EncapsulateJay
@EncapsulateJ
SOC Analyst @HuntressLabs
Bạn có thể thích
Cheers to @TheDFIRReport team for all the guidance and mentorship. This was a really interesting case to work!
🌟New report out today!🌟 Blurring the Lines: Intrusion Shows Connection With Three Major Ransomware Gangs Analysis and reporting completed by @r3nzsec, @EncapsulateJ, @rkonicekr, & Adam Rowe Audio: Available on Spotify, Apple, YouTube and more! Report:⬇️

ClickFix just got clever-ditched Win+R for Win+X (Power User Menu) ⚠️ New variant drops Lumma after Defender exclusion: - Prompts for elevation till user accept - Add defender exclusion on %temp% - Drops & runs Lumma Multiple Sigma rules fired 💥 Process Tree👇




There's pretty much never been a better time to start learning or get hands on blue team experience through labs. The availability and quality of labs being released today compared to 4 years ago is night and day. Training providers like Xintra are paving the way for the future!
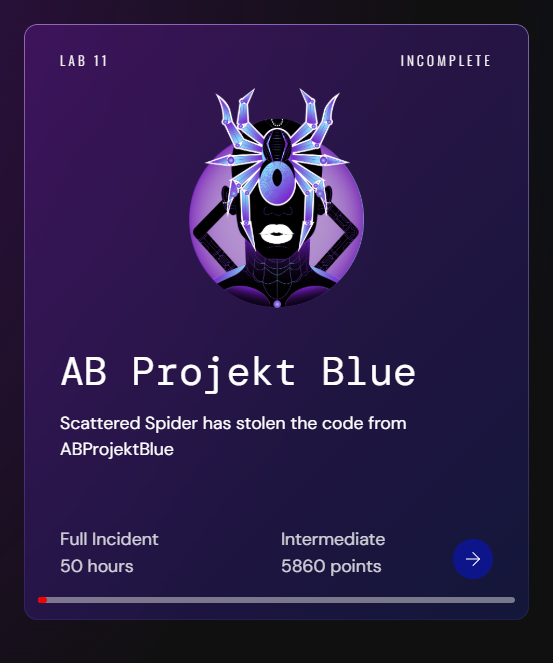
NEW LAB: Scattered Spider (UNC3944) 🕷️🕸️ Scattered Spider hits indie studio AB Projekt Blue, deploying ransomware and stealing unreleased game code. Test your skills on: 👀 Social Engineering & MFA Fatigue 👀 Credential Theft via OST Files 👀 Bring Your Own Vulnerable Driver…

If you’re running an SSLVPN (SonicWall, Fortigate, etc.) and not retaining those logs, you’re setting yourself up for disaster. It's not uncommon to see sub-10 minute slices of activity in the totality of exported logs; which is next to useless.
🚨 Case from @HuntressLabs 🔎 Cephalus seen side loading DLL 'SentinelAgentCore.dll' into legitimate 'SentinelBrowserNativeHost.exe' for ransomware execution ✏️ File extension for encrypted files - '.sss'


🚨 Search for software, end up getting ransomware! SEO-driven #Bumblebee malware campaigns observed throughout July led to domain compromise, data theft & #Akira ransomware. Tools included #AdaptixC2 & #Netscan. thedfirreport.com/2025/08/05/fro…
Anton bringing the heat as always!
Got a new @HuntressLabs blog out today taking a look at some intrusion analysis methodology with practical examples - check it out! huntress.com/blog/intrusion…
Proud to work alongside these two 🔥 Congrats to you both!
Congratulations to @RussianPanda9xx & @polygonben for having talks accepted at #defcon33! Follow these folks and if you're headed to @defcon put it on you to-do list to be in attendance!

HijackLibs.net details hundreds of publicly disclosed DLL Hijacking opportunities. With over 700 stars on GitHub and a growing list, @Wietze does an amazing job maintaining it. Despite this contributing can be time consuming. That's why I've created HijackLibs Helper!👇


Sample deployed via low detection Octowave Loader caught: virustotal.com/gui/file/141a6… - econusi[.digital/nwmb Interestingly low detection C2 amongst the noise is the newly registered domain posing as @warhammer - wawrhamer[.live



🚨 We are observing #Lumma samples that retrieve their C2 from Telegram channels, using the channel name to conceal it. The C2 domain is further obfuscated with a ROT15 or ROT13 cipher. Lumma samples: 062c56f740bb6c2f7297169b873899da35d02470a52d3e88f3181c594aec4d3d…


huntress.com/blog/cve-2025-… Check out what @HuntressLabs has been busy with this weekend! If you're an IR/SOC analyst responding to this, we've included a query using @WithSecure's Chainsaw to help ease the lift. #cve202530406 #CentreStack
Quality breakdown here from @xorJosh @Antonlovesdnb @Purp1eW0lf
🚨 [ New blog ] out today with my 🐐 colleagues @xorJosh and @Purp1eW0lf - this case started with a simple brute force and ended with some really interesting findings - check it out! huntress.com/blog/brute-for…
We wrote up what @HuntressLabs has been seeing for the CrushFTP authentication bypass: CVE-2025-31161 (or CVE-2025-2825, whichever side of the bed you woke up on) leading to MeshCentral agents, AnyDesk, and neato "TelegramBot" malware. Patch plz! ✌️ huntress.com/blog/crushftp-…

Got a new @HuntressLabs blog out today looking at a case that @Purp1eW0lf @xorJosh and I worked on recently - VPN compromise, lateral movement, Veeam exploitation & some methodology notes throughout that newer folks might find particularly interesting! huntress.com/blog/untold-ta…
United States Xu hướng
- 1. Good Saturday 29.5K posts
- 2. GAME DAY 11.8K posts
- 3. Massie 78.3K posts
- 4. #SaturdayVibes 4,330 posts
- 5. #Caturday 3,752 posts
- 6. #Varanasi 61.5K posts
- 7. #MeAndTheeSeriesEP1 848K posts
- 8. Senior Day 2,293 posts
- 9. Draymond 27.1K posts
- 10. #GlobeTrotter 423K posts
- 11. PONDPHUWIN AT MAT PREMIERE 583K posts
- 12. Marjorie 92.2K posts
- 13. Brooklynn 1,345 posts
- 14. St. Albert N/A
- 15. Willie Green 1,473 posts
- 16. Diosa 7,597 posts
- 17. Wemby 50.7K posts
- 18. For God 191K posts
- 19. America Only 34.4K posts
- 20. Bubba 68.5K posts
Something went wrong.
Something went wrong.