You might like
🚨 CFP aberto — Bug Bounty Village @ H2HC 2025 🚨 Achou um bug insano, bypass criativo ou tem case real de pentest/bug bounty? Manda sua talk! 👉 docs.google.com/forms/d/e/1FAI… #H2HC #BugBounty #Call4Papers #HackerCulture
This is some really nice research! It's definitely worth trying these techniques against cryptocurrency extensions! marektoth.com/blog/dom-based…
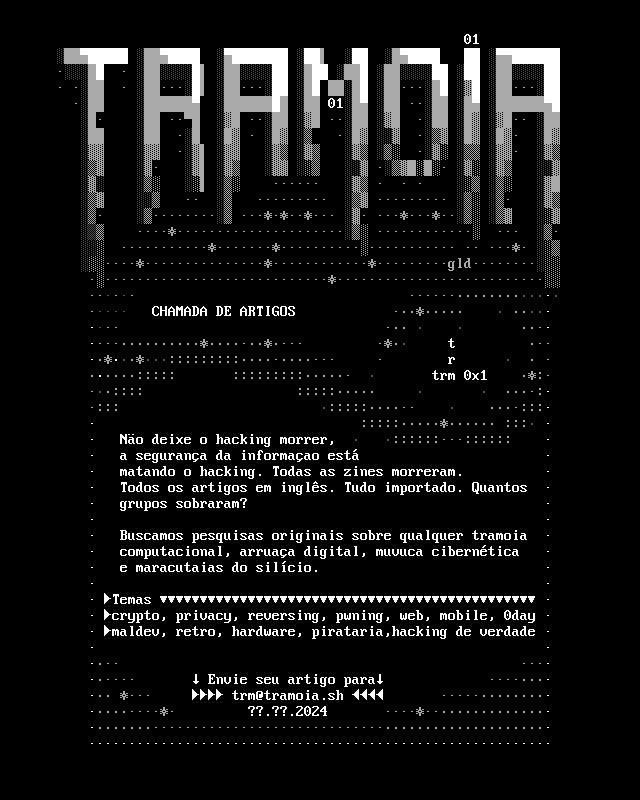
CHAMADA DE ARTIGOS 2025 Mais artigos, novos autores, pwnage e 0days. Com esses objetivos iniciamos a nova Chamada de Artigos 2025 para a segunda edição! Envie seu artigo para : [email protected]

New Active Directory Mindmap v2025.03! 🚀 📖 Readable version: orange-cyberdefense.github.io/ocd-mindmaps/i… 🔧 Now fully generated from markdown files—way easier to update and maintain! 💡 Got improvements? PRs welcome! 👉 github.com/Orange-Cyberde…

very pleased to announce the release of my new article based on my research that led to CVE-2024-46982 titled: Next.js, cache, and chains: the stale elixir zhero-web-sec.github.io/research-and-t… note: does not cover the latest findings shared in my recent posts enjoy reading;

ADCS Attack Techniques Cheatsheet for all of you lazy folks who prefer colored tables over reading a bunch of articles just to find some specific information: bit.ly/adcs-cheatsheet
New writeup from @_specters_ and I: we're finally allowed to disclose a vulnerability reported to Kia which would've allowed an attacker to remotely control almost all vehicles made after 2013 using only the license plate. Full disclosure: samcurry.net/hacking-kia
In August, watchTowr Labs hijacked parts of the global .mobi TLD - and went on to discover the mayhem that we could cause. Enjoy.... labs.watchtowr.com/we-spent-20-to…
Yay, I was awarded a $1000 bounty on @Hacker0x01 for a 1-Click RCE vulnerability! Collab with my bro @LuskaBol hackerone.com/xpl #TogetherWeHitHarder
PHP just fixed one of my RCE vulnerabilities, which affects XAMPP by default. Check to see if you are affected and update now! 🔥 blog.orange.tw/2024/06/cve-20…
Modern implant design: position independent malware development. A small blog post on how to design "modern" malware with features like global variables, raw strings, and compile-time hashing. 5pider.net/blog/2024/01/2… Repo: github.com/Cracked5pider/…
“Rook to XSS: How I hacked chess[.]com with a rookie exploit” skii.dev/rook-to-xss/ Really great read! If you’ve never looked, chess.com has a great off-platform bug bounty program via [email protected]
This is a very unknown technique. Tried googling it and found no results, so maybe even a novelty. This allows you to dump all domains from a Cloudflare user by doing nameserver correlation. Great for finding base domains owned by the company. celes.in/posts/cloudfla…
"A tale of making internet pollution free" - Exploiting Client-Side Prototype Pollution in the wild - @S1r1u5_ blog.s1r1us.ninja/research/PP
Sharing my experience with alias path traversals on nginx, and how we leaked sensitive data on Bitwarden and GCP with that. Along with that, we also released a tool called navgix to check for the presence of these vulnerabilities in an automated manner. labs.hakaioffsec.com/nginx-alias-tr…
I hacked into a @Bing CMS that allowed me to alter search results and take over millions of @Office365 accounts. How did I do it? Well, it all started with a simple click in @Azure… 👀 This is the story of #BingBang 🧵⬇️

The team at @OpenAI just fixed a critical account takeover vulnerability I reported few hours ago affecting #ChatGPT. It was possible to takeover someone's account, view their chat history, and access their billing information without them ever realizing it. Breakdown below 👇
We recently found a vulnerability affecting Hyundai and Genesis vehicles where we could remotely control the locks, engine, horn, headlights, and trunk of vehicles made after 2012. To explain how it worked and how we found it, we have @_specters_ as our mock car thief:

United States Trends
- 1. Ravens 57.3K posts
- 2. Lamar 45.8K posts
- 3. Bengals 51.3K posts
- 4. #heatedrivalry 11.3K posts
- 5. ilya 14.4K posts
- 6. shane 17K posts
- 7. Joe Burrow 20.5K posts
- 8. Zay Flowers 4,106 posts
- 9. Cowboys 92.5K posts
- 10. Chiefs 108K posts
- 11. Hudson 11.2K posts
- 12. #WhoDey 3,744 posts
- 13. Derrick Henry 4,421 posts
- 14. #hrspoilers 1,552 posts
- 15. connor storrie 1,783 posts
- 16. Sarah Beckstrom 213K posts
- 17. Harbaugh 3,111 posts
- 18. Zac Taylor 2,611 posts
- 19. AFC North 2,304 posts
- 20. Perine 1,582 posts
Something went wrong.
Something went wrong.