You might like
#ESETresearch discovered and analyzed a previously undocumented malicious tool for network devices that we have named #EdgeStepper, enabling China-aligned #PlushDaemon APT to perform adversary-in-the-middle to hijack updates to deliver malware. @0xfmz welivesecurity.com/en/eset-resear… 1/5
🚨🚨CVE-2025-12762 (CVSS 9.1): Critical pgAdmin4 RCE pgAdmin4 server mode + plain backup restore = instant RCE Search by vul.cve Filter👉vul.cve="CVE-2025-12762" ZoomEye Dork👉app="pgAdmin4" 40.3k+ exposed instances ZoomEye Link: zoomeye.ai/searchResult?q… Refer: 1.…

GitHub - uziii2208/CVE-2025-33073: Universal exploitation tool for CVE-2025-33073 targeting Windows Domain Controllers with DNSAdmins privileges and WinRM enabled. github.com/uziii2208/CVE-…
🖨️ Brother, can you spare us a root shell? We were ready for Pwn2Own but they patched it on the LAST DAY of registration 😭 Hope you enjoy this new blog post from us. 📖 starlabs.sg/blog/2025/11-b…
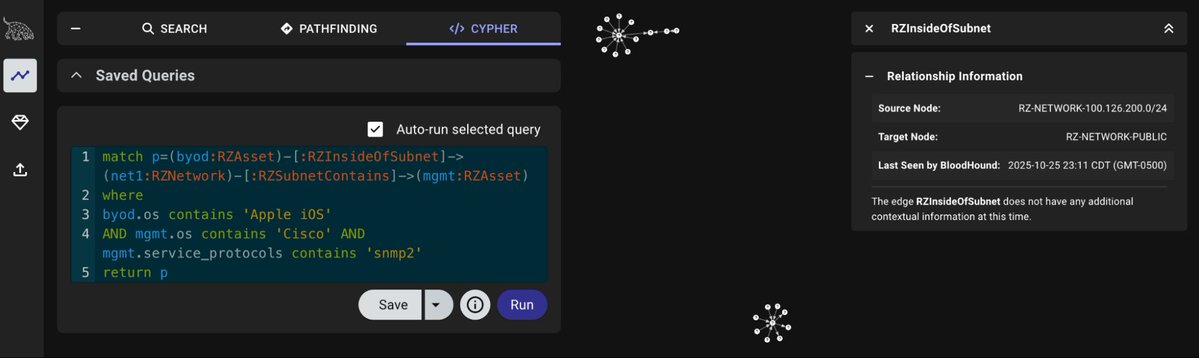
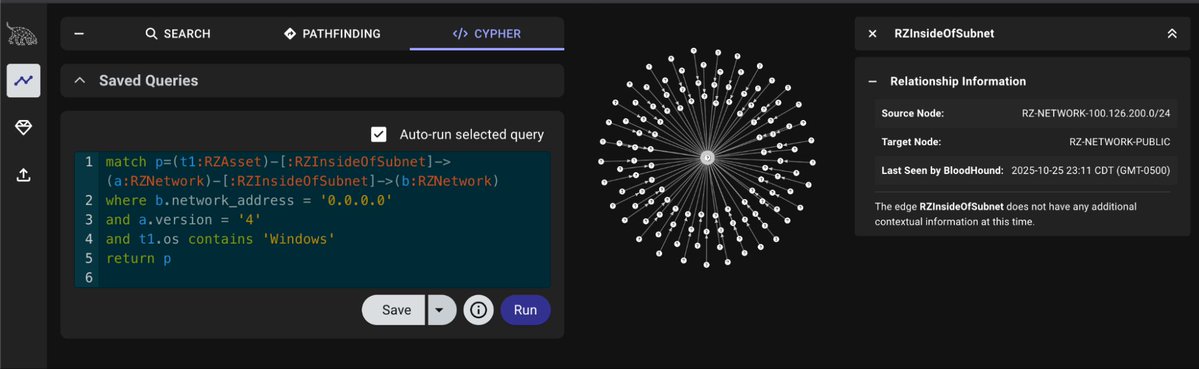
Just like chocolate and peanut butter, runZero and BloodHound are an amazing combination. Today we are introducing runZeroHound - an open source toolkit for bringing runZero Asset Inventory data into BloodHound attack graphs: runzero.com/blog/introduci…


Last month, @d_tranman and I gave a talk @MCTTP_Con called "COM to the Darkside" focusing on COM/DCOM cross-session and fileless lateral movement tradecraft. Check out the slides here: github.com/bohops/COM-to-… Recording should be released soon.
Credential Guard was supposed to end credential dumping. It didn't. @bytewreck just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️ ghst.ly/4qtl2rm
While the exploit craddles from hawktrace for CVE-2025-59287 did not work in our testbed, github.com/jiansiting/CVE… actually did. Be aware, include SCCM when the Software Update Point role is in use, as this requires WSUS.
Today, we publish our analysis of CVE-2025-3600 that we discovered in Telerik UI, a prolific library used in hundreds of thousands of applications. Tagged as a Denial of Service vulnerability, today we go deeper and demonstrate RCE scenarios.. labs.watchtowr.com/more-than-dos-…
FLARE-VM just got a serious upgrade — new GUI, automated builds, and 288+ tools (with better IDA + Go support). The latest update brings: 🧰 Revamped installer ⚙️ New Python script for full VM automation 📚 (cont) bit.ly/48VetqY

🚨 Hackers are hijacking WordPress sites right now. A critical flaw (CVE-2025-5947) in the Service Finder theme lets anyone log in as an admin — no password needed. 13,800+ exploit attempts. Still rising. Most sites haven’t patched. Details here → thehackernews.com/2025/10/critic…
WriteAccountRestrictions fun (@unsigned_sh0rt), RCE in Dell UnityVSA (@SinSinology), Unity Runtime exploit (@ryotkak), Lenovo DCC LPE (@0x4d5aC), and more! blog.badsectorlabs.com/last-week-in-s…
I’ll be teaching how EDR REALLY works this Friday at BSIDES NOVA bsidesnova-2025.sessionize.com/session/998540. It’ll be a medium level course where we analyze malware and its telemetry found in EDR, then try to build hunts around it. Great for attackers and defenders. Hope to see you there!
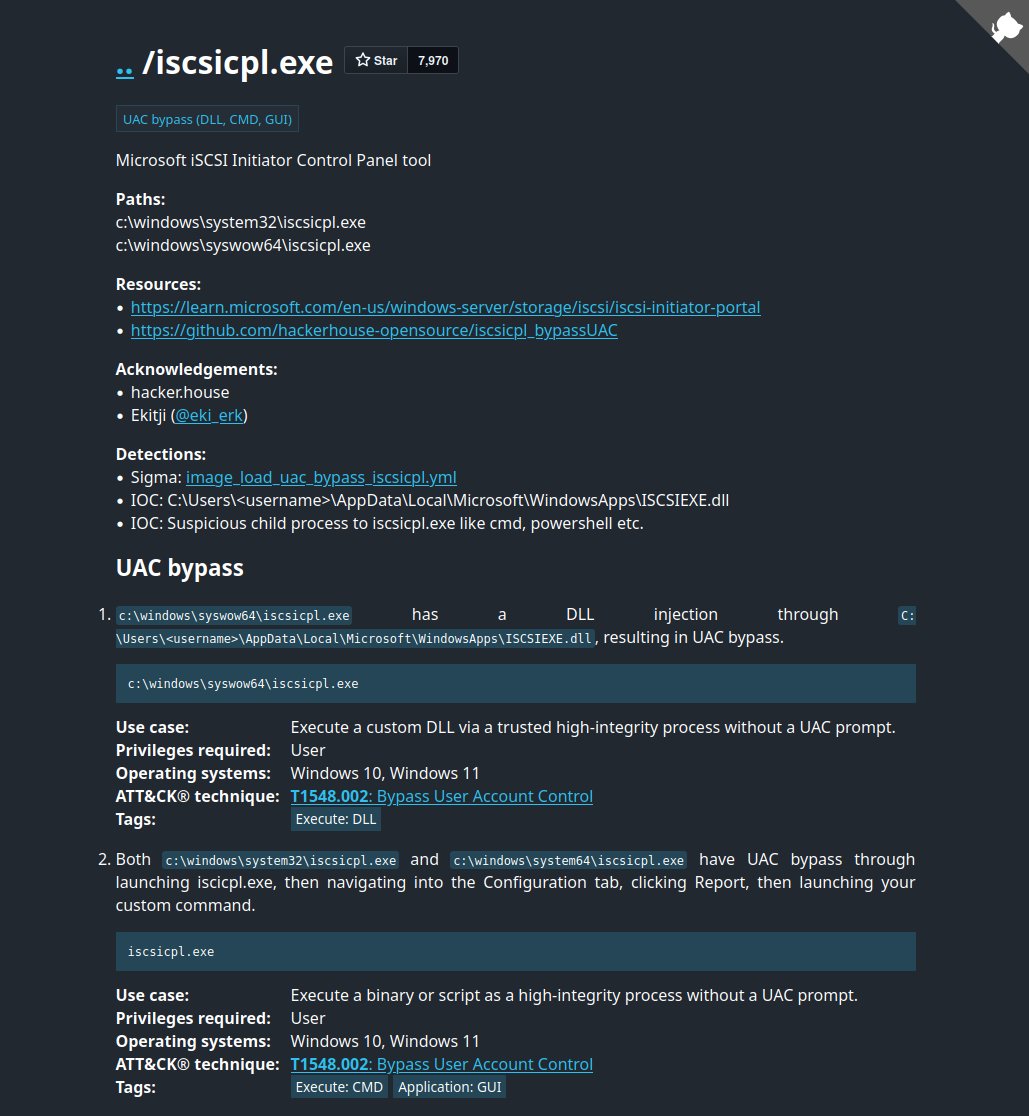
🆕Recent additions to LOLBAS-Project.github.io: • iscsicpl.exe for DLL exec+UAC bypass • eudcedit.exe for UAC bypass • reset.exe/change.exe/query.exe for proxy exec • pixtool.exe/applauncher.exe/mpiexec.exe for dev tool proxy exec ⭐Nearly 8,000 GitHub stars - thank you all!
Lateral movement getting blocked by traditional methods? @werdhaihai just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
How @Mandiant's groundbreaking APT 1 report, which exposed China's PLA hackers, came to be. I spoke with the architect of the 2013 report, @invisig0th, about the backstory behind the report, how they chose what to expose and the gov's surprising response zetter-zeroday.com/how-the-infamo…
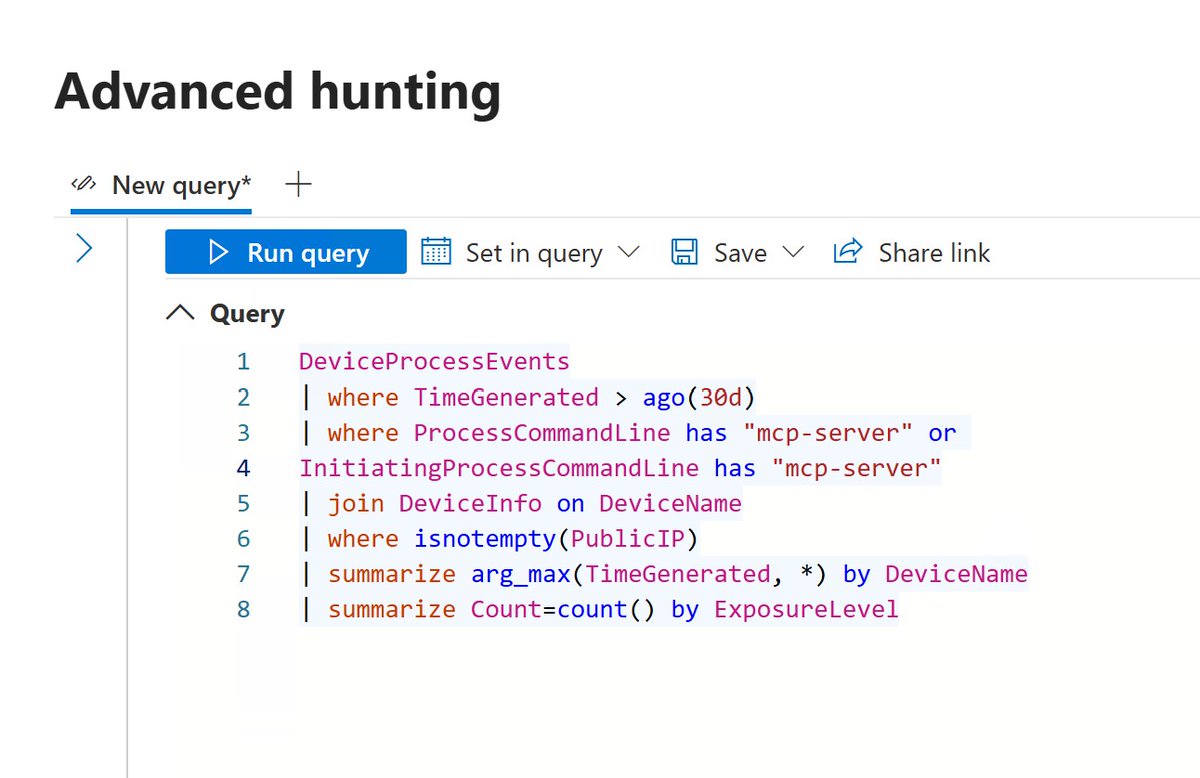
𝗛𝘂𝗻𝘁𝗶𝗻𝗴 𝗘𝘅𝗽𝗼𝘀𝗲𝗱 𝗠𝗖𝗣 𝗦𝗲𝗿𝘃𝗲𝗿 🤖 🚨 Trend Micro found 492 MCP servers exposed online—no auth, no encryption. These act as backdoors to sensitive data like cloud resources, customer info & internal tools. 🔓 90% allow direct read access via natural…
Why should Microsoft's Nested App Authentication (NAA) should be on your security team's radar? @Icemoonhsv breaks down NAA and shows how attackers can pivot between Azure resources using brokered authentication. ghst.ly/45h2Zw3
EDR vendors secure their sales pipelines but neglect monitoring GitHub for exposed installer tokens -leaving customers vulnerable to abuse and over-licensing. Adversaries likely exploit these tokens to build sandboxes for payload testing. Here are search patterns to help…

United States Trends
- 1. Good Monday 33.1K posts
- 2. #MondayMotivation 8,692 posts
- 3. TOP CALL 3,969 posts
- 4. AI Alert 1,664 posts
- 5. Market Focus 2,735 posts
- 6. Check Analyze N/A
- 7. Token Signal 2,180 posts
- 8. Victory Monday 1,625 posts
- 9. #centralwOrldXmasXFreenBecky 643K posts
- 10. SAROCHA REBECCA DISNEY AT CTW 663K posts
- 11. NAMJOON 64.9K posts
- 12. #LingOrmDiorAmbassador 328K posts
- 13. DOGE 191K posts
- 14. #BaddiesUSA 68.2K posts
- 15. Chip Kelly 9,732 posts
- 16. Happy Thanksgiving 10.4K posts
- 17. Monad 125K posts
- 18. Soles 78.7K posts
- 19. Stacey 23.8K posts
- 20. Stefanski 10.1K posts
Something went wrong.
Something went wrong.





































































![AlmasterKsa's profile picture. [ C|EH - Penetration Testing - Developer - Tools - Metasploit - WiFi - web application - Linux ]#تكنولوجيا #اختبار_اختراق #Metasploitable #نصائح_تقنية #PenTesti](https://pbs.twimg.com/profile_images/768868544406839296/mYXrbC_G.jpg)