Byte
@ByteShell101
SOC Analyst . ambitious security person, AI Automation
Potrebbero piacerti
October 15th, 2025, F5 networks submitted SEC 8-K disclosing they had suffered a network compromise. tl;dr some source code stolen, some customer data stolen, potentially impacts usa gov national security F5 reports that they had suffered a compromise through a suspected nation…
Weird stuff going on. This is a CRAZY anime arc. I beg you to read this post. This shit is crazy. Check this shit out June 16th, 2025: @phrack reports suspected offensive state-sponsored activity from China and/or North Korea targeting South Korea. They notify KR-CERT (Defense…

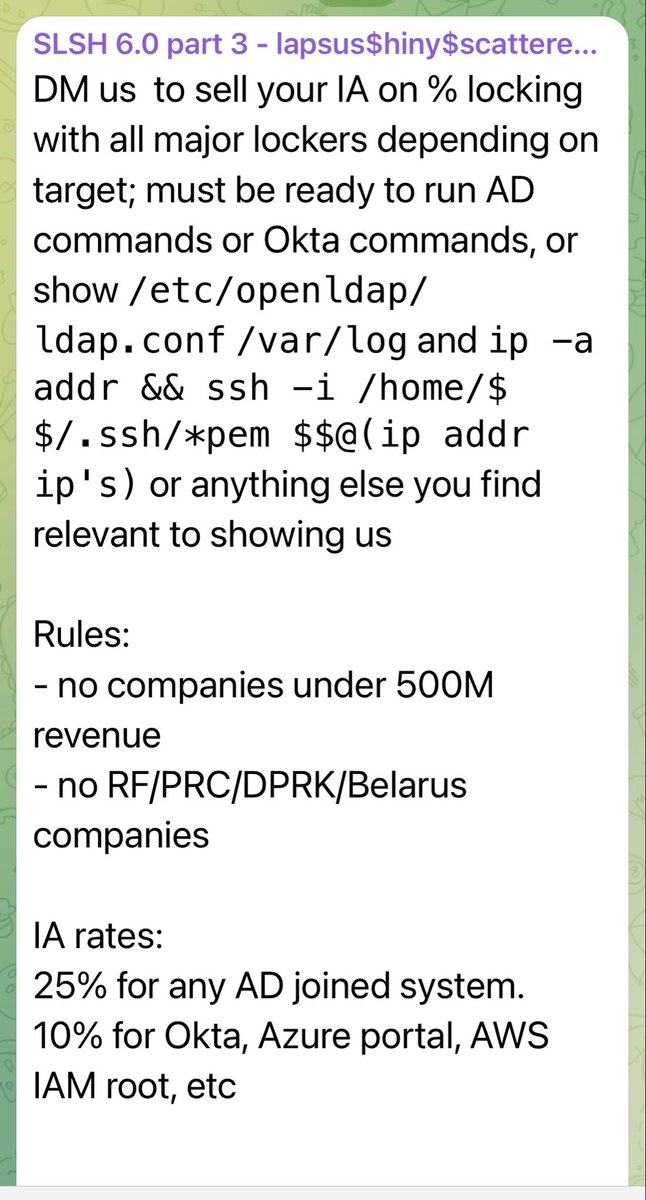
🚨 Scattered Spider’s New Playbook — Insider Recruitment & Access Marketplace The group has moved from chaotic data leaks to an organized cybercrime model. They’re now: 🔸 Recruiting employees and insiders in telecom, SaaS, gaming, and hosting firms (US/UK/AU/CA/FR). 🔸…


🚨 Upcoming Secure by Default Settings Changes for Exchange and Teams APIs Starting late October to November 2025, Microsoft will require admin consent for third-party apps accessing Exchange and Teams content via Microsoft-managed default consent policy. Finally!👏…

Dear Threat Actors, I need Robux. Give me Robux. I know you're all a bunch of fucking degenerates spending your drainer money on that fucking game. Don't be stingy. Found some bullshit Roblox game. There is Robux spent leaderboard. Someone spent over $100,000 in this game. I…
We are releasing details on BRICKSTORM malware activity, a China-based threat hitting US tech to potentially target downstream customers and hunt for data on vulnerabilities in products. This actor is stealthy, and we've provided a tool to hunt for them. cloud.google.com/blog/topics/th…
The XOXO From Prague guy is back and he's compromising Lockbit ransomware group (again)
LockBit is down again —XOXO from Prague LockBit's 5.0 panel just got wrecked lockbitfbinpwhbyomxkiqtwhwiyetrbkb4hnqmshaonqxmsrqwg7yad[.onion] #LockBit #Ransomware
![xoxofromprague's tweet image. LockBit is down again —XOXO from Prague
LockBit's 5.0 panel just got wrecked
lockbitfbinpwhbyomxkiqtwhwiyetrbkb4hnqmshaonqxmsrqwg7yad[.onion]
#LockBit #Ransomware](https://pbs.twimg.com/media/G0kGgTyXMAEgIgK.jpg)
![xoxofromprague's tweet image. LockBit is down again —XOXO from Prague
LockBit's 5.0 panel just got wrecked
lockbitfbinpwhbyomxkiqtwhwiyetrbkb4hnqmshaonqxmsrqwg7yad[.onion]
#LockBit #Ransomware](https://pbs.twimg.com/media/G0kGgTlWwAEy4G_.jpg)
![xoxofromprague's tweet image. LockBit is down again —XOXO from Prague
LockBit's 5.0 panel just got wrecked
lockbitfbinpwhbyomxkiqtwhwiyetrbkb4hnqmshaonqxmsrqwg7yad[.onion]
#LockBit #Ransomware](https://pbs.twimg.com/media/G0kGgTvWQAENz01.jpg)
![xoxofromprague's tweet image. LockBit is down again —XOXO from Prague
LockBit's 5.0 panel just got wrecked
lockbitfbinpwhbyomxkiqtwhwiyetrbkb4hnqmshaonqxmsrqwg7yad[.onion]
#LockBit #Ransomware](https://pbs.twimg.com/media/G0kGgTqXQAAGLAu.jpg)
Friendly reminder, having a CISSP doesn't make you a good job candidate for exactly the same reason as having a drivers license doesn't make you a good driver
If you’re just stepping into cybersecurity, there are two brutal truths you must tattoo into your brain 1) No system is ever 100% secure. Once you accept this fact, you will be free. The name of the game is prioritization. If you're not sure, prioritize some more. 2) Jeffrey…
Update: Microsoft has released security updates that fully protect customers using all supported versions of SharePoint affected by CVE-2025-53770 and CVE-2025-53771.
Microsoft has released security updates that fully protect customers using all supported versions of SharePoint affected by CVE-2025-53770 and CVE-2025-53771. These vulnerabilities apply to on-premises SharePoint Servers only. Customers should apply these updates immediately to…
Microsoft has continuously observed hybrid attacks leading to espionage, business interruption, and ransomware deployment that involve threat actors moving from on-premises environments to the cloud. Many organizations manage their resources across different realms, including…

Microsoft and CrowdStrike are teaming up to create alignment across our threat actor taxonomies, mapping where knowledge of these actors align to enable security professionals to connect insights faster and make decisions with greater confidence. msft.it/6011SlOZ9
Microsoft has discovered worldwide cloud abuse activity by new Russia-affiliated threat actor Void Blizzard (LAUNDRY BEAR), whose cyberespionage activity targets gov't, defense, transportation, media, NGO, and healthcare in Europe and North America. msft.it/6011S9JpN
Over the past year, Microsoft Threat Intelligence observed the persistent growth and operational sophistication of Lumma Stealer, an infostealer malware used by multiple financially motivated threat actors to target various industries. msft.it/6010Sd2zi
🚨 Fake CAPTCHA Evolution: Homoglyphs & Unicode ⚠️ The user sees a #CAPTCHA that prompts to press a few buttons instead of just clicking a checkbox. Pressing the keys triggers code execution, leading to system compromise. 👨💻 Using #ANYRUN Sandbox, security teams can dive into…


Microsoft Threat Intelligence observed a new and notable method used by the threat actor Storm-0249 for distributing the Latrodectus trojan, a malware loader designed to facilitate multi-stage attacks by downloading and installing additional payloads onto compromised devices.

United States Tendenze
- 1. #2025MAMAVOTE 50.7K posts
- 2. Deport Harry Sisson 10.4K posts
- 3. Brevis ZK 133K posts
- 4. Mila 17.5K posts
- 5. DuPont 1,953 posts
- 6. #PokemonZA 2,256 posts
- 7. Deloitte 7,899 posts
- 8. #EliraGotCake2025 9,348 posts
- 9. Ninja Gaiden 7,600 posts
- 10. #PokemonLegendZA 1,899 posts
- 11. #ENHYPEN 113K posts
- 12. Gabe Vincent 4,292 posts
- 13. BNB Chain 21.1K posts
- 14. Angel Reese 54.9K posts
- 15. Lakers 18.3K posts
- 16. Domain For Sale 19.2K posts
- 17. Mad Max 4,106 posts
- 18. tzuyu 261K posts
- 19. Mavs 5,648 posts
- 20. Everest 3,480 posts
Potrebbero piacerti
-
 mpgn
mpgn
@mpgn_x64 -
 Martin Bose
Martin Bose
@MartinBose8 -
 rice
rice
@00iTheo -
 Steve Campbell
Steve Campbell
@lpha3ch0 -
 Synacktiv
Synacktiv
@Synacktiv -
 Csaba Fitzl
Csaba Fitzl
@theevilbit -
 Clément Notin
Clément Notin
@cnotin -
 Poofy Puffs
Poofy Puffs
@Poofy_Puffs -
 Avi.eth
Avi.eth
@AviAisenberg -
 Cryptacles
Cryptacles
@cryptacles -
 MajesticSloths
MajesticSloths
@sloths_win -
 KevTheHermit
KevTheHermit
@KevTheHermit -
 Marcopolo
Marcopolo
@blizzard_crypto -
 Mark C.
Mark C.
@LargeCardinal -
 Oscaaaa
Oscaaaa
@Oscar_Kwok
Something went wrong.
Something went wrong.