
C2Workbench
@C2Workbench
Open access intelligence database for open-source C2 frameworks. Search, compare & track tools with source code analysis. For red & blue teams.
XiebroC2 runs fully in-memory—config in globals, runtime data in RAM, ObfuscateStrings rewrites blacklisted strings in byte-slices to evade memory scanning. Plus plugins for custom post-ex modules. Zero disk + in-memory obfuscation Full analysis: c2workbench.com/framework/xieb…
Although c2workbench.com only shows 98 frameworks at the moment, we have 239 catalogued in the back-end - which will eventually be made available in the front end. If I was to add an analytics page - what trends/analytics would you be interested in seeing?
AlanFramework ships agents as PE/DLL/PowerShell/shellcode - pick your delivery method. Fully in-memory execution + reflective DLL injection into remote processes + SOCKS5 pivoting. Multi-format flexibility meets operational versatility. Full analysis: c2workbench.com/framework/alan…
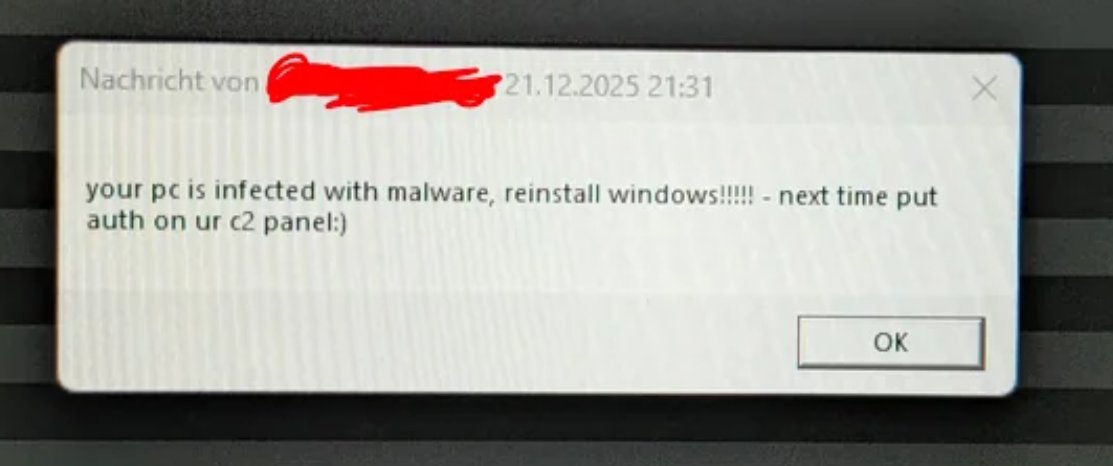
Multiple users are reporting messages like this one. Seems someone has hacked a malware C2 reddit.com/r/antivirus/co…
BlackMamba packs a full evasion suite: API unhooking, ETW patching, AMSI bypass, VM detection via registry/files, XOR string obfuscation, Working hours + kill-switch monitoring. All the EDR bypass primitives you need in one framework. Full Analysis: c2workbench.com/framework/blac…
DeimosC2's DoH agent hides C2 traffic inside DNS queries sent as HTTPS to Google/Cloudflare resolvers. Data chunked to DNS size limits & reassembled server-side. Clever use of legit infrastructure. DoH + encryption + Legit Infa = Stealthy Full analysis: c2workbench.com/framework/deim…
If you're a red teamer, C2 Workbench helps you understand your OPSEC gaps before deployment. Check what blue teams can actually see: default profiles, file system artifacts, network IOCs; what's configurable and what's hard-coded. c2workbench.com
If you’re into C2 (for redteam) and you’re not using C2 Workbench yet, you’re missing out. They catalogue top C2 frameworks like Havoc, Merlin… and even my humble phpsploit made the list 🙃 Check it out: c2workbench.com/framework/phps…
To be clear, it's a work-in-progress, not a polished product. I've tried my best to fine tune various LLM's that do the source code analysis and included references to the code base but automated analysis isn't perfect. If you find issues, please tell me.
Before I go further: huge respect to @JorgeOrchilles and the @c2_matrix team. They pioneered C2 cataloguing and their matrix is the go-to. C2 Workbench takes a different angle with source code analysis. Complementary, not competitive. Both for the community
I've been building C2 Workbench - a free platform analyzing C2 frameworks with installation guides, capability mappings, protocol analysis, and detection artifacts. It's not perfect and the data has gaps, but I think it's useful. c2workbench.com
United States Trends
- 1. #heatedrivalry 72.1K posts
- 2. #StrangerThings5 325K posts
- 3. Anthony Edwards 4,754 posts
- 4. ilya 66.8K posts
- 5. jancy 42.2K posts
- 6. Holly 78.7K posts
- 7. Broncos 43.4K posts
- 8. Dustin 137K posts
- 9. Lakers 40K posts
- 10. tammy 29.8K posts
- 11. Ant Man 1,585 posts
- 12. Jokic 7,806 posts
- 13. Murray 19.5K posts
- 14. yuna 28.2K posts
- 15. Anta Claus N/A
- 16. Chris Jones 2,413 posts
- 17. robin 63.8K posts
- 18. jacob tierney 3,053 posts
- 19. Lucas 88.8K posts
- 20. Kali 73.9K posts
Something went wrong.
Something went wrong.



























































