FortiWeb users, be alert! A serious OS Command Injection flaw (CVE-2025-58034) is being actively exploited. Ensure you're upgraded to the patched versions to stay secure. Have you checked for vulnerabilities lately? #FortiWeb_vulnerability

PlushDaemon's latest tactics reveal a silent threat in global cyber espionage. Their undocumented implant shifts DNS traffic, enabling malicious software updates. The reach? Worldwide. How prepared is your organization for these evolving cyber risks? #ciberseguridad

A new threat campaign linked to China has compromised thousands of ASUS routers worldwide, aiming to create a stealth espionage network. With vulnerabilities exploited for persistent access, how are we safeguarding our devices? #CyberSecurity #Ciberseguridad

Ransomware attacks soared in Q3 2025, with three groups causing 65% of breaches. Vouchers of valid VPN credentials remain the main entry point. Are we prioritizing stronger multi-factor authentication enough? #CyberSecurity #CiberSeguridad

Beware of the hidden danger on LinkedIn! MI5 warns of espionage tactics from Chinese operatives posing as headhunters, targeting UK officials. How can we better shield our networks from threats like this? Let's discuss! #LinkedIn_Security

Crypto isn't as anonymous as many think. European authorities just uncovered €47 million in illicit payments from IPTV pirates. Targeting the wallets of digital pirates disrupts their revenue. What do you think about these efforts? #crypto_anonymity
Get ready for SECON & eGISEC 2026! Join us from March 18-20 at KINTEX, Korea, for a showcase of cutting-edge security innovations. With over 400 exhibitors, what advances in security technology are you most excited about? #SECON_eGISEC_2026
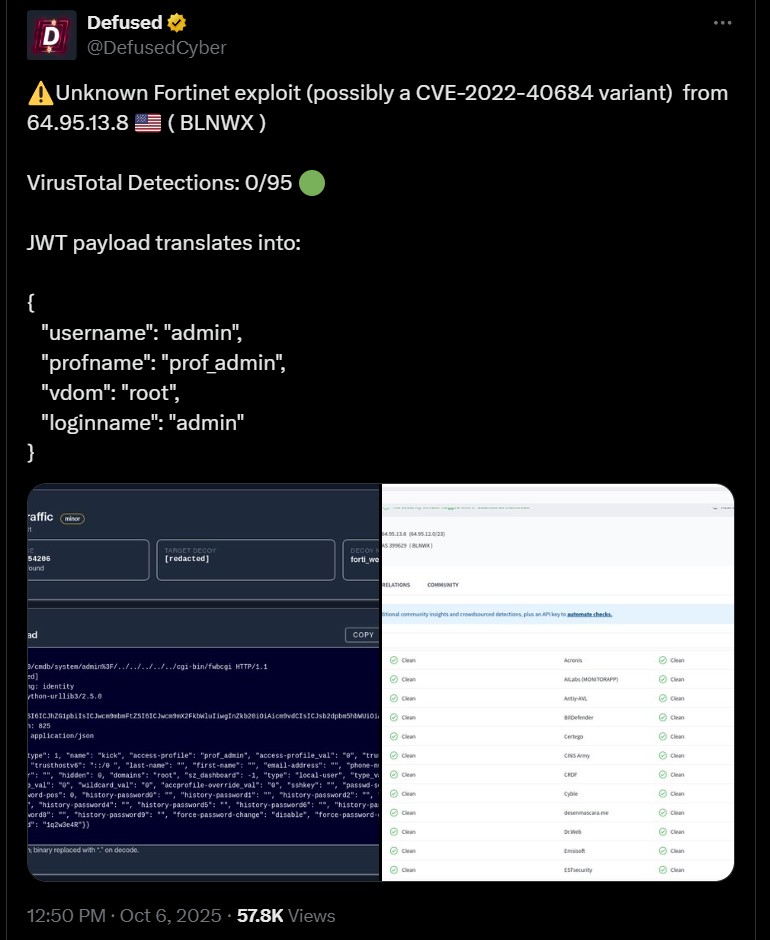
Fortinet's recent silent patch of a critical zero-day vulnerability is raising alarms. Cybersecurity professionals warn that hiding vulnerabilities invites attacks. How can we ensure transparent communication in security? #transparent_security_communication
Despite penalties and court oversight, major crypto exchanges continued to facilitate hundreds of millions in illicit transactions. A recent investigation sheds light on this concerning reality. Can we really trust these platforms to clean up their act? #crypto_transparency
Grok 4.1 is reshaping the chatbot landscape, boasting a dramatic reduction in hallucinations and enhanced emotional intelligence. However, concerns linger around its content filtering. Are stricter safety measures needed, or is the performance spot on? #Grok41_CHATBOT
A critical vulnerability in Fortinet's FortiWeb could allow attackers remote code execution. Users must update immediately to avoid exploitation—patch your systems and share your thoughts on security practices! #CyberSecurity #SeguridadCibernética

AI-powered developer tools like Cursor may have unaddressed vulnerabilities, exposing users to credential theft and other risks. Relying on these technologies requires vigilance and code review. How do you ensure security in your development environment? #seguridad_en_desarrollo

The US is fighting back against North Korea’s fake IT scam as five individuals plead guilty for their roles in the scheme. This highlights that the threat isn’t just overseas—it's here too. How can companies better protect themselves? #ciberseguridad

Caught in a web of deceit, five men facilitated North Korean IT workers' infiltration of U.S. companies. This led to over $2M for the DPRK while compromising 136 firms. What can we do to protect against such cyber threats? #ciberseguridad

Logitech recently faced a serious cybersecurity breach but assures it hasn’t disrupted operations or sensitive data. They’re working with experts and expect insurance will cover related costs. Have you ever dealt with a cyber incident? #ciberseguridad
The Washington Post has disclosed a data breach revealing sensitive details of nearly 10,000 individuals due to a Cl0p ransomware attack. Such incidents highlight the growing vulnerabilities in digital systems. How can organizations bolster their cyber defenses? #cyber_defense
Cybersecurity in 2026 will shift focus: attackers will exploit human vulnerabilities over software flaws. With AI amplifying risks and geopolitical tensions rising, how prepared are we? Let's discuss! #ciberseguridad2026

AI should elevate our productivity, but many are falling into the "workslop" trap. Relying on it for shortcuts often backfires, causing more time waste and strained relationships. How can we shift our approach to maximize its true potential? #maximizing_productivity
WiFi 7 is here to revolutionize connectivity with its Multi-link Operation, combining 2.4, 5, and 6 GHz for unprecedented speeds! But with great power comes great responsibility. Are you ready to tackle the complexity of securing your home network? #WiFi7
The rise of AI browsers like ChatGPT Atlas and Perplexity Comet is revolutionizing how we interact with the web, transforming it into a more intuitive experience. Are you ready to embrace this shift? 🌐✨ #nueva_era_de_IA
United States 트렌드
- 1. #AcousticPianoSnowGlobe 1,618 posts
- 2. Cheney 24.3K posts
- 3. Nano Banana Pro 10.2K posts
- 4. #TSTheErasTour 1,387 posts
- 5. #NXXT_NEWS N/A
- 6. FINAL DRAFT FINAL LOVE 226K posts
- 7. #LoveDesignFinalEP 208K posts
- 8. YOYOK N/A
- 9. Nnamdi Kanu 142K posts
- 10. #thursdayvibes 3,670 posts
- 11. Haymitch 13.3K posts
- 12. Husqvarna N/A
- 13. SEDITIOUS BEHAVIOR 5,104 posts
- 14. Good Thursday 39.1K posts
- 15. sohee 39.1K posts
- 16. Reaping 81.3K posts
- 17. Trump and Vance 24.3K posts
- 18. Pablo 68.8K posts
- 19. Unemployment 30.3K posts
- 20. The Hunger Games 92.1K posts
Something went wrong.
Something went wrong.






























