke) this access at anytime = And grant or decline access request from Dapps Idos did not just make KYC reuseable They are…
We’re excited to share that Auth.js (formerly known as NextAuth.js), is now part of Better Auth. We're excited to keep making auth *better across the web.

Building onchain identity just got easier. The @idOS_network Issuer SDK now supports prebuilt credential templates, making it simple for projects to issue verified claims without reinventing the wheel. Instead of custom building every credential from scratch, issuers can select…
Excited to announce the Auth.js project (formelry NextAuth.js) joins Better Auth

It’s been exactly **one year** since I shared this teaser here that sparked the beginning of Better Auth. This time we’ve got another big announcement coming sep. 26th
Things Every Developer Should Know: JSON Web Token (JWT). JWTs are one of the most widely used methods for API authentication, providing a secure, stateless and scalable way to verify clients. Here’s a simple-to-understand breakdown of how it works (step by step): 𝟭)…

I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
Most decentralized identity systems, like @idOS_network don’t force users into fixed identity categories. Each profile is based on a JSON schemaa flexible, structured format that defines what data types can exist and how they’re organized. Why is this important? Developers can…

Adapt AI security based on user roles. See how to block or allow access without changing your code. youtu.be/Ta-nrefqdb0 #PurviewSDK #purview #datagovernance #microsoft #microsoft365 #microsoftsecurity
The idOS SDKs and Application-Layer Tools The @idOS_network SDK (Software Development Kit) is a modular toolkit for developers that is aimed at helping the integration of identity functions into apps, supporting EVM-compatible (e.g., MetaMask, zerion, etc) and NEAR-compatible…

Most people still think identity is about knowing “who someone is.” That’s outdated. Identity is about knowing who has permission. @idOS_network makes permission portable. Once access becomes reusable, users move across apps, networks, and financial systems without friction.…

Over the weekend I wrote an ADSecurity.org article on "How to Improve Entra ID Security More Quickly" based on my recent @BSides_NoVA talk. This covers important areas including user & guest user configuration, Entra ID roles, admin protections, application permissions,…
In @idOS_network, your identity isn’t a bulky passport it’s a modular toolkit. Each credential age, email, reputation, etc. is structured separately, like Lego bricks. Apps can request only what they need, nothing more. You’re not forced to hand over your full data profile just…

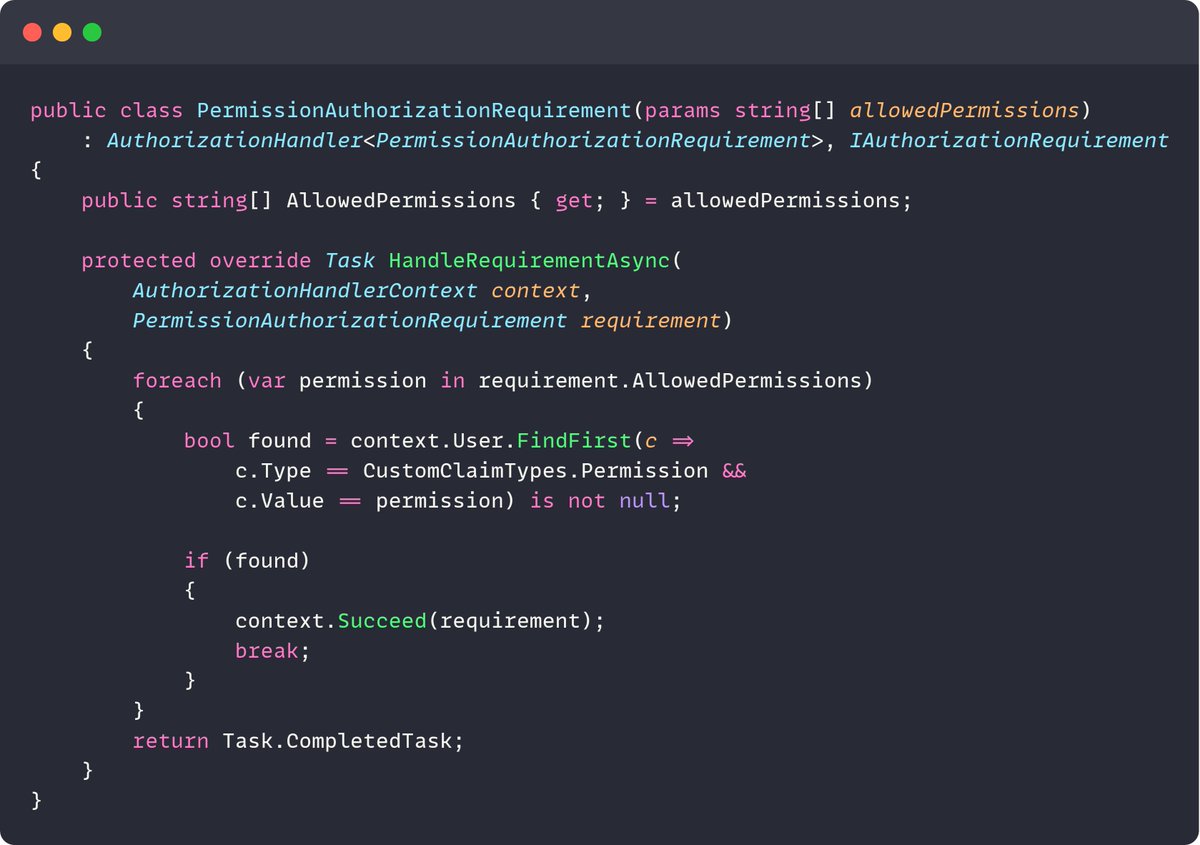
Permission authorization handler in ASP .NET Core 👇 You can use this to enforce Role-Based Access Control.
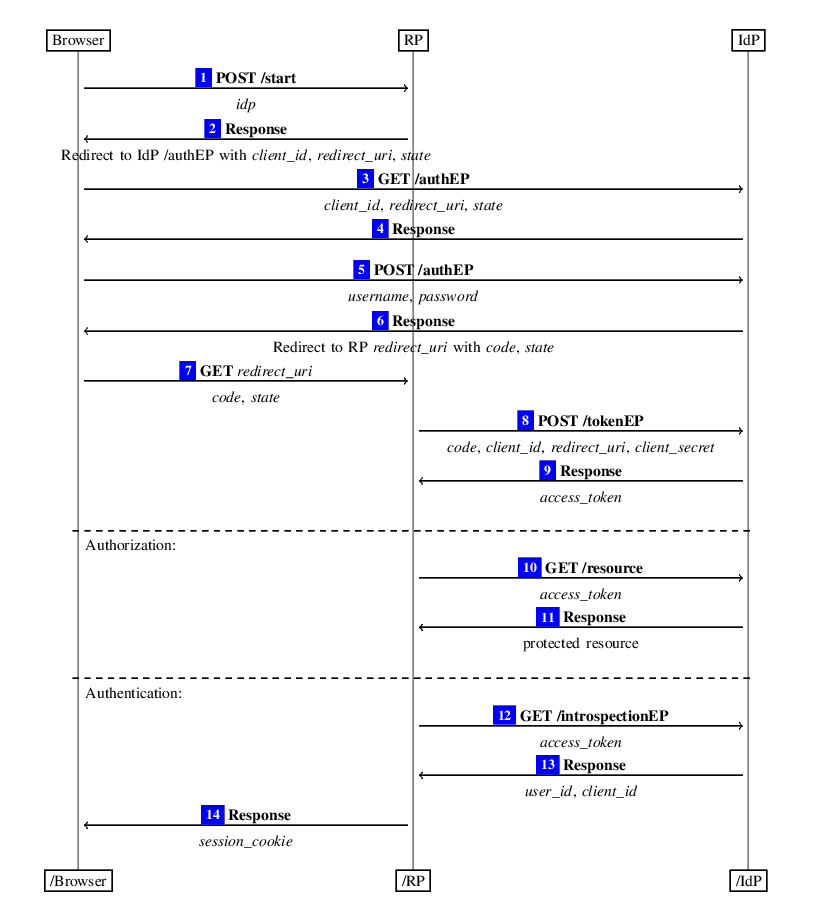
Exploiting OAuth 2.0 — Authorization Code Grants (Everything required to test a novel OAuth 2.0 implementation ) : xploitprotocol.medium.com/exploiting-oau… credits @xploitprotocol Ref* : A Comprehensive Formal Security Analysis of OAuth 2.0∗ : arxiv.org/pdf/1601.01229… (pdf)
"The Three Things to Never Build In Your App: Authentication, Notifications, and Payments" by @trycourier hackernoon.com/the-three-thin… #userauthorizationmethods #notificationsapi
hackernoon.com
How To Save Time Building Authentication, Notifications, and Payments In Your App | HackerNoon
In this post, we use Auth0’s post-user registration hook and Courier’s automations feature to learn how to help a user sign up for your product.
"The Three Things to Never Build In Your App: Authentication, Notifications, and Payments" by @trycourier hackernoon.com/the-three-thin… #userauthorizationmethods #notificationsapi
hackernoon.com
How To Save Time Building Authentication, Notifications, and Payments In Your App | HackerNoon
In this post, we use Auth0’s post-user registration hook and Courier’s automations feature to learn how to help a user sign up for your product.
Something went wrong.
Something went wrong.
United States Trends
- 1. Lakers 89.8K posts
- 2. Luka 69.2K posts
- 3. Ayton 14.8K posts
- 4. Marcus Smart 8,425 posts
- 5. Curry 40.6K posts
- 6. Warriors 95.2K posts
- 7. Sengun 25.3K posts
- 8. #DWTS 48.5K posts
- 9. Shai 33.6K posts
- 10. #DubNation 13.1K posts
- 11. Draymond 8,359 posts
- 12. Rockets 58.9K posts
- 13. Reaves 9,118 posts
- 14. Double OT 6,617 posts
- 15. Jimmy Butler 9,153 posts
- 16. #LakeShow 6,559 posts
- 17. #TusksUp 1,082 posts
- 18. Kuminga 10.2K posts
- 19. LeBron 36.7K posts
- 20. Vando 2,990 posts