
Ayush Anand
@Securityinbits
I tweet about my learning in Malware analysis, Threat Intel, Detection engineer and DFIR journey. Opinions are mine only!
You might like
Ever run into randomly obfuscated PowerShell? 😵💫 I did - thanks to a recent tool (revshell) that generate random versions of obfuscated PowerShell But here’s the fix 👇 MinusOne — written in Rust by @AirbusCERT - cleans it up in seconds.


Ever lost track of short-lived malware processes? Use ProcMon Process Tree to catch even exited Processes + cmdline. 1. Start capture 2. Run sample 3. Hit Ctrl+T -> full tree, even the gone ones 🚀 Bonus: Right-click root -> "Add Process & Children to Include" to cut noise.


Turns out even built‑in cmds like nltest, net & whoami are still handy tools in real attacks. Seen them in ransomware plays & real‑world incidents. Shared tested Sigma rules + SIEM detections (KQL & Elastic) + example output to catch them🔍 👇Blog link in the reply.


New Sigma release r2025-10-01 is available for download. 🌟43 New Rules 🛡️34 Rule updates 🔬27 Rule Fixes Explore the full release -> github.com/SigmaHQ/sigma/… This release introduces a bunch of new rules and updates - A bunch of CVE detections including CVE-2025-54309,…

My recent writeup on updates in #Rhadamanthys stealer, along with some scripts that may be helpful in analysis. Check it out!
🚨 Rhadamanthys v0.9.2 is here! What’s new in this multi-layered stealer’s latest evolution? We break down the updates, tactics, and what defenders need to know. Dive into our blog for the full analysis. research.checkpoint.com/2025/rhadamant…
Just got my Sigma → Markdown (KQL & Elastic) converter working vibe-coded using Codex CLI - Converts into Markdown (KQL & Lucene) using sigma backends. - Saves them into your Obsidian - easy to search & link. If anyone’s interested, drop me a comment or DM. I might publish…


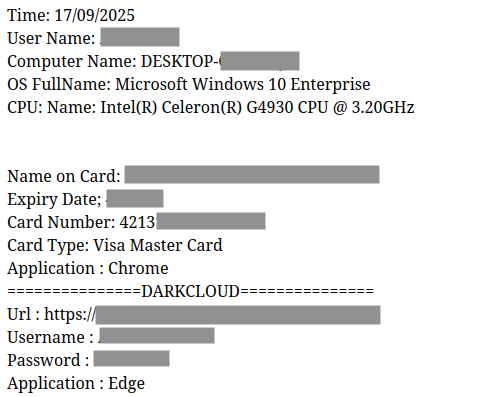
New malware analysis blog on #DarkCloud, an infostealer written in VB6 + a config extractor and string decryption tool for IDA Pro! esentire.com/blog/eye-of-th…

Seeing AdaptixC2 pop up in real breaches now 🔍Hunting tips for AdaptixC2: • Look for default user-agent • Use YARA rules + config extractor from @Unit42_Intel • Leverage C2 & hash feeds: ThreatFox, MalwareBazaar, @drb_ra Here’s how defenders can spot it fast 👇


Attackers are still dumping LSASS - comsvcs.dll is showing up in real breaches. What's Inside: ✅ Exact cmd ✅Visual Sigma mapping ✅ Microsoft (Kusto) + Splunk queries Thanks to @cyb3rops, @nas_bench & @_swachchhanda_ for the Sigma rules 👇 Full blog link in reply



LSASS dump via comsvcs.dll is still in play. Recently seen in a ransomware cases Rundll32 calling MiniDump from comsvcs is a big red flag. I tested this in the lab. These 3 Sigma rules fired without fail 👇 Blog with full command and sigma rule links dropping soon..


I teach malware analysis. Use this coupon for -40% on the intermediate course MAH4HEDGEHOGS …nalysis-for-hedgehogs.learnworlds.com
United States Trends
- 1. Bama 17.9K posts
- 2. #UFC322 32.7K posts
- 3. Oklahoma 27.3K posts
- 4. Ty Simpson 3,706 posts
- 5. Jeremiah Smith 1,710 posts
- 6. Boomer Sooner 1,966 posts
- 7. Wingo N/A
- 8. Iowa 19.1K posts
- 9. #AEWCollision 2,915 posts
- 10. Sabatini 1,346 posts
- 11. Mateer 3,152 posts
- 12. Noah Thomas N/A
- 13. Brent Venables 1,368 posts
- 14. #RollTide 3,209 posts
- 15. UConn 4,392 posts
- 16. Jungkook 254K posts
- 17. Heisman 11K posts
- 18. Kyle Daukaus N/A
- 19. #Svengoolie N/A
- 20. Benn 39.5K posts
You might like
-
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 Myrtus
Myrtus
@Myrtus0x0 -
 Karsten Hahn
Karsten Hahn
@struppigel -
 UNPACME
UNPACME
@unpacme -
 Arkbird
Arkbird
@Arkbird_SOLG -
 Tony Lambert
Tony Lambert
@ForensicITGuy -
 Dee
Dee
@ViriBack -
 Matthew
Matthew
@embee_research -
 RedDrip Team
RedDrip Team
@RedDrip7 -
 Jiří Vinopal
Jiří Vinopal
@vinopaljiri -
 Tommy M (TheAnalyst)
Tommy M (TheAnalyst)
@ffforward -
 Mehmet Ergene
Mehmet Ergene
@Cyb3rMonk -
 ReversingLabs
ReversingLabs
@ReversingLabs -
 CAPE Sandbox
CAPE Sandbox
@CapeSandbox -
 nao_sec
nao_sec
@nao_sec
Something went wrong.
Something went wrong.


































































































































